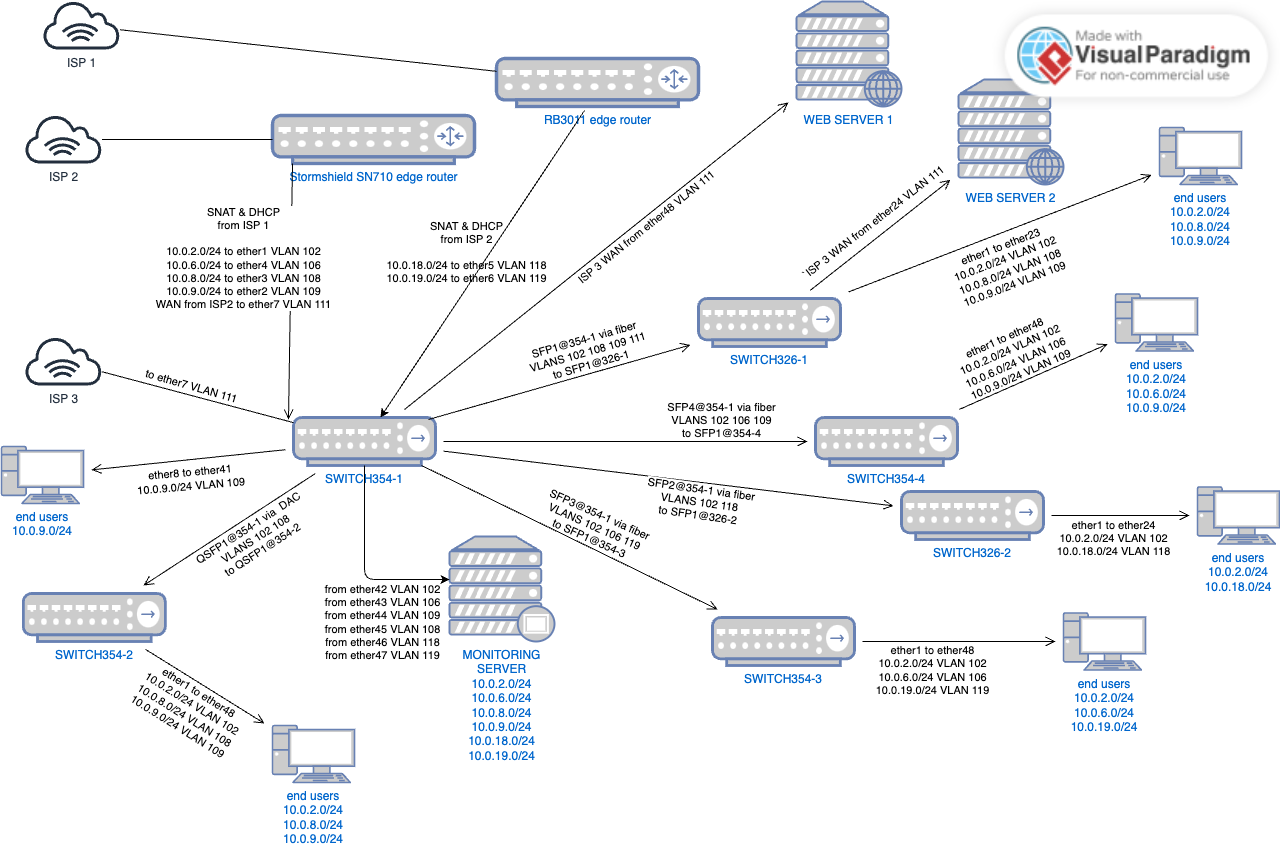
I'm fighting with configuration of my CRS354. I have a bridge set over all ports, some of them are set as access ports (defined both by PVID in /interface/bridge/port and by being set as "untagged" in /interface/bridge/vlan), some are set as trunk ports.
Bridge setup is simple:
0 R ;;; defconf
name="bridge" mtu=auto actual-mtu=1500 l2mtu=1584 arp=enabled arp-timeout=auto mac-address=78:9A:18:5A:89:32 protocol-mode=rstp fast-forward=yes igmp-snooping=no auto-mac=yes ageing-time=5m
priority=0x8000 max-message-age=20s forward-delay=15s transmit-hold-count=6 vlan-filtering=yes ether-type=0x8100 pvid=1 frame-types=admit-all ingress-filtering=yes dhcp-snooping=no
/interface bridge port add bridge=bridge comment="WAN 2" frame-types=admit-only-untagged-and-priority-tagged interface=ether7 pvid=111
/interface bridge port add bridge=bridge comment=defconf frame-types=admit-only-untagged-and-priority-tagged interface=ether48 pvid=111
/interface bridge port add bridge=bridge comment=defconf interface=sfp-sfpplus1
/interface bridge vlan add bridge=bridge comment="WAN 2" tagged=sfp-sfpplus1 untagged=ether7,ether48 vlan-ids=111
- secondary WAN input from the Internet Provider on ether7
- WAN goes to the first router via ether48
- WAN goes to another switch (CRS326) via sfp-sfpplus1 where it is being used by another router
The problem is... it does not work.
