Wireguard VPN on dual WAN
Hello guys,
I want to setup wireguard VPN Site-to-Site on dual WAN on 2 Site, running OS v7.16.2
Site A: WAN1 primary PPPoE, WAN2 ILL backup, both are static IP
Site B: WAN1 primary PPPoE, WAN2 ILL backup, both are static IP
I want to make Wireguard traffic go throught WAN2, just give me sample configuration.
I have searched in forum but no scenario match with my case,
Thank you all,
I want to setup wireguard VPN Site-to-Site on dual WAN on 2 Site, running OS v7.16.2
Site A: WAN1 primary PPPoE, WAN2 ILL backup, both are static IP
Site B: WAN1 primary PPPoE, WAN2 ILL backup, both are static IP
I want to make Wireguard traffic go throught WAN2, just give me sample configuration.
I have searched in forum but no scenario match with my case,
Thank you all,
Last edited by haianh on Sat Dec 21, 2024 2:37 pm, edited 1 time in total.
Re: Wireguard VPN on dual WAN [SOLVED]
If all you want is that the site-to-site Wireguard between A and B would use WAN 2 at both sites, and if you don't plan on any other traffic among the public addresses of Site A and Site B, just add static routes:
Site A:
dst-address=ip.of.siteB.wan2/32 gateway=ip.or.siteA.wan2-gw
Site B:
dst-address=ip.of.siteA.wan2/32 gateway=ip.or.siteB.wan2-gw
For any more complicated scenario, you'll need policy routing in its full complexity, including special provisions for the specific behavior of Wireguard.
Site A:
dst-address=ip.of.siteB.wan2/32 gateway=ip.or.siteA.wan2-gw
Site B:
dst-address=ip.of.siteA.wan2/32 gateway=ip.or.siteB.wan2-gw
For any more complicated scenario, you'll need policy routing in its full complexity, including special provisions for the specific behavior of Wireguard.
Re: Wireguard VPN on dual WAN
this takes several steps, start with the correct configuration of the policy routing:
/routing table
add disabled=no fib name=to_WAN_main
add disabled=no fib name=to_WAN_bkp
/routing rule
add action=lookup disabled=no src-address=1.1.1.0/30 table=to_WAN_main
add action=lookup disabled=no routing-mark=to_WAN_main table=to_WAN_main
add action=lookup disabled=no src-address=2.2.2.0/30 table=to_WAN_bkp
add action=lookup disabled=no routing-mark=to_WAN_bkp table=to_WAN_bkp
/ip route
add disabled=no distance=1 dst-address=0.0.0.0/0 gateway=1.1.1.1 pref-src=1.1.1.2 routing-table=main
add disabled=no distance=2 dst-address=0.0.0.0/0 gateway=2.2.2.1 pref-src=2.2.2.2 routing-table=main
add disabled=no distance=1 dst-address=0.0.0.0/0 gateway=1.1.1.1 pref-src=1.1.1.2 routing-table=to_WAN_main
add disabled=no distance=1 dst-address=0.0.0.0/0 gateway=2.2.2.1 pref-src=2.2.2.2 routing-table=to_WAN_bkp
check it by ping:
/ping address=8.8.8.8 src-address=1.1.1.2
/ping address=8.8.8.8 src-address=2.2.2.2
If it works, I will in step 2 write you the Wireguard configuration
/routing table
add disabled=no fib name=to_WAN_main
add disabled=no fib name=to_WAN_bkp
/routing rule
add action=lookup disabled=no src-address=1.1.1.0/30 table=to_WAN_main
add action=lookup disabled=no routing-mark=to_WAN_main table=to_WAN_main
add action=lookup disabled=no src-address=2.2.2.0/30 table=to_WAN_bkp
add action=lookup disabled=no routing-mark=to_WAN_bkp table=to_WAN_bkp
/ip route
add disabled=no distance=1 dst-address=0.0.0.0/0 gateway=1.1.1.1 pref-src=1.1.1.2 routing-table=main
add disabled=no distance=2 dst-address=0.0.0.0/0 gateway=2.2.2.1 pref-src=2.2.2.2 routing-table=main
add disabled=no distance=1 dst-address=0.0.0.0/0 gateway=1.1.1.1 pref-src=1.1.1.2 routing-table=to_WAN_main
add disabled=no distance=1 dst-address=0.0.0.0/0 gateway=2.2.2.1 pref-src=2.2.2.2 routing-table=to_WAN_bkp
check it by ping:
/ping address=8.8.8.8 src-address=1.1.1.2
/ping address=8.8.8.8 src-address=2.2.2.2
If it works, I will in step 2 write you the Wireguard configuration
Re: Wireguard VPN on dual WAN
Thank you for the advice, the WAN2 is the backup when WAN1 down, so it also need to access the internet.If all you want is that the site-to-site Wireguard between A and B would use WAN 2 at both sites, and if you don't plan on any other traffic among the public addresses of Site A and Site B, just add static routes:
Site A:
dst-address=ip.of.siteB.wan2/32 gateway=ip.or.siteA.wan2-gw
Site B:
dst-address=ip.of.siteA.wan2/32 gateway=ip.or.siteB.wan2-gw
For any more complicated scenario, you'll need policy routing in its full complexity, including special provisions for the specific behavior of Wireguard.
Re: Wireguard VPN on dual WAN
thank you for the instruction, I'm sorry that forgot to inform WAN1 is PPPoE, not static, so the config is different ?this takes several steps, start with the correct configuration of the policy routing:
/routing table
add disabled=no fib name=to_WAN_main
add disabled=no fib name=to_WAN_bkp
/routing rule
add action=lookup disabled=no src-address=1.1.1.0/30 table=to_WAN_main
add action=lookup disabled=no routing-mark=to_WAN_main table=to_WAN_main
add action=lookup disabled=no src-address=2.2.2.0/30 table=to_WAN_bkp
add action=lookup disabled=no routing-mark=to_WAN_bkp table=to_WAN_bkp
/ip route
add disabled=no distance=1 dst-address=0.0.0.0/0 gateway=1.1.1.1 pref-src=1.1.1.2 routing-table=main
add disabled=no distance=2 dst-address=0.0.0.0/0 gateway=2.2.2.1 pref-src=2.2.2.2 routing-table=main
add disabled=no distance=1 dst-address=0.0.0.0/0 gateway=1.1.1.1 pref-src=1.1.1.2 routing-table=to_WAN_main
add disabled=no distance=1 dst-address=0.0.0.0/0 gateway=2.2.2.1 pref-src=2.2.2.2 routing-table=to_WAN_bkp
check it by ping:
/ping address=8.8.8.8 src-address=1.1.1.2
/ping address=8.8.8.8 src-address=2.2.2.2
If it works, I will in step 2 write you the Wireguard configuration
Re: Wireguard VPN on dual WAN
Before replying....... Is there any port forwarding going on (aka external users) or just VPN coming in externally?
Both WAN1s are static PPPOE addresses, so confirm
a. they dont change
b. they are indeed public not private IP addresses.
Both WAN2s are ?????
a. static or private IP addresses???
b. public or private IP addresses??
There is also a bug with Wireguard when coming in on WAN2 while its the secondary WAN.
Both WAN1s are static PPPOE addresses, so confirm
a. they dont change
b. they are indeed public not private IP addresses.
Both WAN2s are ?????
a. static or private IP addresses???
b. public or private IP addresses??
There is also a bug with Wireguard when coming in on WAN2 while its the secondary WAN.
Re: Wireguard VPN on dual WAN
MAIN ROUTER A ( server peer for wireguard handshake )
/routing table
add disabled=no fib name=use-WAN2
/ip route ( minimum )
add distance=2 check-gateway=ping dst-address=0.0.0.0/0 gateway=pppoe-out1
add distance=4 dst-address=0.0.0.0/0 gateway=WAN2-gateway-ip
add dst-address=0.0.0.0/0 gateway=WAN2-gateway-ip routing-table=use-WAN2
/ip route ( better - recursive - checks connection to internet is actually up, not just connection to ISP )
add distance=2 check-gateway=ping dst-address=0.0.0.0/0 gateway=1.0.0.1 scope=10 target-scope=12
add distance=2 dst-address=1.0.0.1/32 gateway=pppoe-out1 scope=10 target-scope=11
add distance=4 dst-address=0.0.0.0/0 gateway=WAN2-gateway-ip
add dst-address=0.0.0.0/0 gateway=WAN2-gateway-ip routing-table=use-WAN2
Now all traffic will go to WAN1, and if WAN1 is not available traffic will move to WAN2 and will go back to WAN1 when it is functional.
Ensure you use the standard masquerade sourcenat rule as well.
/ip firewall mangle ( to ensure traffic coming in on WAN2 goes back out WAN2 )
add chain=input action=mark-connection connection-mark=no-mark \
in-interface=WAN2 new-connection-mark=incomingWAN2 passthrough=yes
add chain=output action=mark-routing connection-mark=incomingWAN2 \
new-routing-mark=use-WAN2 passthrough=no
Ensure on the forward chain fasttrack rule you add the following:
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related connection=mark=no-mark
Finally to deal with the bug, we need a trick destination nat rule to ensure wireguard traffic does NOT go back out WAN1
/ip firewall nat
add action=masquerade chain=srcnat out-interface-list=WAN
add action=dstnat chain=dst-nat in-interface=WAN2 dst-address-type=local dst-port=wireguardport protocol=udp to-address=staticWAN1-ip
The idea being, the router will assume all wireguard traffic that wants to exit WAN1, will be un-detinatted to wan2........
+++++++++++++++++++++
Basically the same for Router B.
Main differences - no need for input chain rule for handshake.
Allowed peers need endpoint address of WAN2 on router A, and wireguard port and persistent keep alive set.
Would add another mangle rule on router B as first rule to ensure MTU handling....
add action=change-mss chain=forward comment="Clamp MSS to PMTU for Outgoing packets" new-mss=clamp-to-pmtu out-interface=wireguard1 passthrough=yes protocol=tcp tcp-flags=syn
++++++++++++
Best bet is to post complete config for review after an attempt to incorporate method of choice.
/export file=anynameyouwish ( minus router serial number, any public WANIP information, keys etc. )
/routing table
add disabled=no fib name=use-WAN2
/ip route ( minimum )
add distance=2 check-gateway=ping dst-address=0.0.0.0/0 gateway=pppoe-out1
add distance=4 dst-address=0.0.0.0/0 gateway=WAN2-gateway-ip
add dst-address=0.0.0.0/0 gateway=WAN2-gateway-ip routing-table=use-WAN2
/ip route ( better - recursive - checks connection to internet is actually up, not just connection to ISP )
add distance=2 check-gateway=ping dst-address=0.0.0.0/0 gateway=1.0.0.1 scope=10 target-scope=12
add distance=2 dst-address=1.0.0.1/32 gateway=pppoe-out1 scope=10 target-scope=11
add distance=4 dst-address=0.0.0.0/0 gateway=WAN2-gateway-ip
add dst-address=0.0.0.0/0 gateway=WAN2-gateway-ip routing-table=use-WAN2
Now all traffic will go to WAN1, and if WAN1 is not available traffic will move to WAN2 and will go back to WAN1 when it is functional.
Ensure you use the standard masquerade sourcenat rule as well.
/ip firewall mangle ( to ensure traffic coming in on WAN2 goes back out WAN2 )
add chain=input action=mark-connection connection-mark=no-mark \
in-interface=WAN2 new-connection-mark=incomingWAN2 passthrough=yes
add chain=output action=mark-routing connection-mark=incomingWAN2 \
new-routing-mark=use-WAN2 passthrough=no
Ensure on the forward chain fasttrack rule you add the following:
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related connection=mark=no-mark
Finally to deal with the bug, we need a trick destination nat rule to ensure wireguard traffic does NOT go back out WAN1
/ip firewall nat
add action=masquerade chain=srcnat out-interface-list=WAN
add action=dstnat chain=dst-nat in-interface=WAN2 dst-address-type=local dst-port=wireguardport protocol=udp to-address=staticWAN1-ip
The idea being, the router will assume all wireguard traffic that wants to exit WAN1, will be un-detinatted to wan2........
+++++++++++++++++++++
Basically the same for Router B.
Main differences - no need for input chain rule for handshake.
Allowed peers need endpoint address of WAN2 on router A, and wireguard port and persistent keep alive set.
Would add another mangle rule on router B as first rule to ensure MTU handling....
add action=change-mss chain=forward comment="Clamp MSS to PMTU for Outgoing packets" new-mss=clamp-to-pmtu out-interface=wireguard1 passthrough=yes protocol=tcp tcp-flags=syn
++++++++++++
Best bet is to post complete config for review after an attempt to incorporate method of choice.
/export file=anynameyouwish ( minus router serial number, any public WANIP information, keys etc. )
Re: Wireguard VPN on dual WAN
The command:MAIN ROUTER A ( server peer for wireguard handshake )
/routing table
add disabled=no fib name=use-WAN2
/ip route ( minimum )
add distance=2 check-gateway=ping dst-address=0.0.0.0/0 gateway=pppoe-out1
add distance=4 dst-address=0.0.0.0/0 gateway=WAN2-gateway-ip
add dst-address=0.0.0.0/0 gateway=WAN2-gateway-ip routing-table=use-WAN2
/ip route ( better - recursive - checks connection to internet is actually up, not just connection to ISP )
add distance=2 check-gateway=ping dst-address=0.0.0.0/0 gateway=1.0.0.1 scope=10 target-scope=12
add distance=2 dst-address=1.0.0.1/32 gateway=pppoe-out1 scope=10 target-scope=11
add distance=4 dst-address=0.0.0.0/0 gateway=WAN2-gateway-ip
add dst-address=0.0.0.0/0 gateway=WAN2-gateway-ip routing-table=use-WAN2
Now all traffic will go to WAN1, and if WAN1 is not available traffic will move to WAN2 and will go back to WAN1 when it is functional.
Ensure you use the standard masquerade sourcenat rule as well.
/ip firewall mangle ( to ensure traffic coming in on WAN2 goes back out WAN2 )
add chain=input action=mark-connection connection-mark=no-mark \
in-interface=WAN2 new-connection-mark=incomingWAN2 passthrough=yes
add chain=output action=mark-routing connection-mark=incomingWAN2 \
new-routing-mark=use-WAN2 passthrough=no
Ensure on the forward chain fasttrack rule you add the following:
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related connection=mark=no-mark
Finally to deal with the bug, we need a trick destination nat rule to ensure wireguard traffic does NOT go back out WAN1
/ip firewall nat
add action=masquerade chain=srcnat out-interface-list=WAN
add action=dstnat chain=dst-nat in-interface=WAN2 dst-address-type=local dst-port=wireguardport protocol=udp to-address=staticWAN1-ip
The idea being, the router will assume all wireguard traffic that wants to exit WAN1, will be un-detinatted to wan2........
+++++++++++++++++++++
Basically the same for Router B.
Main differences - no need for input chain rule for handshake.
Allowed peers need endpoint address of WAN2 on router A, and wireguard port and persistent keep alive set.
