v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Note: wireless-fp package is discontinued in this version. It needs to be uninstalled/disabled before upgrade. Use wireless-rep or wireless-cm2 instead.
What's new in 6.36rc3 (2016-Apr-19 11:33):
*) bonding - do not corrupt bonding statistics on configuration changes;
*) bonding - fixed crash when vlan parent mtu is higher than bonding mtu;
*) ethernet - do not allow mtu to be higher than l2mtu and l2mtu to be higher than max-l2mtu (reduce automatically on upgrade if it was wrong before);
*) firewall - added udplite, dccp, sctp connection tracking helpers;
*) switch - fixed switch compact export;
*) traffic-flow - added ipfix support (RFC5101 and RFC5102);
*) wireless - wireless-fp is discontinued, it needs to be uninstalled/disabled before upgrade;
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash.
What's new in 6.36rc3 (2016-Apr-19 11:33):
*) bonding - do not corrupt bonding statistics on configuration changes;
*) bonding - fixed crash when vlan parent mtu is higher than bonding mtu;
*) ethernet - do not allow mtu to be higher than l2mtu and l2mtu to be higher than max-l2mtu (reduce automatically on upgrade if it was wrong before);
*) firewall - added udplite, dccp, sctp connection tracking helpers;
*) switch - fixed switch compact export;
*) traffic-flow - added ipfix support (RFC5101 and RFC5102);
*) wireless - wireless-fp is discontinued, it needs to be uninstalled/disabled before upgrade;
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
PLEASE make wireless-fp auto replaced by wireless-cm2. Otherwise it will be a pain to upgrade all CPEs in the network to 6.36 
And... Could you please release a changelog for wireless-fp -> wireless-cm2?
And... Could you please release a changelog for wireless-fp -> wireless-cm2?
-

-
kometchtech
Member Candidate

- Posts: 194
- Joined:
- Location: Japan
- Contact:
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
have the USB disk is not detected by the RB3011.
[Ticket#2016041966000617]
[Ticket#2016041966000617]
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
You can install cm2 before update. Then switch the packages and update afterwards. I agree that automatic wireless packages switch during the update would be much more convenient.PLEASE make wireless-fp auto replaced by wireless-cm2. Otherwise it will be a pain to upgrade all CPEs in the network to 6.36
And... Could you please release a changelog for wireless-fp -> wireless-cm2?
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Sure, but you have to manually (or automatically in batch) change package.You can install cm2 before update. Then switch the packages and update afterwards. I agree that automatic wireless packages switch during the update would be much more convenient.PLEASE make wireless-fp auto replaced by wireless-cm2. Otherwise it will be a pain to upgrade all CPEs in the network to 6.36
And... Could you please release a changelog for wireless-fp -> wireless-cm2?
It's not so simple and you have to schedule both wireless package change and RouterOS upgrade.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
As far as I'm aware the only major difference between the two is the supported version of CAPsMAN. Otherwise they should be functionally equivalent. If you happen to used CAPsMAN v1, there are upgrade instruction on the wiki.Could you please release a changelog for wireless-fp -> wireless-cm2?
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
That's true, but you don't have to do that at the same time- start doing the former now already, if you feel like.you have to schedule both wireless package change and RouterOS upgrade.
Having said that, automatic upgrade from old wireless or wireless-fp to wireless-cm2 would be much appreciated, of course.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
yes, but doing auto-upgrade with manually added packages (e.g. not the bundled in main package) will fail as wireless-fp-x.xx-arch.npk will not be on the distribution site.As far as I'm aware the only major difference between the two is the supported version of CAPsMAN. Otherwise they should be functionally equivalent. If you happen to used CAPsMAN v1, there are upgrade instruction on the wiki.Could you please release a changelog for wireless-fp -> wireless-cm2?
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
I´d like to request a feature for wireless-rep package:
- Is it possible to show the username (beside the MAC address) for all connected clients within CAPSMAN window?
(It would be helpful to see on which access point a client is connected when users calling support and complains about connectivity issues they have...)
- Is it possible to show the username (beside the MAC address) for all connected clients within CAPSMAN window?
(It would be helpful to see on which access point a client is connected when users calling support and complains about connectivity issues they have...)
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Can on 6.36 final release a forced changeover from wireless-fp to wireless-cm2?
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
+1I´d like to request a feature for wireless-rep package:
- Is it possible to show the username (beside the MAC address) for all connected clients within CAPSMAN window?
(It would be helpful to see on which access point a client is connected when users calling support and complains about connectivity issues they have...)
I have a few more requests:
Is it possible to show CCQ for each connected client? Or dropped / retransmitted frames percentage?
Is it possible to perform background scan for each remote radio?
(It would be helpful to see connection quality statistics as well as channel usage statistics within CAPSMAN window)
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Let´s summarize the feature requests for wireless-rep:
+ custom names for CAP devices
+ centralized ressource monitoring / statistics ([CPU, RAM, amount of connected clients for each CAP device], total amount of connected devices, frequency band usage, "rogue devices" using the same frequency band or the same SSID per CAP device,...)
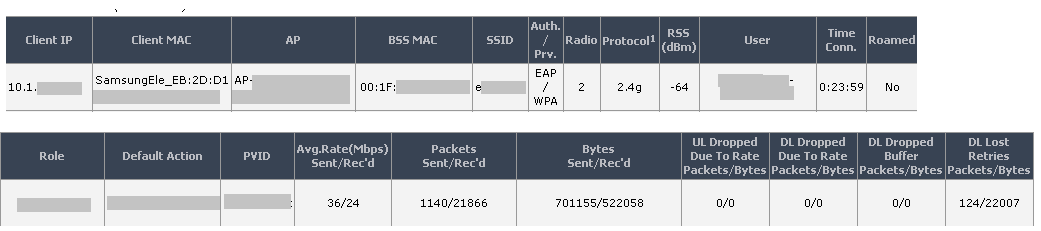
Is it possible to show CCQ for each connected client? Or dropped / retransmitted frames percentage?
Is it possible to perform background scan for each remote radio?
(It would be helpful to see connection quality statistics as well as channel usage statistics within CAPSMAN window)
+ vendor OUI auto namingshow the username (beside the MAC address) for all connected clients within CAPSMAN window?
)
+ custom names for CAP devices
+ centralized ressource monitoring / statistics ([CPU, RAM, amount of connected clients for each CAP device], total amount of connected devices, frequency band usage, "rogue devices" using the same frequency band or the same SSID per CAP device,...)

Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
What do you mean? Is '/system identity' on a CAP device not what you need?+ custom names for CAP devices
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Let´s summarize the feature requests for wireless-rep:Is it possible to show CCQ for each connected client? Or dropped / retransmitted frames percentage?
Is it possible to perform background scan for each remote radio?
(It would be helpful to see connection quality statistics as well as channel usage statistics within CAPSMAN window)+ vendor OUI auto namingshow the username (beside the MAC address) for all connected clients within CAPSMAN window?
)
+ custom names for CAP devices
+ centralized ressource monitoring / statistics ([CPU, RAM, amount of connected clients for each CAP device], total amount of connected devices, frequency band usage, "rogue devices" using the same frequency band or the same SSID per CAP device,...)
My post with CAPsMAN feature requests in the 6.35rc thread:
Requests for CAPsMAN bug fixes and new features, based on my experience with the current RC version:
1. {Nice to have} Add "CCQ", P Throughput" and "Signal to Noise", "Encryption" and "Group Encryption" and "WMM Enabled" fields to CAPsMAN Registration Table.
2. {Feature} Add "Frequency Mode", "WMM Support", "Multicast Buffering", "Keepalive frames", "Adaptive Noise Immunity" and "AMPDU Priorities" to CAPsMAN Config Settings.
3. {BUG} Make "Multicast Helper=full" in CAPsMAN slave interfaces work (now the interfaces stay in default setting).
4. {BUG} Make "Country=no_country_set" work on CAPsMAN 5GHz 802.11ac interfaces (it works on 2.4GHz, but on 5GHz ones it results in "no supported band" error message, regardless of the band and frequency settings).
5. {Feature} Add a scan/freq usage feature in CAPsMAN, with an aption to run in the background. Right now, if one wants to scan, they have to detach the physical interface from the Manager, do the scan and re-attach it. [In the future, use this info to auto-adjust CAP channels and power levels.]
6. {Annoying} Stop CAPsMAN from creating virtual interfaces on CAPs with name "wlanXXX" where XXX is a number which is incremented every time the interface is disabled and re-enabled.
7. {Nice to have} Let the user rename the virtual interfaces on the CAPs, like he/she can do with physical interfaces.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Also: Since upgrading from 6.35rc48 to 6.35, my hAP acting as CAPsMAN loses the association with some of the CAPs after a few hours (<1 day), even though the CAPs are accessible from the hAP. The CAPs that have dissassociated stop publishing any wlans. A reboot of the problematic CAPs fixes the problem: they appear again in the "Remote CAP" table. This has happened three times within two days, while had never happened before. I don't know whether this is of any relevance, but free disk space on the hAP is low, to about 1.4MB, even though there are no files taking up any significant space. Sometimes I even get error messages from User Manager because of low space.
All devices are running on 6.35 stable.
I am publishing this here because it has to be worked on in this version.
All devices are running on 6.35 stable.
I am publishing this here because it has to be worked on in this version.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
nkourtzis, this problem is reproduced and fixed. We hope we will be able to release a fixed version today.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
+1Can on 6.36 final release a forced changeover from wireless-fp to wireless-cm2?
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
please add into the CapsMan Registration Table fields:
CCQ, RadioName, Distance,
and the option to scan for free frequencies for each cap
and also the Channel Width 10mhz
I use CapsMan to have a centralized management of all my sectors and customers with SXT of my Wisp
so the request of the CCQ and RadioName
and in some sector still in use migrated 10mhz
CCQ, RadioName, Distance,
and the option to scan for free frequencies for each cap
and also the Channel Width 10mhz
I use CapsMan to have a centralized management of all my sectors and customers with SXT of my Wisp
so the request of the CCQ and RadioName
and in some sector still in use migrated 10mhz
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Good news, but...nkourtzis, this problem is reproduced and fixed. We hope we will be able to release a fixed version today.
When was this bug introduced and how did it make it into the "stable" version? It is not a rare bug. Possibly you should start remaining to the last RC, the one which can ACTUALLY be named Release Candidate, for a few days without making any further additions, just bug fixing, before releasing it as stable. Even from rc48 and rc49 to the stable, there were additions which could introduce new bugs.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
What you call "stable" is called "bugfix only" by Mikrotik guys. And it is version 6.32.4 at the moment. Please read release branch descriptions at the top of official download page. CAPsMAN is rock solid in 6.32.4 with wireless-cm2 for me.When was this bug introduced and how did it make it into the "stable" version?
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
please add CCQ for clients on registration table of caps manager
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
MikroTik RouterOS v6.36rc4 is released.
What's new in 6.36rc4 (2016-Apr-20 12:46):
*) arp - added arp-timeout option per interface;
*) log - fixed reboot log messages;
*) traffic-flow - added ipfix support (RFC5101 and RFC5102);
*) tunnel - added option to auto detect tunnel local-address;
*) wireless - fixed issue when CAPsMAN could lock CAPs interface;
*) wireless-rep - fixed scan-list unset;
http://www.mikrotik.com/download
What's new in 6.36rc4 (2016-Apr-20 12:46):
*) arp - added arp-timeout option per interface;
*) log - fixed reboot log messages;
*) traffic-flow - added ipfix support (RFC5101 and RFC5102);
*) tunnel - added option to auto detect tunnel local-address;
*) wireless - fixed issue when CAPsMAN could lock CAPs interface;
*) wireless-rep - fixed scan-list unset;
http://www.mikrotik.com/download
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Hi Sergejs,*) traffic-flow - added ipfix support (RFC5101 and RFC5102);
It is great to see IPFIX being added to RouterOS
Does the added IPFIX feature have the Layer2 features of IPFIX ? e.g. can it export flows for traffic traversing a bridge ?
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
How it can be used? I have not found in winbox anywhere.MikroTik RouterOS v6.36rc4 is released.
*) tunnel - added option to auto detect tunnel local-address;
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
We will adjust Winbox in future rc releases.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
ОК.We will adjust Winbox in future rc releases.
In the terminal mode it is still also unavailable?
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
it would be something like this example for tunnelbroker 6to4:
Code: Select all
/interface 6to4 add local-address=0.0.0.0 remote-address=192.168.88.1Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Work with 6to4, but not with gre or ipip existing tunnels.it would be something like this example for tunnelbroker 6to4:
Code: Select all/interface 6to4 add local-address=0.0.0.0 remote-address=192.168.88.1
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Any hope to get IPIP point to multipoint tunnel interfaces like in GNU/Linux?it would be something like this example for tunnelbroker 6to4:
Code: Select all/interface 6to4 add local-address=0.0.0.0 remote-address=192.168.88.1
Code: Select all
/interface ipip add local-address=11.22.33.44 remote-address=0.0.0.0 name="ipip1"Code: Select all
/ip route add dst-address=10.0.1.0/24 gateway=1.2.3.4%ipip1
/ip route add dst-address=10.0.2.0/24 gateway=2.3.4.5%ipip1The kernel IPIP module supports this out of the box, which is probably also true for the kernel you use in ROS:
Code: Select all
/ip tunnel add ipip1 mode ipip local 11.22.33.44
/ip route add 10.0.1.0/24 via 1.2.3.4 dev ipip1
/ip route add 10.0.2.0/24 via 2.3.4.5 dev ipip1Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Poor performance between 2 CCR 1072...
Bandwith test with direct 10G connected, from one CCR to another, DIRECT CABLE, no switches no nothing.
Same configuration on both:
L2MTU: 9216
MTU: 9000
[admin@ICMAN02] > /tool bandwidth-test protocol=tcp address=10.1.2.7 user=admin password=somepassword
status: running
duration: 11s
rx-current: 484.9Mbps
rx-10-second-average: 690.3Mbps
rx-total-average: 700.7Mbps
random-data: no
direction: receive
[admin@ICMAN02] > /tool bandwidth-test protocol=tcp address=10.1.2.7 user=admin password=somepassword direction=transmit
status: running
duration: 9s
tx-current: 622.0Mbps
tx-10-second-average: 785.6Mbps
tx-total-average: 785.6Mbps
random-data: no
direction: transmit
Both supout.rif are uploaded to my Mikrotik account, login is nadeu
Regards
Bandwith test with direct 10G connected, from one CCR to another, DIRECT CABLE, no switches no nothing.
Same configuration on both:
L2MTU: 9216
MTU: 9000
[admin@ICMAN02] > /tool bandwidth-test protocol=tcp address=10.1.2.7 user=admin password=somepassword
status: running
duration: 11s
rx-current: 484.9Mbps
rx-10-second-average: 690.3Mbps
rx-total-average: 700.7Mbps
random-data: no
direction: receive
[admin@ICMAN02] > /tool bandwidth-test protocol=tcp address=10.1.2.7 user=admin password=somepassword direction=transmit
status: running
duration: 9s
tx-current: 622.0Mbps
tx-10-second-average: 785.6Mbps
tx-total-average: 785.6Mbps
random-data: no
direction: transmit
Both supout.rif are uploaded to my Mikrotik account, login is nadeu
Regards
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Are you aware that BW test runs on single core? And single core is not capable of generating TCP traffic much more than that?
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Can you please tell exactly what should i use instead of it to still have fastpath enabled(as on CCR without it fastpath support was disabled)?wireless - wireless-fp is discontinued, it needs to be uninstalled/disabled before upgrade;
Or fastpath support migrated fully to main module now?
-

-
MartijnVdS
Frequent Visitor

- Posts: 93
- Joined:
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Both replacement modules (wireless-cm2 and wireless-rep) support fastpath.Can you please tell exactly what should i use instead of it to still have fastpath enabled(as on CCR without it fastpath support was disabled)?wireless - wireless-fp is discontinued, it needs to be uninstalled/disabled before upgrade;
Or fastpath support migrated fully to main module now?
As far as I understand, -cm2 and -rep contain everything that was in -fp and then some.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
The only wireless package that does not support fastpath was old/regular "wireless", which was first removed from the bundle package lust July, then completely discontinued last December. All three "wireless-fp", "wireless-cm2" and "wireless-rep" do support fastpath. The major difference is -fp supports CAPsMAN v1 while -cm2 and -rep support CAPsMAN v2, and v1 is not compatible with v2 so you have to plan the migration in case you use CAPsMAN.Can you please tell exactly what should i use instead of it to still have fastpath enabled(as on CCR without it fastpath support was disabled)?
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Version 6.36rc5 has been released.
Changes since previous version:
*) arp - added arp-timeout option per interface;
*) log - fixed reboot log messages;
*) lte - do not allow to set multiple modes when it is not supported;
*) lte - fixed address acquisition on Huaweii LTE interfaces;
*) ntp - fixed time keeping on SXT ac, RB911L, cAP and wAP
*) traffic-flow - added ipfix support (RFC5101 and RFC5102);
*) winbox - show voltage in Health only if there actually is voltage monitor;
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash.
Changes since previous version:
*) arp - added arp-timeout option per interface;
*) log - fixed reboot log messages;
*) lte - do not allow to set multiple modes when it is not supported;
*) lte - fixed address acquisition on Huaweii LTE interfaces;
*) ntp - fixed time keeping on SXT ac, RB911L, cAP and wAP
*) traffic-flow - added ipfix support (RFC5101 and RFC5102);
*) winbox - show voltage in Health only if there actually is voltage monitor;
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Hi.
Is any chance to improve TCP performance on single session over IPSEC on IPIP/GRE tunnel in this version?
Now is max 40-80 Mbps per session regardless of device model (tested on CCR 1009 and CCR 1036).
Is any chance to improve TCP performance on single session over IPSEC on IPIP/GRE tunnel in this version?
Now is max 40-80 Mbps per session regardless of device model (tested on CCR 1009 and CCR 1036).
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
What encryption are you running?Hi.
Is any chance to improve TCP performance on single session over IPSEC on IPIP/GRE tunnel in this version?
Now is max 40-80 Mbps per session regardless of device model (tested on CCR 1009 and CCR 1036).
We see close to 600mbit/s over EoIP/IPSEC with AES256-AES256-CBC on a CCR1036
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Why is LTE package not available for ARM architecture?
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
After upgrade the latest RC, RB 2011UiAS-2HnD


Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
dev246 - Is any of CPU cores loaded 100%? Not total CPU load but load per CPU core.
wombat - This is 6.36rc topic. Upgrade to 6.36rc version where issue is fixed.
wombat - This is 6.36rc topic. Upgrade to 6.36rc version where issue is fixed.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Hi,
on RB2011 is 6.36 RC it is only view from put above unit for see problems. On RB2011 with 6.36 i can't login at the moment only netinstall is way ..
on RB2011 is 6.36 RC it is only view from put above unit for see problems. On RB2011 with 6.36 i can't login at the moment only netinstall is way ..
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Could you share that config?What encryption are you running?Hi.
Is any chance to improve TCP performance on single session over IPSEC on IPIP/GRE tunnel in this version?
Now is max 40-80 Mbps per session regardless of device model (tested on CCR 1009 and CCR 1036).
We see close to 600mbit/s over EoIP/IPSEC with AES256-AES256-CBC on a CCR1036
Skickat från min Nexus 6P via Tapatalk
-

-
kometchtech
Member Candidate

- Posts: 194
- Joined:
- Location: Japan
- Contact:
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Routerboard mipsbe system raise the bootloop.
ROS6.36rc5
ROS6.36rc5
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
reboot loop as well on ccr1009 for v6.36rc5
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
reboot loop for me too on RB2011 for v6.36r5. Reverted to 6.35 using Netinstall to revive.
Again, wow... won't say more.
Again, wow... won't say more.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Several RB751's and a 951G have locked up... WTF guys... Please, quit putting out software that locks up our units.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
I don't know if Mikrotik hired a monkey to direct the development team, but going from bad to worse. Where is the stability of the branch 5? MikroTik is provoking nightmares to their "carrier users".Several RB751's and a 951G have locked up... WTF guys... Please, quit putting out software that locks up our units.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
v6.36r5 cause reboot loop on mAP2n, netinstall to v6.35
Calling mikrotik staff to be monkeys is not appropriate. Why are you installing rc versions? Keep the bugfix branch installed and don't touch working things.
If you would like to help mikrotik to fine tune the rc, you have to expect that the device will be frozen so netinstall will be the only solution. If you are not prepared for it, don't do it.
Making netinstall is question of 2 minutes...
If you would like to help mikrotik to fine tune the rc, you have to expect that the device will be frozen so netinstall will be the only solution. If you are not prepared for it, don't do it.
Making netinstall is question of 2 minutes...
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
RC software is for testing purposes, do not complain if your unit doesn't boot after upgrade. If you want to be useful, try to describe your problem to mikrotik's staff, so they can find and fix the bug that caused it.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
I have every right to complain if the software locks up my router !!RC software is for testing purposes, do not complain if your unit doesn't boot after upgrade. If you want to be useful, try to describe your problem to mikrotik's staff, so they can find and fix the bug that caused it.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
You have never been a programmer. Test software is far from perfect. Complex software can easily include deadly bugs. If you don't want your device to lock up, don't use RC, there are other two branches that suit you better.I have every right to complain if the software locks up my router !!
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Thank you for your comments, but I must say..You do not know who I am, or what I am able to do. The one thing I am though is a customer, and so I EXPECT certain things.

