Mikrotik's own traffic with mangle rules
It is possible to control the output of Mikrotik's own traffic with mangle rules?
Re: Mikrotik's own traffic with mangle rules
What is the requirement in better detail.
a. identify user(s)/device(s), groups of users/devices
b. identify what traffic they should be allowed to execute.
c. identify any particular routes traffic should take
d. identify any traffic that the router needs to execute ( aka router services like VPN ).
Short answer: Yes, Long answer: Yes. Without more information,...............
a. identify user(s)/device(s), groups of users/devices
b. identify what traffic they should be allowed to execute.
c. identify any particular routes traffic should take
d. identify any traffic that the router needs to execute ( aka router services like VPN ).
Short answer: Yes, Long answer: Yes. Without more information,...............
Re: Mikrotik's own traffic with mangle rules [SOLVED]
Yes. It's covered by Packet Flow Diagram.
The "Mikrotik's own traffic" is a "routing process" here going through LOCAL:
https://help.mikrotik.com/docs/display/ ... lowDiagram

And mangle can catch, among other places, the "output" chain:
https://help.mikrotik.com/docs/display/ ... rOS-Output
Specifically in the "Mangle Output" and "Mangle Input", which break out the "Routing Decision" in first diagram:
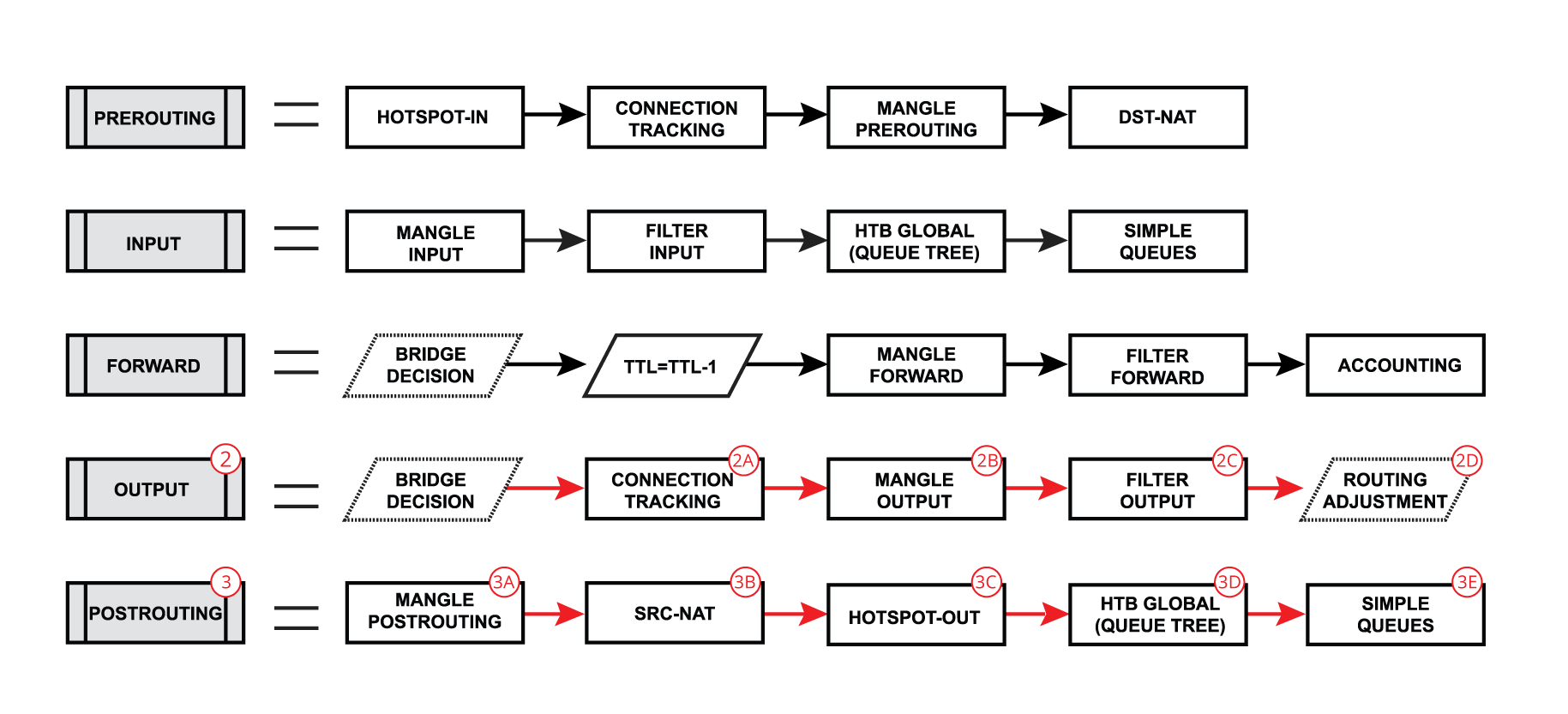
The OUTPUT and INPUT part are clear from first diagram, but just to clarify...