Would add another mangle rule on router B as first rule to ensure MTU handling....
add action=change-mss chain=forward comment="Clamp MSS to PMTU for Outgoing packets" new-mss=clamp-to-pmtu out-interface=wireguard1 passthrough=yes protocol=tcp tcp-flags=syn
++++++++++++
Best bet is to post complete config for review after an attempt to incorporate method of choice.
/export file=anynameyouwish ( minus router serial number, any public WANIP information, keys etc. )
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related connection=mark=no-mark
need to correct with:
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related connection-mark=no-mark
After I followed your config, Wireguard traffic still go on WAN1, I will give you my current configuration.
Last edited by haianh on Sun Dec 22, 2024 2:06 am, edited 2 times in total.
Re: Wireguard VPN on dual WAN
When it's fixed, do I need the config you give me ?Before replying....... Is there any port forwarding going on (aka external users) or just VPN coming in externally?
Both WAN1s are static PPPOE addresses, so confirm
a. they dont change
b. they are indeed public not private IP addresses.
Both WAN2s are ?????
a. static or private IP addresses???
b. public or private IP addresses??
There is also a bug with Wireguard when coming in on WAN2 while its the secondary WAN.
Re: Wireguard VPN on dual WAN
Site A:MAIN ROUTER A ( server peer for wireguard handshake )
/routing table
add disabled=no fib name=use-WAN2
/ip route ( minimum )
add distance=2 check-gateway=ping dst-address=0.0.0.0/0 gateway=pppoe-out1
add distance=4 dst-address=0.0.0.0/0 gateway=WAN2-gateway-ip
add dst-address=0.0.0.0/0 gateway=WAN2-gateway-ip routing-table=use-WAN2
/ip route ( better - recursive - checks connection to internet is actually up, not just connection to ISP )
add distance=2 check-gateway=ping dst-address=0.0.0.0/0 gateway=1.0.0.1 scope=10 target-scope=12
add distance=2 dst-address=1.0.0.1/32 gateway=pppoe-out1 scope=10 target-scope=11
add distance=4 dst-address=0.0.0.0/0 gateway=WAN2-gateway-ip
add dst-address=0.0.0.0/0 gateway=WAN2-gateway-ip routing-table=use-WAN2
Now all traffic will go to WAN1, and if WAN1 is not available traffic will move to WAN2 and will go back to WAN1 when it is functional.
Ensure you use the standard masquerade sourcenat rule as well.
/ip firewall mangle ( to ensure traffic coming in on WAN2 goes back out WAN2 )
add chain=input action=mark-connection connection-mark=no-mark \
in-interface=WAN2 new-connection-mark=incomingWAN2 passthrough=yes
add chain=output action=mark-routing connection-mark=incomingWAN2 \
new-routing-mark=use-WAN2 passthrough=no
Ensure on the forward chain fasttrack rule you add the following:
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related connection=mark=no-mark
Finally to deal with the bug, we need a trick destination nat rule to ensure wireguard traffic does NOT go back out WAN1
/ip firewall nat
add action=masquerade chain=srcnat out-interface-list=WAN
add action=dstnat chain=dst-nat in-interface=WAN2 dst-address-type=local dst-port=wireguardport protocol=udp to-address=staticWAN1-ip
The idea being, the router will assume all wireguard traffic that wants to exit WAN1, will be un-detinatted to wan2........
+++++++++++++++++++++
Basically the same for Router B.
Main differences - no need for input chain rule for handshake.
Allowed peers need endpoint address of WAN2 on router A, and wireguard port and persistent keep alive set.
Would add another mangle rule on router B as first rule to ensure MTU handling....
add action=change-mss chain=forward comment="Clamp MSS to PMTU for Outgoing packets" new-mss=clamp-to-pmtu out-interface=wireguard1 passthrough=yes protocol=tcp tcp-flags=syn
++++++++++++
Best bet is to post complete config for review after an attempt to incorporate method of choice.
/export file=anynameyouwish ( minus router serial number, any public WANIP information, keys etc. )
# 2024-12-22 07:27:56 by RouterOS 7.16.2
# software id = 9931-M8FK
#
# model = CCR1016-12G
# serial number =
/interface bridge
add name=guest-lan
add name=py1-lan
/interface ethernet
set [ find default-name=ether1 ] comment=WAN-FTTH
set [ find default-name=ether2 ] comment=WAN-ILL
/interface pppoe-client
add disabled=no interface=ether1 name=WAN-FTTH user=netnam_manipy
/interface wireguard
add listen-port=51248 mtu=1420 name=WG-VPN-To-PY2
add listen-port=12677 mtu=1420 name=WG-client-to-site-PY1
/interface list
add name=LAN
add name=WAN
/interface wireless security-profiles
set [ find default=yes ] supplicant-identity=MikroTik
/ip pool
add name=dhcp_pool0 ranges=10.0.255.1-10.0.255.253
add name=dhcp_pool1 ranges=10.22.10.10-10.22.10.200
/ip dhcp-server
add address-pool=dhcp_pool0 interface=guest-lan lease-time=1d name=guest-dhcp
add address-pool=dhcp_pool1 interface=py1-lan lease-time=8h name=dhcp1
/port
set 0 name=serial0
set 1 name=serial1
/routing table
add disabled=no fib name=FTTH-table
add disabled=no fib name=ILL-table
/interface bridge port
add bridge=py1-lan interface=ether11
add bridge=py1-lan interface=ether12
add bridge=guest-lan interface=ether8
add bridge=py1-lan interface=ether9
add bridge=py1-lan interface=ether10
/ip neighbor discovery-settings
set discover-interface-list=!dynamic
/interface l2tp-server server
set use-ipsec=yes
/interface list member
add interface=guest-lan list=LAN
add interface=py1-lan list=LAN
add interface=WAN-FTTH list=WAN
add interface=ether2 list=WAN
/interface wireguard peers
add allowed-address=172.25.0.0/16 endpoint-address=SiteB-WAN2-IP \
endpoint-port=51248 interface=WG-VPN-To-PY2 name=vpn-to-PY2 public-key=\
""
add allowed-address=10.22.19.2/32 interface=WG-client-to-site-PY1 name=\
hangmmh public-key=""
add allowed-address=10.22.19.1/32 interface=WG-client-to-site-PY1 name=bh.anh \
public-key=""
add allowed-address=10.22.19.3/32 interface=WG-client-to-site-PY1 name=\
ngocmmh public-key=""
add allowed-address=10.22.19.4/32 interface=WG-client-to-site-PY1 name=\
damhammh public-key=""
add allowed-address=10.22.19.5/32 interface=WG-client-to-site-PY1 name=\
hung.bravo public-key=""
add allowed-address=10.22.19.6/32 interface=WG-client-to-site-PY1 name=\
hoangbravo public-key=""
add allowed-address=10.22.19.7/32 interface=WG-client-to-site-PY1 name=\
bh.anh2 public-key=""
add allowed-address=10.22.19.8/32 interface=WG-client-to-site-PY1 name=\
bh.anh3 public-key=""
add allowed-address=10.22.19.9/32 interface=WG-client-to-site-PY1 name=\
lanbravo public-key=""
add allowed-address=10.22.19.10/32 interface=WG-client-to-site-PY1 name=\
nm.hung public-key=""
/ip address
add address=10.22.10.254/24 interface=py1-lan network=10.22.10.0
add address=10.0.255.254/24 interface=guest-lan network=10.0.255.0
add address=202.151.163.46/30 interface=ether2 network=202.151.163.44
add address=10.22.0.254/30 interface=WG-VPN-To-PY2 network=10.22.0.252
add address=10.22.19.254/24 interface=WG-client-to-site-PY1 network=\
10.22.19.0
/ip cloud
set ddns-enabled=yes
/ip dhcp-server network
add address=10.0.255.0/24 gateway=10.0.255.254
add address=10.22.10.0/24 dns-server=8.8.8.8,8.8.4.4 gateway=10.22.10.254
/ip dns
set servers=8.8.8.8,8.8.4.4
/ip firewall address-list
add address=172.20.0.0/16 list=LAN
add address=10.0.255.0/24 list=LAN
add address=10.22.10.0/24 list=LAN
add address=thuedientu.gdt.gov.vn list=traffic-via-ILL
add address=172.25.0.0/16 list=VPN
add address=tracuunnt.gdt.gov.vn list=traffic-via-ILL
add address=vieclamthainguyen.gov.vn list=traffic-via-ILL
add address=sn.mynetname.net list=WAN
add address=dichvucong.thainguyen.gov.vn list=traffic-via-ILL
add address=hoadondientu.gdt.gov.vn list=traffic-via-ILL
add address=www.gdt.gov.vn list=traffic-via-ILL
add address=thainguyen.gov.vn list=traffic-via-ILL
add address=canhan.gdt.gov.vn list=traffic-via-ILL
add address=kcn.thainguyen.gov.vn list=traffic-via-ILL
add address=speedtest.vn list=traffic-via-ILL
/ip firewall filter
add action=accept chain=input comment="allow WireGuard" dst-port=12677 \
protocol=udp
add action=accept chain=input src-address=10.22.19.0/24
add action=accept chain=input dst-port=51248 protocol=udp src-address=\
SiteB-WAN1-IP
add action=accept chain=input dst-port=51248 protocol=udp src-address=\
SiteB-WAN2-IP
/ip firewall nat
add action=dst-nat chain=dstnat dst-address=WAN1-IP dst-port=443 \
protocol=tcp to-addresses=10.22.10.253 to-ports=443
add action=dst-nat chain=dstnat dst-address=WAN2-IP dst-port=443 \
protocol=tcp to-addresses=10.22.10.253 to-ports=443
add action=masquerade chain=srcnat out-interface=WAN-FTTH to-addresses=\
WAN1-IP
add action=masquerade chain=srcnat out-interface=ether2 to-addresses=\
WAN2-IP
/ip ipsec profile
set [ find default=yes ] dpd-interval=2m dpd-maximum-failures=5
/ip route
add disabled=no distance=1 dst-address=172.20.0.0/16 gateway=10.22.10.253 \
routing-table=main scope=30 suppress-hw-offload=no target-scope=10
add disabled=no distance=1 dst-address=172.25.0.0/16 gateway=WG-VPN-To-PY2 \
routing-table=main scope=30 suppress-hw-offload=no target-scope=10
add disabled=no distance=1 dst-address=10.22.20.0/24 gateway=10.22.0.253 \
routing-table=main scope=30 suppress-hw-offload=no target-scope=10
add check-gateway=ping disabled=no distance=4 dst-address=0.0.0.0/0 gateway=\
WAN2-Gateway-IP routing-table=main scope=30 suppress-hw-offload=no \
target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=\
WAN2-Gateway-IP routing-table=ILL-table scope=30 suppress-hw-offload=no \
target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=\
WAN1-Gateway-IP routing-table=FTTH-table scope=30 suppress-hw-offload=no \
target-scope=10
add check-gateway=ping disabled=no distance=2 dst-address=0.0.0.0/0 gateway=\
8.8.8.8 routing-table=main scope=10 suppress-hw-offload=no target-scope=\
12
add check-gateway=ping disabled=no distance=2 dst-address=8.8.8.8/32 gateway=\
WAN1-Gateway-IP routing-table=main scope=10 suppress-hw-offload=no \
target-scope=11
/ip service
set telnet disabled=yes
set ftp disabled=yes
set www disabled=yes
set ssh disabled=yes
set api disabled=yes
set api-ssl disabled=yes
/lcd
set time-interval=daily
/system clock
set time-zone-name=Asia/Ho_Chi_Minh
/system identity
set name=PY1-router-mikrotik
/system note
set show-at-login=no
/system ntp client
set enabled=yes
/system ntp client servers
add address=vn.pool.ntp.org
/tool e-mail
set from=1@gmail.com port=465 server=smtp.gmail.com tls=yes user=\
1@gmail.com
Site B:
# 2024-12-22 07:29:16 by RouterOS 7.16.2
# software id = 2M0R-ULGQ
#
# model = CCR2004-16G-2S+
# serial number =
/interface bridge
add name=guest-lan
add name=py2-lan
/interface ethernet
set [ find default-name=ether1 ] comment=WAN-FTTH
set [ find default-name=ether2 ] comment=WAN-ILL
/interface pppoe-client
add disabled=no interface=ether1 name=netnam-ftth user=netnam_manitn2
/interface wireguard
add listen-port=51248 mtu=1420 name=WG-VPN-To-PY1
add listen-port=35359 mtu=1420 name=wg-vpn-client-to-PY2
/interface list
add name=LAN
/ip pool
add name=dhcp_pool0 ranges=10.255.255.1-10.255.255.250
/ip dhcp-server
add address-pool=dhcp_pool0 interface=guest-lan lease-time=8h name=dhcp1
/port
set 0 name=serial0
set 1 name=serial1
/routing table
add disabled=no fib name=FTTH-table
add disabled=no fib name=ILL-table
/interface bridge port
add bridge=py2-lan interface=ether16
add bridge=py2-lan interface=ether15
add bridge=py2-lan interface=ether14
add bridge=py2-lan interface=ether13
add bridge=guest-lan interface=ether12
/ip neighbor discovery-settings
set discover-interface-list=!dynamic
/interface list member
add interface=guest-lan list=LAN
add interface=py2-lan list=LAN
/interface wireguard peers
add allowed-address=172.20.0.0/16 endpoint-address=SiteB-WAN2-IP \
endpoint-port=51248 interface=WG-VPN-To-PY1 name=vpn-to-PY1 public-key=\
""
add allowed-address=10.22.29.1/24 interface=wg-vpn-client-to-PY2 name=bh.anh \
public-key=""
/ip address
add address=10.22.20.254/24 interface=py2-lan network=10.22.20.0
add address=10.255.255.254/24 interface=guest-lan network=10.255.255.0
add address=101.96.76.126/30 interface=ether2 network=101.96.76.124
add address=10.22.0.253/30 interface=WG-VPN-To-PY1 network=10.22.0.252
add address=10.22.29.254/24 interface=wg-vpn-client-to-PY2 network=10.22.29.0
/ip cloud
set ddns-enabled=yes
/ip dhcp-server network
add address=10.255.255.0/24 dns-server=8.8.8.8,8.8.4.4 gateway=10.255.255.254
/ip dns
set servers=8.8.8.8,8.8.4.4
/ip firewall address-list
add address=172.25.0.0/16 list=LAN
add address=10.255.255.0/24 list=LAN
add address=10.22.20.0/24 list=LAN
add address=10.22.29.0/24 list=VPN
add address=172.20.0.0/16 list=VPN
/ip firewall filter
add action=accept chain=input dst-port=35359 protocol=udp
add action=accept chain=input src-address=10.22.29.0/24
add action=accept chain=input dst-port=51248 protocol=udp src-address=\
SiteA-WAN1-IP
add action=accept chain=input dst-port=51248 protocol=udp src-address=\
SiteA-WAN2-IP
/ip firewall nat
add action=dst-nat chain=dstnat dst-address=WAN2-IP dst-port=443 \
protocol=tcp to-addresses=10.22.20.253 to-ports=443
add action=dst-nat chain=dstnat dst-address=WAN1-IP dst-port=443 \
protocol=tcp to-addresses=10.22.20.253 to-ports=443
add action=masquerade chain=srcnat out-interface=netnam-ftth to-addresses=\
WAN1-IP
add action=masquerade chain=srcnat out-interface=ether2 to-addresses=\
WAN2-IP
/ip ipsec profile
set [ find default=yes ] dpd-interval=2m dpd-maximum-failures=5
/ip route
add check-gateway=ping disabled=no distance=4 dst-address=0.0.0.0/0 gateway=\
WAN2-Gateway-IP routing-table=main scope=30 suppress-hw-offload=no \
target-scope=10
add disabled=no distance=4 dst-address=10.22.10.0/24 gateway=10.22.0.254 \
routing-table=main scope=30 suppress-hw-offload=no target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=\
WAN1-Gateway-IP routing-table=FTTH-table scope=30 suppress-hw-offload=no \
target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=\
WAN2-Gateway-IP routing-table=ILL-table scope=30 suppress-hw-offload=no \
target-scope=10
add check-gateway=ping disabled=no distance=2 dst-address=0.0.0.0/0 gateway=\
8.8.8.8 routing-table=main scope=10 suppress-hw-offload=no target-scope=\
12
add disabled=no distance=1 dst-address=172.20.0.0/16 gateway=WG-VPN-To-PY1 \
routing-table=main scope=30 suppress-hw-offload=no target-scope=10
add disabled=no dst-address=172.25.0.0/16 gateway=10.22.20.253 routing-table=\
main suppress-hw-offload=no
add check-gateway=ping disabled=no distance=2 dst-address=8.8.8.8/32 gateway=\
WAN1-Gateway-IP routing-table=main scope=10 suppress-hw-offload=no \
target-scope=11
/ip service
set telnet disabled=yes
set ftp disabled=yes
set www disabled=yes
set ssh disabled=yes
set api disabled=yes
set api-ssl disabled=yes
/system clock
set time-zone-name=Asia/Ho_Chi_Minh
/system identity
set name=PY2-Mikrotik-Router
/system note
set show-at-login=no
/system ntp client
set enabled=yes
/system ntp client servers
add address=vn.pool.ntp.org
/system routerboard settings
set enter-setup-on=delete-key
Re: Wireguard VPN on dual WAN
Before I get two into it....