If I ran a company like Mikrotik, I wouldn't want people to think that my product might include "deadly bugs".
Again, I thank you for your constructive(?) comments.
Are you speaking for Mikrotik as an authority of what will, and what won't lock up? Or should I just roll the dice?If you don't want your device to lock up, don't use RC, there are other two branches that suit you better.
If I ran a company like Mikrotik, I wouldn't want people to think that my product might include "deadly bugs".
Again, I thank you for your constructive(?) comments.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
MT might not be rock solid and probably never will, not only it's extremely complicated system but also it's constantly evolving. That being said if you randomly upload RC version on your production system you can't really have right to complain, it says right at the top of the download page - "(...) Release candidate for testing the absolute latest builds in test environments".Are you speaking for Mikrotik as an authority of what will, and what won't lock up? Or should I just roll the dice?
If I ran a company like Mikrotik, I wouldn't want people to think that my product might include "deadly bugs".
Do you want to hear something constructive - use bugfix version in the future.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
@w0lt and nadeu,
Do you know what an RC is? It's a "Release Candidate" and its purpose is to be tested so that the developers know what doesn't work beyond the numerous configurations they have tried themselves. They cannot possibly try every config combination before they release a version and if they did, there would be no bugs and no RC. If you are installing these versions on a live production network then you guy's are the monkeys and i feel sorry for your customers.
Do you know what an RC is? It's a "Release Candidate" and its purpose is to be tested so that the developers know what doesn't work beyond the numerous configurations they have tried themselves. They cannot possibly try every config combination before they release a version and if they did, there would be no bugs and no RC. If you are installing these versions on a live production network then you guy's are the monkeys and i feel sorry for your customers.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
The only thing we know about you is your bad behaviour.Thank you for your comments, but I must say..You do not know who I am, or what I am able to do.
You should expect that official software releases work as they should. If not, you have right to complain.The one thing I am though is a customer, and so I EXPECT certain things.
You can even roll two dices at once.Are you speaking for Mikrotik as an authority of what will, and what won't lock up? Or should I just roll the dice?
Who stops you to run your own software company ? Show us how to release software with no errors ? Each time.If I ran a company like Mikrotik, I wouldn't want people to think that my product might include "deadly bugs".
Thank you for your constructive complaints.Again, I thank you for your constructive(?) comments.
P.S.
Do you really blindly upgrade your working infrastructure to RC versions without any lab tests ?
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
For example:RC software is for testing purposes, do not complain if your unit doesn't boot after upgrade. If you want to be useful, try to describe your problem to mikrotik's staff, so they can find and fix the bug that caused it.
In forum branch about 6.35 verison MikroTik Support time to time says - "...issues are already fixed in 6.36rc"
My question about 6.35.1 with bugfixes - silent ignore.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
6.36rc5 kernel panics on boot on CCR 1036 even after a fresh netinstall
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Each and every release we have to remind two things.
First of all, rc versions are nightly builds and are not completely tested. It means that each version can and must be tested only on devices which you are willing to Netinstall, if it will be necessary. Basically - just for testing.
Secondary, if you want to complain about specific things, then please create specific topic for that. This is 6.36rc version topic which is created for actual software related discussions to help MikroTik staff and our clients to get rid of problems within specific version - 6.36.
Support staff is actually very open minded and is open for suggestions. Send your requests, suggestions and complaints to support team, if problem is related to software in any way. Otherwise, please create separate topics and do not hijack topic within which people are actually tying to help each other.
As for rc version itself - we are not seeing reboot loops with this version in general. It must/should be related to configuration. Please send supout files and/or serial output to support@mikrotik.com so we can research this particular issue.
First of all, rc versions are nightly builds and are not completely tested. It means that each version can and must be tested only on devices which you are willing to Netinstall, if it will be necessary. Basically - just for testing.
Secondary, if you want to complain about specific things, then please create specific topic for that. This is 6.36rc version topic which is created for actual software related discussions to help MikroTik staff and our clients to get rid of problems within specific version - 6.36.
Support staff is actually very open minded and is open for suggestions. Send your requests, suggestions and complaints to support team, if problem is related to software in any way. Otherwise, please create separate topics and do not hijack topic within which people are actually tying to help each other.
As for rc version itself - we are not seeing reboot loops with this version in general. It must/should be related to configuration. Please send supout files and/or serial output to support@mikrotik.com so we can research this particular issue.
-

-
JimmyNyholm
Member Candidate

- Posts: 248
- Joined:
- Location: Sweden
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
OK So I'm an idiot. Not Reading and just upgrading. What happens if I didn't disable the package?
I have one mAPLite upgraded and now it just boot loops. How do I apply a firmware reset on the unit?
I have one mAPLite upgraded and now it just boot loops. How do I apply a firmware reset on the unit?
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
If you are talking about not disabling wireless package, then you can not upgrade until you have removed it. From which version did you upgrade? As we were telling in previous topics about other versions, there was a problem with upgrade but it is not an issue of 6.36rc. It was a problem with old version on which actually upgrade is performed.
Try to Netinstall device to this same rc version to see if problem was caused by old version or this new one:
http://wiki.mikrotik.com/wiki/Manual:Netinstall
Try to Netinstall device to this same rc version to see if problem was caused by old version or this new one:
http://wiki.mikrotik.com/wiki/Manual:Netinstall
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Reboot loop with 6.36rc5 version will be fixed within 6.36rc6 version. We will release it later today.
-

-
JimmyNyholm
Member Candidate

- Posts: 248
- Joined:
- Location: Sweden
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Great Thanks. I will back down to 6.35, disable package and w8 for the new rc to come out. I'm eager to se what have been done with automatic tunnel ip selection..... May solve some of our pressing needs.If you are talking about not disabling wireless package, then you can not upgrade until you have removed it. From which version did you upgrade? As we were telling in previous topics about other versions, there was a problem with upgrade but it is not an issue of 6.36rc. It was a problem with old version on which actually upgrade is performed.
Try to Netinstall device to this same rc version to see if problem was caused by old version or this new one:
http://wiki.mikrotik.com/wiki/Manual:Netinstall
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Version 6.36rc6 has been released.
Changes since previous version:
*) ipsec - fix initiator modecfg dynamic dns;
*) nand - improved nand refresh feature to enhance stored data integrity;
*) route - fixed ospf by handling ipv6 encoded prefixes with stray bits;
*) watchdog - fixed reboot loop on startup (introduced in 6.36rc5);
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash.
Changes since previous version:
*) ipsec - fix initiator modecfg dynamic dns;
*) nand - improved nand refresh feature to enhance stored data integrity;
*) route - fixed ospf by handling ipv6 encoded prefixes with stray bits;
*) watchdog - fixed reboot loop on startup (introduced in 6.36rc5);
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Looks like OSPF is not working properly with rc6 because of this fix. Please use with caution. This change will hopefully fix problems when two OSPFv3 neighbors are stuck in Exchange/ExStart states.*) route - fixed ospf by handling ipv6 encoded prefixes with stray bits;
-

-
NetworkPro
Forum Guru

- Posts: 1376
- Joined:
- Location: bit.ly/the-qos
- Contact:
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
I revived the CCR1072 by NetInstall with preserve configuration.
However now there is a problem with LCD: it is white and does not display anything.
6.36rc6
However now there is a problem with LCD: it is white and does not display anything.
6.36rc6
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
ATTENTION ON CHR
ON CHR under proxmox
after upgrade 6.36rc5 to rc6 cant ping, telnet, winbox
using hypervisor console can access it
but freeze if i try to use the ping tool
ip address print get no output
ip arp print get no output
need to ctrl +c to get back
since I don’t have connectivity to the chr I can’t export the supout file
ON CHR under proxmox
after upgrade 6.36rc5 to rc6 cant ping, telnet, winbox
using hypervisor console can access it
but freeze if i try to use the ping tool
ip address print get no output
ip arp print get no output
need to ctrl +c to get back
since I don’t have connectivity to the chr I can’t export the supout file
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
If you have a Routerboard that has the memory allocation to add an additional partition, then before you install any further RC firmware I would accomplish the following procedure.
1. Ensure you have ROS 6.35 (Stable) on Partition-0, if not upgrade or downgrade to it.
2. Select "Partition" off the left hand side menu, and "Add" an additional partition. This will cause the router to reboot, that's ok.
3. Once rebooted, select "Partition" off the menu, then select Partition-0, after that, copy Partition-0 to Partition-1. Once that's done, Save the Partition-0 "Config" to Partition-1
4. When this is done, you can upgrade to the latest RC firmware, and if it locks up, it should fallback to the Partition-1 firmware.
At the very lease, you can recover your box. Hope this might help, it has helped me.
-tp
1. Ensure you have ROS 6.35 (Stable) on Partition-0, if not upgrade or downgrade to it.
2. Select "Partition" off the left hand side menu, and "Add" an additional partition. This will cause the router to reboot, that's ok.
3. Once rebooted, select "Partition" off the menu, then select Partition-0, after that, copy Partition-0 to Partition-1. Once that's done, Save the Partition-0 "Config" to Partition-1
4. When this is done, you can upgrade to the latest RC firmware, and if it locks up, it should fallback to the Partition-1 firmware.
At the very lease, you can recover your box. Hope this might help, it has helped me.
-tp
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
I have a long open ticket with Mikrotik on this issue. I'm guessing you are using an application that is sensitive to packet loss and/or you have latency above a few milliseconds.What encryption are you running?Hi.
Is any chance to improve TCP performance on single session over IPSEC on IPIP/GRE tunnel in this version?
Now is max 40-80 Mbps per session regardless of device model (tested on CCR 1009 and CCR 1036).
We see close to 600mbit/s over EoIP/IPSEC with AES256-AES256-CBC on a CCR1036
The problem is the hardware encryption driver (on CCR that means aes-*-cbc encryption) encrypts/sends packets out of order. This results in the client seeing packet loss, duplicate acks, out of order packets, etc, which cause performance issues with TCP (some benchmarking/real world traffic shows about 50% of packets are retransmits and duplicate acks). How much depends on a variety of things (like application, tcp window, latency, etc). Because of this, I actually use software encryption (aes-256-ctr) instead because I see about 10x faster single-threaded transfers. Here are some example numbers:
Software/single stream: 75Mbps
Software/multiple stream: 150Mbps (single cpu core maxed)
Hardware/single stream: ~7.5Mbps
Hardware/multiple stream: >500Mbps
Note: Same tests performed. Only difference is toggling (default in /ip ipsec proposal) between CBC (hardware) and CTR (software). Also, you often have to flush installed SAs after changing this on both sides to get the session to actually switch over.
This is unfortunate because the software driver is virtually error-free and performs better on single stream, but means you are cpu bound and can't take advantage of the hardware's builtin decryption capabilities that give you far better multiple stream data rates. If they can fix the hardware driver, we should be able to get the best of both worlds.
This is the last thing I heard when checking up on April 5, 2016:
So I just keep waiting to see it in the changelog. I would welcome others inviting them to make this a higher priority though.Hello,
There is no fix yet. When we will fix it, changes will be in the changelog.
Regards,
Maris B.
Update on May 20:
We are working on the fix.
Last edited by alexjhart on Fri May 20, 2016 7:11 pm, edited 1 time in total.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
I don't know if Mikrotik hired a monkey to direct the development team, but going from bad to worse. Where is the stability of the branch 5? MikroTik is provoking nightmares to their "carrier users".Several RB751's and a 951G have locked up... WTF guys... Please, quit putting out software that locks up our units.
Why don't you move to another brand then? Many less features, many less bugs. Or many features, less bugs, 10 times the price. Slow release cycle and no access to beta software. You have a choice. I anyone told you you can have it all, they lied to you my friend.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
We upgraded to RC because MikroTik support indicates, we are following with MikroTik support team.I don't know if Mikrotik hired a monkey to direct the development team, but going from bad to worse. Where is the stability of the branch 5? MikroTik is provoking nightmares to their "carrier users".Several RB751's and a 951G have locked up... WTF guys... Please, quit putting out software that locks up our units.
Why don't you move to another brand then? Many less features, many less bugs. Or many features, less bugs, 10 times the price. Slow release cycle and no access to beta software. You have a choice. I anyone told you you can have it all, they lied to you my friend.
Did not mean it literally was a joke from the monkeys. We have over 30 CloudCores in production, and more than 200 radiolinks, we trust MikroTik and bet on them, all we ask is more feedback.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
The upgrade process of the latests RC and the final version must upgrade automatically wireless-fp to the most reliable alternative wireless package, as it did when plain wireless got replaced by wireless-fp somewhere around v6.30. I understand that this is are initial RC releases and for testing purposes manually uninstalling a package its ok, but this is something that Mikrotik should address before final release to avoid some nightmares their fellow Wisp's...Note: wireless-fp package is discontinued in this version. It needs to be uninstalled/disabled before upgrade. Use wireless-rep or wireless-cm2 instead.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Hi.
And I also get around 600mbit/s or even 800 mbit/s on IPIP /IPSEC but for >18 simultaneous connections, on single connection I got only 40-80 mbit/s
When I use 1 connection i got ~50Mbit/s , using 2 connections ~118Mbit/s, 4 connections ~231Mbit/s, so is strictly related whit number of parallel TCP session. This situation looks like one session could be handled only by one processor (without seeing it on CPU graph). CCR 1009 have 9 cores (with HT would give as 18 cores), connection bandwidth grow until they reach 18 parallel sessions (looks like 2 session per Core, or 1 session per core with HT).
All test was made in lab environment between 2 mikrotik without any other devices.
I have separate threat describing this tests and lab environment http://forum.mikrotik.com/viewtopic.php?f=2&t=106857 but still without answer.
I using default settings and encryption - aes-128-cbc (I use property "IPsec Secret" in IPIP tunnel).nz_monkey wrote:
dev246 wrote:
Hi.
Is any chance to improve TCP performance on single session over IPSEC on IPIP/GRE tunnel in this version?
Now is max 40-80 Mbps per session regardless of device model (tested on CCR 1009 and CCR 1036).
What encryption are you running?
We see close to 600mbit/s over EoIP/IPSEC with AES256-AES256-CBC on a CCR1036
And I also get around 600mbit/s or even 800 mbit/s on IPIP /IPSEC but for >18 simultaneous connections, on single connection I got only 40-80 mbit/s
Per cor CPU does not exceed 1-5%, this same with total CPUstrods wotre:
dev246 - Is any of CPU cores loaded 100%? Not total CPU load but load per CPU core.
This isn't sensitive application issue and is fully replicable. Application that i'm using is simply iperf with parm "-P" for setting number of parallel connections (result as this same when i using filezilla for FTP traffic , or simple windows file sharing for SMB traffic)alexjhart wotre:
nz_monkey wrote:
dev246 wrote:
Hi.
Is any chance to improve TCP performance on single session over IPSEC on IPIP/GRE tunnel in this version?
Now is max 40-80 Mbps per session regardless of device model (tested on CCR 1009 and CCR 1036).
What encryption are you running?
We see close to 600mbit/s over EoIP/IPSEC with AES256-AES256-CBC on a CCR1036
I have a long open ticket with Mikrotik on this issue. I'm guessing you are using an application that is sensitive to packet loss and/or you have latency above a few milliseconds.
When I use 1 connection i got ~50Mbit/s , using 2 connections ~118Mbit/s, 4 connections ~231Mbit/s, so is strictly related whit number of parallel TCP session. This situation looks like one session could be handled only by one processor (without seeing it on CPU graph). CCR 1009 have 9 cores (with HT would give as 18 cores), connection bandwidth grow until they reach 18 parallel sessions (looks like 2 session per Core, or 1 session per core with HT).
All test was made in lab environment between 2 mikrotik without any other devices.
I have separate threat describing this tests and lab environment http://forum.mikrotik.com/viewtopic.php?f=2&t=106857 but still without answer.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
So on one hand, I have some sympathy for you, with regard to the criticism you are receiving. I agree that in general practice, you should only install RC software (most of the time) on a production system if a) you absolutely need the features in the RC, and b) you have a reasonably good history with the developer that gives you confidence in the stability of their RC releases. As an example, I wouldn't have any problem putting a pfSense RC release in a production environment if, say, it was the only version that would support the NIC I was using, because PFS has a history of releasing betas that are stable enough for production, and RCs that are more stable than other companies' "release" versions.Each and every release we have to remind two things.
First of all, rc versions are nightly builds and are not completely tested. It means that each version can and must be tested only on devices which you are willing to Netinstall, if it will be necessary. Basically - just for testing.
Secondary, if you want to complain about specific things, then please create specific topic for that. This is 6.36rc version topic which is created for actual software related discussions to help MikroTik staff and our clients to get rid of problems within specific version - 6.36.
Support staff is actually very open minded and is open for suggestions. Send your requests, suggestions and complaints to support team, if problem is related to software in any way. Otherwise, please create separate topics and do not hijack topic within which people are actually tying to help each other.
As for rc version itself - we are not seeing reboot loops with this version in general. It must/should be related to configuration. Please send supout files and/or serial output to support@mikrotik.com so we can research this particular issue.
At the same time, if what you have stated above is correct, I think some of the criticism in the thread is also fair, at least to the extent that you are using "release candidate" in a very different way than most of (at least the English speaking) world. What you have described is often labeled a "snapshot" or "nightly" release. Users downloading a snapshot or nightly have the expectation that things are going to be broken, and that there may be serious regressions between builds. It is absolutely a "caveat emptor" process, where you know you shouldn't flash the build unless you feel comfortable doing low level recovery. On the other hand, a "release candidate" often implies a level of stability that is better than a "beta" release. In other words, when most people see "RC" they have the expectation that as long as no major problems are found, this version is going to be the "final" release - in fact, that the final project might have the same build number, just with the RC dropped.
If you plan on using the structure you outlined above (i.e. builds released with limited or no testing), I would suggest changing the branch name from "release candidate" to "snapshot" or "nightly" to reduce confusion, and bring the terminology more inline with what is used more broadly in the industry.
-