And when I try sniffing on this port by /tool/sniffer/quick interface=ether7, it shows only 802.2 protocol frames.
However, once I disable that ether7 from bridge - it immediately shows real traffic there. Once enabled in port - returns to show only 802.2 frames.
It looks like this:
[admin@Router354-1-PPD3-S3-1] /interface/bridge> /tool/sniffer/quick interface=ether7
Columns: INTERFACE, TIME, NUM, DIR, SRC-MAC, DST-MAC, PROTOCOL, SIZE, CPU
INTERFACE TIME NUM DIR SRC-MAC DST-MAC PROTOCOL SIZE CPU
ether7 14.215 8 <- CC:3E:5F:DF:87:80 01:80:C2:00:00:00 802.2 64 0
ether7 16.215 9 <- CC:3E:5F:DF:87:80 01:80:C2:00:00:00 802.2 64 0
ether7 18.215 10 <- CC:3E:5F:DF:87:80 01:80:C2:00:00:00 802.2 64 0
(here I'm disabling port from bridge, by /interface/bridge/port disable numbers=6)
ether7 29.973 20 <- AC:7A:56:89:CF:C0 FF:FF:FF:FF:FF:FF xxx.yyy.183.153: who has xxx.yyy.183.156? arp 60 0
ether7 30.215 21 <- CC:3E:5F:DF:87:80 01:80:C2:00:00:00 802.2 64 0
ether7 30.783 22 <- AC:7A:56:89:CF:C0 FF:FF:FF:FF:FF:FF xxx.yyy.183.153: who has xxx.yyy.183.155? arp 60 0
ether7 30.914 23 -> 78:9A:18:5A:89:44 33:33:00:00:00:16 fe80::7a9a:18ff:fe5a:8944 ff02::16 ipv6:icmpv6 130 0
ether7 30.944 24 -> 78:9A:18:5A:89:44 33:33:00:00:00:16 fe80::7a9a:18ff:fe5a:8944 ff02::16 ipv6:icmpv6 90 0
ether7 31.074 25 -> 78:9A:18:5A:89:44 33:33:00:00:00:16 fe80::7a9a:18ff:fe5a:8944 ff02::16 ipv6:icmpv6 90 0
ether7 31.415 26 <- 98:3F:60:AF:29:70 01:00:0C:CC:CC:CD 802.2 64 0
ether7 31.634 27 -> 78:9A:18:5A:89:44 33:33:00:00:00:16 fe80::7a9a:18ff:fe5a:8944 ff02::16 ipv6:icmpv6 130 0
ether7 32.215 28 <- CC:3E:5F:DF:87:80 01:80:C2:00:00:00 802.2 64 0
ether7 33.416 29 <- 98:3F:60:AF:29:70 01:00:0C:CC:CC:CD 802.2 64 0
ether7 33.802 30 <- AC:7A:56:89:CF:C0 FF:FF:FF:FF:FF:FF xxx.yyy.183.153: who has xxx.yyy.183.155? arp 60 0
ether7 34.215 31 <- CC:3E:5F:DF:87:80 01:80:C2:00:00:00 802.2 64 0
ether7 35.425 32 <- 98:3F:60:AF:29:70 01:00:0C:CC:CC:CD 802.2 64 0
ether7 35.516 33 <- AC:7A:56:89:CF:C0 FF:FF:FF:FF:FF:FF xxx.yyy.183.153: who has xxx.yyy.183.157? arp 60 0
(and here I'm enabling port in bridge again)
ether7 36.215 34 <- CC:3E:5F:DF:87:80 01:80:C2:00:00:00 802.2 64 0
ether7 36.89 35 <- 38:94:ED:CB:03:26 01:00:0C:CC:CC:CC 802.2 93 0
ether7 37.517 36 <- 98:3F:60:AF:29:70 01:00:0C:CC:CC:CD 802.2 64 0
ether7 37.522 37 -> 78:9A:18:5A:89:44 01:80:C2:00:00:00 802.2 53 0
ether7 38.215 38 <- CC:3E:5F:DF:87:80 01:80:C2:00:00:00 802.2 64 0
What am I doing wrong?
And it is not the problem with built-in sniffer, I have another Mikrotik device on port ether48 sniffing and there are just 802.2 frames. Also, I have checked that the network on port ether48 does not work - I have connected xxx.yyy.183.157 to this port and it is unreachable, but if I connect this device directly to the cable that goes into ether7 - instantly works.
Any ideas?