You never mentioned two wireguard networks, what is the purpose please.
I dont see any value in dual connections between the same two routers, if one router has an isssue, 50 wireguard networks between the two will still not be fruitful.
Also is the intention for Router A or Router B to be the client server for handshake.
I thought it was Router A.......
You never mentioned two wireguard networks, what is the purpose please.
I dont see any value in dual connections between the same two routers, if one router has an isssue, 50 wireguard networks between the two will still not be fruitful.
Also is the intention for Router A or Router B to be the client server for handshake.
I thought it was Router A.......
Re: Wireguard VPN on dual WAN
@sindy already gave you the best and simplest answer to your needs. Did you really try to apply it at all?
Re: Wireguard VPN on dual WAN
Okay, I see what Sindy means now.......... possible due to all static public IP addresses...
Further its simply router to router connectivity no need to go out internet of the other.....
Thus Router B being peer client will send wireguard handshake and due to SIndys rule go out its WAN2 ( heading for WAN2 of Router A)
Router A will respond to the handshake and using its static route ensure the reply goes out its WAN2.
+++++++++++++++++++
Thus we avoid mangling rules or routing rules altogether and also getting rid of two Wireguard interfaces, when only one is required.
Simplify where possible is a decent MT motto.
Also in your config, besides some allowed IPs missing the wireguard address (site to site) you have some weird non-existant IPs in the mix 172.25.xx AND 172.20.xx
What I did do is create two subnets for the single wireguard interface separating remote warrior access to Router A and the site to site between Router A and Router B, for some clarity.
Simplified dstnat rules and masquerade rules.
Site A:
....
...............
Missing pool for main lan???
Missing interface list entries???
Site B:
...............
Further its simply router to router connectivity no need to go out internet of the other.....
Thus Router B being peer client will send wireguard handshake and due to SIndys rule go out its WAN2 ( heading for WAN2 of Router A)
Router A will respond to the handshake and using its static route ensure the reply goes out its WAN2.
+++++++++++++++++++
Thus we avoid mangling rules or routing rules altogether and also getting rid of two Wireguard interfaces, when only one is required.
Simplify where possible is a decent MT motto.
Also in your config, besides some allowed IPs missing the wireguard address (site to site) you have some weird non-existant IPs in the mix 172.25.xx AND 172.20.xx
What I did do is create two subnets for the single wireguard interface separating remote warrior access to Router A and the site to site between Router A and Router B, for some clarity.
Simplified dstnat rules and masquerade rules.
Site A:
....
Code: Select all
# 2024-12-22 07:27:56 by RouterOS 7.16.2
# software id = 9931-M8FK
#
# model = CCR1016-12G
# serial number =
/interface bridge
add name=guest-lan
add name=py1-lan
/interface ethernet
set [ find default-name=ether1 ] comment=WAN-FTTH
set [ find default-name=ether2 ] comment=WAN-ILL
/interface pppoe-client
add disabled=no interface=ether1 name=WAN-FTTH user=netnam_manipy
/interface wireguard
add listen-port=51248 mtu=1420 name=WG-RouterA
/interface list
add name=LAN
add name=WAN
add name=TRUSTED
/interface wireless security-profiles
set [ find default=yes ] supplicant-identity=MikroTik
/ip pool
add name=dhcp_pool0 ranges=10.0.255.1-10.0.255.253
add name=dhcp_pool1 ranges=10.22.10.10-10.22.10.200
/ip dhcp-server
add address-pool=dhcp_pool0 interface=guest-lan lease-time=1d name=guest-dhcp
add address-pool=dhcp_pool1 interface=py1-lan lease-time=8h name=dhcp1
/port
set 0 name=serial0
set 1 name=serial1
/interface bridge port
add bridge=guest-lan interface=ether8
add bridge=py1-lan interface=ether9
add bridge=py1-lan interface=ether10
add bridge=py1-lan interface=ether11
add bridge=py1-lan interface=ether12
/ip neighbor discovery-settings
set discover-interface-list=TRUSTED
/interface l2tp-server server
set use-ipsec=yes
/interface list member
add interface=WAN-FTTH list=WAN
add interface=ether2 list=WAN
add interface=guest-lan list=LAN
add interface=py1-lan list=LAN
add interface=WG-RouterA list=LAN
add interface=py1-lan list=TRUSTED
add interface=WG-RouterA list=TRUSTED
/interface wireguard peers
add allowed-address=10.22.0.2/32,10.22.20.0/24 interface=WG-RouterA public-key="--" comment="site to site"
add allowed-address=10.22.19.1/32 interface=WG-RouterA name=bh.anh public-key=""
add allowed-address=10.22.19.2/32 interface=WG-RouterA name=hangmmh public-key=""
add allowed-address=10.22.19.3/32 interface=WG-RouterA name=ngocmmh public-key=""
add allowed-address=10.22.19.4/32 interface=WG-RouterA name=damhammh public-key=""
add allowed-address=10.22.19.5/32 interface=WG-RouterA name=hung.bravo public-key=""
add allowed-address=10.22.19.6/32 interface=WG-RouterA name=hoangbravo public-key=""
add allowed-address=10.22.19.7/32 interface=WG-RouterA name=bh.anh2 public-key=""
add allowed-address=10.22.19.8/32 interface=WG-RouterA name=bh.anh3 public-key=""
add allowed-address=10.22.19.9/32 interface=WG-RouterA name=lanbravo public-key=""
add allowed-address=10.22.19.10/32 interface=WG-RouterA name=nm.hung public-key=""
/ip address
add address=202.151.163.46/30 interface=ether2 network=202.151.163.44
add address=10.22.10.254/24 interface=py1-lan network=10.22.10.0
add address=10.0.255.254/24 interface=guest-lan network=10.0.255.0
add address=10.22.0.1/30 interface=WG-RouterA network=10.22.0.0 comment="site to site"
add address=10.22.19.254/24 interface=WG-RouterA network=10.22.19.0 comment="remote users"
/ip cloud
set ddns-enabled=yes
/ip dhcp-server network
add address=10.0.255.0/24 gateway=10.0.255.254
add address=10.22.10.0/24 dns-server=8.8.8.8,8.8.4.4 gateway=10.22.10.254
/ip dns
set servers=8.8.8.8,8.8.4.4
/ip firewall address-list
add address=10.22.10.XX list=AUTHORIZED comment="local admin pc"
add address=10.22.10.YY list=AUTHORIZED comment="local admin device2"
add address=10.22.19.AB list=AUTHORIZED comment="remote wg admin laptop"
add address=10.22.19.CD list=AUTHORIZED comment="remote wg admin smartphone/ipad"
add address=10.22.20.EF list=AUTHORIZED comment="admin local IP at RouterB"
add address=10.22.20.GH list=AUTHORIZED comment="admin local IP at RouterB device 2"
/ip firewall filter
add action=accept chain=input connection-state=established,related,untracked
add action=drop chain=input connection-state=invalid
add action=accept chain=input protocol=icmp
add action=accept chain=input dst-address=127.0.0.1
add action=accept chain=input comment="wireguard handshake" dst-port=51248
add action=accept chain=input comment="admin access" src-address=list=AUTHORIZED
add action=accept chain=input comment="users to services" in-interface-list=LAN dst-port=53,123 protocol=udp
add action=accept chain=input comment="users to services" in-interface-list=LAN dst-port=53 protocol=tcp
add action=drop chain=input comment="Drop all else" { make this rule last }
+++++++++++++++++++++++++++
add action=fasttrack-connection chain=forward connection-state=established,related hw-offload=yes
add action=accept chain=forward connection-state=established,related,untracked
add action=drop chain=forward connection-state=invalid
add action=accept chain=forward comment="internet traffic" in-interface-list=LAN out-interface-list=WAN
add action=accept chain=forward commeint="RB to RA" in-interface=WG-RouterA src-address=10.22.20.0/24 dst-address=10.22.10.0/24
add action=accept chain=forward comment="RA to RB" out-interface=WG-RouterA src-address=10.22.10.0/24 dst-address=10.22.20.0/24
add action=accept chain=forward comment="remote users to RA" in-interface=WG-RouterA src-address=10.22.19.0/24 dst-address=10.22.10.0/24
add action=accept chain=forward comment="relay remote to RB" in-interface=WG-RouterA src-address=10.22.19.0/24 out-interface=WG-RouterA
add action=accept chain=forward comment="admin access" src-address-list=Authorized out-interface-list=LAN
add action=accept chain=forward comment="port forwarding" connection-nat-state=dstnat
add action=drop chain=forward comment="drop all else"
/ip firewall nat
add action=masquerade chain=srcnat out-interface=WAN-FTTH
add action=masquerade chain=srcnat out-interface=ether2
add action=dst-nat chain=dstnat in-interface-list=WAN dst-port=443 protocol=tcp to-addresses=10.22.10.253
/ip route
{ Main routes for backup }
add check-gateway=ping dst-address=0.0.0.0/0 gateway=1.0.0.1 routing-table=main scope=10 target-scope=12
add dst-address=1.0.0.1/32 gateway=WAN1-Gateway-IP routing-table=main scope=10 target-scope=11
++++++++++++++++
add check-gateway=ping distance=2 dst-address=0.0.0.0/0 gateway=WAN2-Gateway-IP routing-table=main
++++++++++++++++
{ to ensure traffic to Router B subnet }
add dst-address=10.22.20.0/24 gateway=WG-RouterA routing-table=main
+++++++++++++++
{ special route for wireguard to wan2 }
add dst-address=ip.of.siteB.wan2/32 gateway=ip.or.siteA.wan2-gw
/ip service
set telnet disabled=yes
set ftp disabled=yes
set www disabled=yes
set ssh disabled=yes
set api disabled=yes
set api-ssl disabled=yes
/lcd
set time-interval=daily
/system clock
set time-zone-name=Asia/Ho_Chi_Minh
/system identity
set name=PY1-router-mikrotik
/system note
set show-at-login=no
/system ntp client
set enabled=yes
/system ntp client servers
add address=vn.pool.ntp.org
/tool mac-server
set allowed-interface-list=none
/tool mac-server mac-winbox
set allowed-interface-list=TRUSTED
/tool e-mail
set from=1@gmail.com port=465 server=smtp.gmail.com tls=yes user=\
1@gmail.comMissing pool for main lan???
Missing interface list entries???
Site B:
...............