-
florentrivoire
newbie
- Posts: 44
- Joined:
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Agree !If you plan on using the structure you outlined above (i.e. builds released with limited or no testing), I would suggest changing the branch name from "release candidate" to "snapshot" or "nightly" to reduce confusion, and bring the terminology more inline with what is used more broadly in the industry.
The releases that are currently named "RC" should be called "snapshot" or "alpha" or "beta".
Because, between a RC1 and RCx, there should not be anymore new feature or change of behaviour, but only some final bugfix that have not been seen before. If Mikrotik continue to add new feature, new patchs (i'm not talking about bugfixes) between releases, we are still in the development phase, so : snapshot/alpha/beta, but not RC.
NB: just one difference with jwisch : I think "nightly" is not the right term, because the builds currently named "RC" are not automatically build and publish every night, but when developers estimate it's ok, so they are "better" (more consistent, so a little more reliable) than "nightly".
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Version 6.36rc8 has been released.
*) chr - fixed stalling services (introduced in 6.36rc6);
*) dhcp-server - fixed radius framed route addition after reboot on client renew;
*) firewall - added "/interface list" menu which allows to create list of interfaces which can be used as in/out-zone matcher in firewall (CLI only);
*) firewall - added raw table to be able to disable connection tracking on selected packets or drop packets before connection tracking (CLI only);
*) lte - added cinterion pls8 support;
*) lte - improved multiple same model modems identification;
*) route - fixed ospf-v3 crash (introduced in 6.36rc6);
*) traffic-flow - added ipfix support (RFC5101 and RFC5102);
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash.
*) chr - fixed stalling services (introduced in 6.36rc6);
*) dhcp-server - fixed radius framed route addition after reboot on client renew;
*) firewall - added "/interface list" menu which allows to create list of interfaces which can be used as in/out-zone matcher in firewall (CLI only);
*) firewall - added raw table to be able to disable connection tracking on selected packets or drop packets before connection tracking (CLI only);
*) lte - added cinterion pls8 support;
*) lte - improved multiple same model modems identification;
*) route - fixed ospf-v3 crash (introduced in 6.36rc6);
*) traffic-flow - added ipfix support (RFC5101 and RFC5102);
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
*) firewall - added "/interface list" menu which allows to create list of interfaces which can be used as in/out-zone matcher in firewall (CLI only)
Since 6.36rc8 version there is a possibility to create list of interfaces. It works similar as address-list in firewall. Under "/interface list" you can add multiple interfaces and group under list with a common name. Now this list/zone will be available in firewall. In firewall there are new matchers called in-zone and out-zone implemented. Basically, it is the same thing as in-interface and out-interface, but now by using "/interface list" you can select multiple interfaces on one firewall rule.
*) firewall - added raw table to be able to disable connection tracking on selected packets or drop packets before connection tracking (CLI only)
Since 6.36rc8 it is possible to configure firewall rules in a raw table ("/ip firewall raw", "/ipv6 firewall raw"). These rules have two possible chains - prerouting and output which happens before connection tracking in packet flow.
There is action called "notrack". It means that you can select on which packets you want to use connection tracking. It is also possible to drop packets already before connection tracking.
These rules do not have firewall rule matchers that would depend on connection tracking like "connection-state".
Packets which match rules with action "notrack" also are not being fragmented. In past as soon as you loaded connection tracking packets were fragmented. Now even if connection tracking is on "notrack" packets are not being defragmented.
Now in regular firewall, there is new possible connection-state value called "untracked".
Basically, this raw firewall should be used to protect your devices against DDoS attacks.
Since 6.36rc8 version there is a possibility to create list of interfaces. It works similar as address-list in firewall. Under "/interface list" you can add multiple interfaces and group under list with a common name. Now this list/zone will be available in firewall. In firewall there are new matchers called in-zone and out-zone implemented. Basically, it is the same thing as in-interface and out-interface, but now by using "/interface list" you can select multiple interfaces on one firewall rule.
*) firewall - added raw table to be able to disable connection tracking on selected packets or drop packets before connection tracking (CLI only)
Since 6.36rc8 it is possible to configure firewall rules in a raw table ("/ip firewall raw", "/ipv6 firewall raw"). These rules have two possible chains - prerouting and output which happens before connection tracking in packet flow.
There is action called "notrack". It means that you can select on which packets you want to use connection tracking. It is also possible to drop packets already before connection tracking.
These rules do not have firewall rule matchers that would depend on connection tracking like "connection-state".
Packets which match rules with action "notrack" also are not being fragmented. In past as soon as you loaded connection tracking packets were fragmented. Now even if connection tracking is on "notrack" packets are not being defragmented.
Now in regular firewall, there is new possible connection-state value called "untracked".
Basically, this raw firewall should be used to protect your devices against DDoS attacks.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
OMG ... no more doubled/tripled rules for each interface ... OMG*) firewall - added "/interface list" menu which allows to create list of interfaces which can be used as in/out-zone matcher in firewall (CLI only);
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
strods
This is amazing
Thanks you
This is amazing
Thanks you
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Very good firewall additions
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Change of the year!*) firewall - added "/interface list" menu which allows to create list of interfaces which can be used as in/out-zone matcher in firewall (CLI only)
Will this make it's way in to WinBox eventually ?
Last edited by nz_monkey on Thu Apr 28, 2016 3:20 pm, edited 1 time in total.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Can I add a single interface into multiple zones?Under "/interface list" you can add multiple interfaces and group under list with a common name. Now this list/zone will be available in firewall. In firewall there are new matchers called in-zone and out-zone implemented. Basically, it is the same thing as in-interface and out-interface, but now by using "/interface list" you can select multiple interfaces on one firewall rule.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Yes, you can add interface in multiple lists. Of course these both are new features and might contain bugs at the beginning but for now they work for us.
Of course, in future we will implement them in Winbox, but we decided better to start with CLI than just delay whole process and wait for Winbox implementation right away.
Of course, in future we will implement them in Winbox, but we decided better to start with CLI than just delay whole process and wait for Winbox implementation right away.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
OK I have had a play with it, and it appears to work as advertised*) firewall - added "/interface list" menu which allows to create list of interfaces which can be used as in/out-zone matcher in firewall (CLI only)
My feedback is:
- Calling it an "interface list" in one part of RouterOS, and a "zone" in another is confusing. Make it either a "zone" or an "interface list" not both.
- Using "in-zone" and "out-zone" is not consistent with the rest of the firewall rule config on RouterOS. It should be "src-zone" and "dst-zone" or "src-interface-list" and "dst-interface-list"
-

-
florentrivoire
newbie
- Posts: 44
- Joined:
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Before reading this message from nz_monkey, I was going to say the exact same thing :My feedback is:
- Calling it an "interface list" in one part of RouterOS, and a "zone" in another is confusing. Make it either a "zone" or an "interface list" not both.
- Using "in-zone" and "out-zone" is not consistent with the rest of the firewall rule config on RouterOS. It should be "src-zone" and "dst-zone" or "src-interface-list" and "dst-interface-list"
=> please, try to use the same word to describe the same concept (consistency is really important to simplify the configuration)
But, this feature sounds great
Thanks (in advance) Mikrotik !!
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Looks like OSPF is not working properly with rc6 because of this fix. Please use with caution. This change will hopefully fix problems when two OSPFv3 neighbors are stuck in Exchange/ExStart states.*) route - fixed ospf by handling ipv6 encoded prefixes with stray bits;
OSPFv3 still not working with other "system".
Code: Select all
09:18:50 route,ospf,info OSPFv3 neighbor 138.97.60.1: state change from Exchange to 2-Way
09:18:56 route,ospf,info Database Description packet has different options field
09:18:56 route,ospf,info received=11001000 (V6|E|R)
09:18:56 route,ospf,info mine=11001000 (V6|E|R)
09:18:56 route,ospf,info OSPFv3 neighbor 138.97.60.1: state change from Exchange to 2-Way
09:19:01 route,ospf,info OSPFv3 neighbor 138.97.60.1: state change from ExStart to DownI really need this working!
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
I vote for interface list naming convention. Should be in and out as the interfaces are also called in and out. Src and dst is about the addresses in the packet not about interfaces of the router.OK I have had a play with it, and it appears to work as advertised*) firewall - added "/interface list" menu which allows to create list of interfaces which can be used as in/out-zone matcher in firewall (CLI only)very nice.
My feedback is:
- Calling it an "interface list" in one part of RouterOS, and a "zone" in another is confusing. Make it either a "zone" or an "interface list" not both.
- Using "in-zone" and "out-zone" is not consistent with the rest of the firewall rule config on RouterOS. It should be "src-zone" and "dst-zone" or "src-interface-list" and "dst-interface-list"
Please don't implement new word zone. It is not necessary.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Or "interface group" but "interface list" is consistent with the rest of ROS.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
as for "interfaces list" addition - how about adding "ports list" aswell then for similar purposes ?
ie to make bit more streamlined/shortened, transparet and fast config
ie to make bit more streamlined/shortened, transparet and fast config
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
TLDR:
Perhaps it would be more consistent to rename the list to zones and move it under firewall prefix, i.e. /ip firewall zones.
Long story:
The name 'list' is not that bad but the command 'interface list' suggest something different than it should really do in this case (like list of all interface but I might be nitpicking here), 'interface group' is better but on the other hand it might suggest some kind of physical grouping (bonding) rather than abstract classification.
The name 'zone' is quite fitting when you think about implementing firewall - most of you might be familiar with term DMZ, in fact if you type the term in search engine you will get quite a few hits, not only in terms of some abstractions (internet/local/administration/etc zones) but also some real technologies - see http://packetlife.net/blog/2012/jan/30/ ... d-firewall (looks familiar, eh ?). So since at the end of the day it all has to do with the firewall just keep it all there.
Perhaps it would be more consistent to rename the list to zones and move it under firewall prefix, i.e. /ip firewall zones.
Long story:
The name 'list' is not that bad but the command 'interface list' suggest something different than it should really do in this case (like list of all interface but I might be nitpicking here), 'interface group' is better but on the other hand it might suggest some kind of physical grouping (bonding) rather than abstract classification.
The name 'zone' is quite fitting when you think about implementing firewall - most of you might be familiar with term DMZ, in fact if you type the term in search engine you will get quite a few hits, not only in terms of some abstractions (internet/local/administration/etc zones) but also some real technologies - see http://packetlife.net/blog/2012/jan/30/ ... d-firewall (looks familiar, eh ?). So since at the end of the day it all has to do with the firewall just keep it all there.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
I'm guessing they put in under /interfaces because they plan on being able to use that list/group/zone in other areas outside of firewall, like queues. I agree naming should be consistent. Also, regardless of context/naming issues and not being available in winbox yet, I am happy to see this new feature. Long desired feature 
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Does route marking problem fixed?(bug in 6.35.1 and 6.36rc6)Version 6.36rc8 has been released.
*) chr - fixed stalling services (introduced in 6.36rc6);
*) dhcp-server - fixed radius framed route addition after reboot on client renew;
*) firewall - added "/interface list" menu which allows to create list of interfaces which can be used as in/out-zone matcher in firewall (CLI only);
*) firewall - added raw table to be able to disable connection tracking on selected packets or drop packets before connection tracking (CLI only);
*) lte - added cinterion pls8 support;
*) lte - improved multiple same model modems identification;
*) route - fixed ospf-v3 crash (introduced in 6.36rc6);
*) traffic-flow - added ipfix support (RFC5101 and RFC5102);
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
This is great! ...*) firewall - added "/interface list" menu which allows to create list of interfaces which can be used as in/out-zone matcher in firewall (CLI only);
I hope we get "mac address lists" implemented some day ...
JF
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Spoiler alert - alexjhart was correct. This new feature for now is available in firewall only, but will be available also in other places. That is why it is available under "/interface list" not "/ip firewall interfaces-list".
As for naming - we will discuss and decide which name we should use for firewall matcher.
As for naming - we will discuss and decide which name we should use for firewall matcher.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Dear mikrotik developers, add export by SNMP system resource parameters: "write-sect-since-reboot,write-sect-total,bad-blocks,architecture-name,board-name" and all of "/int ethernet monitor" data too.
-

- mrtester
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Awesome. I was just telling to my clients how to create configuration with multiple interfaces and on the next day such improvements. Thank you guys! Great to hear about cinterion lte update. I had few of these modems in my stock. Now I can use them 
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Please tell me we're going to extend that!!!Spoiler alert - alexjhart was correct. This new feature for now is available in firewall only, but will be available also in other places. That is why it is available under "/interface list" not "/ip firewall interfaces-list".
As for naming - we will discuss and decide which name we should use for firewall matcher.
Something like "/ip address-list" which can then be used for other service controls:- /ip services, /snmp community, /ip dns, etc.
That would mean we could use address-lists anywhere, consistently!!!
That would be awesome!
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
After your requests we have renamed matchers in firewall by replacing zone with interface-list.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Why new matcher? It is not posibble to integrate into In-Interface and Out-Interface? Address list should be too integrate into Src-Address and Dst-Address.*) firewall - added "/interface list" menu which allows to create list of interfaces which can be used as in/out-zone matcher in firewall (CLI only);
Is it plan to dynamic adding VPN interfaces (like pptp, l2tp etc.) to interface list (like with adress lists)?
Please add posibility to add leased IP adress to adress list in DHCP client and allow using them (adress lists) in To-Adresses in Firewall NAT (Action).
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Because of greater flexibility ? I can bet that in short time someone finds a "case" when it will be useful.Why new matcher? It is not posibble to integrate into In-Interface and Out-Interface?
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Thank you for the sanityAfter your requests we have renamed matchers in firewall by replacing zone with interface-list.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Version 6.36rc9 has been released.
Changes since previous version:
*) arm - added Dude server support;
*) arm - fixed kernel failure on low memory;
*) discovery - fixed identity discovery (introduced in 6.36rc5 and 6.35.1);
*) firewall - added "/interface list" menu which allows to create list of interfaces which can be used as in/out-zone matcher in firewall (CLI only);
*) log - fixed time zone adjustment (introduced in 6.36rc5 and 6.35.1);
*) lte - added cinterion pls8 support;
*) snmp - fixed snmp timeout (introduced in 6.36rc5 and 6.35.1);
*) ssl - fixed memory leak on ssl connect/disconnect (fetch, ovpn, etc.);
*) trafficflow - allow to filter with interface lists;
*) vrrp - fixed missing vrrp interfaces after upgrade (introduced in 6.36rc5 and 6.35.1);
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash.
Changes since previous version:
*) arm - added Dude server support;
*) arm - fixed kernel failure on low memory;
*) discovery - fixed identity discovery (introduced in 6.36rc5 and 6.35.1);
*) firewall - added "/interface list" menu which allows to create list of interfaces which can be used as in/out-zone matcher in firewall (CLI only);
*) log - fixed time zone adjustment (introduced in 6.36rc5 and 6.35.1);
*) lte - added cinterion pls8 support;
*) snmp - fixed snmp timeout (introduced in 6.36rc5 and 6.35.1);
*) ssl - fixed memory leak on ssl connect/disconnect (fetch, ovpn, etc.);
*) trafficflow - allow to filter with interface lists;
*) vrrp - fixed missing vrrp interfaces after upgrade (introduced in 6.36rc5 and 6.35.1);
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash.
-

-
kometchtech
Member Candidate

- Posts: 194
- Joined:
- Location: Japan
- Contact:
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Issues in RB3011 (unrecognized disk) cannot mount USB flash drive supported?Version 6.36rc9 has been released.
Changes since previous version:
*) arm - added Dude server support;
*) arm - fixed kernel failure on low memory;
*) discovery - fixed identity discovery (introduced in 6.36rc5 and 6.35.1);
*) firewall - added "/interface list" menu which allows to create list of interfaces which can be used as in/out-zone matcher in firewall (CLI only);
*) log - fixed time zone adjustment (introduced in 6.36rc5 and 6.35.1);
*) lte - added cinterion pls8 support;
*) snmp - fixed snmp timeout (introduced in 6.36rc5 and 6.35.1);
*) ssl - fixed memory leak on ssl connect/disconnect (fetch, ovpn, etc.);
*) trafficflow - allow to filter with interface lists;
*) vrrp - fixed missing vrrp interfaces after upgrade (introduced in 6.36rc5 and 6.35.1);
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash.
[Ticket#2016041966000617]
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
IMHO those two fields are basically exclusive, you need one (in-interface=<interface name>) or the other (in-interface-list=<list name>), I can't think about any use for both at the same time (feel free to correct me). To me it looks like unnecessary exposing of low level stuff and I think common in-interface=<interface or list name> would work fine.Because of greater flexibility ? I can bet that in short time someone finds a "case" when it will be useful.Why new matcher? It is not posibble to integrate into In-Interface and Out-Interface?
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Version 6.36rc10 has been released.
Changes since previous version:
*) firewall - added raw table to be able to disable connection tracking on selected packets or drop packets before connection tracking and packet defragmentation (CLI only);
*) firewall - fixed policy routing configurations (introduced in 6.35rc38);
*) queue - fixed interface queue type for ovpn tunnels;
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash.
Changes since previous version:
*) firewall - added raw table to be able to disable connection tracking on selected packets or drop packets before connection tracking and packet defragmentation (CLI only);
*) firewall - fixed policy routing configurations (introduced in 6.35rc38);
*) queue - fixed interface queue type for ovpn tunnels;
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Quick example:IMHO those two fields are basically exclusive, you need one (in-interface=<interface name>) or the other (in-interface-list=<list name>
Deny traffic to 8291 port for all "in-interface-list=<list name>" except the management "in-interface=<interface name>" and the traffic comes from particular "src-address=x.x.x.x"
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Ok, you're right. It sure does look now, like I didn't give it much thought. Sorry.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Keeping them separated would be consistent with the address list implementation style.
Even if in-interface=<interface or list name> would be more to my liking and easier to see in prints and winbox tables. And the same goes for address lists, which are already there.
The presented use case would result in 2 rules, an exception and the regular list evaluation, with not much fuss.
Even if in-interface=<interface or list name> would be more to my liking and easier to see in prints and winbox tables. And the same goes for address lists, which are already there.
The presented use case would result in 2 rules, an exception and the regular list evaluation, with not much fuss.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Don't we have a kind of port list? You can put multiple ports and ranges in the port fields. They are not named lists, but still a list.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
*) arm - added Dude server support;
Pffff, no words for that!
Love you!
Pffff, no words for that!
Love you!
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
i was not tested eariler snapshots, but rc10 seems had broken "export" command so managing config not really possible.
update: my mistake its worked, just differently than in ancient versions. sorry for misleading.
update: my mistake its worked, just differently than in ancient versions. sorry for misleading.
Last edited by Zorro on Sat Apr 30, 2016 5:10 pm, edited 1 time in total.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Since v 6.35.1 there is a bug that causes mikrotik to fail routing based on routing marks.
For example i have a mangle rule that sets routing mark on connections to certain IPs to go via different interface.
This stopped worked since 6.35.1.
Worst part is that if i start packet sniffer on the affected device, all starts to work normally
Downgrading to 6.35 resolves the problem
6.36 rc 10 that claims to resolve problem does not resolve the problem
For example i have a mangle rule that sets routing mark on connections to certain IPs to go via different interface.
This stopped worked since 6.35.1.
Worst part is that if i start packet sniffer on the affected device, all starts to work normally
Downgrading to 6.35 resolves the problem
6.36 rc 10 that claims to resolve problem does not resolve the problem
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
please add cli command something like force-yes=enabled
/system routerboard upgrade force-yes=enabled
/system package upgrade force-yes=enabled
/system package downgrade force-yes=enabled
/system reboot force-yes=enabled
Currently, when using SSH cli scripts, this hangs as the y/N input wait is not catched by most auto-cli scripts...
/system routerboard upgrade force-yes=enabled
/system package upgrade force-yes=enabled
/system package downgrade force-yes=enabled
/system reboot force-yes=enabled
Currently, when using SSH cli scripts, this hangs as the y/N input wait is not catched by most auto-cli scripts...
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
An example to ip firewall raw would be good to see especially for a dDOS case.
Anything to share ?
Anything to share ?
-