PREROUTING chain is traffic going through ⒾⓀ
POSTROUTING chain is traffic going through 🅙🅛
e.g. from the "break-out" of top diagram of this post
The "Mikrotik's own traffic" is a "routing process" here going through LOCAL:
https://help.mikrotik.com/docs/display/ ... lowDiagram
And mangle can catch, among other places, the "output" chain:
https://help.mikrotik.com/docs/display/ ... rOS-Output
Or when a packet is originated from the router (routing output):
The packet is originated from the router itself
the packet goes through the routing table to make a routing decision
A packet enters the output process
process packet through the Bridge decision;
send the packet through connection tracking;
process packet through the Mangle output chain;
process packet through the Filter output chain;
send the packet to routing adjustment ( policy routing)
The packet enters postrouting process;
- process packet through Mangle postrouting chain;
- process packet through NATs src-nat chain;
- if there is a hotspot undo any modifications made in hotspot-in;
- process packet through queue tree (HTB Global);
- process packet through simple queues;
Check if there is IPsec and then process through IPsec policies;
Specifically in the "Mangle Output" and "Mangle Input", which break out the "Routing Decision" in first diagram:

The OUTPUT and INPUT part are clear from first diagram, but just to clarify...
PREROUTING chain is traffic going through ⒾⓀ
POSTROUTING chain is traffic going through 🅙🅛
e.g. from the "break-out" of top diagram of this post
Re: Mikrotik's own traffic with mangle rules
Anav, thank you for your time and the incredible speed in responding.What is the requirement in better detail.
a. identify user(s)/device(s), groups of users/devices
b. identify what traffic they should be allowed to execute.
c. identify any particular routes traffic should take
d. identify any traffic that the router needs to execute ( aka router services like VPN ).
Short answer: Yes, Long answer: Yes. Without more information,...............
It would be options C and D, but precisely for D. The intention is to make Mikrotik itself execute some script tasks that will use the VPN and some DNS queries.
I initially had doubts about knowing the possibility, now I'm going to research and study. Thanks a lot for the help.
Re: Mikrotik's own traffic with mangle rules
Anm0, thank you for your time, incredible speed in putting together the material and responding.Yes. It's covered by Packet Flow Diagram.
The "Mikrotik's own traffic" is a "routing process" here going through LOCAL:
https://help.mikrotik.com/docs/display/ ... lowDiagram
And mangle can catch, among other places, the "output" chain:
https://help.mikrotik.com/docs/display/ ... rOS-OutputOr when a packet is originated from the router (routing output):
The packet is originated from the router itself
the packet goes through the routing table to make a routing decision
A packet enters the output process
process packet through the Bridge decision;
send the packet through connection tracking;
process packet through the Mangle output chain;
process packet through the Filter output chain;
send the packet to routing adjustment ( policy routing)
The packet enters postrouting process;
- process packet through Mangle postrouting chain;
- process packet through NATs src-nat chain;
- if there is a hotspot undo any modifications made in hotspot-in;
- process packet through queue tree (HTB Global);
- process packet through simple queues;
Check if there is IPsec and then process through IPsec policies;
Specifically in the "Mangle Output" and "Mangle Input", which break out the "Routing Decision" in first diagram:
The OUTPUT and INPUT part are clear from first diagram, but just to clarify...
PREROUTING chain is traffic going through ⒾⓀ
POSTROUTING chain is traffic going through 🅙🅛
e.g. from the "break-out" of top diagram of this post
You gave me a lot of content, Wow! Complex, I will need to assimilate the information and test a lot. Thank you very much for your help, you've already given me a lot of homework. lol!
Re: Mikrotik's own traffic with mangle rules
In simple terms there are tools you can use.
What is common to both is needing a table and an IP route.
One is create a table
add fib table=utilizeWANX
Create the route
add dst-address=0.0.0.0/0 gateway=ISPX routing-table=utilizeWANX
Then you have two options:
a. use routing rule This basically states, that any traffic coming from WANX ( and since this includes responses to external traffic hitting WANX like vpn handshake, any response will be forced out the table to WANX and not follow the normal main table routes.
add action=lookup-only-in-table src-address=WANX-IP table=utilizeWANX
b. use mangling These rule mark traffic coming in a WAN, and force any return traffic with those marks to go out same WAN, regardless of priority on main table as we force the traffic out a separate table. This is also valid for any port forwardings coming in on WANX.
add action=mark-connection chain=prerouting connection-mark=no-mark \
in-interface=WAN2 new-connection-mark=incomingWANX passthrough=yes
add action=mark-routing chain=output connection-mark=incomingWANX \
new-routing-mark=utilizeWANX passthrough=no
and modify fastrack rule....
add action=fasttrack-connection chain=forward comment=Fasttrack \
connection-state=established,related hw-offload=yes connection-mark=no-mark
These are just possible tools to consider, depending on how complex the config may be...... some variations are expected.
What is common to both is needing a table and an IP route.