Code: Select all
# 2024-12-22 07:29:16 by RouterOS 7.16.2
# software id = 2M0R-ULGQ
#
# model = CCR2004-16G-2S+
# serial number =
/interface bridge
add name=guest-lan
add name=py2-lan
/interface ethernet
set [ find default-name=ether1 ] comment=WAN-FTTH
set [ find default-name=ether2 ] comment=WAN-ILL
/interface pppoe-client
add disabled=no interface=ether1 name=netnam-ftth user=netnam_manitn2
/interface wireguard
add listen-port=35359 mtu=1420 name=WG-RouterB
/interface list
add name=LAN
add name=WAN
add name=TRUSTED
/ip pool
add name=dhcp_pool0 ranges=10.255.255.1-10.255.255.250
add name=dhcp_pool2 ranges=10.22.20.1-10.22.20.250
/ip dhcp-server
add address-pool=dhcp_pool0 interface=guest-lan lease-time=8h name=dhcp1
add address-pool=dhcp_pool2 interface=py2-lan lease-time=8h name=dhcp2
/port
set 0 name=serial0
set 1 name=serial1
/interface bridge port
add bridge=py2-lan interface=ether16
add bridge=py2-lan interface=ether15
add bridge=py2-lan interface=ether14
add bridge=py2-lan interface=ether13
add bridge=guest-lan interface=ether12
/ip neighbor discovery-settings
set discover-interface-list=TRUSTED
/interface list member
add interface=netnam-ftth list=WAN
add interface=ether2 list=WAN
add interface=guest-lan list=LAN
add interface=py2-lan list=LAN
add interface=py2-lan list=TRUSTED
add interface=WG-RouterB list=TRUSTED
/interface wireguard peers
add allowed-address=10.22.0.1/32, 10.22.19.0/24,10.22.10.0/24 endpoint-address=SiteB-WAN2-IP \
endpoint-port=51248 interface=WG-RouterB persistent-keep-alive=25s public-key="----"
/ip address
add address=10.22.20.254/24 interface=py2-lan network=10.22.20.0
add address=10.255.255.254/24 interface=guest-lan network=10.255.255.0
add address=101.96.76.126/30 interface=ether2 network=101.96.76.124
add address=10.22.0.2/30 interface=WG-RouterB network=10.22.0.0
/ip cloud
set ddns-enabled=yes
/ip dhcp-server network
add address=10.255.255.0/24 dns-server=8.8.8.8,8.8.4.4 gateway=10.255.255.254
add address=10.22.20.0/24 dns-server=8.8.8.8,8.8.4.4 gateway=10.22.20.254
/ip dns
set servers=8.8.8.8,8.8.4.4
/ip firewall address-list
add address=10.22.10.XX list=AUTHORIZED comment="admin local IP at RouterA"
add address=10.22.10.YY list=AUTHORIZED comment="admin local IP at RouterA device2"
add address=10.22.19.AB list=AUTHORIZED comment="remote wg admin laptop"
add address=10.22.19.CD list=AUTHORIZED comment="remote wg admin smartphone/ipad"
add address=10.22.20.EF list=AUTHORIZED comment="local admin IP"
add address=10.22.20.GH list=AUTHORIZED comment="local admin IP device 2"
/ip firewall filter
add action=accept chain=input connection-state=established,related,untracked
add action=drop chain=input connection-state=invalid
add action=accept chain=input protocol=icmp
add action=accept chain=input dst-address=127.0.0.1
add action=accept chain=input comment="admin access" src-address=list=AUTHORIZED
add action=accept chain=input comment="users to services" in-interface-list=LAN dst-port=53,123 protocol=udp
add action=accept chain=input comment="users to services" in-interface-list=LAN dst-port=53 protocol=tcp
add action=drop chain=input comment="Drop all else" make this rule last
+++++++++++++++++++++++++++
add action=fasttrack-connection chain=forward connection-state=established,related hw-offload=yes
add action=accept chain=forward connection-state=established,related,untracked
add action=drop chain=forward connection-state=invalid
add action=accept chain=forward comment="internet traffic" in-interface-list=LAN out-interface-list=WAN
add action=accept chain=forward commeint="RA to RB" in-interface=WG-RouterB src-address=10.22.10.0/24 dst-address=10.22.20.0/24
add action=accept chain=forward comment="RB to RB" out-interface=WG-RouterB src-address=10.22.20.0/24 dst-address=10.22.10.0/24
add action=accept chain=forward comment="remote users to RB" in-interface=WG-RouterB src-address=10.22.19.0/24 dst-address=10.22.20.0/24
add action=accept chain=forward comment="admin access" src-address-list=AUTHORIZED out-interface-list=LAN
add action=accept chain=forward comment="port forwarding" connection-nat-state=dstnat
add action=drop chain=forward comment="drop all else"
/ip firewall nat
add action=masquerade chain=srcnat out-interface-list=WAN
add action=dst-nat chain=dstnat in-interface-list=WAN dst-port=443 protocol=tcp to-addresses=10.22.20.253
/ip firewall mangle
add action=change-mss chain=forward comment="Clamp MSS to PMTU for Outgoing packets" new-mss=clamp-to-pmtu out-interface=WG-RouterB passthrough=yes protocol=tcp tcp-flags=syn
/ip route
{ Main routes for backup }
add check-gateway=ping dst-address=0.0.0.0/0 gateway=1.1.1.1 routing-table=main scope=10 target-scope=12
add dst-address=1.1.1.1/32 gateway=WAN1-Gateway-IP routing-table=main scope=10 target-scope=11
++++++++++++++++
add check-gateway=ping distance=2 dst-address=0.0.0.0/0 gateway=WAN2-Gateway-IP routing-table=main
++++++++++++++++
{ to ensure traffic to Router A subnet }
add dst-address=10.22.10.0/24 gateway=WG-RouterA routing-table=main
{ to ensure return traffic for remote wg users }
add dst-address=10.22.19.0/24 gateway=WG-RouterB routing-table=main
+++++++++++++++
{ special route for wireguard to wan2 }
add dst-address=ip.of.siteA.wan2/32 gateway=ip.or.siteB.wan2-gw
/ip service
set telnet disabled=yes
set ftp disabled=yes
set www disabled=yes
set ssh disabled=yes
set api disabled=yes
set api-ssl disabled=yes
/system clock
set time-zone-name=Asia/Ho_Chi_Minh
/system identity
set name=PY2-Mikrotik-Router
/system note
set show-at-login=no
/system ntp client
set enabled=yes
/system ntp client servers
add address=vn.pool.ntp.org
/tool mac-server
set allowed-interface-list=none
/tool mac-server mac-winbox
set allowed-interface-list=TRUSTED
/system routerboard settings
set enter-setup-on=delete-key
Last edited by anav on Thu Dec 26, 2024 10:54 pm, edited 1 time in total.
Re: Wireguard VPN on dual WAN
Hello guys,
Thank you for you kindy support,
I just add iproute in 2 router to my current config, re-enable wireguard, and traffic goes on wan2 on 2 site,
Site A:
dst-address=ip.of.siteB.wan2/32 gateway=ip.or.siteA.wan2-gw
Site B:
dst-address=ip.of.siteA.wan2/32 gateway=ip.or.siteB.wan2-gw
According to sindy:
If all you want is that the site-to-site Wireguard between A and B would use WAN 2 at both sites, and if you don't plan on any other traffic among the public addresses of Site A and Site B, just add static routes:
Site A:
dst-address=ip.of.siteB.wan2/32 gateway=ip.or.siteA.wan2-gw
Site B:
dst-address=ip.of.siteA.wan2/32 gateway=ip.or.siteB.wan2-gw
For any more complicated scenario, you'll need policy routing in its full complexity, including special provisions for the specific behavior of Wireguard.
I wonder when wan1 is down, can I access the internet through wan2 ?
Thank you for you kindy support,
I just add iproute in 2 router to my current config, re-enable wireguard, and traffic goes on wan2 on 2 site,
Site A:
dst-address=ip.of.siteB.wan2/32 gateway=ip.or.siteA.wan2-gw
Site B:
dst-address=ip.of.siteA.wan2/32 gateway=ip.or.siteB.wan2-gw
According to sindy:
If all you want is that the site-to-site Wireguard between A and B would use WAN 2 at both sites, and if you don't plan on any other traffic among the public addresses of Site A and Site B, just add static routes:
Site A:
dst-address=ip.of.siteB.wan2/32 gateway=ip.or.siteA.wan2-gw
Site B:
dst-address=ip.of.siteA.wan2/32 gateway=ip.or.siteB.wan2-gw
For any more complicated scenario, you'll need policy routing in its full complexity, including special provisions for the specific behavior of Wireguard.
I wonder when wan1 is down, can I access the internet through wan2 ?
Re: Wireguard VPN on dual WAN
I wonder when wan1 is down, can I access the internet through wan2 ?
Yes. If WAN1 is down, the route with destination 0.0.0.0/0 distance=2 gateway=WAN2-Gateway-IP in the main table will take over.
Re: Wireguard VPN on dual WAN
Thank you for the information, that's all I need now.I wonder when wan1 is down, can I access the internet through wan2 ?
Yes. If WAN1 is down, the route with destination 0.0.0.0/0 distance=2 gateway=WAN2-Gateway-IP in the main table will take over.
Thank you all, again.
Re: Wireguard VPN on dual WAN
Hello guys,
Me again, sorry to bother you,
I have some client connect to 2 site via wireguard but still using wan1, any suggestion to make all wireguard traffic on wan2?
Me again, sorry to bother you,
I have some client connect to 2 site via wireguard but still using wan1, any suggestion to make all wireguard traffic on wan2?
Re: Wireguard VPN on dual WAN
And here we goI have some client connect to 2 site via wireguard but still using wan1, any suggestion to make all wireguard traffic on wan2?
It was simple right until this point. As soon as you want the router to always use WAN2 not just for a single remote address known in advance, regardless what kind of packet it is and if it is a response, via which WAN has the matching request come, you need the complete setup with multiple routing tables, connection marking, and special treatment of Wireguard's special behavior.
So by adding this requirement into the mix, you have embarked the same boat like many other forum members, and there are at least five similar topics here.
For roaming clients that connect from "random" (as in "unknown in advance") addresses, you cannot use dedicated routes in routing table main to make the router send traffic to the addresses of these clients no matter what. You have to assign a connection-mark to each transport Wireguard connection when handling its very first packet, and let the router route the packets it sends itself within these connections via WAN2, by means of "translating" that connection-mark to a routing-mark that tells the routing to use another table, which contains a single default route via the gateway reachable via WAN2. Plus, since it is Wireguard with its special behavior, you must use a dst-nat rule to make the Wireguard process see even packets that have actually arrived to the IP address of WAN2 as if they arrived to the IP address of WAN1. The background is that Wireguard, unlike normal services, does not respond from the same IP address to which the request being responded has arrived, but sends the response as an independent packet, so it uses routing table main, which tells it to send it via the gateway reachable through WAN1 and thus use the IP address of WAN1 as the source one of the packet. In the next step, a mangle rule in chain output tells the router to actually use the alternative routing table, so the packet gets routed again but its source address remains unchanged. And in the next step, the connection tracking finds out that the packet belongs to a known connection and "un-dst-nats" it, i.e. it replaces its current source address (WAN1) by the one to which the matching request has initially arrived - WAN2. If it wasn't for that, the response would still be routed via WAN 2, but it would bear a source address belonging to WAN 1, so if the WAN 2 ISP would not filter it out, the remote Wireguard peer would switch to talking to that IP and therefore via WAN 1 (in your case, even on both ends).
If you want a list of commands to apply to implement the above, post the current export of the configuration of the router that should be modified this way first.
Re: Wireguard VPN on dual WAN
Sound likes complicated, @anav said that is a bug with wireguard on secondary WAN, I wonder when does it fixed? The current config I will give you tomorrow.
Re: Wireguard VPN on dual WAN
I am afraid it is an intentional behavior, not a bug. Wireguard is written that way for a reason (to allow connections to adapt to address changes at both peers) and trying to "fix" it would break other things. Also, it would further increase the workload of Mikrotik developers if they had to maintain their own fork of the Wireguard code.@anav said that is a bug with wireguard on secondary WAN, I wonder when does it fixed?
However, it does not really matter what I or @anav say, as neither of us is a Mikrotik developer or even Jason A. Donenfeld. So what we say regarding this are just assumptions.
Re: Wireguard VPN on dual WAN
Perhaps a bit more clarity can help avoid getting complex.
What I understand.
a. you have RouterA server peer for handshake and its lan users can access lan of router B.
b. you have RouterB client peer for handshake and its lan users can access lan of router A.
c. you have remote wireguard users that can access both LANs
d. you have an authorized firewall admin address list consisting of local and remote router IPs and wireguard IPs that can access the routers and LANs.
Please explain this new requirement.
Currently remote wireguard users connect to WAN2 of RouterA. that is the endpoint they are given.
What is new ???
What I understand.
a. you have RouterA server peer for handshake and its lan users can access lan of router B.
b. you have RouterB client peer for handshake and its lan users can access lan of router A.
c. you have remote wireguard users that can access both LANs
d. you have an authorized firewall admin address list consisting of local and remote router IPs and wireguard IPs that can access the routers and LANs.
Please explain this new requirement.
Currently remote wireguard users connect to WAN2 of RouterA. that is the endpoint they are given.
What is new ???
Re: Wireguard VPN on dual WAN
What is new is that now there are other Wireguard peers than just "the other router" for at least one of the routers, and these are the generic roaming ones that may drift from one address to another.
Re: Wireguard VPN on dual WAN
Here is my 2 factory's network diagram:
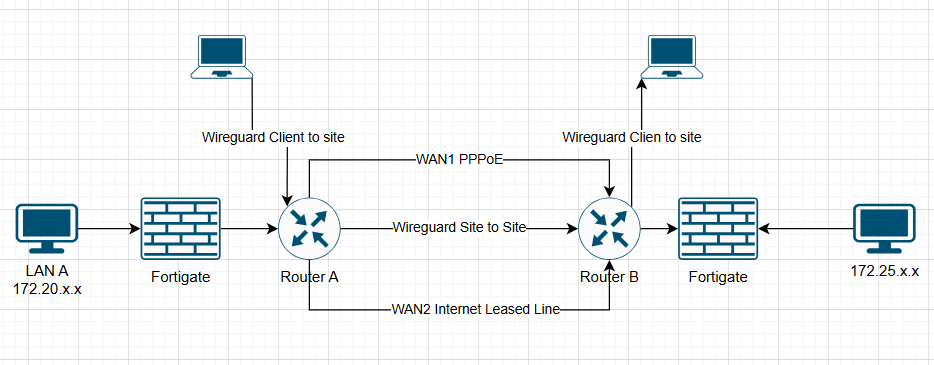
Currently, I have configured remote access on each router, no need to access other one's network.
Wireguard site to site between 2 factory is now using WAN2.
Wireguard client to site VPN still using WAN1, how can I make these connection usng WAN2.
Another issue, I cannot connect to WAN2 by winbox on both Router.
I make WAN2 primary but still not work, while WAN1 still accessible, I think it's cause maybe by ISP's Security.