- mrtester
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Beone - Just use -:execute script="/system reboot"
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
/lcd export import not work properly
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
jondavy - Please provide an example of export which you are not being able to import afterwards
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
I have one as welljondavy - Please provide an example of export which you are not being able to import afterwards
Code: Select all
#line 1407 + 1408
set cpu-frequency=650MHz init-delay=0s memory-frequency=300MHz \
expected end of command (line 1 column 26)Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
notToNew - This is not LCD configuration but try to delete init-delay configuration and import afterwards. Does device on which you test import support init-delay and actually has firmware version with init-delay support?
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
notToNew - This is not LCD configuration but try to delete init-delay configuration and import afterwards. Does device on which you test import support init-delay and actually has firmware version with init-delay support?
Starting with which firmware version supports init-delay?
RouterBOOT_changelog is at version 3.31 and seems not include all changes in every log version:
http://wiki.mikrotik.com/wiki/RouterBOOT_changelog
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Sorry, I should have added that it's not LCD.notToNew - This is not LCD configuration but try to delete init-delay configuration and import afterwards. Does device on which you test import support init-delay and actually has firmware version with init-delay support?
The Test-router is a simple
Code: Select all
RouterBOARD 952Ui-5ac2nDI see no init-delay support.
I just removed the complete line as I don't need it, but it actually brakes
the import every time. As I understand, this should not be exported by "export compact".
Edit: Sorry, I was wrong!!
executing this in terminal does work, so i don't know whats going wrong with import/export.
Code: Select all
/system routerboard settings> set cpu-frequency=650MHz init-delay=0s memory-frequency=300MHz protected-routerboot=disabledCode: Select all
/system routerboard settings
set cpu-frequency=650MHz init-delay=0s memory-frequency=300MHz \
protected-routerboot=disabled
Code: Select all
expected end of command (line 1 column 26)Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
do not forget for the broken snmp at /system health voltage at 6.35.1 and the not working 'safe mode' under winbox
tq
P
tq
P
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Version 6.36rc11 has been released.
Changes since previous version:
*) bonding - fixed crash on RoMON traffic transmit;
*) bonding - implemented l2mtu value == smallest slave interfaces l2mtu;
*) dude - (changes discussed here: forum.mikrotik.com/viewtopic.php?f=8&t=108083 );
*) ipsec - added dead ph2 reply detection;
*) ipsec - fixed AH with SHA2;
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash.
Changes since previous version:
*) bonding - fixed crash on RoMON traffic transmit;
*) bonding - implemented l2mtu value == smallest slave interfaces l2mtu;
*) dude - (changes discussed here: forum.mikrotik.com/viewtopic.php?f=8&t=108083 );
*) ipsec - added dead ph2 reply detection;
*) ipsec - fixed AH with SHA2;
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Has anyone tried IPFIX over NetFlow?*) traffic-flow - added ipfix support (RFC5101 and RFC5102);
I wonder if the issue described here is fixed using IPFIX
http://forum.mikrotik.com/viewtopic.php ... hilit=flow
https://serverfault.com/questions/73920 ... unter-wrap
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Thank you to the support staff and developers who worked to fix this!
*) bonding - implemented l2mtu value == smallest slave interfaces l2mtu;
-

- mrtester
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Thank you guys. Did not know that my crash was caused by RoMON over bonding  . Now it is not rebooting any more after upgrade to 6.36rc11.
. Now it is not rebooting any more after upgrade to 6.36rc11.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
How exactly this works?MikroTik RouterOS v6.36rc4 is released.
*) tunnel - added option to auto detect tunnel local-address;
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
you not need add local address to an tunnel only the remote addressHow exactly this works?MikroTik RouterOS v6.36rc4 is released.
*) tunnel - added option to auto detect tunnel local-address;
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
I have EoIP/IpSEC and it says I must fill local address.
Now I solved this problem by writing script which is checking every 15 secs if local address changed and makes update but with this new update I dont see any way of going without it.
Now I solved this problem by writing script which is checking every 15 secs if local address changed and makes update but with this new update I dont see any way of going without it.
-

-
tamilmaran
Frequent Visitor

- Posts: 74
- Joined:
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
why wireless FP is discontinued..?
any specific reason
any specific reason
-

-
soyelpulpo
newbie
- Posts: 38
- Joined:
- Location: Lima - Peru
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
6 should be like: cap_abcdef. Where abcdef are the last digits of the cap WiFi mac address.Let´s summarize the feature requests for wireless-rep:Is it possible to show CCQ for each connected client? Or dropped / retransmitted frames percentage?
Is it possible to perform background scan for each remote radio?
(It would be helpful to see connection quality statistics as well as channel usage statistics within CAPSMAN window)+ vendor OUI auto namingshow the username (beside the MAC address) for all connected clients within CAPSMAN window?
)
+ custom names for CAP devices
+ centralized ressource monitoring / statistics ([CPU, RAM, amount of connected clients for each CAP device], total amount of connected devices, frequency band usage, "rogue devices" using the same frequency band or the same SSID per CAP device,...)
My post with CAPsMAN feature requests in the 6.35rc thread:
Requests for CAPsMAN bug fixes and new features, based on my experience with the current RC version:
1. {Nice to have} Add "CCQ", P Throughput" and "Signal to Noise", "Encryption" and "Group Encryption" and "WMM Enabled" fields to CAPsMAN Registration Table.
2. {Feature} Add "Frequency Mode", "WMM Support", "Multicast Buffering", "Keepalive frames", "Adaptive Noise Immunity" and "AMPDU Priorities" to CAPsMAN Config Settings.
3. {BUG} Make "Multicast Helper=full" in CAPsMAN slave interfaces work (now the interfaces stay in default setting).
4. {BUG} Make "Country=no_country_set" work on CAPsMAN 5GHz 802.11ac interfaces (it works on 2.4GHz, but on 5GHz ones it results in "no supported band" error message, regardless of the band and frequency settings).
5. {Feature} Add a scan/freq usage feature in CAPsMAN, with an aption to run in the background. Right now, if one wants to scan, they have to detach the physical interface from the Manager, do the scan and re-attach it. [In the future, use this info to auto-adjust CAP channels and power levels.]
6. {Annoying} Stop CAPsMAN from creating virtual interfaces on CAPs with name "wlanXXX" where XXX is a number which is incremented every time the interface is disabled and re-enabled.
7. {Nice to have} Let the user rename the virtual interfaces on the CAPs, like he/she can do with physical interfaces.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
I can understand that having 3 different wireless packages is not desirable.why wireless FP is discontinued..?
any specific reason
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
cm2 has many improvements and works much better than FP
-

-
autostoper76
Frequent Visitor

- Posts: 72
- Joined:
- Location: Serbia- Belgrade
- Contact:
Re: v6.36rc ARM DUDE Client
The Dude client for ARM , missing
Re: v6.36rc ARM DUDE Client
1) dude server nt clientThe Dude client for ARM , missing
2) separate package can be downloaded here:
http://download2.mikrotik.com/routeros/ ... 11-arm.npk
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Please add CCQ to CapsMAN
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Once again, I second request #6, and was promised about two months ago by support that they would try to work on implementing it if it didn't conflict with anything else. I figured I would wait until the 3 month mark to follow up on their progress. I like the idea to tie the name of the interface to the wifi MAC - that would be even more helpful than just a static number.6 should be like: cap_abcdef. Where abcdef are the last digits of the cap WiFi mac address.Let´s summarize the feature requests for wireless-rep:
+ vendor OUI auto naming
+ custom names for CAP devices
+ centralized ressource monitoring / statistics ([CPU, RAM, amount of connected clients for each CAP device], total amount of connected devices, frequency band usage, "rogue devices" using the same frequency band or the same SSID per CAP device,...)
My post with CAPsMAN feature requests in the 6.35rc thread:
Requests for CAPsMAN bug fixes and new features, based on my experience with the current RC version:
1. {Nice to have} Add "CCQ", P Throughput" and "Signal to Noise", "Encryption" and "Group Encryption" and "WMM Enabled" fields to CAPsMAN Registration Table.
2. {Feature} Add "Frequency Mode", "WMM Support", "Multicast Buffering", "Keepalive frames", "Adaptive Noise Immunity" and "AMPDU Priorities" to CAPsMAN Config Settings.
3. {BUG} Make "Multicast Helper=full" in CAPsMAN slave interfaces work (now the interfaces stay in default setting).
4. {BUG} Make "Country=no_country_set" work on CAPsMAN 5GHz 802.11ac interfaces (it works on 2.4GHz, but on 5GHz ones it results in "no supported band" error message, regardless of the band and frequency settings).
5. {Feature} Add a scan/freq usage feature in CAPsMAN, with an aption to run in the background. Right now, if one wants to scan, they have to detach the physical interface from the Manager, do the scan and re-attach it. [In the future, use this info to auto-adjust CAP channels and power levels.]
6. {Annoying} Stop CAPsMAN from creating virtual interfaces on CAPs with name "wlanXXX" where XXX is a number which is incremented every time the interface is disabled and re-enabled.
7. {Nice to have} Let the user rename the virtual interfaces on the CAPs, like he/she can do with physical interfaces.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
jondavy - Please provide an example of export which you are not being able to import afterwards
/interface bridge
add name=LAN
add name=WAN1
add name=WAN2
add name=WAN3
/lcd
set backlight-timeout=never default-screen=stat-slideshow read-only-mode=yes
/lcd interface
set sfp-sfpplus1 disabled=yes
set sfp1 disabled=yes
set ether1 disabled=yes
set ether2 disabled=yes
set ether3 disabled=yes
set ether4 disabled=yes
set ether5 disabled=yes
set ether6 disabled=yes
set ether7 disabled=yes
set ether8 disabled=yes
add interface=LAN
add interface=WAN1 timeout=5s
add interface=WAN2 timeout=5s
add interface=WAN3 timeout=5s
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
is it possible when using wireless-rep and wlan1 is currently NOT connected, that i can use wlan1-subdevice in AP-mode?
Currently, the virtual subdevice in the repeater-config is always automatically disabled, when wlan1 doesnt get a connection.
This makes the repeater-mode somehow useless for me. Do I miss anything?
I cann't even connect wireless to the Mikrotik-Device to change the config of wlan1 or change the security-profile. If I have to change
it, i do need a cable.
Currently, the virtual subdevice in the repeater-config is always automatically disabled, when wlan1 doesnt get a connection.
This makes the repeater-mode somehow useless for me. Do I miss anything?
I cann't even connect wireless to the Mikrotik-Device to change the config of wlan1 or change the security-profile. If I have to change
it, i do need a cable.
-

-
autostoper76
Frequent Visitor

- Posts: 72
- Joined:
- Location: Serbia- Belgrade
- Contact:
Re: v6.36rc ARM DUDE Client
ok, Dude windows client, please link1) dude server nt clientThe Dude client for ARM , missing
2) separate package can be downloaded here:
http://download2.mikrotik.com/routeros/ ... 11-arm.npk
dude client for windows
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
RC11 on hAp (951Ui-2nD, FW 3.33) shows USB port invalid.
Reverting to 6.35.2 fixes the port issue.
Reverting to 6.35.2 fixes the port issue.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
docmarius - Please send supout file to support@mikrotik.com. Generate file while port is inactive. We can not reproduce such issue. If something is connected then it is active, if we disconnect USB, then it becomes inactive. Connect back and active again.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Version 6.36rc12 has been released.
Changes since previous version:
*) capsman - fixed crash when running over ovpn;
*) dhcp-pd - correct server listing for commands;
*) dude - (changes discussed here: forum.mikrotik.com/viewtopic.php?f=8&t=108083 );
*) fastpath - fixed kernel failure when fastpath handles packet with multicast dst-address;
*) ipsec - don't register temporary ph2 on dead list;
*) ipsec - fixed mode-config export;
*) ipsec - fixed route cache overflow when using ipsec with route cache disabled;
*) sniffer - fixed ipv6 address matching;
*) ssh - add rsa host key size parameter;
*) ssh-keygen - add rsa key size parameter;
*) usb - I-tec U3GLAN3HUB usb hub/ethernet dongle now shows up correctly as ethernet interface;
*) usb - implement possibility to recognize usb hubs/ethernet-dongles;
(if usb hubs/ethernet-dongles shows up as LTE interface with this version - send supout.rif file)
*) wireless-rep - added initial API support for snooper.
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash.
Changes since previous version:
*) capsman - fixed crash when running over ovpn;
*) dhcp-pd - correct server listing for commands;
*) dude - (changes discussed here: forum.mikrotik.com/viewtopic.php?f=8&t=108083 );
*) fastpath - fixed kernel failure when fastpath handles packet with multicast dst-address;
*) ipsec - don't register temporary ph2 on dead list;
*) ipsec - fixed mode-config export;
*) ipsec - fixed route cache overflow when using ipsec with route cache disabled;
*) sniffer - fixed ipv6 address matching;
*) ssh - add rsa host key size parameter;
*) ssh-keygen - add rsa key size parameter;
*) usb - I-tec U3GLAN3HUB usb hub/ethernet dongle now shows up correctly as ethernet interface;
*) usb - implement possibility to recognize usb hubs/ethernet-dongles;
(if usb hubs/ethernet-dongles shows up as LTE interface with this version - send supout.rif file)
*) wireless-rep - added initial API support for snooper.
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Still no band steering and CCQ in CAPsMAN 
If want to use it in a commercial environment, 2.4 and 5G in a same SSID is a basic requirement !!!!
In our China market, we often lost to other competitors, because there is no BAND STEERING. Our customers say Without this feature it is only a "HOME AP"
MT, can provide some way(script, access-list.......) to temporarily solve the Band Steering problem? Thanks a lot.
cisco : band select
Ruckus : holding the transmit beacon
aruba :http://www.arubanetworks.com/techdocs/A ... eering.htm
EnGenius : Band Steering
ASUS : SmartConnect
zyxel : client steering
d-link : http://www.dlink.com/uk/en/technology/band-steering
ubnt : https://community.ubnt.com/t5/UniFi-Wir ... -p/1429904
tp-link : http://www.tp-link.com/res/down/doc/Aur ... asheet.pdf
If want to use it in a commercial environment, 2.4 and 5G in a same SSID is a basic requirement !!!!
In our China market, we often lost to other competitors, because there is no BAND STEERING. Our customers say Without this feature it is only a "HOME AP"
MT, can provide some way(script, access-list.......) to temporarily solve the Band Steering problem? Thanks a lot.
cisco : band select
Ruckus : holding the transmit beacon
aruba :http://www.arubanetworks.com/techdocs/A ... eering.htm
EnGenius : Band Steering
ASUS : SmartConnect
zyxel : client steering
d-link : http://www.dlink.com/uk/en/technology/band-steering
ubnt : https://community.ubnt.com/t5/UniFi-Wir ... -p/1429904
tp-link : http://www.tp-link.com/res/down/doc/Aur ... asheet.pdf
Last edited by m94646602 on Thu May 12, 2016 12:19 pm, edited 4 times in total.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
really I'm just not using it and installing the companies that attend for lack of decent monitoringStill no band steering and CCQ in CAPsMAN
If want to use it in a commercial environment, 2.4 and 5G in a same SSID is a basic requirement !!!!
CCQ is an essential basic thing
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Done Ticket#2016051166000808.docmarius - Please send supout file to support@mikrotik.com. Generate file while port is inactive. We can not reproduce such issue. If something is connected then it is active, if we disconnect USB, then it becomes inactive. Connect back and active again.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Is it possible add support for ASIX USB3 Ethernet?Version 6.36rc12 has been released.
...
*) usb - implement possibility to recognize usb hubs/ethernet-dongles;
(if usb hubs/ethernet-dongles shows up as LTE interface with this version - send supout.rif file)
...
Chip: AX88179
VID: 0x0b95
PID: 0x1790
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
When OSPFv3 will be fixed? Still cant use it with different manufacter!
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
OSPFv3 is running fine with H3C/Comware 5 (HP A series switches) here.When OSPFv3 will be fixed? Still cant use it with different manufacter!
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
I trying to run this with an EdgeRouter Pro.OSPFv3 is running fine with H3C/Comware 5 (HP A series switches) here.When OSPFv3 will be fixed? Still cant use it with different manufacter!
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
MikroTik RouterOS 6.36rc13 version has been released!
What's new in 6.36rc13 (2016-May-17 12:20):
*) dude - (changes discussed here: forum.mikrotik.com/viewtopic.php?f=8&t=108083 );
*) dhcpv6 client - fixed ia lifetime validation when it is set by dhcpv6 client;
*) health - fixed incorrect voltage after reboot on RB2011UAS;
*) health - fixed broken factory voltage calibration data for some hAP ac boards;
*) log - added whole scep certificate chain print;
*) lte - fix crash on SXT LTE while resetting card while at high traffic;
*) lte - added allow-roaming option for Huawei MU709, ME909s, ME909u devices;
*) lte - changed driver loading for class 2 usb rndis devices;
*) userman - use ipnpb.paypal.com for payment verification;
http://www.mikrotik.com/download
What's new in 6.36rc13 (2016-May-17 12:20):
*) dude - (changes discussed here: forum.mikrotik.com/viewtopic.php?f=8&t=108083 );
*) dhcpv6 client - fixed ia lifetime validation when it is set by dhcpv6 client;
*) health - fixed incorrect voltage after reboot on RB2011UAS;
*) health - fixed broken factory voltage calibration data for some hAP ac boards;
*) log - added whole scep certificate chain print;
*) lte - fix crash on SXT LTE while resetting card while at high traffic;
*) lte - added allow-roaming option for Huawei MU709, ME909s, ME909u devices;
*) lte - changed driver loading for class 2 usb rndis devices;
*) userman - use ipnpb.paypal.com for payment verification;
http://www.mikrotik.com/download
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Is there a possibility to log PSU failures on CCR in future versions?
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
and what the problem with that today ?Is there a possibility to log PSU failures on CCR in future versions?
you just need: bump "UPS" part of logging to more verbose/obvious levels than non-existent/disabled default to say "disk", "echo" or "remote" variations of. and then use that logged infor for relevant purposes.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Are you sure, UPS will log PSU failures? (on CCR with redundant PSU).
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
+1Since v 6.35.1 there is a bug that causes mikrotik to fail routing based on routing marks.
For example i have a mangle rule that sets routing mark on connections to certain IPs to go via different interface.
This stopped worked since 6.35.1.
Worst part is that if i start packet sniffer on the affected device, all starts to work normally
Downgrading to 6.35 resolves the problem
6.36 rc 10 that claims to resolve problem does not resolve the problem
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Hello! Add in the possibility CAPsMAN - Access List to add one client for several interfaces Cap. Thank you!
В мене дві мережі - корпоративна - фізичний інтерфейс і гостьова - віртуальний інтерфейс. Підключено 8 AP. Доступ до корпоративної мережі зробив через прив'язку до фізичного адреса клієнта. І потрібно прописувати
caps-man access-list add mac-address=01:01:01:01:01:01 action=accept interface=IT-1
caps-man access-list add mac-address=01:01:01:01:01:01 action=accept interface=IT-2
caps-man access-list add mac-address=01:01:01:01:01:01 action=accept interface=IT-3
caps-man access-list add mac-address=01:01:01:01:01:01 action=accept interface=IT-4
....
and so 8 times for each client
В мене дві мережі - корпоративна - фізичний інтерфейс і гостьова - віртуальний інтерфейс. Підключено 8 AP. Доступ до корпоративної мережі зробив через прив'язку до фізичного адреса клієнта. І потрібно прописувати
caps-man access-list add mac-address=01:01:01:01:01:01 action=accept interface=IT-1
caps-man access-list add mac-address=01:01:01:01:01:01 action=accept interface=IT-2
caps-man access-list add mac-address=01:01:01:01:01:01 action=accept interface=IT-3
caps-man access-list add mac-address=01:01:01:01:01:01 action=accept interface=IT-4
....
and so 8 times for each client
Last edited by Nekromans on Fri May 20, 2016 12:15 pm, edited 1 time in total.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
You want to have multiple drop-down options for the access list interface, so you could select multiple cap interfaces?Hello! Add in the possibility CAPsMAN - Access List to add one client for several interfaces Cap. Thank you!
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Yes!
Or the possibility of combining a group of several interfaces
Or the possibility of combining a group of several interfaces
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
and why it shouldn't ?Are you sure, UPS will log PSU failures? (on CCR with redundant PSU).

Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Because PSU has nothing to do with UPS?
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
screenshot above given "just as reference", explanation how to create additionl(to deafult/pre-created by ROS deployment itself)logging rules/policies.Because PSU has nothing to do with UPS?
but you may be right, i cannot reproduce PSU failures in logs ("Critical", "Warning" and "system" are checked)
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Very interesting! Is there a reason that you have not done a PPC build of The Dude? There are PPC RouterBoards that outclass the RB3011.*) arm - added Dude server support;
-- Nathan
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Version 6.36rc16 has been released.
Changes since previous version:
*) dude - (changes discussed here: forum.mikrotik.com/viewtopic.php?f=8&t=108083 );
*) address - allow multiple euqla ip addresses to be added if neither or only one is enabled;
*) bonding - fixed 802.3ad load balancing mode over tunnels ;
*) certificate - display issuer and subject on check failure;
*) cloud - fixed export order;
*) dhcpv6-server - fixed binding last-seen update;
*) e-mail - removed subject and body length limit;
*) ethernet - fixed memory leak when setting interface without changing configuration;
*) firewall - added "/interface list" menu which allows to create list of interfaces which can be used as in/out-interface-list matcher in firewall;
*) firewall - added pre-connection tracking filter - "raw" table, that allow to protect connection-tracking from unnecessary traffic;
*) firewall - allow to add domain name to address-lists (dynamic entries for resolved addresses will be added to specified list);
*) ipsec - fixed checks before accessing ph1 nat options;
*) ipsec - store udp encapsulation type in proposal;
*) ovpn - enable perfect forwarding secrecy support by default;
*) ovpn - fixed compatibility with OpenVPN 2.3.11;
*) rb3011 - fixed port flapping on ether6-ether10;
*) snmp - fixed get function for snmp>=v2 when oid does not exist;
*) winbox - report correctly dude users in active users list;
*) wireless-rep - treat missing SSID element as hidden SSID;
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash.
Changes since previous version:
*) dude - (changes discussed here: forum.mikrotik.com/viewtopic.php?f=8&t=108083 );
*) address - allow multiple euqla ip addresses to be added if neither or only one is enabled;
*) bonding - fixed 802.3ad load balancing mode over tunnels ;
*) certificate - display issuer and subject on check failure;
*) cloud - fixed export order;
*) dhcpv6-server - fixed binding last-seen update;
*) e-mail - removed subject and body length limit;
*) ethernet - fixed memory leak when setting interface without changing configuration;
*) firewall - added "/interface list" menu which allows to create list of interfaces which can be used as in/out-interface-list matcher in firewall;
*) firewall - added pre-connection tracking filter - "raw" table, that allow to protect connection-tracking from unnecessary traffic;
*) firewall - allow to add domain name to address-lists (dynamic entries for resolved addresses will be added to specified list);
*) ipsec - fixed checks before accessing ph1 nat options;
*) ipsec - store udp encapsulation type in proposal;
*) ovpn - enable perfect forwarding secrecy support by default;
*) ovpn - fixed compatibility with OpenVPN 2.3.11;
*) rb3011 - fixed port flapping on ether6-ether10;
*) snmp - fixed get function for snmp>=v2 when oid does not exist;
*) winbox - report correctly dude users in active users list;
*) wireless-rep - treat missing SSID element as hidden SSID;
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Nice!!!Version 6.36rc16 has been released.
*) firewall - allow to add domain name to address-lists (dynamic entries for resolved addresses will be added to specified list);
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Nice!!!Version 6.36rc16 has been released.
*) firewall - allow to add domain name to address-lists (dynamic entries for resolved addresses will be added to specified list);
How often is updated?
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
So which is faster in terms of throughput - fasttrack or no tracking at all?*) firewall - added pre-connection tracking filter - "raw" table, that allow to protect connection-tracking from unnecessary traffic;
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
My question exactlyNice!!!Version 6.36rc16 has been released.
*) firewall - allow to add domain name to address-lists (dynamic entries for resolved addresses will be added to specified list);
How often is updated?
-

-
juliobrito
just joined
- Posts: 8
- Joined:
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Regards,
Please, remember that all Mikrotik users need the implementation of PEAP-MSCHAPv2 Wireless Station Mode. We have more that 7 years waiting for it option.
Please, remember that all Mikrotik users need the implementation of PEAP-MSCHAPv2 Wireless Station Mode. We have more that 7 years waiting for it option.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
I am afraid that not all users need it. Please, be so kind and ask just for yourself and don't take others as your hostages.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
That's what I would like to know as well.My question exactly
Nice!!!
How often is updated?
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
I will try to answer the question myself: I think the address is resolved at boot and when DNS TTL reaches 0 and is renew in cache.That's what I would like to know as well.My question exactly
How often is updated?
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Test it yourself? That's crazy talk!I will try to answer the question myself: I think the address is resolved at boot and when DNS TTL reaches 0 and is renew in cache.That's what I would like to know as well.
My question exactly
Good job so far Mikrotik.
Feature request: put the timeout remaining calculated from TTL in the timeout column
Thanks @tomaskir for testing with me
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Thank you grusu. You managed to answer before us and answer is completely correct.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Until now I have used a script to resolve the dynamic IP address from where I manage routers. Now it is much easier.Thank you grusu. You managed to answer before us and answer is completely correct.
Thank you!
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Regarding:
This works in Firewall/Filter but when you select a valid Interface-List for "In. Interface List" or "Out. Interface List" on a Firewall/NAT or Firewall/Mangle policy, it resets to "unknown" a few seconds after clicking OK/Apply.
Code: Select all
*) firewall - added "/interface list" menu which allows to create list of interfaces which can be used as in/out-interface-list matcher in firewall;Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Version 6.36rc16 has been released.
..[CUT]..
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash.
On two RB3011 upgraded to 6.36rc16 I've lost USB/Disk (present in system/resources/usb ..but not in system/disk).
Someone can confirm ?
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
nz_monkey - what type of interfaces do you add there?
bajodel - please generate supout file on device and send it to support@mikrotik.com
bajodel - please generate supout file on device and send it to support@mikrotik.com
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
OK ..to give more help I've netinstalled one of the RB3011 with 6.36rc16...[cut].. bajodel - please generate supout file on device and send it to support@mikrotik.com
Problem persist, so supout sent to support@mikrotik.com with screenshot and details.
>> [Ticket#2016052566000541]
Thank you..
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
frankly ROS also need suuport of EAPoL rather than just EAP/PEAP over Wifi or other 802.1x flavors/portions.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Why structure of "/interface list" menu is different from "/address list" in WinBox? Why they haven't same logic?*) firewall - added "/interface list" menu which allows to create list of interfaces which can be used as in/out-interface-list matcher in firewall;
Please add posibilities for auto adding dynamic (ppp) interfaces to selected interface list when they connect (start running).
Please add same logic for IP addresses (address lists) when dhcp client leases IP.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Hi Strodsnz_monkey - what type of interfaces do you add there?
bajodel - please generate supout file on device and send it to support@mikrotik.com
Just vlan sub interfaces. Nothing complicated.
My testing was on a RB2011
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
I wondered exactly the same thing!Why structure of "/interface list" menu is different from "/address list" in WinBox? Why they haven't same logic?.
Workflow inconsistency = Bad
-

-
JimmyNyholm
Member Candidate

- Posts: 248
- Joined:
- Location: Sweden
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
The Only viable sullution should be the TTL and Refresh values specified on each individual record but then again a confirmation on that one would be very much apprechiated as the wiki seldom states new features until very much later.My question exactly
Nice!!!
How often is updated?
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
It has been confirmed already. Check a few posts above.The Only viable sullution should be the TTL and Refresh values specified on each individual record but then again a confirmation on that one would be very much apprechiated as the wiki seldom states new features until very much later.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
We talked about this earlier in the thread. They are planning more for this than the current firewall use. Ideally, they consolidate all in the future to use the same logic, but one came long ago and has had less intended scope than the new one.I wondered exactly the same thing!Why structure of "/interface list" menu is different from "/address list" in WinBox? Why they haven't same logic?.
Workflow inconsistency = Bad
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
As we have explained already earlier in this post and others have told - interface list is not a firewall feature. It is already supported not only in firewall but also on traffic flow.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Version 6.36rc19 has been released.
Changes since previous version:
*) dude - (changes discussed here: forum.mikrotik.com/viewtopic.php?f=8&t=108083 );
*) certificate - added automatic scep renewal delay after startup to avoid all requests accessing CA at the same time;
*) certificate - cancel pending renew when certificate becomes valid after date change;
*) certificate - force scep renewal on system clock updates;
*) clock - save current time to configuration once per day even if there are no time zone adjustments pending;
*) console - show message time in echo log messages;
*) defconf - changed channel extension to 20/40/80mhz for all ac boards;
*) fetch - support tls host name extension;
*) kernel - fixed possible kernel deadlock when Sierra USB mode is being used;
*) rb3011 - improved performance on high cpu usage;
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash.
Changes since previous version:
*) dude - (changes discussed here: forum.mikrotik.com/viewtopic.php?f=8&t=108083 );
*) certificate - added automatic scep renewal delay after startup to avoid all requests accessing CA at the same time;
*) certificate - cancel pending renew when certificate becomes valid after date change;
*) certificate - force scep renewal on system clock updates;
*) clock - save current time to configuration once per day even if there are no time zone adjustments pending;
*) console - show message time in echo log messages;
*) defconf - changed channel extension to 20/40/80mhz for all ac boards;
*) fetch - support tls host name extension;
*) kernel - fixed possible kernel deadlock when Sierra USB mode is being used;
*) rb3011 - improved performance on high cpu usage;
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Hi Strods, AlexAs we have explained already earlier in this post and others have told - interface list is not a firewall feature. It is already supported not only in firewall but also on traffic flow.
I think my comment has been mis-understood.
What I was saying is that the workflow of the new feature is NOT in line with other "similar" features. e.g.
To add an interface to a new list
1. Click on Interface-List tab
2. Click on "Lists" in tab control pane (new dialogue will appear)
3. In "Interface Lists" dialogue box, click on +
4. Enter List Name
5. Click OK
6. Return to "Interface-List" tab
7. Click on + (yet another dialogue box appears)
8. in "New Interface List Member" tab, select a list, and select a interface.
9. Click OK
To add an address to a new list:
1. Click on Address-List tab
2. Click +
3. Enter List name
4. Enter IP address
5. Click OK
The "flow" taken to add a new "Interface-List" is much longer, and is different from other similar features in RouterOS.
In my opinion, the new feature should be changed to match the existing features. Or the existing features workflow should be updated to match the new features.
Im not saying "Combine Interface-Lists and Address-Lists" I am saying, make the workflow's consistent!
Please don't make this a repeat of the RoMON / Mac-Server / IP Neighbor workflow mess
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Workflow is consistent to other interface related features. For example you first add bridge,mesh and only then add ports. The same is with list, you first add list and then interfaces to the list.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
But there is "Bridge" tab where the bridges are added and the "Ports" tab where ports are added to bridges.
There is no "Bridge" button on "Ports" tab.
There is no "Bridge" button on "Ports" tab.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Will you please consider fixing the bug where if a wireless interface is set to 2GHz-G/N then all subsequent config changes to this interface done in winbox fail with the message "not supported" and so all config has to be done using the CLI? Changing the interface to any other mode fixes it.
-