One is create a table
add fib table=utilizeWANX
Create the route
add dst-address=0.0.0.0/0 gateway=ISPX routing-table=utilizeWANX
Then you have two options:
a. use routing rule This basically states, that any traffic coming from WANX ( and since this includes responses to external traffic hitting WANX like vpn handshake, any response will be forced out the table to WANX and not follow the normal main table routes.
add action=lookup-only-in-table src-address=WANX-IP table=utilizeWANX
b. use mangling These rule mark traffic coming in a WAN, and force any return traffic with those marks to go out same WAN, regardless of priority on main table as we force the traffic out a separate table. This is also valid for any port forwardings coming in on WANX.
add action=mark-connection chain=prerouting connection-mark=no-mark \
in-interface=WAN2 new-connection-mark=incomingWANX passthrough=yes
add action=mark-routing chain=output connection-mark=incomingWANX \
new-routing-mark=utilizeWANX passthrough=no
and modify fastrack rule....
add action=fasttrack-connection chain=forward comment=Fasttrack \
connection-state=established,related hw-offload=yes connection-mark=no-mark
These are just possible tools to consider, depending on how complex the config may be...... some variations are expected.
Re: Mikrotik's own traffic with mangle rules
Perfect, Anav.In simple terms there are tools you can use.
What is common to both is needing a table and an IP route.
One is create a table
add fib table=utilizeWANX
Create the route
add dst-address=0.0.0.0/0 gateway=ISPX routing-table=utilizeWANX
Then you have two options:
a. use routing rule This basically states, that any traffic coming from WANX ( and since this includes responses to external traffic hitting WANX like vpn handshake, any response will be forced out the table to WANX and not follow the normal main table routes.
add action=lookup-only-in-table src-address=WANX-IP table=utilizeWANX
b. use mangling These rule mark traffic coming in a WAN, and force any return traffic with those marks to go out same WAN, regardless of priority on main table as we force the traffic out a separate table. This is also valid for any port forwardings coming in on WANX.
add action=mark-connection chain=prerouting connection-mark=no-mark \
in-interface=WAN2 new-connection-mark=incomingWANX passthrough=yes
add action=mark-routing chain=output connection-mark=incomingWANX \
new-routing-mark=utilizeWANX passthrough=no
and modify fastrack rule....
add action=fasttrack-connection chain=forward comment=Fasttrack \
connection-state=established,related hw-offload=yes connection-mark=no-mark
These are just possible tools to consider, depending on how complex the config may be...... some variations are expected.
Thanks for the examples. Two ways, the simple one like routing and the more complicated one like mangle.
I understood your explanation.
Re: Mikrotik's own traffic with mangle rules
I'm the "big picture" guy ... I'd listen to @anav if you want something working 
@anav – the connection-mark=no-mark is pretty cleaver way to be generic about what's going through main routing table...
@anav – the connection-mark=no-mark is pretty cleaver way to be generic about what's going through main routing table...
and modify fastrack rule....
add action=fasttrack-connection chain=forward comment=Fasttrack \
connection-state=established,related hw-offload=yes connection-mark=no-mark
Re: Mikrotik's own traffic with mangle rules
My middle name is clever, I will give you hint.
Anav "SINDY" Llama
Anav "SINDY" Llama
Re: Mikrotik's own traffic with mangle rules
For completeness, the reason for the "extra rule" for fasttrack comes later in the Packet Flow. RouterOS has a feature called "fastrack" that's enabled in default firewall. This, essentially, does work when using routing tables... As you can see below, before the MANGLE PREROUTING, the FASTTRACKED? is checked ... so traffic can "jump the shark"
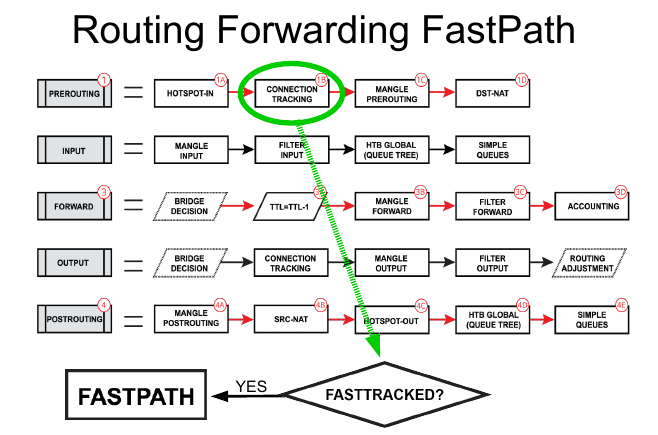
Traffic that belongs to a fast-tracked connection travels in FastPath, which means that it will not be visible by other router L3 facilities (firewall, queues, IPsec, IP accounting, VRF assignment, etc). Fasttrack lookups route before routing marks have been set, so it works only with the main routing table.

Last edited by Amm0 on Wed Sep 27, 2023 10:36 pm, edited 2 times in total.
Re: Mikrotik's own traffic with mangle rules
Super helpful to describe where it fits !!!
Re: Mikrotik's own traffic with mangle rules
It's very satisfying to witness a conversation between intelligent people.
If I understand correctly, using no-mark on the connection marked in the connection state would disable fasttracked? This way it would use the mangle rules and not be ignored by the jump from fasttrack to fastpath.
If I understand correctly, using no-mark on the connection marked in the connection state would disable fasttracked? This way it would use the mangle rules and not be ignored by the jump from fasttrack to fastpath.