Current config after following anav's advice:
Router A:
# 2024-12-23 21:51:14 by RouterOS 7.16.2
# software id = 9931-M8FK
#
# model = CCR1016-12G
/interface bridge
add name=guest-lan
add name=py1-lan
/interface ethernet
set [ find default-name=ether1 ] comment=WAN-FTTH
set [ find default-name=ether2 ] comment=WAN-ILL
/interface pppoe-client
add disabled=no interface=ether1 name=WAN-FTTH user=netnam_manipy
/interface wireguard
add listen-port=51248 mtu=1420 name=PY1-Wireguard
/interface list
add name=LAN
add name=WAN
/interface wireless security-profiles
set [ find default=yes ] supplicant-identity=MikroTik
/ip pool
add name=dhcp_pool0 ranges=10.0.255.1-10.0.255.253
add name=dhcp_pool1 ranges=10.22.10.10-10.22.10.200
/ip dhcp-server
add address-pool=dhcp_pool0 interface=guest-lan lease-time=1d name=guest-dhcp
add address-pool=dhcp_pool1 interface=py1-lan lease-time=8h name=dhcp1
/port
set 0 name=serial0
set 1 name=serial1
/routing table
add disabled=no fib name=FTTH-table
add disabled=no fib name=ILL-table
/interface bridge port
add bridge=py1-lan interface=ether11
add bridge=py1-lan interface=ether12
add bridge=guest-lan interface=ether8
add bridge=py1-lan interface=ether9
add bridge=py1-lan interface=ether10
/ip neighbor discovery-settings
set discover-interface-list=!dynamic
/interface l2tp-server server
set use-ipsec=yes
/interface list member
add interface=guest-lan list=LAN
add interface=py1-lan list=LAN
add interface=WAN-FTTH list=WAN
add interface=ether2 list=WAN
/interface wireguard peers
add allowed-address=172.25.0.0/16 endpoint-address=RouterB-WAN2-IP \
endpoint-port=51248 interface=PY1-Wireguard name=vpn-to-PY2 public-key=\
"1"
add allowed-address=10.22.0.2/32 interface=PY1-Wireguard name=hangmmh \
public-key="1"
add allowed-address=10.22.0.1/32 interface=PY1-Wireguard name=bh.anh \
public-key="1"
add allowed-address=10.22.0.3/32 interface=PY1-Wireguard name=ngocmmh \
public-key="1"
add allowed-address=10.22.0.4/32 interface=PY1-Wireguard name=damhammh \
public-key="1"
add allowed-address=10.22.0.5/32 interface=PY1-Wireguard name=hung.bravo \
public-key="1"
add allowed-address=10.22.0.6/32 interface=PY1-Wireguard name=hoangbravo \
public-key="1"
add allowed-address=10.22.0.7/32 interface=PY1-Wireguard name=bh.anh2 \
public-key="1"
add allowed-address=10.22.0.8/32 interface=PY1-Wireguard name=bh.anh3 \
public-key="1"
add allowed-address=10.22.0.9/32 interface=PY1-Wireguard name=lanbravo \
public-key="1"
add allowed-address=10.22.0.10/32 interface=PY1-Wireguard name=nm.hung \
public-key="1"
/ip address
add address=10.22.10.254/24 interface=py1-lan network=10.22.10.0
add address=10.0.255.254/24 interface=guest-lan network=10.0.255.0
add address=WAN2-IP interface=ether2 network=WAN2-DG-IP
add address=10.22.0.254/24 interface=PY1-Wireguard network=10.22.0.0
/ip cloud
set ddns-enabled=yes
/ip dhcp-server network
add address=10.0.255.0/24 gateway=10.0.255.254
add address=10.22.10.0/24 dns-server=8.8.8.8,8.8.4.4 gateway=10.22.10.254
/ip dns
set servers=8.8.8.8,8.8.4.4
/ip firewall address-list
add address=172.20.0.0/16 list=LAN
add address=10.0.255.0/24 list=LAN
add address=10.22.10.0/24 list=LAN
add address=thuedientu.gdt.gov.vn list=traffic-via-ILL
add address=172.25.0.0/16 list=VPN
add address=tracuunnt.gdt.gov.vn list=traffic-via-ILL
add address=vieclamthainguyen.gov.vn list=traffic-via-ILL
add address=dichvucong.thainguyen.gov.vn list=traffic-via-ILL
add address=hoadondientu.gdt.gov.vn list=traffic-via-ILL
add address=www.gdt.gov.vn list=traffic-via-ILL
add address=thainguyen.gov.vn list=traffic-via-ILL
add address=canhan.gdt.gov.vn list=traffic-via-ILL
add address=kcn.thainguyen.gov.vn list=traffic-via-ILL
add address=10.22.0.0/24 list=VPN
add address=speedtest.vn list=traffic-via-ILL
add address=smartone.vps.com.vn list=traffic-via-ILL
/ip firewall filter
add action=accept chain=input dst-port=51248 in-interface-list=WAN protocol=\
udp
/ip firewall mangle
add action=mark-routing chain=prerouting dst-address-list=traffic-via-ILL \
dst-address-type=!local new-routing-mark=ILL-table passthrough=yes \
src-address-list=LAN
/ip firewall nat
add action=dst-nat chain=dstnat dst-port=443 in-interface-list=WAN protocol=\
tcp to-addresses=10.22.10.253 to-ports=443
add action=masquerade chain=srcnat out-interface-list=WAN
/ip ipsec profile
set [ find default=yes ] dpd-interval=2m dpd-maximum-failures=5
/ip route
add disabled=no distance=1 dst-address=172.20.0.0/16 gateway=10.22.10.253 \ *To RouterA's Factory LAN*
routing-table=main scope=30 suppress-hw-offload=no target-scope=10
add disabled=no distance=1 dst-address=172.25.0.0/16 gateway=PY1-Wireguard \ *To RouterB's Factory LAN*
routing-table=main scope=30 suppress-hw-offload=no target-scope=10
add disabled=no distance=1 dst-address=10.22.20.0/24 gateway=10.22.0.253 \
routing-table=main scope=30 suppress-hw-offload=no target-scope=10
add check-gateway=ping disabled=no distance=4 dst-address=0.0.0.0/0 gateway=\
WAN2-DG-IP routing-table=main scope=30 suppress-hw-offload=no \
target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=\
WAN2-IP routing-table=ILL-table scope=30 suppress-hw-offload=no \
target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=\
WAN1-DG-IP routing-table=FTTH-table scope=30 suppress-hw-offload=no \
target-scope=10
add check-gateway=ping disabled=no distance=2 dst-address=0.0.0.0/0 gateway=\
8.8.8.8 routing-table=main scope=10 suppress-hw-offload=no target-scope=\
12
add check-gateway=ping disabled=no distance=2 dst-address=8.8.8.8/32 gateway=\
WAN1-DG-IP routing-table=main scope=10 suppress-hw-offload=no \
target-scope=11
add comment=vpn-to-py2 disabled=no distance=1 dst-address=RouterB-WAN2-IP \
gateway=RouterA-WAN2-DG-IP routing-table=main scope=30 suppress-hw-offload=no \
target-scope=10
/ip service
set telnet disabled=yes
set ftp disabled=yes
set www disabled=yes
set ssh disabled=yes
set api disabled=yes
set api-ssl disabled=yes
/lcd
set time-interval=daily
/system clock
set time-zone-name=Asia/Ho_Chi_Minh
/system identity
set name=PY1-router-mikrotik
/system note
set show-at-login=no
/system ntp client
set enabled=yes
/system ntp client servers
add address=vn.pool.ntp.org
/tool e-mail
set from="" server=smtp.gmail.com tls=yes
Router B:
# 2024-12-23 21:53:09 by RouterOS 7.16.2
# software id = 2M0R-ULGQ
#
# model = CCR2004-16G-2S+
/interface bridge
add name=guest-lan
add name=py2-lan
/interface ethernet
set [ find default-name=ether1 ] comment=WAN-FTTH
set [ find default-name=ether2 ] comment=WAN-ILL
/interface pppoe-client
add disabled=no interface=ether1 name=netnam-ftth user=netnam_manitn2
/interface wireguard
add listen-port=51248 mtu=1420 name=PY2-Wireguard
/interface list
add name=LAN
add name=WAN
/ip pool
add name=dhcp_pool0 ranges=10.255.255.1-10.255.255.250
/ip dhcp-server
add address-pool=dhcp_pool0 interface=guest-lan lease-time=8h name=dhcp1
/port
set 0 name=serial0
set 1 name=serial1
/routing table
add disabled=no fib name=FTTH-table
add disabled=no fib name=ILL-table
/interface bridge port
add bridge=py2-lan interface=ether16
add bridge=py2-lan interface=ether15
add bridge=py2-lan interface=ether14
add bridge=py2-lan interface=ether13
add bridge=guest-lan interface=ether12
/ip neighbor discovery-settings
set discover-interface-list=!dynamic
/interface list member
add interface=guest-lan list=LAN
add interface=py2-lan list=LAN
add interface=netnam-ftth list=WAN
add interface=ether2 list=WAN
/interface wireguard peers
add allowed-address=172.20.0.0/16 endpoint-address=RouterA-WAN2-IP \
endpoint-port=51248 interface=PY2-Wireguard name=vpn-to-PY1 \
persistent-keepalive=25s public-key=\
"1"
add allowed-address=10.22.29.1/24 interface=PY2-Wireguard name=bh.anh \
public-key="1"
/ip address
add address=10.22.20.254/24 interface=py2-lan network=10.22.20.0 *RouterB's LAN*
add address=10.255.255.254/24 interface=guest-lan network=10.255.255.0 *Guest LAN*
add address=WAN2-IP interface=ether2 network=WAN2-DG-IP *WAN2*
add address=10.22.0.253/24 interface=PY2-Wireguard network=10.22.0.0 *PY2-Wireguard*
/ip cloud
set ddns-enabled=yes
/ip dhcp-server network
add address=10.255.255.0/24 dns-server=8.8.8.8,8.8.4.4 gateway=10.255.255.254
/ip dns
set servers=8.8.8.8,8.8.4.4
/ip firewall address-list
add address=172.25.0.0/16 list=LAN
add address=10.255.255.0/24 list=LAN
add address=10.22.20.0/24 list=LAN
add address=10.22.29.0/24 list=VPN
add address=172.20.0.0/16 list=VPN
/ip firewall filter
add action=accept chain=input dst-port=51248 in-interface-list=WAN protocol=\
udp
/ip firewall nat
add action=dst-nat chain=dstnat dst-port=443 in-interface-list=WAN protocol=\
tcp to-addresses=10.22.20.253 to-ports=443
add action=masquerade chain=srcnat out-interface-list=WAN to-addresses=\
14.241.82.232
/ip ipsec profile
set [ find default=yes ] dpd-interval=2m dpd-maximum-failures=5
/ip route
add check-gateway=ping disabled=no distance=4 dst-address=0.0.0.0/0 gateway=\
WAN2-DG-IP routing-table=main scope=30 suppress-hw-offload=no \
target-scope=10
add disabled=no distance=4 dst-address=10.22.10.0/24 gateway=10.22.0.254 \
routing-table=main scope=30 suppress-hw-offload=no target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=\
WAN1-DG-IP routing-table=FTTH-table scope=30 suppress-hw-offload=no \
target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=\
WAN2-DG-IP routing-table=ILL-table scope=30 suppress-hw-offload=no \
target-scope=10
add check-gateway=ping disabled=no distance=2 dst-address=0.0.0.0/0 gateway=\
8.8.8.8 routing-table=main scope=10 suppress-hw-offload=no target-scope=\
12
add disabled=no distance=1 dst-address=172.20.0.0/16 gateway=PY2-Wireguard \ *To RouterA's Facotry LAN*
routing-table=main scope=30 suppress-hw-offload=no target-scope=10
add disabled=no dst-address=172.25.0.0/16 gateway=10.22.20.253 routing-table=\ *To RouterB's Factory LAN*
main suppress-hw-offload=no
add check-gateway=ping disabled=no distance=2 dst-address=8.8.8.8/32 gateway=\
WAN1-DG-IP routing-table=main scope=10 suppress-hw-offload=no \
target-scope=11
add comment=vpn-to-py1 disabled=no distance=1 dst-address=RouterA-WAN2-IP \
gateway=WAN2-DG-IP routing-table=main scope=30 suppress-hw-offload=no \
target-scope=10
/ip service
set telnet disabled=yes
set ftp disabled=yes
set www disabled=yes
set ssh disabled=yes
set api disabled=yes
set api-ssl disabled=yes
/system clock
set time-zone-name=Asia/Ho_Chi_Minh
/system identity
set name=PY2-Mikrotik-Router
/system note
set show-at-login=no
/system ntp client
set enabled=yes
/system ntp client servers
add address=vn.pool.ntp.org
/system routerboard settings
set enter-setup-on=delete-key

Currently, I have configured remote access on each router, no need to access other one's network.
Wireguard site to site between 2 factory is now using WAN2.
Wireguard client to site VPN still using WAN1, how can I make these connection usng WAN2.
Another issue, I cannot connect to WAN2 by winbox on both Router.
I make WAN2 primary but still not work, while WAN1 still accessible, I think it's cause maybe by ISP's Security.