-
andersonlich
Frequent Visitor

- Posts: 55
- Joined:
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Can we set from 5 sec to 5 minThat's what I would like to know as well.My question exactly
How often is updated?
?
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Hello,
I just gave IPFIX a try on version 6.36rc19 on a RB2011UAS and it seems that it exports the flows with 'random' timestamps in the year 1970.
The time on the RB2011 is correct (double checked).
Those netflow packets where exported to wireshark by mikrotik every 2 seconds.
The full capture:
Reverting back to NetFlow v9 the timestamp fields contain the right date/time.
Those bad timestamps cause software like nfacct/pmacct to insert bad data to the database.
Also it discards many flows due to bad sequence number (although checking the capture the sequence numbers seem ok. Maybe nfacct consults the timestamp along with the sequence number to detect if a received flow is valid)
Here's my traffic flow configuration:
[Ticket#2016052966000463]
I just gave IPFIX a try on version 6.36rc19 on a RB2011UAS and it seems that it exports the flows with 'random' timestamps in the year 1970.
The time on the RB2011 is correct (double checked).
Code: Select all
Timestamp: Jul 5, 1970 11:05:20.000000000 GTB Daylight Time
Timestamp: Jul 5, 1970 11:38:40.000000000 GTB Daylight Time
Timestamp: Jul 5, 1970 12:12:00.000000000 GTB Daylight TimeThe full capture:
Code: Select all
No. Time Source Destination Protocol Length Info
383778 748.591451000 10.10.153.218 10.26.35.34 CFLOW 542 IPFIX partial flow (500/5 bytes)
Frame 383778: 542 bytes on wire (4336 bits), 542 bytes captured (4336 bits) on interface 0
Ethernet II, Src: Routerbo_XX:XX:XX (XX:XX:XX:XX:XX:XX), Dst: YY:YY:YY:YY:YY:YY (YY:YY:YY:YY:YY:YY)
Internet Protocol Version 4, Src: 10.10.153.218 (10.10.153.218), Dst: 10.26.35.34 (10.26.35.34)
User Datagram Protocol, Src Port: 2055 (2055), Dst Port: 2055 (2055)
Cisco NetFlow/IPFIX
Version: 10
Length: 5
Timestamp: Jul 5, 1970 11:05:20.000000000 GTB Daylight Time
ExportTime: 16013120
FlowSequence: 384
Observation Domain Id: 0
Set 1
FlowSet Id: (Data) (258)
FlowSet Length: 484
Flow 1
IPVersion: 04
[Duration: 0.000000000 seconds]
StartTime: 16010.600000000 seconds
EndTime: 16010.600000000 seconds
Packets: 3
Octets: 192
SrcPort: 2000
DstPort: 39216
InputInt: 4
OutputInt: 0
Protocol: 6
IP ToS: 0x00
TCP Flags: 0x18
Destination Mac Address: Routerbo_ZZ:ZZ:ZZ (ZZ:ZZ:ZZ:ZZ:ZZ:ZZ)
Post Source Mac Address: 00:00:00_00:00:00 (00:00:00:00:00:00)
SrcAddr: 10.10.153.217 (10.10.153.217)
DstAddr: 10.10.153.218 (10.10.153.218)
NextHop: 10.10.153.218 (10.10.153.218)
SrcMask: 0
DstMask: 0
IP TTL: 64
IsMulticast: 0
IP Header Length: 5
IP Total Length: 64
UDP Length: 0
TCP Sequence Number: 1439408172
TCP Acknowledgement Number: 786858282
TCP Windows Size: 905
IGMP Type: 0
IPv4 ICMP Type: 0
IPv4 ICMP Code: 0
Post NAT Source IPv4 Address: 10.10.153.217 (10.10.153.217)
Post NAT Destination IPv4 Address: 10.10.153.218 (10.10.153.218)
Post NAPT Source Transport Port: 0
Post NAPT Destination Transport Port: 0
Flow 2
IPVersion: 04
[Duration: 0.000000000 seconds]
StartTime: 16011.120000000 seconds
EndTime: 16011.120000000 seconds
Packets: 2
Octets: 1056
SrcPort: 2055
DstPort: 2055
InputInt: 0
OutputInt: 4
Protocol: 17
IP ToS: 0x00
TCP Flags: 0x00
Destination Mac Address: 00:00:00_00:00:00 (00:00:00:00:00:00)
Post Source Mac Address: Routerbo_ZZ:ZZ:ZZ (ZZ:ZZ:ZZ:ZZ:ZZ:ZZ)
SrcAddr: 10.10.153.218 (10.10.153.218)
DstAddr: 10.26.35.34 (10.26.35.34)
NextHop: 10.10.153.217 (10.10.153.217)
SrcMask: 0
DstMask: 0
IP TTL: 255
IsMulticast: 0
IP Header Length: 5
IP Total Length: 528
UDP Length: 508
TCP Sequence Number: 0
TCP Acknowledgement Number: 0
TCP Windows Size: 0
IGMP Type: 0
IPv4 ICMP Type: 0
IPv4 ICMP Code: 0
Post NAT Source IPv4 Address: 10.10.153.218 (10.10.153.218)
Post NAT Destination IPv4 Address: 10.26.35.34 (10.26.35.34)
Post NAPT Source Transport Port: 0
Post NAPT Destination Transport Port: 0
Flow 3
IPVersion: 04
[Duration: 0.000000000 seconds]
StartTime: 16011.120000000 seconds
EndTime: 16011.120000000 seconds
Packets: 2
Octets: 800
SrcPort: 2055
DstPort: 2055
InputInt: 0
OutputInt: 4
Protocol: 17
IP ToS: 0x00
TCP Flags: 0x00
Destination Mac Address: 00:00:00_00:00:00 (00:00:00:00:00:00)
Post Source Mac Address: Routerbo_ZZ:ZZ:ZZ (ZZ:ZZ:ZZ:ZZ:ZZ:ZZ)
SrcAddr: 10.10.153.218 (10.10.153.218)
DstAddr: 10.69.110.21 (10.69.110.21)
NextHop: 10.10.153.217 (10.10.153.217)
SrcMask: 0
DstMask: 0
IP TTL: 255
IsMulticast: 0
IP Header Length: 5
IP Total Length: 400
UDP Length: 380
TCP Sequence Number: 0
TCP Acknowledgement Number: 0
TCP Windows Size: 0
IGMP Type: 0
IPv4 ICMP Type: 0
IPv4 ICMP Code: 0
Post NAT Source IPv4 Address: 10.10.153.218 (10.10.153.218)
Post NAT Destination IPv4 Address: 10.69.110.21 (10.69.110.21)
Post NAPT Source Transport Port: 0
Post NAPT Destination Transport Port: 0
Flow 4
IPVersion: 04
[Duration: 0.000000000 seconds]
StartTime: 16012.000000000 seconds
EndTime: 16012.000000000 seconds
Packets: 3
Octets: 194
SrcPort: 33353
DstPort: 179
InputInt: 0
OutputInt: 4
Protocol: 6
IP ToS: 0xc0
TCP Flags: 0x18
Destination Mac Address: 00:00:00_00:00:00 (00:00:00:00:00:00)
Post Source Mac Address: Routerbo_ZZ:ZZ:ZZ (ZZ:ZZ:ZZ:ZZ:ZZ:ZZ)
SrcAddr: 10.10.153.218 (10.10.153.218)
DstAddr: 10.10.153.217 (10.10.153.217)
NextHop: 10.10.153.217 (10.10.153.217)
SrcMask: 0
DstMask: 0
IP TTL: 64
IsMulticast: 0
IP Header Length: 5
IP Total Length: 71
UDP Length: 0
TCP Sequence Number: 131047850
TCP Acknowledgement Number: 1912585720
TCP Windows Size: 1016
IGMP Type: 0
IPv4 ICMP Type: 0
IPv4 ICMP Code: 0
Post NAT Source IPv4 Address: 10.10.153.218 (10.10.153.218)
Post NAT Destination IPv4 Address: 10.10.153.217 (10.10.153.217)
Post NAPT Source Transport Port: 0
Post NAPT Destination Transport Port: 0
Flow 5
IPVersion: 04
[Duration: 0.000000000 seconds]
StartTime: 16012.000000000 seconds
EndTime: 16012.000000000 seconds
Packets: 3
Octets: 175
SrcPort: 179
DstPort: 33353
InputInt: 4
OutputInt: 0
Protocol: 6
IP ToS: 0xc0
TCP Flags: 0x10
Destination Mac Address: Routerbo_ZZ:ZZ:ZZ (ZZ:ZZ:ZZ:ZZ:ZZ:ZZ)
Post Source Mac Address: 00:00:00_00:00:00 (00:00:00:00:00:00)
SrcAddr: 10.10.153.217 (10.10.153.217)
DstAddr: 10.10.153.218 (10.10.153.218)
NextHop: 10.10.153.218 (10.10.153.218)
SrcMask: 0
DstMask: 0
IP TTL: 64
IsMulticast: 0
IP Header Length: 5
IP Total Length: 52
UDP Length: 0
TCP Sequence Number: 1912585720
TCP Acknowledgement Number: 131047869
TCP Windows Size: 1082
IGMP Type: 0
IPv4 ICMP Type: 0
IPv4 ICMP Code: 0
Post NAT Source IPv4 Address: 10.10.153.217 (10.10.153.217)
Post NAT Destination IPv4 Address: 10.10.153.218 (10.10.153.218)
Post NAPT Source Transport Port: 0
Post NAPT Destination Transport Port: 0
No. Time Source Destination Protocol Length Info
384733 750.593356000 10.10.153.218 10.26.35.34 CFLOW 638 IPFIX partial flow (596/6 bytes)
Frame 384733: 638 bytes on wire (5104 bits), 638 bytes captured (5104 bits) on interface 0
Ethernet II, Src: Routerbo_XX:XX:XX (XX:XX:XX:XX:XX:XX), Dst: YY:YY:YY:YY:YY:YY (YY:YY:YY:YY:YY:YY)
Internet Protocol Version 4, Src: 10.10.153.218 (10.10.153.218), Dst: 10.26.35.34 (10.26.35.34)
User Datagram Protocol, Src Port: 2055 (2055), Dst Port: 2055 (2055)
Cisco NetFlow/IPFIX
Version: 10
Length: 6
Timestamp: Jul 5, 1970 11:38:40.000000000 GTB Daylight Time
ExportTime: 16015120
FlowSequence: 385
Observation Domain Id: 0
Set 1
FlowSet Id: (Data) (258)
FlowSet Length: 580
Flow 1
IPVersion: 04
[Duration: 1.820000000 seconds]
StartTime: 16011.220000000 seconds
EndTime: 16013.040000000 seconds
Packets: 3
Octets: 288
SrcPort: 0
DstPort: 0
InputInt: 4
OutputInt: 0
Protocol: 1
IP ToS: 0x00
TCP Flags: 0x00
Destination Mac Address: Routerbo_ZZ:ZZ:ZZ (ZZ:ZZ:ZZ:ZZ:ZZ:ZZ)
Post Source Mac Address: 00:00:00_00:00:00 (00:00:00:00:00:00)
SrcAddr: 10.69.110.16 (10.69.110.16)
DstAddr: 10.10.153.218 (10.10.153.218)
NextHop: 10.10.153.218 (10.10.153.218)
SrcMask: 0
DstMask: 0
IP TTL: 63
IsMulticast: 0
IP Header Length: 5
IP Total Length: 96
UDP Length: 0
TCP Sequence Number: 0
TCP Acknowledgement Number: 0
TCP Windows Size: 0
IGMP Type: 0
IPv4 ICMP Type: 8
IPv4 ICMP Code: 0
Post NAT Source IPv4 Address: 10.69.110.16 (10.69.110.16)
Post NAT Destination IPv4 Address: 10.10.153.218 (10.10.153.218)
Post NAPT Source Transport Port: 0
Post NAPT Destination Transport Port: 0
Flow 2
IPVersion: 04
[Duration: 1.820000000 seconds]
StartTime: 16011.220000000 seconds
EndTime: 16013.040000000 seconds
Packets: 3
Octets: 288
SrcPort: 0
DstPort: 0
InputInt: 0
OutputInt: 4
Protocol: 1
IP ToS: 0x00
TCP Flags: 0x00
Destination Mac Address: 00:00:00_00:00:00 (00:00:00:00:00:00)
Post Source Mac Address: Routerbo_ZZ:ZZ:ZZ (ZZ:ZZ:ZZ:ZZ:ZZ:ZZ)
SrcAddr: 10.10.153.218 (10.10.153.218)
DstAddr: 10.69.110.16 (10.69.110.16)
NextHop: 10.10.153.217 (10.10.153.217)
SrcMask: 0
DstMask: 0
IP TTL: 64
IsMulticast: 0
IP Header Length: 5
IP Total Length: 96
UDP Length: 0
TCP Sequence Number: 0
TCP Acknowledgement Number: 0
TCP Windows Size: 0
IGMP Type: 0
IPv4 ICMP Type: 0
IPv4 ICMP Code: 0
Post NAT Source IPv4 Address: 10.10.153.218 (10.10.153.218)
Post NAT Destination IPv4 Address: 10.69.110.16 (10.69.110.16)
Post NAPT Source Transport Port: 0
Post NAPT Destination Transport Port: 0
Flow 3
IPVersion: 04
[Duration: 0.000000000 seconds]
StartTime: 16013.120000000 seconds
EndTime: 16013.120000000 seconds
Packets: 2
Octets: 1056
SrcPort: 2055
DstPort: 2055
InputInt: 0
OutputInt: 4
Protocol: 17
IP ToS: 0x00
TCP Flags: 0x00
Destination Mac Address: 00:00:00_00:00:00 (00:00:00:00:00:00)
Post Source Mac Address: Routerbo_ZZ:ZZ:ZZ (ZZ:ZZ:ZZ:ZZ:ZZ:ZZ)
SrcAddr: 10.10.153.218 (10.10.153.218)
DstAddr: 10.26.35.34 (10.26.35.34)
NextHop: 10.10.153.217 (10.10.153.217)
SrcMask: 0
DstMask: 0
IP TTL: 255
IsMulticast: 0
IP Header Length: 5
IP Total Length: 528
UDP Length: 508
TCP Sequence Number: 0
TCP Acknowledgement Number: 0
TCP Windows Size: 0
IGMP Type: 0
IPv4 ICMP Type: 0
IPv4 ICMP Code: 0
Post NAT Source IPv4 Address: 10.10.153.218 (10.10.153.218)
Post NAT Destination IPv4 Address: 10.26.35.34 (10.26.35.34)
Post NAPT Source Transport Port: 0
Post NAPT Destination Transport Port: 0
Flow 4
IPVersion: 04
[Duration: 0.000000000 seconds]
StartTime: 16013.120000000 seconds
EndTime: 16013.120000000 seconds
Packets: 2
Octets: 800
SrcPort: 2055
DstPort: 2055
InputInt: 0
OutputInt: 4
Protocol: 17
IP ToS: 0x00
TCP Flags: 0x00
Destination Mac Address: 00:00:00_00:00:00 (00:00:00:00:00:00)
Post Source Mac Address: Routerbo_ZZ:ZZ:ZZ (ZZ:ZZ:ZZ:ZZ:ZZ:ZZ)
SrcAddr: 10.10.153.218 (10.10.153.218)
DstAddr: 10.69.110.21 (10.69.110.21)
NextHop: 10.10.153.217 (10.10.153.217)
SrcMask: 0
DstMask: 0
IP TTL: 255
IsMulticast: 0
IP Header Length: 5
IP Total Length: 400
UDP Length: 380
TCP Sequence Number: 0
TCP Acknowledgement Number: 0
TCP Windows Size: 0
IGMP Type: 0
IPv4 ICMP Type: 0
IPv4 ICMP Code: 0
Post NAT Source IPv4 Address: 10.10.153.218 (10.10.153.218)
Post NAT Destination IPv4 Address: 10.69.110.21 (10.69.110.21)
Post NAPT Source Transport Port: 0
Post NAPT Destination Transport Port: 0
Flow 5
IPVersion: 04
[Duration: 1.010000000 seconds]
StartTime: 16012.600000000 seconds
EndTime: 16013.610000000 seconds
Packets: 4
Octets: 256
SrcPort: 2000
DstPort: 39216
InputInt: 4
OutputInt: 0
Protocol: 6
IP ToS: 0x00
TCP Flags: 0x18
Destination Mac Address: Routerbo_ZZ:ZZ:ZZ (ZZ:ZZ:ZZ:ZZ:ZZ:ZZ)
Post Source Mac Address: 00:00:00_00:00:00 (00:00:00:00:00:00)
SrcAddr: 10.10.153.217 (10.10.153.217)
DstAddr: 10.10.153.218 (10.10.153.218)
NextHop: 10.10.153.218 (10.10.153.218)
SrcMask: 0
DstMask: 0
IP TTL: 64
IsMulticast: 0
IP Header Length: 5
IP Total Length: 64
UDP Length: 0
TCP Sequence Number: 1439408196
TCP Acknowledgement Number: 786858306
TCP Windows Size: 905
IGMP Type: 0
IPv4 ICMP Type: 0
IPv4 ICMP Code: 0
Post NAT Source IPv4 Address: 10.10.153.217 (10.10.153.217)
Post NAT Destination IPv4 Address: 10.10.153.218 (10.10.153.218)
Post NAPT Source Transport Port: 0
Post NAPT Destination Transport Port: 0
Flow 6
IPVersion: 04
[Duration: 2.030000000 seconds]
StartTime: 16011.580000000 seconds
EndTime: 16013.610000000 seconds
Packets: 9
Octets: 528
SrcPort: 39216
DstPort: 2000
InputInt: 0
OutputInt: 4
Protocol: 6
IP ToS: 0x00
TCP Flags: 0x18
Destination Mac Address: 00:00:00_00:00:00 (00:00:00:00:00:00)
Post Source Mac Address: Routerbo_ZZ:ZZ:ZZ (ZZ:ZZ:ZZ:ZZ:ZZ:ZZ)
SrcAddr: 10.10.153.218 (10.10.153.218)
DstAddr: 10.10.153.217 (10.10.153.217)
NextHop: 10.10.153.217 (10.10.153.217)
SrcMask: 0
DstMask: 0
IP TTL: 64
IsMulticast: 0
IP Header Length: 5
IP Total Length: 64
UDP Length: 0
TCP Sequence Number: 786858282
TCP Acknowledgement Number: 1439408184
TCP Windows Size: 913
IGMP Type: 0
IPv4 ICMP Type: 0
IPv4 ICMP Code: 0
Post NAT Source IPv4 Address: 10.10.153.218 (10.10.153.218)
Post NAT Destination IPv4 Address: 10.10.153.217 (10.10.153.217)
Post NAPT Source Transport Port: 0
Post NAPT Destination Transport Port: 0
No. Time Source Destination Protocol Length Info
385861 752.592360000 10.10.153.218 10.26.35.34 CFLOW 830 IPFIX partial flow (788/8 bytes)
Frame 385861: 830 bytes on wire (6640 bits), 830 bytes captured (6640 bits) on interface 0
Ethernet II, Src: Routerbo_XX:XX:XX (XX:XX:XX:XX:XX:XX), Dst: YY:YY:YY:YY:YY:YY (YY:YY:YY:YY:YY:YY)
Internet Protocol Version 4, Src: 10.10.153.218 (10.10.153.218), Dst: 10.26.35.34 (10.26.35.34)
User Datagram Protocol, Src Port: 2055 (2055), Dst Port: 2055 (2055)
Cisco NetFlow/IPFIX
Version: 10
Length: 8
Timestamp: Jul 5, 1970 12:12:00.000000000 GTB Daylight Time
ExportTime: 16017120
FlowSequence: 386
Observation Domain Id: 0
Set 1
FlowSet Id: (Data) (258)
FlowSet Length: 772
Flow 1
IPVersion: 04
[Duration: 0.000000000 seconds]
StartTime: 16014.870000000 seconds
EndTime: 16014.870000000 seconds
Packets: 2
Octets: 192
SrcPort: 0
DstPort: 0
InputInt: 4
OutputInt: 0
Protocol: 1
IP ToS: 0x00
TCP Flags: 0x00
Destination Mac Address: Routerbo_ZZ:ZZ:ZZ (ZZ:ZZ:ZZ:ZZ:ZZ:ZZ)
Post Source Mac Address: 00:00:00_00:00:00 (00:00:00:00:00:00)
SrcAddr: 10.69.110.16 (10.69.110.16)
DstAddr: 10.10.153.218 (10.10.153.218)
NextHop: 10.10.153.218 (10.10.153.218)
SrcMask: 0
DstMask: 0
IP TTL: 63
IsMulticast: 0
IP Header Length: 5
IP Total Length: 96
UDP Length: 0
TCP Sequence Number: 0
TCP Acknowledgement Number: 0
TCP Windows Size: 0
IGMP Type: 0
IPv4 ICMP Type: 8
IPv4 ICMP Code: 0
Post NAT Source IPv4 Address: 10.69.110.16 (10.69.110.16)
Post NAT Destination IPv4 Address: 10.10.153.218 (10.10.153.218)
Post NAPT Source Transport Port: 0
Post NAPT Destination Transport Port: 0
Flow 2
IPVersion: 04
[Duration: 0.000000000 seconds]
StartTime: 16014.870000000 seconds
EndTime: 16014.870000000 seconds
Packets: 2
Octets: 192
SrcPort: 0
DstPort: 0
InputInt: 0
OutputInt: 4
Protocol: 1
IP ToS: 0x00
TCP Flags: 0x00
Destination Mac Address: 00:00:00_00:00:00 (00:00:00:00:00:00)
Post Source Mac Address: Routerbo_ZZ:ZZ:ZZ (ZZ:ZZ:ZZ:ZZ:ZZ:ZZ)
SrcAddr: 10.10.153.218 (10.10.153.218)
DstAddr: 10.69.110.16 (10.69.110.16)
NextHop: 10.10.153.217 (10.10.153.217)
SrcMask: 0
DstMask: 0
IP TTL: 64
IsMulticast: 0
IP Header Length: 5
IP Total Length: 96
UDP Length: 0
TCP Sequence Number: 0
TCP Acknowledgement Number: 0
TCP Windows Size: 0
IGMP Type: 0
IPv4 ICMP Type: 0
IPv4 ICMP Code: 0
Post NAT Source IPv4 Address: 10.10.153.218 (10.10.153.218)
Post NAT Destination IPv4 Address: 10.69.110.16 (10.69.110.16)
Post NAPT Source Transport Port: 0
Post NAPT Destination Transport Port: 0
Flow 3
IPVersion: 04
[Duration: 27.660000000 seconds]
StartTime: 15987.450000000 seconds
EndTime: 16015.110000000 seconds
Packets: 411
Octets: 32667
SrcPort: 65470
DstPort: 8291
InputInt: 4
OutputInt: 0
Protocol: 6
IP ToS: 0x00
TCP Flags: 0x18
Destination Mac Address: Routerbo_ZZ:ZZ:ZZ (ZZ:ZZ:ZZ:ZZ:ZZ:ZZ)
Post Source Mac Address: 00:00:00_00:00:00 (00:00:00:00:00:00)
SrcAddr: 10.26.35.34 (10.26.35.34)
DstAddr: 10.10.153.218 (10.10.153.218)
NextHop: 10.10.153.218 (10.10.153.218)
SrcMask: 0
DstMask: 0
IP TTL: 61
IsMulticast: 0
IP Header Length: 5
IP Total Length: 523
UDP Length: 0
TCP Sequence Number: 537131081
TCP Acknowledgement Number: 3081807626
TCP Windows Size: 65184
IGMP Type: 0
IPv4 ICMP Type: 0
IPv4 ICMP Code: 0
Post NAT Source IPv4 Address: 10.26.35.34 (10.26.35.34)
Post NAT Destination IPv4 Address: 10.10.153.218 (10.10.153.218)
Post NAPT Source Transport Port: 0
Post NAPT Destination Transport Port: 0
Flow 4
IPVersion: 04
[Duration: 0.000000000 seconds]
StartTime: 16015.120000000 seconds
EndTime: 16015.120000000 seconds
Packets: 2
Octets: 1248
SrcPort: 2055
DstPort: 2055
InputInt: 0
OutputInt: 4
Protocol: 17
IP ToS: 0x00
TCP Flags: 0x00
Destination Mac Address: 00:00:00_00:00:00 (00:00:00:00:00:00)
Post Source Mac Address: Routerbo_ZZ:ZZ:ZZ (ZZ:ZZ:ZZ:ZZ:ZZ:ZZ)
SrcAddr: 10.10.153.218 (10.10.153.218)
DstAddr: 10.26.35.34 (10.26.35.34)
NextHop: 10.10.153.217 (10.10.153.217)
SrcMask: 0
DstMask: 0
IP TTL: 255
IsMulticast: 0
IP Header Length: 5
IP Total Length: 624
UDP Length: 604
TCP Sequence Number: 0
TCP Acknowledgement Number: 0
TCP Windows Size: 0
IGMP Type: 0
IPv4 ICMP Type: 0
IPv4 ICMP Code: 0
Post NAT Source IPv4 Address: 10.10.153.218 (10.10.153.218)
Post NAT Destination IPv4 Address: 10.26.35.34 (10.26.35.34)
Post NAPT Source Transport Port: 0
Post NAPT Destination Transport Port: 0
Flow 5
IPVersion: 04
[Duration: 0.000000000 seconds]
StartTime: 16015.120000000 seconds
EndTime: 16015.120000000 seconds
Packets: 2
Octets: 936
SrcPort: 2055
DstPort: 2055
InputInt: 0
OutputInt: 4
Protocol: 17
IP ToS: 0x00
TCP Flags: 0x00
Destination Mac Address: 00:00:00_00:00:00 (00:00:00:00:00:00)
Post Source Mac Address: Routerbo_ZZ:ZZ:ZZ (ZZ:ZZ:ZZ:ZZ:ZZ:ZZ)
SrcAddr: 10.10.153.218 (10.10.153.218)
DstAddr: 10.69.110.21 (10.69.110.21)
NextHop: 10.10.153.217 (10.10.153.217)
SrcMask: 0
DstMask: 0
IP TTL: 255
IsMulticast: 0
IP Header Length: 5
IP Total Length: 468
UDP Length: 448
TCP Sequence Number: 0
TCP Acknowledgement Number: 0
TCP Windows Size: 0
IGMP Type: 0
IPv4 ICMP Type: 0
IPv4 ICMP Code: 0
Post NAT Source IPv4 Address: 10.10.153.218 (10.10.153.218)
Post NAT Destination IPv4 Address: 10.69.110.21 (10.69.110.21)
Post NAPT Source Transport Port: 0
Post NAPT Destination Transport Port: 0
Flow 6
IPVersion: 04
[Duration: 0.000000000 seconds]
StartTime: 16015.600000000 seconds
EndTime: 16015.600000000 seconds
Packets: 3
Octets: 192
SrcPort: 2000
DstPort: 39216
InputInt: 4
OutputInt: 0
Protocol: 6
IP ToS: 0x00
TCP Flags: 0x18
Destination Mac Address: Routerbo_ZZ:ZZ:ZZ (ZZ:ZZ:ZZ:ZZ:ZZ:ZZ)
Post Source Mac Address: 00:00:00_00:00:00 (00:00:00:00:00:00)
SrcAddr: 10.10.153.217 (10.10.153.217)
DstAddr: 10.10.153.218 (10.10.153.218)
NextHop: 10.10.153.218 (10.10.153.218)
SrcMask: 0
DstMask: 0
IP TTL: 64
IsMulticast: 0
IP Header Length: 5
IP Total Length: 64
UDP Length: 0
TCP Sequence Number: 1439408232
TCP Acknowledgement Number: 786858342
TCP Windows Size: 905
IGMP Type: 0
IPv4 ICMP Type: 0
IPv4 ICMP Code: 0
Post NAT Source IPv4 Address: 10.10.153.217 (10.10.153.217)
Post NAT Destination IPv4 Address: 10.10.153.218 (10.10.153.218)
Post NAPT Source Transport Port: 0
Post NAPT Destination Transport Port: 0
Flow 7
IPVersion: 04
[Duration: 8.370000000 seconds]
StartTime: 16007.320000000 seconds
EndTime: 16015.690000000 seconds
Packets: 50
Octets: 3700
SrcPort: 42989
DstPort: 161
InputInt: 4
OutputInt: 0
Protocol: 17
IP ToS: 0x00
TCP Flags: 0x00
Destination Mac Address: Routerbo_ZZ:ZZ:ZZ (ZZ:ZZ:ZZ:ZZ:ZZ:ZZ)
Post Source Mac Address: 00:00:00_00:00:00 (00:00:00:00:00:00)
SrcAddr: 10.69.110.15 (10.69.110.15)
DstAddr: 10.10.153.218 (10.10.153.218)
NextHop: 10.10.153.218 (10.10.153.218)
SrcMask: 0
DstMask: 0
IP TTL: 63
IsMulticast: 0
IP Header Length: 5
IP Total Length: 74
UDP Length: 54
TCP Sequence Number: 0
TCP Acknowledgement Number: 0
TCP Windows Size: 0
IGMP Type: 0
IPv4 ICMP Type: 0
IPv4 ICMP Code: 0
Post NAT Source IPv4 Address: 10.69.110.15 (10.69.110.15)
Post NAT Destination IPv4 Address: 10.10.153.218 (10.10.153.218)
Post NAPT Source Transport Port: 0
Post NAPT Destination Transport Port: 0
Flow 8
IPVersion: 04
[Duration: 6.340000000 seconds]
StartTime: 16009.350000000 seconds
EndTime: 16015.690000000 seconds
Packets: 48
Octets: 3600
SrcPort: 161
DstPort: 42989
InputInt: 0
OutputInt: 4
Protocol: 17
IP ToS: 0x00
TCP Flags: 0x00
Destination Mac Address: 00:00:00_00:00:00 (00:00:00:00:00:00)
Post Source Mac Address: Routerbo_ZZ:ZZ:ZZ (ZZ:ZZ:ZZ:ZZ:ZZ:ZZ)
SrcAddr: 10.10.153.218 (10.10.153.218)
DstAddr: 10.69.110.15 (10.69.110.15)
NextHop: 10.10.153.217 (10.10.153.217)
SrcMask: 0
DstMask: 0
IP TTL: 64
IsMulticast: 0
IP Header Length: 5
IP Total Length: 75
UDP Length: 55
TCP Sequence Number: 0
TCP Acknowledgement Number: 0
TCP Windows Size: 0
IGMP Type: 0
IPv4 ICMP Type: 0
IPv4 ICMP Code: 0
Post NAT Source IPv4 Address: 10.10.153.218 (10.10.153.218)
Post NAT Destination IPv4 Address: 10.69.110.15 (10.69.110.15)
Post NAPT Source Transport Port: 0
Post NAPT Destination Transport Port: 0Those bad timestamps cause software like nfacct/pmacct to insert bad data to the database.
Also it discards many flows due to bad sequence number (although checking the capture the sequence numbers seem ok. Maybe nfacct consults the timestamp along with the sequence number to detect if a received flow is valid)
Here's my traffic flow configuration:
Code: Select all
> /ip traffic-flow export verbose
# may/29/2016 22:35:09 by RouterOS 6.36rc19
# software id =
#
/ip traffic-flow
set active-flow-timeout=1m cache-entries=32k enabled=yes inactive-flow-timeout=1s interfaces=ether3-ibgp
/ip traffic-flow ipfix
set bytes=yes dst-address=yes dst-address-mask=yes dst-mac-address=yes dst-port=yes first-forwarded=yes gateway=yes icmp-code=yes \
icmp-type=yes igmp-type=yes in-interface=yes ip-header-length=yes ip-total-length=yes ipv6-flow-label=yes is-multicast=yes \
last-forwarded=yes nat-dst-address=yes nat-dst-port=yes nat-src-address=yes nat-src-port=yes out-interface=yes packets=yes \
protocol=yes src-address=yes src-address-mask=yes src-mac-address=yes src-port=yes tcp-ack-num=yes tcp-flags=yes tcp-seq-num=yes \
tcp-window-size=yes tos=yes ttl=yes udp-length=yes
/ip traffic-flow target
add disabled=no dst-address=10.69.110.21 port=2055 src-address=0.0.0.0 v9-template-refresh=20 v9-template-timeout=1m version=9
add disabled=no dst-address=10.26.35.34 port=2055 src-address=0.0.0.0 v9-template-refresh=20 v9-template-timeout=1m version=ipfix
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Ticket#2016051166000808 is solved (tnx).
USB port with GPS and GPS is working (again) since rc16.
NTP server with GPS is still broken and remains in INIT state (since 6.35, works on 6.34.2).
USB port with GPS and GPS is working (again) since rc16.
NTP server with GPS is still broken and remains in INIT state (since 6.35, works on 6.34.2).
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Version 6.36rc20 has been released.
Changes since previous version:
*) dude - (changes discussed here: forum.mikrotik.com/viewtopic.php?f=8&t=108083 );
*) ippool6 - fixed crash on acquire when prefix length is equal with pool prefix length;
*) rb3011 - improved performance on high cpu usage;
*) snmp - report ram memory as ram instead of other;
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash.
Changes since previous version:
*) dude - (changes discussed here: forum.mikrotik.com/viewtopic.php?f=8&t=108083 );
*) ippool6 - fixed crash on acquire when prefix length is equal with pool prefix length;
*) rb3011 - improved performance on high cpu usage;
*) snmp - report ram memory as ram instead of other;
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
i have tested the rc20 release on my rb3011.
interface flapping on ether6-10 is not solved.
now i have problems with fasttrack,
i have a mange rule to add a route mark to packets and if the connection is set to fasttrack it seems that is not added anymore, with stable this works without problems.
interface flapping on ether6-10 is not solved.
now i have problems with fasttrack,
i have a mange rule to add a route mark to packets and if the connection is set to fasttrack it seems that is not added anymore, with stable this works without problems.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
timtasse - Please generate supout file on your device when it is not working as suspected and send this supout file to support@mikrotik.com together with problem description. We will try to find a solution.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
I`ve got hAP ac with RouterOS v6.35.2. But there`re some features in v6.36rc which are interesting me. What will you advice me ? Update to v6.36rc or wait for final release?
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
If it is a production unit, better wait. Say to yourself that v6.36 does not exist yet.I`ve got hAP ac with RouterOS v6.35.2. But there`re some features in v6.36rc which are interesting me. What will you advice me ? Update to v6.36rc or wait for final release?
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
We are seeseeing issues with fasttrack on RB2011 with 6.36rc as well
I'll send support an email.
I'll send support an email.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Version 6.36rc21 has been released.
Changes since previous version:
*) icmp - fixed kernel failure when icmp packet could not be processed on high load;
*) lte - Huawei MU609 must use latest firmware to work correctly;
*) lte - use only creg result codes as network status indications;
*) proxy - limit max ram usage to 80% for tile and x86 devices;
*) rb3011 - fixed reset button functionality;
*) snmp - fixed interface stats branch from MikroTik MIB;
*) snmp - report current access technology and cell id for lte modems;
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash.
Changes since previous version:
*) icmp - fixed kernel failure when icmp packet could not be processed on high load;
*) lte - Huawei MU609 must use latest firmware to work correctly;
*) lte - use only creg result codes as network status indications;
*) proxy - limit max ram usage to 80% for tile and x86 devices;
*) rb3011 - fixed reset button functionality;
*) snmp - fixed interface stats branch from MikroTik MIB;
*) snmp - report current access technology and cell id for lte modems;
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
I am trying to test this new feature but I haven't got any results yet.*) firewall - added raw table to be able to disable connection tracking on selected packets or drop packets before connection tracking (CLI only)
Since 6.36rc8 it is possible to configure firewall rules in a raw table ("/ip firewall raw", "/ipv6 firewall raw"). These rules have two possible chains - prerouting and output which happens before connection tracking in packet flow.
There is action called "notrack". It means that you can select on which packets you want to use connection tracking. It is also possible to drop packets already before connection tracking.
These rules do not have firewall rule matchers that would depend on connection tracking like "connection-state".
Packets which match rules with action "notrack" also are not being fragmented. In past as soon as you loaded connection tracking packets were fragmented. Now even if connection tracking is on "notrack" packets are not being defragmented.
Now in regular firewall, there is new possible connection-state value called "untracked".
Basically, this raw firewall should be used to protect your devices against DDoS attacks.
I am matching udp packets on ports 2000-2100 to 'untrack' a bandwidth test passing through an RB850Gx2.
I don't see any difference in the cpu usage of firewall weather I enable or disable this 'untrack' rule.
It measures packets but no visible change in performance.
Can you provide any examples to play with?
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Nevermind my previous question, I misunderstood what raw table is supposed to do.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
There's problem with CNAMEs, when more of them point to same host. If DNS contains records like this:*) firewall - allow to add domain name to address-lists (dynamic entries for resolved addresses will be added to specified list);
Code: Select all
test.test.lan. A 127.0.0.1
test1.test.lan. CNAME test.test.lan.
test2.test.lan. CNAME test.test.lan.Code: Select all
/ip firewall address-list
add address=test1.test.lan list=test
add address=test2.test.lan list=testCode: Select all
/ip firewall address-list print detail
Flags: X - disabled, D - dynamic
0 list=test address=test1.test.lan dynamic=no
1 D ;;; test1.test.lan
list=test address=127.0.0.1 dynamic=yes
2 list=test address=test2.test.lan dynamic=noEdit: On second thought, it's correct. It does not make sense to have same address in one list twice. With different lists it works fine. Sorry, my bad. The only valid concern might be when you add several hostnames and you don't know in advance that they resolve to same address, it might look like there's a problem, even though there isn't.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
I was about to chime in with thisEdit: On second thought, it's correct. It does not make sense to have same address in one list twice. With different lists it works fine. Sorry, my bad. The only valid concern might be when you add several hostnames and you don't know in advance that they resolve to same address, it might look like there's a problem, even though there isn't.
-