Current config after following anav's advice:
Router A:
# 2024-12-23 21:51:14 by RouterOS 7.16.2
# software id = 9931-M8FK
#
# model = CCR1016-12G
/interface bridge
add name=guest-lan
add name=py1-lan
/interface ethernet
set [ find default-name=ether1 ] comment=WAN-FTTH
set [ find default-name=ether2 ] comment=WAN-ILL
/interface pppoe-client
add disabled=no interface=ether1 name=WAN-FTTH user=netnam_manipy
/interface wireguard
add listen-port=51248 mtu=1420 name=PY1-Wireguard
/interface list
add name=LAN
add name=WAN
/interface wireless security-profiles
set [ find default=yes ] supplicant-identity=MikroTik
/ip pool
add name=dhcp_pool0 ranges=10.0.255.1-10.0.255.253
add name=dhcp_pool1 ranges=10.22.10.10-10.22.10.200
/ip dhcp-server
add address-pool=dhcp_pool0 interface=guest-lan lease-time=1d name=guest-dhcp
add address-pool=dhcp_pool1 interface=py1-lan lease-time=8h name=dhcp1
/port
set 0 name=serial0
set 1 name=serial1
/routing table
add disabled=no fib name=FTTH-table
add disabled=no fib name=ILL-table
/interface bridge port
add bridge=py1-lan interface=ether11
add bridge=py1-lan interface=ether12
add bridge=guest-lan interface=ether8
add bridge=py1-lan interface=ether9
add bridge=py1-lan interface=ether10
/ip neighbor discovery-settings
set discover-interface-list=!dynamic
/interface l2tp-server server
set use-ipsec=yes
/interface list member
add interface=guest-lan list=LAN
add interface=py1-lan list=LAN
add interface=WAN-FTTH list=WAN
add interface=ether2 list=WAN
/interface wireguard peers
add allowed-address=172.25.0.0/16 endpoint-address=RouterB-WAN2-IP \
endpoint-port=51248 interface=PY1-Wireguard name=vpn-to-PY2 public-key=\
"1"
add allowed-address=10.22.0.2/32 interface=PY1-Wireguard name=hangmmh \
public-key="1"
add allowed-address=10.22.0.1/32 interface=PY1-Wireguard name=bh.anh \
public-key="1"
add allowed-address=10.22.0.3/32 interface=PY1-Wireguard name=ngocmmh \
public-key="1"
add allowed-address=10.22.0.4/32 interface=PY1-Wireguard name=damhammh \
public-key="1"
add allowed-address=10.22.0.5/32 interface=PY1-Wireguard name=hung.bravo \
public-key="1"
add allowed-address=10.22.0.6/32 interface=PY1-Wireguard name=hoangbravo \
public-key="1"
add allowed-address=10.22.0.7/32 interface=PY1-Wireguard name=bh.anh2 \
public-key="1"
add allowed-address=10.22.0.8/32 interface=PY1-Wireguard name=bh.anh3 \
public-key="1"
add allowed-address=10.22.0.9/32 interface=PY1-Wireguard name=lanbravo \
public-key="1"
add allowed-address=10.22.0.10/32 interface=PY1-Wireguard name=nm.hung \
public-key="1"
/ip address
add address=10.22.10.254/24 interface=py1-lan network=10.22.10.0
add address=10.0.255.254/24 interface=guest-lan network=10.0.255.0
add address=WAN2-IP interface=ether2 network=WAN2-DG-IP
add address=10.22.0.254/24 interface=PY1-Wireguard network=10.22.0.0
/ip cloud
set ddns-enabled=yes
/ip dhcp-server network
add address=10.0.255.0/24 gateway=10.0.255.254
add address=10.22.10.0/24 dns-server=8.8.8.8,8.8.4.4 gateway=10.22.10.254
/ip dns
set servers=8.8.8.8,8.8.4.4
/ip firewall address-list
add address=172.20.0.0/16 list=LAN
add address=10.0.255.0/24 list=LAN
add address=10.22.10.0/24 list=LAN
add address=thuedientu.gdt.gov.vn list=traffic-via-ILL
add address=172.25.0.0/16 list=VPN
add address=tracuunnt.gdt.gov.vn list=traffic-via-ILL
add address=vieclamthainguyen.gov.vn list=traffic-via-ILL
add address=dichvucong.thainguyen.gov.vn list=traffic-via-ILL
add address=hoadondientu.gdt.gov.vn list=traffic-via-ILL
add address=www.gdt.gov.vn list=traffic-via-ILL
add address=thainguyen.gov.vn list=traffic-via-ILL
add address=canhan.gdt.gov.vn list=traffic-via-ILL
add address=kcn.thainguyen.gov.vn list=traffic-via-ILL
add address=10.22.0.0/24 list=VPN
add address=speedtest.vn list=traffic-via-ILL
add address=smartone.vps.com.vn list=traffic-via-ILL
/ip firewall filter
add action=accept chain=input dst-port=51248 in-interface-list=WAN protocol=\
udp
/ip firewall mangle
add action=mark-routing chain=prerouting dst-address-list=traffic-via-ILL \
dst-address-type=!local new-routing-mark=ILL-table passthrough=yes \
src-address-list=LAN
/ip firewall nat
add action=dst-nat chain=dstnat dst-port=443 in-interface-list=WAN protocol=\
tcp to-addresses=10.22.10.253 to-ports=443
add action=masquerade chain=srcnat out-interface-list=WAN
/ip ipsec profile
set [ find default=yes ] dpd-interval=2m dpd-maximum-failures=5
/ip route
add disabled=no distance=1 dst-address=172.20.0.0/16 gateway=10.22.10.253 \ *To RouterA's Factory LAN*
routing-table=main scope=30 suppress-hw-offload=no target-scope=10
add disabled=no distance=1 dst-address=172.25.0.0/16 gateway=PY1-Wireguard \ *To RouterB's Factory LAN*
routing-table=main scope=30 suppress-hw-offload=no target-scope=10
add disabled=no distance=1 dst-address=10.22.20.0/24 gateway=10.22.0.253 \
routing-table=main scope=30 suppress-hw-offload=no target-scope=10
add check-gateway=ping disabled=no distance=4 dst-address=0.0.0.0/0 gateway=\
WAN2-DG-IP routing-table=main scope=30 suppress-hw-offload=no \
target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=\
WAN2-IP routing-table=ILL-table scope=30 suppress-hw-offload=no \
target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=\
WAN1-DG-IP routing-table=FTTH-table scope=30 suppress-hw-offload=no \
target-scope=10
add check-gateway=ping disabled=no distance=2 dst-address=0.0.0.0/0 gateway=\
8.8.8.8 routing-table=main scope=10 suppress-hw-offload=no target-scope=\
12
add check-gateway=ping disabled=no distance=2 dst-address=8.8.8.8/32 gateway=\
WAN1-DG-IP routing-table=main scope=10 suppress-hw-offload=no \
target-scope=11
add comment=vpn-to-py2 disabled=no distance=1 dst-address=RouterB-WAN2-IP \
gateway=RouterA-WAN2-DG-IP routing-table=main scope=30 suppress-hw-offload=no \
target-scope=10
/ip service
set telnet disabled=yes
set ftp disabled=yes
set www disabled=yes
set ssh disabled=yes
set api disabled=yes
set api-ssl disabled=yes
/lcd
set time-interval=daily
/system clock
set time-zone-name=Asia/Ho_Chi_Minh
/system identity
set name=PY1-router-mikrotik
/system note
set show-at-login=no
/system ntp client
set enabled=yes
/system ntp client servers
add address=vn.pool.ntp.org
/tool e-mail
set from="" server=smtp.gmail.com tls=yes
Router B:
# 2024-12-23 21:53:09 by RouterOS 7.16.2
# software id = 2M0R-ULGQ
#
# model = CCR2004-16G-2S+
/interface bridge
add name=guest-lan
add name=py2-lan
/interface ethernet
set [ find default-name=ether1 ] comment=WAN-FTTH
set [ find default-name=ether2 ] comment=WAN-ILL
/interface pppoe-client
add disabled=no interface=ether1 name=netnam-ftth user=netnam_manitn2
/interface wireguard
add listen-port=51248 mtu=1420 name=PY2-Wireguard
/interface list
add name=LAN
add name=WAN
/ip pool
add name=dhcp_pool0 ranges=10.255.255.1-10.255.255.250
/ip dhcp-server
add address-pool=dhcp_pool0 interface=guest-lan lease-time=8h name=dhcp1
/port
set 0 name=serial0
set 1 name=serial1
/routing table
add disabled=no fib name=FTTH-table
add disabled=no fib name=ILL-table
/interface bridge port
add bridge=py2-lan interface=ether16
add bridge=py2-lan interface=ether15
add bridge=py2-lan interface=ether14
add bridge=py2-lan interface=ether13
add bridge=guest-lan interface=ether12
/ip neighbor discovery-settings
set discover-interface-list=!dynamic
/interface list member
add interface=guest-lan list=LAN
add interface=py2-lan list=LAN
add interface=netnam-ftth list=WAN
add interface=ether2 list=WAN
/interface wireguard peers
add allowed-address=172.20.0.0/16 endpoint-address=RouterA-WAN2-IP \
endpoint-port=51248 interface=PY2-Wireguard name=vpn-to-PY1 \
persistent-keepalive=25s public-key=\
"1"
add allowed-address=10.22.29.1/24 interface=PY2-Wireguard name=bh.anh \
public-key="1"
/ip address
add address=10.22.20.254/24 interface=py2-lan network=10.22.20.0 *RouterB's LAN*
add address=10.255.255.254/24 interface=guest-lan network=10.255.255.0 *Guest LAN*
add address=WAN2-IP interface=ether2 network=WAN2-DG-IP *WAN2*
add address=10.22.0.253/24 interface=PY2-Wireguard network=10.22.0.0 *PY2-Wireguard*
/ip cloud
set ddns-enabled=yes
/ip dhcp-server network
add address=10.255.255.0/24 dns-server=8.8.8.8,8.8.4.4 gateway=10.255.255.254
/ip dns
set servers=8.8.8.8,8.8.4.4
/ip firewall address-list
add address=172.25.0.0/16 list=LAN
add address=10.255.255.0/24 list=LAN
add address=10.22.20.0/24 list=LAN
add address=10.22.29.0/24 list=VPN
add address=172.20.0.0/16 list=VPN
/ip firewall filter
add action=accept chain=input dst-port=51248 in-interface-list=WAN protocol=\
udp
/ip firewall nat
add action=dst-nat chain=dstnat dst-port=443 in-interface-list=WAN protocol=\
tcp to-addresses=10.22.20.253 to-ports=443
add action=masquerade chain=srcnat out-interface-list=WAN to-addresses=\
14.241.82.232
/ip ipsec profile
set [ find default=yes ] dpd-interval=2m dpd-maximum-failures=5
/ip route
add check-gateway=ping disabled=no distance=4 dst-address=0.0.0.0/0 gateway=\
WAN2-DG-IP routing-table=main scope=30 suppress-hw-offload=no \
target-scope=10
add disabled=no distance=4 dst-address=10.22.10.0/24 gateway=10.22.0.254 \
routing-table=main scope=30 suppress-hw-offload=no target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=\
WAN1-DG-IP routing-table=FTTH-table scope=30 suppress-hw-offload=no \
target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=\
WAN2-DG-IP routing-table=ILL-table scope=30 suppress-hw-offload=no \
target-scope=10
add check-gateway=ping disabled=no distance=2 dst-address=0.0.0.0/0 gateway=\
8.8.8.8 routing-table=main scope=10 suppress-hw-offload=no target-scope=\
12
add disabled=no distance=1 dst-address=172.20.0.0/16 gateway=PY2-Wireguard \ *To RouterA's Facotry LAN*
routing-table=main scope=30 suppress-hw-offload=no target-scope=10
add disabled=no dst-address=172.25.0.0/16 gateway=10.22.20.253 routing-table=\ *To RouterB's Factory LAN*
main suppress-hw-offload=no
add check-gateway=ping disabled=no distance=2 dst-address=8.8.8.8/32 gateway=\
WAN1-DG-IP routing-table=main scope=10 suppress-hw-offload=no \
target-scope=11
add comment=vpn-to-py1 disabled=no distance=1 dst-address=RouterA-WAN2-IP \
gateway=WAN2-DG-IP routing-table=main scope=30 suppress-hw-offload=no \
target-scope=10
/ip service
set telnet disabled=yes
set ftp disabled=yes
set www disabled=yes
set ssh disabled=yes
set api disabled=yes
set api-ssl disabled=yes
/system clock
set time-zone-name=Asia/Ho_Chi_Minh
/system identity
set name=PY2-Mikrotik-Router
/system note
set show-at-login=no
/system ntp client
set enabled=yes
/system ntp client servers
add address=vn.pool.ntp.org
/system routerboard settings
set enter-setup-on=delete-key
Re: Wireguard VPN on dual WAN
You should have been clear from the start.
Firstly, to keep things simple, just connect to WAN 2 for all wireguard clients.
There is no need to connect to WAN1 for anybody.
So now we know that there is no LAN to LAN connectivity at all between the subnets on both routers correct??
So basically the setup I gave you still works. We just remove the allow wireguard LAN to LAN rules in both forward chain firewall rules.
Both router are easily accessed by the remote users. Since SiteA is acting as server, what happens is all users till connect to RouterA for wiregaurd
and then get relayed to router B. Its all setup to do that, so you should have no issues accessing either routers LANs or router itself for config purposes.
I have provided rules that allow such already!!
IN other words your still good to go for the most part.
Finally, I dont know why you insist on not keeping stuff provided in allowed IPs for the site to site but do insist on installing other subnets that dont exist on either router 170 etc.........
Is that a VPN on a server on the LAN for each router???
The confusing part is any additional VPN.
Can you clarify what you mean. Are there other users coming in to either router via some other type of VPN??
If so, is that what the dst nat to 443 port is being used for, some server you have the LAN??
Assuming that will be coming in on WAN1 on each router?
Assuming you want those users to be able to do what.....
Since I sound vague its because information required in detail has not been provided.
Are you using a VPN server you have behind each LAN??
How are the fortigates connecting to the Mikrotik........... is this a double nat scenario for each MT router??
So the other subnets are LAN subnets behind the fortiner????
Firstly, to keep things simple, just connect to WAN 2 for all wireguard clients.
There is no need to connect to WAN1 for anybody.
So now we know that there is no LAN to LAN connectivity at all between the subnets on both routers correct??
So basically the setup I gave you still works. We just remove the allow wireguard LAN to LAN rules in both forward chain firewall rules.
Both router are easily accessed by the remote users. Since SiteA is acting as server, what happens is all users till connect to RouterA for wiregaurd
and then get relayed to router B. Its all setup to do that, so you should have no issues accessing either routers LANs or router itself for config purposes.
I have provided rules that allow such already!!
IN other words your still good to go for the most part.
Finally, I dont know why you insist on not keeping stuff provided in allowed IPs for the site to site but do insist on installing other subnets that dont exist on either router 170 etc.........
Is that a VPN on a server on the LAN for each router???
The confusing part is any additional VPN.
Can you clarify what you mean. Are there other users coming in to either router via some other type of VPN??
If so, is that what the dst nat to 443 port is being used for, some server you have the LAN??
Assuming that will be coming in on WAN1 on each router?
Assuming you want those users to be able to do what.....
Since I sound vague its because information required in detail has not been provided.
Are you using a VPN server you have behind each LAN??
How are the fortigates connecting to the Mikrotik........... is this a double nat scenario for each MT router??
So the other subnets are LAN subnets behind the fortiner????
Re: Wireguard VPN on dual WAN
Hello anav,
So now we know that there is no LAN to LAN connectivity at all between the subnets on both routers correct??
- Yes, I need to connect LAN subnet behind fortigates on both side: Site A: 172.20.x.x - Site B: 172.25.x.x
Finally, I dont know why you insist on not keeping stuff provided in allowed IPs for the site to site but do insist on installing other subnets that dont exist on either router 170 etc.........
Is that a VPN on a server on the LAN for each router???
- There is no VPN on the server, MT router on both side are the VPN server
Are there other users coming in to either router via some other type of VPN??
- I only using Wireguard VPN for user and site to site connection.
If so, is that what the dst nat to 443 port is being used for, some server you have the LAN??
- I nat 443 port for 2 fortigate's remote management.
Assuming that will be coming in on WAN1 on each router?
Assuming you want those users to be able to do what.....
- Remote user can access LAN behind fortigate: Site A: 172.20.x.x, Site B: 172.25.x.x
Are you using a VPN server you have behind each LAN??
- No, I'm using only 2 MT routers for vpn connection.
How are the fortigates connecting to the Mikrotik........... is this a double nat scenario for each MT router??
- No NAT on 2 fortigates, only NAT on 2 MT routers.
So the other subnets are LAN subnets behind the fortiner????
- Yes, Site A: 172.20.x.x, Site B: 172.25.x.x
So now we know that there is no LAN to LAN connectivity at all between the subnets on both routers correct??
- Yes, I need to connect LAN subnet behind fortigates on both side: Site A: 172.20.x.x - Site B: 172.25.x.x
Finally, I dont know why you insist on not keeping stuff provided in allowed IPs for the site to site but do insist on installing other subnets that dont exist on either router 170 etc.........
Is that a VPN on a server on the LAN for each router???
- There is no VPN on the server, MT router on both side are the VPN server
Are there other users coming in to either router via some other type of VPN??
- I only using Wireguard VPN for user and site to site connection.
If so, is that what the dst nat to 443 port is being used for, some server you have the LAN??
- I nat 443 port for 2 fortigate's remote management.
Assuming that will be coming in on WAN1 on each router?
Assuming you want those users to be able to do what.....
- Remote user can access LAN behind fortigate: Site A: 172.20.x.x, Site B: 172.25.x.x
Are you using a VPN server you have behind each LAN??
- No, I'm using only 2 MT routers for vpn connection.
How are the fortigates connecting to the Mikrotik........... is this a double nat scenario for each MT router??
- No NAT on 2 fortigates, only NAT on 2 MT routers.
So the other subnets are LAN subnets behind the fortiner????
- Yes, Site A: 172.20.x.x, Site B: 172.25.x.x
Re: Wireguard VPN on dual WAN
@haianh, before diving any deeper into the topic of Wireguard on dual WAN, there is a serious security flaw in your configurations - you have got no firewall at all. By design, the default handling of packets in firewall is "accept". So whatever is not explicitly dropped is accepted. When any of the tutorials and videos here and there say "you must add an accept rule to make it work", they assume that at least the default firewall rules that come pre-set in the SOHO product line are in place. In your case, you have added the chain=input protocol=udp dst-port=51248 action=accept rules to /ip firewall filter in order to allow incoming Wireguard traffic, but as there are no other rules in filter, all the incoming traffic that does not match to the rules you have added is accepted anyway due to the default being accept as well. The CCR product line is intended for use by networking professionals mostly in ISP networks where the requirements are site-specific so the default configuration contains no firewall rules, assuming that the administrators will add their own ones before connecting the device to the internet for the first time.
So as you have public IP addresses on your CCRs themselves, the only things that prevent people who would like to also become their administrators from breaking in is the uniquity of your usernames and strength of your passwords on one hand and the security of of the Winbox server on the other one. Leaving Winbox access open to the world has not been considered safe since years ago - in the past, vulnerabilities in Winbox existed and have been exploited, and there may still be more ones, just not widely known and thus not patched yet.
I will continue later regarding the failover routing and the "Wireguard via WAN 2" issue.
So as you have public IP addresses on your CCRs themselves, the only things that prevent people who would like to also become their administrators from breaking in is the uniquity of your usernames and strength of your passwords on one hand and the security of of the Winbox server on the other one. Leaving Winbox access open to the world has not been considered safe since years ago - in the past, vulnerabilities in Winbox existed and have been exploited, and there may still be more ones, just not widely known and thus not patched yet.
I will continue later regarding the failover routing and the "Wireguard via WAN 2" issue.
Re: Wireguard VPN on dual WAN
The next thing to deal with are the recursive next hop search issues. Taking Router B as an example as there is only one roaming Wireguard peer so messing up on that router should causes less people to suffer.
You have configured the following routes in table main that are relevant for the failover (leaving additional routes aside and omitting irrelevant default settings):
(1) check-gateway=ping dst-address=8.8.8.8/32 gateway=WAN1-DG-IP distance=2 scope=10 target-scope=11
(2) check-gateway=ping dst-address=0.0.0.0/0 gateway=8.8.8.8 distance=2 scope=10 target-scope=12
(3) check-gateway=ping dst-address=0.0.0.0/0 gateway=WAN2-DG-IP distance=4 scope=30 target-scope=10
Strictly speaking nothing there affects the operation but some settings indicate copy-pasting without understanding and some things could be better.
You have configured the following routes in table main that are relevant for the failover (leaving additional routes aside and omitting irrelevant default settings):
(1) check-gateway=ping dst-address=8.8.8.8/32 gateway=WAN1-DG-IP distance=2 scope=10 target-scope=11
(2) check-gateway=ping dst-address=0.0.0.0/0 gateway=8.8.8.8 distance=2 scope=10 target-scope=12
(3) check-gateway=ping dst-address=0.0.0.0/0 gateway=WAN2-DG-IP distance=4 scope=30 target-scope=10
Strictly speaking nothing there affects the operation but some settings indicate copy-pasting without understanding and some things could be better.
- check-gateway=ping on route (1) is pointless as it just adds pings to WAN1-DG-IP but if that one is down, the check-gateway=ping configured on route (2) will make route (2) inactive in that case, which is what we actually need.
- check-gateway=ping on route (3) is pointless unless you have yet another backup possibility and/or some means to get a notification that the route is down. Without such a notification, its failure may stay unnoticed until WAN 1 fails too and the traffic stops. In your particular case, you will notice a WAN 2 issue much sooner as the Wireguard site to site tunnel will stop working, but the check-gateway=ping is redundant.
- Since there is only one level of recursion and you don't use recursive next-hop search on WAN 2, only target-scope is relevant on route (2) so scope may stay at the default 30, whereas only scope is relevant on route (1) so target-scope may stay at the default 10. If, however, you were using recursive next-hop search for WAN 2 with another canary address (like e.g. 9.9.9.9) and there was a route similar to (2) with gateway=9.9.9.9/32 and target-scope=12, that hypothetical route would be able to use route (2) recursively because the scope of route (2) is 10, which is not what you want.
Re: Wireguard VPN on dual WAN
Okay so the fortigates are behind the MT routers and they have double NAT on them not the MT devices.
AKA the internet for fortigate is through the MT and you simply want to connect the private LANs behind each fortigate to each other?
Which LAN are the fortigates on at each router, what is their IP address on each router.
AKA the internet for fortigate is through the MT and you simply want to connect the private LANs behind each fortigate to each other?
Which LAN are the fortigates on at each router, what is their IP address on each router.
Re: Wireguard VPN on dual WAN
Regarding making the Wireguard respond via the interface through which the request came in, you following settings on Router B are necessary:
/ip firewall nat
add action=masquerade chain=srcnat out-interface-list=WAN
(this one is already in place, I just reiterate it here because it is essential for the rest to work; also, as far as I am aware, the to-addresses parameter is ignored in case of action=masquerade so I don't get why it even got exported. Also, forgot to obfuscate it so it reveals one of your public addresses, you may want to edit the post.)
/ip route set [find where dst-address=0.0.0.0/0 gateway=WAN2-DG-IP] pref-src=WAN1-IP
This one is necessary for the situation where WAN1 is down so the initial round of routing finds a route via WAN2 - in order that the workaround to Wireguard's specific behavior worked, we have to make sure that the original source address of the Wireguard packets will be the WAN1 one even in this situation.
/ip firewall mangle add chain=prerouting in-interface=ether2 protocol=udp dst-port=51248 dst-address-type=local connection-state=new action=mark-connection new-connection-mark=ILL-cm
This one makes sure that connections created by incoming Wireguard connection attempts that arrive via WAN2 to router's own address will be marked, so that the outgoing packets belonging to these connection would be routed via WAN2.
/ip firewall mangle add chain=output connection-mark=ILL-cm action=mark-routing new-routing-mark=ILL-table
This one tells the router to use the ILL table for the second round of routing of packets belonging to the connections marked with ILL-cm.
/ip firewall nat add connection-mark=ILL-cm action=dst-nat to-addresses=WAN1-IP
This one makes sure that the connection tracking will properly un-dst-nat the packets whose original source address will be WAN1-IP to WAN2-IP.
Such a setup is a slight overkill as compared to your requirements because it allows the roaming Wireguard peers to connect to either WAN1-IP or WAN2-IP. A setup that would only accept incoming Wireguard connections on WAN2-IP would be only a tad simpler - instead of marking the connections and assigning the routing-mark based on connection-mark, it would assign the routing mark based on protocol=udp src-port=51248.
/ip firewall nat
add action=masquerade chain=srcnat out-interface-list=WAN
(this one is already in place, I just reiterate it here because it is essential for the rest to work; also, as far as I am aware, the to-addresses parameter is ignored in case of action=masquerade so I don't get why it even got exported. Also, forgot to obfuscate it so it reveals one of your public addresses, you may want to edit the post.)
/ip route set [find where dst-address=0.0.0.0/0 gateway=WAN2-DG-IP] pref-src=WAN1-IP
This one is necessary for the situation where WAN1 is down so the initial round of routing finds a route via WAN2 - in order that the workaround to Wireguard's specific behavior worked, we have to make sure that the original source address of the Wireguard packets will be the WAN1 one even in this situation.
/ip firewall mangle add chain=prerouting in-interface=ether2 protocol=udp dst-port=51248 dst-address-type=local connection-state=new action=mark-connection new-connection-mark=ILL-cm
This one makes sure that connections created by incoming Wireguard connection attempts that arrive via WAN2 to router's own address will be marked, so that the outgoing packets belonging to these connection would be routed via WAN2.
/ip firewall mangle add chain=output connection-mark=ILL-cm action=mark-routing new-routing-mark=ILL-table
This one tells the router to use the ILL table for the second round of routing of packets belonging to the connections marked with ILL-cm.
/ip firewall nat add connection-mark=ILL-cm action=dst-nat to-addresses=WAN1-IP
This one makes sure that the connection tracking will properly un-dst-nat the packets whose original source address will be WAN1-IP to WAN2-IP.
Such a setup is a slight overkill as compared to your requirements because it allows the roaming Wireguard peers to connect to either WAN1-IP or WAN2-IP. A setup that would only accept incoming Wireguard connections on WAN2-IP would be only a tad simpler - instead of marking the connections and assigning the routing-mark based on connection-mark, it would assign the routing mark based on protocol=udp src-port=51248.
Re: Wireguard VPN on dual WAN
Hi sindy, if winbox is security risk, which option for remote management ?@haianh, before diving any deeper into the topic of Wireguard on dual WAN, there is a serious security flaw in your configurations - you have got no firewall at all. By design, the default handling of packets in firewall is "accept". So whatever is not explicitly dropped is accepted. When any of the tutorials and videos here and there say "you must add an accept rule to make it work", they assume that at least the default firewall rules that come pre-set in the SOHO product line are in place. In your case, you have added the chain=input protocol=udp dst-port=51248 action=accept rules to /ip firewall filter in order to allow incoming Wireguard traffic, but as there are no other rules in filter, all the incoming traffic that does not match to the rules you have added is accepted anyway due to the default being accept as well. The CCR product line is intended for use by networking professionals mostly in ISP networks where the requirements are site-specific so the default configuration contains no firewall rules, assuming that the administrators will add their own ones before connecting the device to the internet for the first time.
So as you have public IP addresses on your CCRs themselves, the only things that prevent people who would like to also become their administrators from breaking in is the uniquity of your usernames and strength of your passwords on one hand and the security of of the Winbox server on the other one. Leaving Winbox access open to the world has not been considered safe since years ago - in the past, vulnerabilities in Winbox existed and have been exploited, and there may still be more ones, just not widely known and thus not patched yet.
I will continue later regarding the failover routing and the "Wireguard via WAN 2" issue.
Beside, the config anav provided before have basic firewall is for block anything else that.
Re: Wireguard VPN on dual WAN
It's not "winbox", it's "any software used for remote management"Hi sindy, if winbox is security risk, which option for remote management ?
The VPN would ideally allow user authentication via RADIUS (e.g. the user-manager add-on package to RouterOS), allowing to use TOTP for a very basic multi-factor authentication. Of course an interactive MFA is better that TOTP but in turn, TOTP is better than just a plain password.
To avoid reading the topic completely after I lost track for a while, I took the last configurations you've posted (along with the network diagram) as the basis, assuming you have already implemented some of @anav's suggestions. In these configurations, all the management services except winbox are disabled and so is the DNS service for external clients (which is definitely a good way to reduce the attack surface), but there is no address list that would restrict access to Winbox to a few public addresses in cooperation with a corresponding set of firewall rules.Beside, the config anav provided before have basic firewall is for block anything else that.
Also, it turns out that my suggestion how to make Wireguard respond via the same WAN through which the connection request has arrived is actually redundant as @anav has already provided his own version of the same. It's just that mine is based on the actual configuration so it may be easier to follow.
Re: Wireguard VPN on dual WAN
Hello Anav,Okay so the fortigates are behind the MT routers and they have double NAT on them not the MT devices.
AKA the internet for fortigate is through the MT and you simply want to connect the private LANs behind each fortigate to each other?
Which LAN are the fortigates on at each router, what is their IP address on each router.
I have disable NAT on Fortigate, I only NAT on MT.
Site A, Fortigates IP: 10.22.10.253/24
Site B, Fortigates IP: 10.22.20.253/24
Re: Wireguard VPN on dual WAN
Still confusing. If the Foritgates have no NAT, then how does it get an IP address from the MT, and yet have other subnets behind it????
I think the idea is to push the data to the fortigates and let them deal with it. So Removed the Port forwarding (dstnat) and doing it through firewall rules and routes.
Okay thanks based on the new info......... minor changes to the previous configs.......
Changes
1. Removed the local subnet from RouterB and added the subnet behind the fortigate.
/interface wireguard peers
add allowed-address=10.22.0.2/32,172.25.0.0/24 interface=WG-RouterA public-key="--" comment="site to site"
2. Removed the two firewall rules allowing local lan to local lan traffic.
add action=accept chain=forward commeint="RB to RA" in-interface=WG-RouterA src-address=10.22.20.0/24 dst-address=10.22.10.0/24
add action=accept chain=forward comment="RA to RB" out-interface=WG-RouterA src-address=10.22.10.0/24 dst-address=10.22.20.0/24
3. Added firewall rules for management FG access both ways. You may want to refine to specific IPs....
4. Removed Routes for local LAN through wireguard and replaced with
a. static route for local FGA as Router does not know its existence when incoming FGB traffic arrives and exits the tunnel, and
b. route to wireguard for outgoing local FG to the FGB aka needs to enter tunnel.
....
................
I think the idea is to push the data to the fortigates and let them deal with it. So Removed the Port forwarding (dstnat) and doing it through firewall rules and routes.
Okay thanks based on the new info......... minor changes to the previous configs.......
Changes
1. Removed the local subnet from RouterB and added the subnet behind the fortigate.
/interface wireguard peers
add allowed-address=10.22.0.2/32,172.25.0.0/24 interface=WG-RouterA public-key="--" comment="site to site"
2. Removed the two firewall rules allowing local lan to local lan traffic.
add action=accept chain=forward commeint="RB to RA" in-interface=WG-RouterA src-address=10.22.20.0/24 dst-address=10.22.10.0/24
add action=accept chain=forward comment="RA to RB" out-interface=WG-RouterA src-address=10.22.10.0/24 dst-address=10.22.20.0/24
3. Added firewall rules for management FG access both ways. You may want to refine to specific IPs....
4. Removed Routes for local LAN through wireguard and replaced with
a. static route for local FGA as Router does not know its existence when incoming FGB traffic arrives and exits the tunnel, and
b. route to wireguard for outgoing local FG to the FGB aka needs to enter tunnel.
....