-
IntrusDave
Forum Guru

- Posts: 1286
- Joined:
- Location: Rancho Cucamonga, CA
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Finally received my first RB3001 for testing. My first issue is minor....Version 6.36rc21 has been released.
Changes since previous version:
*) icmp - fixed kernel failure when icmp packet could not be processed on high load;
*) lte - Huawei MU609 must use latest firmware to work correctly;
*) lte - use only creg result codes as network status indications;
*) proxy - limit max ram usage to 80% for tile and x86 devices;
*) rb3011 - fixed reset button functionality;
*) snmp - fixed interface stats branch from MikroTik MIB;
*) snmp - report current access technology and cell id for lte modems;
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash.
Code: Select all
/system resource printRe: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Hello.
Working on equipment with CCR1016-12G
Use it in different offices, and in the configuration used Bonding and via bonding, I am use VLAN's and via VLAN's work with several ISP's and GRE-tunnels, of course in the logs there are errors, correcting for this error corrected already like, I'm talking about version 6.36rc21
*) bonding - fixed 802.3ad load balancing mode over tunnels;
Question to developers: is used as CCR - equipment, is it possible to early release the latest version (for example 6.35.3) very important and which are just needed now and urgently?
Sorry for English
Working on equipment with CCR1016-12G
Use it in different offices, and in the configuration used Bonding and via bonding, I am use VLAN's and via VLAN's work with several ISP's and GRE-tunnels, of course in the logs there are errors, correcting for this error corrected already like, I'm talking about version 6.36rc21
*) bonding - fixed 802.3ad load balancing mode over tunnels;
Question to developers: is used as CCR - equipment, is it possible to early release the latest version (for example 6.35.3) very important and which are just needed now and urgently?
Sorry for English
-

-
JimmyNyholm
Member Candidate

- Posts: 248
- Joined:
- Location: Sweden
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
*) tunnel - added option to auto detect tunnel local-address;
Can't Seem to find it?
Does it solve changing ip in conjuction of auto ipsec aswell? Otherwise please ad that.
Can't Seem to find it?
Does it solve changing ip in conjuction of auto ipsec aswell? Otherwise please ad that.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Please fix OSPFv3, Mikrotik isnt following the RFC.
https://tools.ietf.org/html/rfc5340#appendix-A.2
https://tools.ietf.org/html/rfc5340#appendix-A.2
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
perhaps you right, its "not completely imlemented" case. same about DNS, IPv6 stack and other things (like netfilter portions, RIP and etc generallty legacy stuff).Please fix OSPFv3, Mikrotik isnt following the RFC.
https://tools.ietf.org/html/rfc5340#appendix-A.2
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
I cant run OSPFv3 with an EdgeRouter, because of wrong RFC implementation of the Mikrotik.perhaps you right, its "not completely imlemented" case. same about DNS, IPv6 stack and other things (like netfilter portions, RIP and etc generallty legacy stuff).Please fix OSPFv3, Mikrotik isnt following the RFC.
https://tools.ietf.org/html/rfc5340#appendix-A.2
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Version 6.36rc27 has been released.
Changes since previous version:
*) dude - (changes discussed here: forum.mikrotik.com/viewtopic.php?f=8&t=108083 );
*) dude - server package is now made smaller. client side content upgrade is now removed from it and is downloaded straight from our cloud. So workstations on which client is used will require access to wan. Alternatively upgrade must be done by reinstalling the client on each new release;
*) address-list - make "dynamic=yes" as read-only option;
*) bonding - fixed bonding privmary slave assignment for ovpn interfaces after startup;
*) disk - added support for Plextor PX-G128M6e(A) SSD on CCR1072;
*) firewall - do not show disabled=no in export;
*) firewall - fixed spelling in built-in firewall commentary;
*) gps - fixed longitude seconds part;
*) lcd - reduced lowest backlight-timeout value from 5m to 30s;
*) logs - increase excessive multicast/broadcast warning threshold every time it is logged;
*) lte - removed option allow-roaming for Huawei ME909u and MU609 devices;
*) userman - fixed crash on database upload;
*) wireless-rep - fixed crash on nv2 reconnect;
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash.
Changes since previous version:
*) dude - (changes discussed here: forum.mikrotik.com/viewtopic.php?f=8&t=108083 );
*) dude - server package is now made smaller. client side content upgrade is now removed from it and is downloaded straight from our cloud. So workstations on which client is used will require access to wan. Alternatively upgrade must be done by reinstalling the client on each new release;
*) address-list - make "dynamic=yes" as read-only option;
*) bonding - fixed bonding privmary slave assignment for ovpn interfaces after startup;
*) disk - added support for Plextor PX-G128M6e(A) SSD on CCR1072;
*) firewall - do not show disabled=no in export;
*) firewall - fixed spelling in built-in firewall commentary;
*) gps - fixed longitude seconds part;
*) lcd - reduced lowest backlight-timeout value from 5m to 30s;
*) logs - increase excessive multicast/broadcast warning threshold every time it is logged;
*) lte - removed option allow-roaming for Huawei ME909u and MU609 devices;
*) userman - fixed crash on database upload;
*) wireless-rep - fixed crash on nv2 reconnect;
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Rb3011 still doesn't see usb disk and partition's tool doesn't work..Version 6.36rc27 has been released.
.. cut ..
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash.
[Ticket#2016052566000541]
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
why-y-y?..*) address-list - make "dynamic=yes" as read-only option;
how to add dynamic entry in this version? the goal is excluding such entries from export and NOT writing them to NAND
it's also not possible to add it with very big timeout:
Code: Select all
[admin@TestPlace] /ip firewall address-list> ad ad=99.88.77.77 list=test timeout=3000w
[admin@TestPlace] /ip firewall address-list> pr
Flags: X - disabled, D - dynamic
# LIST ADDRESS TIMEOUT
0 D test 99.88.77.77 17w2d16h28m43s
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
as for "dynamic-only" adress-list options - i still don' get whole idea of removing tweaking that option from ROS 
if its used not for operrational management(eg marking and balancing, routing traffic)but for example for tracking emerging threats, then persistent elements in adress-lists - a must(preferably with timestamp in). i think that should remain tweakable. but not on "record-level" but on "adress-list level" to adjust it for Both purposes, depend needs.
if its used not for operrational management(eg marking and balancing, routing traffic)but for example for tracking emerging threats, then persistent elements in adress-lists - a must(preferably with timestamp in). i think that should remain tweakable. but not on "record-level" but on "adress-list level" to adjust it for Both purposes, depend needs.
-

-
JimmyNyholm
Member Candidate

- Posts: 248
- Joined:
- Location: Sweden
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Bump... No Comment. Neither Winbox 3.4 nor the CLI is displaying anything on any tunnel interface about this feature. What is is about and where can I explore it?*) tunnel - added option to auto detect tunnel local-address;
Can't Seem to find it?
Does it solve changing ip in conjuction of auto ipsec aswell? Otherwise please ad that.
-

-
IntrusDave
Forum Guru

- Posts: 1286
- Joined:
- Location: Rancho Cucamonga, CA
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Address lists can still be dynamic. Creating an item with a timeout makes it dynamic. it really should not be a big issue. My scripts only required very minor changes.as for "dynamic-only" adress-list options - i still don' get whole idea of removing tweaking that option from ROS
if its used not for operrational management(eg marking and balancing, routing traffic)but for example for tracking emerging threats, then persistent elements in adress-lists - a must(preferably with timestamp in). i think that should remain tweakable. but not on "record-level" but on "adress-list level" to adjust it for Both purposes, depend needs.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
And what if I need infinite timeout?Address lists can still be dynamic. Creating an item with a timeout makes it dynamic. it really should not be a big issue.
-

-
IntrusDave
Forum Guru

- Posts: 1286
- Joined:
- Location: Rancho Cucamonga, CA
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Wouldn't that be, by definition, static?And what if I need infinite timeout?Address lists can still be dynamic. Creating an item with a timeout makes it dynamic. it really should not be a big issue.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
the answer was posted earlier:
I don't want to backup some data that is continuously synced to billing system. and I don't want to kill NAND by writing that data to persistent storagehow to add dynamic entry in this version? the goal is excluding such entries from export and NOT writing them to NAND
-

-
IntrusDave
Forum Guru

- Posts: 1286
- Joined:
- Location: Rancho Cucamonga, CA
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
That doesn't make sense. You want an item permanently in an address list, but you don't want it backed up and you don't want it saved?
Oh well.
There is always a work-around. We all know MT is going to do what they feel is best and we have to live with that. It sounds like your only option is to write a script that will refresh your permeant-dynamic lists.
Oh well.
There is always a work-around. We all know MT is going to do what they feel is best and we have to live with that. It sounds like your only option is to write a script that will refresh your permeant-dynamic lists.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
well, config versioning and NAND resource doesn't make sense for you? welcome to the world of telecomThat doesn't make sense
exactly. if your router reboots once a year just for OS upgrade and in a few dozens seconds after that your billing system recreates all dynamic lists - you don't want them to disturb you in your everyday workYou want an item permanently in an address list, but you don't want it backed up and you don't want it saved?
sounds like working spike-nail, but the main question is: why silly destroy what was working before?It sounds like your only option is to write a script that will refresh your permeant-dynamic lists.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
v6.36rc28 has been released.
What's new in 6.36rc28 (2016-Jun-10 12:12):
*) dude - (changes discussed here: forum.mikrotik.com/viewtopic.php?f=8&t=108083 );
*) ipsec - add dead ph2 detection exception for windows msgid noncompilance with rfc;
*) lte - added cinterion pls8 support;
*) lte - fixed connection for huawei without cell info;
*) supout - erase panic data properly on Netinstall;
What's new in 6.36rc28 (2016-Jun-10 12:12):
*) dude - (changes discussed here: forum.mikrotik.com/viewtopic.php?f=8&t=108083 );
*) ipsec - add dead ph2 detection exception for windows msgid noncompilance with rfc;
*) lte - added cinterion pls8 support;
*) lte - fixed connection for huawei without cell info;
*) supout - erase panic data properly on Netinstall;
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
and when we have this fundamental detail for monitoring the CAPs can be used professionally?
*) CapsMAN added CCQ field into Registration Table
I'm not the only one you need, this was already asked many times in the forum
because that way I will not use or recommend to my business clients
*) CapsMAN added CCQ field into Registration Table
I'm not the only one you need, this was already asked many times in the forum
because that way I will not use or recommend to my business clients
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
thats EXACTLY my point.sounds like working spike-nail, but the main question is: why silly destroy what was working before?
there was number of situations, where you may need BOTH "dynamic" OR "static" entries in adress lists, used.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
EXACTLY! This change was also made in 6.35.4. It makes no sense to eliminate a configuration capability that was working just fine. Perhaps MT could explain what the problem was that needed to be resolved by total removal of a configuration option.why-y-y?..*) address-list - make "dynamic=yes" as read-only option;
how to add dynamic entry in this version? the goal is excluding such entries from export and NOT writing them to NAND
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Hello,
I am little lost what is that you are talking about, what was before and there is no more on address list
I am little lost what is that you are talking about, what was before and there is no more on address list
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Before you was able to manually add dynamic entry without timeout. Now there's no such possibility.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Haven't played with this feature, but I would presume that leaving "local address" field empty is the way to invoke the auto detection....Bump... No Comment. Neither Winbox 3.4 nor the CLI is displaying anything on any tunnel interface about this feature. What is is about and where can I explore it?*) tunnel - added option to auto detect tunnel local-address;
Can't Seem to find it?
Does it solve changing ip in conjuction of auto ipsec aswell? Otherwise please ad that.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
ThanksBefore you was able to manually add dynamic entry without timeout. Now there's no such possibility.
But how was possible? Never used this function
Because I always set ip and hit ok for me that is a static entry
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
He was adding them via command line, and including dynamic=yes in the command. Mikrotik has removed this ability going forward, so if you've never used this ability before, it's probably a bad idea to fall in love with it now.ThanksBefore you was able to manually add dynamic entry without timeout. Now there's no such possibility.
But how was possible? Never used this function
Because I always set ip and hit ok for me that is a static entry
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Thanks,He was adding them via command line, and including dynamic=yes in the command. Mikrotik has removed this ability going forward, so if you've never used this ability before, it's probably a bad idea to fall in love with it now.ThanksBefore you was able to manually add dynamic entry without timeout. Now there's no such possibility.
But how was possible? Never used this function
Because I always set ip and hit ok for me that is a static entry
It just a curiosit,
maybe Mt removed for some reason/conflict or will be back with some improvements.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
yeah. i used that in 3 things: 1. store 2rd stage emergin threats, detected. 2. entries for advertisment filtering, fetched and upadted periodically. 3. full bogons list. 4. unconditional "funky/hostile" datacenters, companies(spammers, offenders, malware, whatever else you may encounter in. aside moving to asia, chinaand pacific from central and east europe now its greatly shifted to NA and Africa s-holes in terms of percentage generated threats)EXACTLY! This change was also made in 6.35.4. It makes no sense to eliminate a configuration capability that was working just fine. Perhaps MT could explain what the problem was that needed to be resolved by total removal of a configuration option.why-y-y?..*) address-list - make "dynamic=yes" as read-only option;
how to add dynamic entry in this version? the goal is excluding such entries from export and NOT writing them to NAND
amount of oboard memory, l1, l2 cache size (&cores count), memory controller bandwidth - slightly limit usage for that, but its remain mainstream thing in other platforms for me aswell.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
When the mystical unicorn that is ROSv7 comes out, it's supposed to have an enhancement to the routing filters with a new action of add prefix to address list.
This will open the gates for amazing dynamic realtime blacklists distributed via BGP, and would totally obviate the problem with the adding-as-dynamic issue (as being discussed here anyway)
This will open the gates for amazing dynamic realtime blacklists distributed via BGP, and would totally obviate the problem with the adding-as-dynamic issue (as being discussed here anyway)
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
I'm wondering about v7 and v6.36
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
I don't like the idea of establishing BGP peer to my billing system, sometime in a future. I prefer RouterOS API and nowThis will open the gates for amazing dynamic realtime blacklists distributed via BGP, and would totally obviate the problem with the adding-as-dynamic issue (as being discussed here anyway)
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
After Upgrade from 3.34.6, all NAT rules got
an non existing "in-interface-list" set.
Example
resulting in all rules stopped working. The number (1389) is increasing in each rule.
when i remove this manually, everything seems to work.
I could only see this in NAT rules, all other firewall rules are ok.
Edit: After restoring a Backup, I had the same issue again. I wasn't able to set the int-interface-list with winbox. as soon as i applied the change, the int-interface-list switched to "unknown". In the CLI i saw again a strange value. Setting it with CLI worked as expected.
an non existing "in-interface-list" set.
Example
Code: Select all
in-interface-list=*1389resulting in all rules stopped working. The number (1389) is increasing in each rule.
when i remove this manually, everything seems to work.
I could only see this in NAT rules, all other firewall rules are ok.
Edit: After restoring a Backup, I had the same issue again. I wasn't able to set the int-interface-list with winbox. as soon as i applied the change, the int-interface-list switched to "unknown". In the CLI i saw again a strange value. Setting it with CLI worked as expected.
-