Code: Select all
# 2024-12-22 07:27:56 by RouterOS 7.16.2
# software id = 9931-M8FK
#
# model = CCR1016-12G
# serial number =
/interface bridge
add name=guest-lan
add name=py1-lan
/interface ethernet
set [ find default-name=ether1 ] comment=WAN-FTTH
set [ find default-name=ether2 ] comment=WAN-ILL
/interface pppoe-client
add disabled=no interface=ether1 name=WAN-FTTH user=netnam_manipy
/interface wireguard
add listen-port=51248 mtu=1420 name=WG-RouterA
/interface list
add name=LAN
add name=WAN
add name=TRUSTED
/interface wireless security-profiles
set [ find default=yes ] supplicant-identity=MikroTik
/ip pool
add name=dhcp_pool0 ranges=10.0.255.1-10.0.255.253
add name=dhcp_pool1 ranges=10.22.10.10-10.22.10.200
/ip dhcp-server
add address-pool=dhcp_pool0 interface=guest-lan lease-time=1d name=guest-dhcp
add address-pool=dhcp_pool1 interface=py1-lan lease-time=8h name=dhcp1
/port
set 0 name=serial0
set 1 name=serial1
/interface bridge port
add bridge=guest-lan interface=ether8
add bridge=py1-lan interface=ether9
add bridge=py1-lan interface=ether10
add bridge=py1-lan interface=ether11
add bridge=py1-lan interface=ether12
/ip neighbor discovery-settings
set discover-interface-list=TRUSTED
/interface l2tp-server server
set use-ipsec=yes
/interface list member
add interface=WAN-FTTH list=WAN
add interface=ether2 list=WAN
add interface=guest-lan list=LAN
add interface=py1-lan list=LAN
add interface=WG-RouterA list=LAN
add interface=py1-lan list=TRUSTED
add interface=WG-RouterA list=TRUSTED
/interface wireguard peers
add allowed-address=10.22.0.2/32,172.25.0.0/24 interface=WG-RouterA public-key="--" comment="site to site"
add allowed-address=10.22.19.1/32 interface=WG-RouterA name=bh.anh public-key=""
add allowed-address=10.22.19.2/32 interface=WG-RouterA name=hangmmh public-key=""
add allowed-address=10.22.19.3/32 interface=WG-RouterA name=ngocmmh public-key=""
add allowed-address=10.22.19.4/32 interface=WG-RouterA name=damhammh public-key=""
add allowed-address=10.22.19.5/32 interface=WG-RouterA name=hung.bravo public-key=""
add allowed-address=10.22.19.6/32 interface=WG-RouterA name=hoangbravo public-key=""
add allowed-address=10.22.19.7/32 interface=WG-RouterA name=bh.anh2 public-key=""
add allowed-address=10.22.19.8/32 interface=WG-RouterA name=bh.anh3 public-key=""
add allowed-address=10.22.19.9/32 interface=WG-RouterA name=lanbravo public-key=""
add allowed-address=10.22.19.10/32 interface=WG-RouterA name=nm.hung public-key=""
/ip address
add address=202.151.163.46/30 interface=ether2 network=202.151.163.44
add address=10.22.10.254/24 interface=py1-lan network=10.22.10.0
add address=10.0.255.254/24 interface=guest-lan network=10.0.255.0
add address=10.22.0.1/30 interface=WG-RouterA network=10.22.0.0 comment="site to site"
add address=10.22.19.254/24 interface=WG-RouterA network=10.22.19.0 comment="remote users"
/ip cloud
set ddns-enabled=yes
/ip dhcp-server network
add address=10.0.255.0/24 gateway=10.0.255.254
add address=10.22.10.0/24 dns-server=8.8.8.8,8.8.4.4 gateway=10.22.10.254
/ip dns
set servers=8.8.8.8,8.8.4.4
/ip firewall address-list
add address=10.22.10.XX list=AUTHORIZED comment="local admin pc"
add address=10.22.10.YY list=AUTHORIZED comment="local admin device2"
add address=10.22.19.AB list=AUTHORIZED comment="remote wg admin laptop"
add address=10.22.19.CD list=AUTHORIZED comment="remote wg admin smartphone/ipad"
add address=10.22.20.EF list=AUTHORIZED comment="admin local IP at RouterB"
add address=10.22.20.GH list=AUTHORIZED comment="admin local IP at RouterB device 2"
/ip firewall filter
add action=accept chain=input connection-state=established,related,untracked
add action=drop chain=input connection-state=invalid
add action=accept chain=input protocol=icmp
add action=accept chain=input dst-address=127.0.0.1
add action=accept chain=input comment="wireguard handshake" dst-port=51248
add action=accept chain=input comment="admin access" src-address=list=AUTHORIZED
add action=accept chain=input comment="users to services" in-interface-list=LAN dst-port=53,123 protocol=udp
add action=accept chain=input comment="users to services" in-interface-list=LAN dst-port=53 protocol=tcp
add action=drop chain=input comment="Drop all else" { make this rule last }
+++++++++++++++++++++++++++
add action=fasttrack-connection chain=forward connection-state=established,related hw-offload=yes
add action=accept chain=forward connection-state=established,related,untracked
add action=drop chain=forward connection-state=invalid
add action=accept chain=forward comment="internet traffic" in-interface-list=LAN out-interface-list=WAN
add action=accept chain=forward comment="remote users to RA" in-interface=WG-RouterA src-address=10.22.19.0/24 dst-address=10.22.10.0/24
add action=accept chain=forward comment="relay remote to RB" in-interface=WG-RouterA src-address=10.22.19.0/24 out-interface=WG-RouterA
add action=accept chain=forward comment="admin access" src-address-list=Authorized out-interface-list=LAN
add action=accept chain=forward comment="FGB to FGA" in-interface=WG-RouterA src-address=175.25.0.0/24 dst-address=175.20.0.0/24 dst-port=443
add action=accept chain=forward comment="FGA to FGB" out-interface=WG-RouterA src-address=175.20.0.0/24 dst-address=175.25.0.0/24 dst-port=443
add action=accept chain=forward comment="port forwarding" connection-nat-state=dstnat
add action=drop chain=forward comment="drop all else"
/ip firewall nat
add action=masquerade chain=srcnat out-interface=WAN-FTTH
add action=masquerade chain=srcnat out-interface=ether2
/ip route
{ Main routes for backup }
add check-gateway=ping dst-address=0.0.0.0/0 gateway=1.0.0.1 routing-table=main scope=10 target-scope=12
add dst-address=1.0.0.1/32 gateway=WAN1-Gateway-IP routing-table=main scope=10 target-scope=11
++++++++++++++++
add check-gateway=ping distance=2 dst-address=0.0.0.0/0 gateway=WAN2-Gateway-IP routing-table=main
++++++++++++++++
{ to ensure incoming RouterB Fortigate traffic gets to local FGA subnet }
add dst-address=175.20.0.0/24 gateway=10.22.10.253 routing-table=main
{ to ensure outgoing RouterA Fortigate traffic gets into tunnel for RouterB }
add dst-address=175.25.0.0/24 gateway=WG-RouterA routing-table=main
+++++++++++++++
{ special route for wireguard to wan2 }
add dst-address=ip.of.siteB.wan2/32 gateway=ip.or.siteA.wan2-gw
/ip service
set telnet disabled=yes
set ftp disabled=yes
set www disabled=yes
set ssh disabled=yes
set api disabled=yes
set api-ssl disabled=yes
/lcd
set time-interval=daily
/system clock
set time-zone-name=Asia/Ho_Chi_Minh
/system identity
set name=PY1-router-mikrotik
/system note
set show-at-login=no
/system ntp client
set enabled=yes
/system ntp client servers
add address=vn.pool.ntp.org
/tool mac-server
set allowed-interface-list=none
/tool mac-server mac-winbox
set allowed-interface-list=TRUSTED
/tool e-mail
set from=1@gmail.com port=465 server=smtp.gmail.com tls=yes user=\
1@gmail.comCode: Select all
# 2024-12-22 07:29:16 by RouterOS 7.16.2
# software id = 2M0R-ULGQ
#
# model = CCR2004-16G-2S+
# serial number =
/interface bridge
add name=guest-lan
add name=py2-lan
/interface ethernet
set [ find default-name=ether1 ] comment=WAN-FTTH
set [ find default-name=ether2 ] comment=WAN-ILL
/interface pppoe-client
add disabled=no interface=ether1 name=netnam-ftth user=netnam_manitn2
/interface wireguard
add listen-port=35359 mtu=1420 name=WG-RouterB
/interface list
add name=LAN
add name=WAN
add name=TRUSTED
/ip pool
add name=dhcp_pool0 ranges=10.255.255.1-10.255.255.250
add name=dhcp_pool2 ranges=10.22.20.1-10.22.20.250
/ip dhcp-server
add address-pool=dhcp_pool0 interface=guest-lan lease-time=8h name=dhcp1
add address-pool=dhcp_pool2 interface=py2-lan lease-time=8h name=dhcp2
/port
set 0 name=serial0
set 1 name=serial1
/interface bridge port
add bridge=py2-lan interface=ether16
add bridge=py2-lan interface=ether15
add bridge=py2-lan interface=ether14
add bridge=py2-lan interface=ether13
add bridge=guest-lan interface=ether12
/ip neighbor discovery-settings
set discover-interface-list=TRUSTED
/interface list member
add interface=netnam-ftth list=WAN
add interface=ether2 list=WAN
add interface=guest-lan list=LAN
add interface=py2-lan list=LAN
add interface=py2-lan list=TRUSTED
add interface=WG-RouterB list=TRUSTED
/interface wireguard peers
add allowed-address=10.22.0.1/32, 10.22.19.0/24,175.20.0.0/24 endpoint-address=SiteB-WAN2-IP \
endpoint-port=51248 interface=WG-RouterB persistent-keep-alive=25s public-key="----"
/ip address
add address=10.22.20.254/24 interface=py2-lan network=10.22.20.0
add address=10.255.255.254/24 interface=guest-lan network=10.255.255.0
add address=101.96.76.126/30 interface=ether2 network=101.96.76.124
add address=10.22.0.2/30 interface=WG-RouterB network=10.22.0.0
/ip cloud
set ddns-enabled=yes
/ip dhcp-server network
add address=10.255.255.0/24 dns-server=8.8.8.8,8.8.4.4 gateway=10.255.255.254
add address=10.22.20.0/24 dns-server=8.8.8.8,8.8.4.4 gateway=10.22.20.254
/ip dns
set servers=8.8.8.8,8.8.4.4
/ip firewall address-list
add address=10.22.10.XX list=AUTHORIZED comment="admin local IP at RouterA"
add address=10.22.10.YY list=AUTHORIZED comment="admin local IP at RouterA device2"
add address=10.22.19.AB list=AUTHORIZED comment="remote wg admin laptop"
add address=10.22.19.CD list=AUTHORIZED comment="remote wg admin smartphone/ipad"
add address=10.22.20.EF list=AUTHORIZED comment="local admin IP"
add address=10.22.20.GH list=AUTHORIZED comment="local admin IP device 2"
/ip firewall filter
add action=accept chain=input connection-state=established,related,untracked
add action=drop chain=input connection-state=invalid
add action=accept chain=input protocol=icmp
add action=accept chain=input dst-address=127.0.0.1
add action=accept chain=input comment="admin access" src-address=list=AUTHORIZED
add action=accept chain=input comment="users to services" in-interface-list=LAN dst-port=53,123 protocol=udp
add action=accept chain=input comment="users to services" in-interface-list=LAN dst-port=53 protocol=tcp
add action=drop chain=input comment="Drop all else" make this rule last
+++++++++++++++++++++++++++
add action=fasttrack-connection chain=forward connection-state=established,related hw-offload=yes
add action=accept chain=forward connection-state=established,related,untracked
add action=drop chain=forward connection-state=invalid
add action=accept chain=forward comment="internet traffic" in-interface-list=LAN out-interface-list=WAN
add action=accept chain=forward comment="FGA to FGB" in-interface=WG-RouterB src-address=175.20.0.0/24 dst-address=175.25.0.0/24 dst-port=443
add action=accept chain=forward comment="FGB to FGA" out-interface=WG-RouterB src-address=175.25.0.0/24 dst-address=175.20.0.0/24 dst-port=443
add action=accept chain=forward comment="remote users to RB" in-interface=WG-RouterB src-address=10.22.19.0/24 dst-address=10.22.20.0/24
add action=accept chain=forward comment="admin access" src-address-list=AUTHORIZED out-interface-list=LAN
add action=accept chain=forward comment="port forwarding" connection-nat-state=dstnat
add action=drop chain=forward comment="drop all else"
/ip firewall nat
add action=masquerade chain=srcnat out-interface-list=WAN
/ip firewall mangle
add action=change-mss chain=forward comment="Clamp MSS to PMTU for Outgoing packets" new-mss=clamp-to-pmtu out-interface=WG-RouterB passthrough=yes protocol=tcp tcp-flags=syn
/ip route
{ Main routes for backup }
add check-gateway=ping dst-address=0.0.0.0/0 gateway=1.1.1.1 routing-table=main scope=10 target-scope=12
add dst-address=1.1.1.1/32 gateway=WAN1-Gateway-IP routing-table=main scope=10 target-scope=11
++++++++++++++++
add check-gateway=ping distance=2 dst-address=0.0.0.0/0 gateway=WAN2-Gateway-IP routing-table=main
++++++++++++++++
{ to ensure incoming RouterA Fortigate traffic gets to local FGB subnet }
add dst-address=175.25.0.0/24 gateway=10.22.20.253 routing-table=main
{ to ensure outgoing RouterB Fortigate traffic gets into tunnel for RouterA }
add dst-address=175.20.0.0/24 gateway=WG-RouterB routing-table=main
+++++++++++++++
{ special route for wireguard to wan2 }
add dst-address=ip.of.siteA.wan2/32 gateway=ip.or.siteB.wan2-gw
/ip service
set telnet disabled=yes
set ftp disabled=yes
set www disabled=yes
set ssh disabled=yes
set api disabled=yes
set api-ssl disabled=yes
/system clock
set time-zone-name=Asia/Ho_Chi_Minh
/system identity
set name=PY2-Mikrotik-Router
/system note
set show-at-login=no
/system ntp client
set enabled=yes
/system ntp client servers
add address=vn.pool.ntp.org
/tool mac-server
set allowed-interface-list=none
/tool mac-server mac-winbox
set allowed-interface-list=TRUSTED
/system routerboard settings
set enter-setup-on=delete-keyRe: Wireguard VPN on dual WAN
You have yet to respond???
As this made no sense to me I had to assume some NAT on the fortigate and thus the config of the two mikrotiks will link the two fortigates as you requested.
Its simply a matter of proper configuration of the two Fortigates to ensure the traffic arriving at the Fortigates is handled appropriately as well as reply traffic.
Edit: I think the take away is that I dont understand networking enough to understand but what you are doing may work just fine and as stated, just configure the Fortigates as required.
As this made no sense to me I had to assume some NAT on the fortigate and thus the config of the two mikrotiks will link the two fortigates as you requested.
Its simply a matter of proper configuration of the two Fortigates to ensure the traffic arriving at the Fortigates is handled appropriately as well as reply traffic.
Edit: I think the take away is that I dont understand networking enough to understand but what you are doing may work just fine and as stated, just configure the Fortigates as required.
Re: Wireguard VPN on dual WAN
Hello guys,
Sorry for my long time offline,
I have received technical support from my local Mikrotik seller, due to their security contract I cannot post current configuration.
In the future, if I have any new I ideal, I'm looking forward to receive your support.
Thank you for your kindly support once again.
Best regards,
Sorry for my long time offline,
I have received technical support from my local Mikrotik seller, due to their security contract I cannot post current configuration.
In the future, if I have any new I ideal, I'm looking forward to receive your support.
Thank you for your kindly support once again.
Best regards,
Re: Wireguard VPN on dual WAN
If you can point out where the mistakes were or where the corrections were made it will help others.
Re: Wireguard VPN on dual WAN
Sindi's initial solution is accurate. You just need to point the IP of another WG to the corresponding WAN gateway in the routing table. In case you have dynamic WG clients (Road Warrior) you will need a script that regularly reads their peer logs and adjusts their main table. Don't mess with mangles, tags or additional tables, it will only mess up your configuration.Hello guys,
Sorry for my long time offline,
I have received technical support from my local Mikrotik seller, due to their security contract I cannot post current configuration.
In the future, if I have any new I ideal, I'm looking forward to receive your support.
Thank you for your kindly support once again.
Best regards,
Re: Wireguard VPN on dual WAN
I just route site to site traffic through WAN2, lesser traffic (remote client) access throught WAN1.If you can point out where the mistakes were or where the corrections were made it will help others.
Who is online
Users browsing this forum: dcavni and 125 guests