-
JimmyNyholm
Member Candidate

- Posts: 248
- Joined:
- Location: Sweden
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
OK. Then it is not possible with ipsec witch i was hoping for. when are we going to be able to set upp crypted tunnels from a dynamic localpoint without hasseling with scripts?Haven't played with this feature, but I would presume that leaving "local address" field empty is the way to invoke the auto detection....Bump... No Comment. Neither Winbox 3.4 nor the CLI is displaying anything on any tunnel interface about this feature. What is is about and where can I explore it?*) tunnel - added option to auto detect tunnel local-address;
Can't Seem to find it?
Does it solve changing ip in conjuction of auto ipsec aswell? Otherwise please ad that.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
You may be able to accomplish what you want by using GRE or L2TP with hooks to IPSec available in those services.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Problem reported earlier persists.
An L2TP tunnel stops routing traffic when any version later than 6.35 is installed.
Seems like fastpath/fasttrack isn't working.
Starting packet sniffer on the interface and all is working again. Stop packet sniffer - all breaks.
Revert back to 6.35 - all works
An L2TP tunnel stops routing traffic when any version later than 6.35 is installed.
Seems like fastpath/fasttrack isn't working.
Starting packet sniffer on the interface and all is working again. Stop packet sniffer - all breaks.
Revert back to 6.35 - all works
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Do you use L2TP over IPsec? In case you do, please make sure your inner-tunnel IPsec traffic isn't fasttracked (otherwise it bypasses the IPsec policies). This is the expected behaviour.L2TP tunnel stops routing traffic when any version later than 6.35 is installed.
Seems like fastpath/fasttrack isn't working.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
that wasn't option in several applications "at all". also BGP usage imply rather bigger resource consumption, while adress lists implementation - would(and actually was. except DNS static overrides since i think ~ 6.10 or 6.11 somewhere)work perfectly even on mid to low -grade devices(sometimes with moderate impact on boottime, but that expected consequences/drawback).When the mystical unicorn that is ROSv7 comes out, it's supposed to have an enhancement to the routing filters with a new action of add prefix to address list.
This will open the gates for amazing dynamic realtime blacklists distributed via BGP, and would totally obviate the problem with the adding-as-dynamic issue (as being discussed here anyway)
that would eventually shit to writing stuff working over API, sadly. or switching vendor, which is even easier in most cases.
i use BGP-based stuff on some of my devices(usually that was fullbogons lists and portion of advertisement filtering), but that esentially Way more powerful things, generally CCR-grade stuff (or CCR's itself sometimes). whole beauty(despite overhead and amount efforts) of static lists is both wider range of platforms, where they usable, simplicity(they work even if whole BGP things collapse apart
for similar purposes for exactly - even ancient things like RIP protocol - still had some use. they "not perfect" but lightweigh and "implemented anywhere"(compared to) and ~ working.
(not all SOHO devices had say for example OSPV 1/2/3 properly working or BGP, or LDP, let alone ancient things like EGP(that you may found yet in some "legacy" projects, sadly), but RIP 1/2 and RIPng - nearly anywhere).
Last edited by Zorro on Fri Jul 01, 2016 11:05 pm, edited 1 time in total.
-

-
JimmyNyholm
Member Candidate

- Posts: 248
- Joined:
- Location: Sweden
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
No I can't becaus if I specify crypto on tunnel interface then routeros complaint and localendpoint must be specified. This is truely unintuitive. I do understand that it is because of reasons with ipsec engine not able to handle dns and other stuff. But, if I want an encrypted tunnel with a dynamic internet connection it is messy to be polite. I can offcoruse solve this by using script but it is a bad user experience and the tunnel will surly go down till script is triggered again. This SHOULD be leaner, meaner, greater implemented with tunnels and ipsec supporting dns on local endpoint as they are now with remote end point. so why not the local endpoint?You may be able to accomplish what you want by using GRE or L2TP with hooks to IPSec available in those services.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Version 6.36rc30 has been released.
Changes since previous version:
*) certificate - do not exit after card-verify;
*) console - fixed get false function;
*) dude - (changes discussed here: forum.mikrotik.com/viewtopic.php?f=8&t=108083 );
*) ipsec - fixed windows msgid check on x86 devices;
*) lte - added support for Huawei E3531;
*) lte - fixed modem init when pin request present;
*) mesh - fixed crash when connection references a mesh network but it is not available any more;
*) modem - added support for SpeedUP SU-900U modem;
*) queue - reset queue type on interfaces which default queue type changes to no-queue after upgrade;
*) rb3011 - fixed usb driver load (introduced in 6.36r22);
*) route - added suppport for more than 8 bits of options;
*) ssl - do not exit while there still are active sessions;
*) timezone - updated timezone information from tzdata2016e release;
*) upnp - fixed nat rule dst-port by making it visible again;
*) wireless-rep - fixed nstreme reset on poll timeout;
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash
Changes since previous version:
*) certificate - do not exit after card-verify;
*) console - fixed get false function;
*) dude - (changes discussed here: forum.mikrotik.com/viewtopic.php?f=8&t=108083 );
*) ipsec - fixed windows msgid check on x86 devices;
*) lte - added support for Huawei E3531;
*) lte - fixed modem init when pin request present;
*) mesh - fixed crash when connection references a mesh network but it is not available any more;
*) modem - added support for SpeedUP SU-900U modem;
*) queue - reset queue type on interfaces which default queue type changes to no-queue after upgrade;
*) rb3011 - fixed usb driver load (introduced in 6.36r22);
*) route - added suppport for more than 8 bits of options;
*) ssl - do not exit while there still are active sessions;
*) timezone - updated timezone information from tzdata2016e release;
*) upnp - fixed nat rule dst-port by making it visible again;
*) wireless-rep - fixed nstreme reset on poll timeout;
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
RB3011 on 6.36rc30 (rebooted 2 times after) doesn't see usb disk (USB kingston datatraveler 8GB); item present in system resources usb list but not in system disks.Version 6.36rc30 has been released.
*) rb3011 - fixed usb driver load (introduced in 6.36r22);
If you experience version related issues.. [cut]..
Exactly the same as in [Ticket#2016052566000541] previosly submitted.
When do you plan to make partitions work on RB3011/ARM ?
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
bajodel - This is different fix for other issue.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
I got it, so I must wait..bajodel - This is different fix for other issue.
Please.. answer.. when do you plan to make partitions work on RB3011/ARM ?
-

-
diablothebest
newbie
- Posts: 31
- Joined:
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Last 24 hours Im update my x86 system to 6.36rc30.
Today we have issue with user manager! Web interface works - but anyone cant login, and admin to!
I send my server to reboot - and can't connect anymore! Man on another side power cycle server to normal boot!
Today we have issue with user manager! Web interface works - but anyone cant login, and admin to!
I send my server to reboot - and can't connect anymore! Man on another side power cycle server to normal boot!
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Version 6.36rc33 has been released.
Changes since previous version:
*) dude - (changes discussed here: forum.mikrotik.com/viewtopic.php?f=8&t=108083 );
*) email - fixed send from winbox;
*) log - make logging process less aggressive on startup;
*) wap-ac - fixed performance problems with 2.4GHz wireless (additional reboot after upgrade required);
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash
Changes since previous version:
*) dude - (changes discussed here: forum.mikrotik.com/viewtopic.php?f=8&t=108083 );
*) email - fixed send from winbox;
*) log - make logging process less aggressive on startup;
*) wap-ac - fixed performance problems with 2.4GHz wireless (additional reboot after upgrade required);
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Any news on that?Hello,
I just gave IPFIX a try on version 6.36rc19 on a RB2011UAS and it seems that it exports the flows with 'random' timestamps in the year 1970.
The time on the RB2011 is correct (double checked).
Those netflow packets where exported to wireshark by mikrotik every 2 seconds.Code: Select allTimestamp: Jul 5, 1970 11:05:20.000000000 GTB Daylight Time Timestamp: Jul 5, 1970 11:38:40.000000000 GTB Daylight Time Timestamp: Jul 5, 1970 12:12:00.000000000 GTB Daylight Time
The full capture:Reverting back to NetFlow v9 the timestamp fields contain the right date/time.Code: Select allNo. Time Source Destination Protocol Length Info 383778 748.591451000 10.10.153.218 10.26.35.34 CFLOW 542 IPFIX partial flow (500/5 bytes) Frame 383778: 542 bytes on wire (4336 bits), 542 bytes captured (4336 bits) on interface 0 Ethernet II, Src: Routerbo_XX:XX:XX (XX:XX:XX:XX:XX:XX), Dst: YY:YY:YY:YY:YY:YY (YY:YY:YY:YY:YY:YY) Internet Protocol Version 4, Src: 10.10.153.218 (10.10.153.218), Dst: 10.26.35.34 (10.26.35.34) User Datagram Protocol, Src Port: 2055 (2055), Dst Port: 2055 (2055) Cisco NetFlow/IPFIX Version: 10 Length: 5 Timestamp: Jul 5, 1970 11:05:20.000000000 GTB Daylight Time ExportTime: 16013120 FlowSequence: 384 Observation Domain Id: 0 Set 1 FlowSet Id: (Data) (258) FlowSet Length: 484 Flow 1 IPVersion: 04 [Duration: 0.000000000 seconds] StartTime: 16010.600000000 seconds EndTime: 16010.600000000 seconds Packets: 3 Octets: 192 SrcPort: 2000 DstPort: 39216 InputInt: 4 OutputInt: 0 Protocol: 6 IP ToS: 0x00 TCP Flags: 0x18 Destination Mac Address: Routerbo_ZZ:ZZ:ZZ (ZZ:ZZ:ZZ:ZZ:ZZ:ZZ) Post Source Mac Address: 00:00:00_00:00:00 (00:00:00:00:00:00) SrcAddr: 10.10.153.217 (10.10.153.217) DstAddr: 10.10.153.218 (10.10.153.218) NextHop: 10.10.153.218 (10.10.153.218) SrcMask: 0 DstMask: 0 IP TTL: 64 IsMulticast: 0 IP Header Length: 5 IP Total Length: 64 UDP Length: 0 TCP Sequence Number: 1439408172 TCP Acknowledgement Number: 786858282 TCP Windows Size: 905 IGMP Type: 0 IPv4 ICMP Type: 0 IPv4 ICMP Code: 0 Post NAT Source IPv4 Address: 10.10.153.217 (10.10.153.217) Post NAT Destination IPv4 Address: 10.10.153.218 (10.10.153.218) Post NAPT Source Transport Port: 0 Post NAPT Destination Transport Port: 0 Flow 2 IPVersion: 04 [Duration: 0.000000000 seconds] StartTime: 16011.120000000 seconds EndTime: 16011.120000000 seconds Packets: 2 Octets: 1056 SrcPort: 2055 DstPort: 2055 InputInt: 0 OutputInt: 4 Protocol: 17 IP ToS: 0x00 TCP Flags: 0x00 Destination Mac Address: 00:00:00_00:00:00 (00:00:00:00:00:00) Post Source Mac Address: Routerbo_ZZ:ZZ:ZZ (ZZ:ZZ:ZZ:ZZ:ZZ:ZZ) SrcAddr: 10.10.153.218 (10.10.153.218) DstAddr: 10.26.35.34 (10.26.35.34) NextHop: 10.10.153.217 (10.10.153.217) SrcMask: 0 DstMask: 0 IP TTL: 255 IsMulticast: 0 IP Header Length: 5 IP Total Length: 528 UDP Length: 508 TCP Sequence Number: 0 TCP Acknowledgement Number: 0 TCP Windows Size: 0 IGMP Type: 0 IPv4 ICMP Type: 0 IPv4 ICMP Code: 0 Post NAT Source IPv4 Address: 10.10.153.218 (10.10.153.218) Post NAT Destination IPv4 Address: 10.26.35.34 (10.26.35.34) Post NAPT Source Transport Port: 0 Post NAPT Destination Transport Port: 0 Flow 3 IPVersion: 04 [Duration: 0.000000000 seconds] StartTime: 16011.120000000 seconds EndTime: 16011.120000000 seconds Packets: 2 Octets: 800 SrcPort: 2055 DstPort: 2055 InputInt: 0 OutputInt: 4 Protocol: 17 IP ToS: 0x00 TCP Flags: 0x00 Destination Mac Address: 00:00:00_00:00:00 (00:00:00:00:00:00) Post Source Mac Address: Routerbo_ZZ:ZZ:ZZ (ZZ:ZZ:ZZ:ZZ:ZZ:ZZ) SrcAddr: 10.10.153.218 (10.10.153.218) DstAddr: 10.69.110.21 (10.69.110.21) NextHop: 10.10.153.217 (10.10.153.217) SrcMask: 0 DstMask: 0 IP TTL: 255 IsMulticast: 0 IP Header Length: 5 IP Total Length: 400 UDP Length: 380 TCP Sequence Number: 0 TCP Acknowledgement Number: 0 TCP Windows Size: 0 IGMP Type: 0 IPv4 ICMP Type: 0 IPv4 ICMP Code: 0 Post NAT Source IPv4 Address: 10.10.153.218 (10.10.153.218) Post NAT Destination IPv4 Address: 10.69.110.21 (10.69.110.21) Post NAPT Source Transport Port: 0 Post NAPT Destination Transport Port: 0 Flow 4 IPVersion: 04 [Duration: 0.000000000 seconds] StartTime: 16012.000000000 seconds EndTime: 16012.000000000 seconds Packets: 3 Octets: 194 SrcPort: 33353 DstPort: 179 InputInt: 0 OutputInt: 4 Protocol: 6 IP ToS: 0xc0 TCP Flags: 0x18 Destination Mac Address: 00:00:00_00:00:00 (00:00:00:00:00:00) Post Source Mac Address: Routerbo_ZZ:ZZ:ZZ (ZZ:ZZ:ZZ:ZZ:ZZ:ZZ) SrcAddr: 10.10.153.218 (10.10.153.218) DstAddr: 10.10.153.217 (10.10.153.217) NextHop: 10.10.153.217 (10.10.153.217) SrcMask: 0 DstMask: 0 IP TTL: 64 IsMulticast: 0 IP Header Length: 5 IP Total Length: 71 UDP Length: 0 TCP Sequence Number: 131047850 TCP Acknowledgement Number: 1912585720 TCP Windows Size: 1016 IGMP Type: 0 IPv4 ICMP Type: 0 IPv4 ICMP Code: 0 Post NAT Source IPv4 Address: 10.10.153.218 (10.10.153.218) Post NAT Destination IPv4 Address: 10.10.153.217 (10.10.153.217) Post NAPT Source Transport Port: 0 Post NAPT Destination Transport Port: 0 Flow 5 IPVersion: 04 [Duration: 0.000000000 seconds] StartTime: 16012.000000000 seconds EndTime: 16012.000000000 seconds Packets: 3 Octets: 175 SrcPort: 179 DstPort: 33353 InputInt: 4 OutputInt: 0 Protocol: 6 IP ToS: 0xc0 TCP Flags: 0x10 Destination Mac Address: Routerbo_ZZ:ZZ:ZZ (ZZ:ZZ:ZZ:ZZ:ZZ:ZZ) Post Source Mac Address: 00:00:00_00:00:00 (00:00:00:00:00:00) SrcAddr: 10.10.153.217 (10.10.153.217) DstAddr: 10.10.153.218 (10.10.153.218) NextHop: 10.10.153.218 (10.10.153.218) SrcMask: 0 DstMask: 0 IP TTL: 64 IsMulticast: 0 IP Header Length: 5 IP Total Length: 52 UDP Length: 0 TCP Sequence Number: 1912585720 TCP Acknowledgement Number: 131047869 TCP Windows Size: 1082 IGMP Type: 0 IPv4 ICMP Type: 0 IPv4 ICMP Code: 0 Post NAT Source IPv4 Address: 10.10.153.217 (10.10.153.217) Post NAT Destination IPv4 Address: 10.10.153.218 (10.10.153.218) Post NAPT Source Transport Port: 0 Post NAPT Destination Transport Port: 0 No. Time Source Destination Protocol Length Info 384733 750.593356000 10.10.153.218 10.26.35.34 CFLOW 638 IPFIX partial flow (596/6 bytes) Frame 384733: 638 bytes on wire (5104 bits), 638 bytes captured (5104 bits) on interface 0 Ethernet II, Src: Routerbo_XX:XX:XX (XX:XX:XX:XX:XX:XX), Dst: YY:YY:YY:YY:YY:YY (YY:YY:YY:YY:YY:YY) Internet Protocol Version 4, Src: 10.10.153.218 (10.10.153.218), Dst: 10.26.35.34 (10.26.35.34) User Datagram Protocol, Src Port: 2055 (2055), Dst Port: 2055 (2055) Cisco NetFlow/IPFIX Version: 10 Length: 6 Timestamp: Jul 5, 1970 11:38:40.000000000 GTB Daylight Time ExportTime: 16015120 FlowSequence: 385 Observation Domain Id: 0 Set 1 FlowSet Id: (Data) (258) FlowSet Length: 580 Flow 1 IPVersion: 04 [Duration: 1.820000000 seconds] StartTime: 16011.220000000 seconds EndTime: 16013.040000000 seconds Packets: 3 Octets: 288 SrcPort: 0 DstPort: 0 InputInt: 4 OutputInt: 0 Protocol: 1 IP ToS: 0x00 TCP Flags: 0x00 Destination Mac Address: Routerbo_ZZ:ZZ:ZZ (ZZ:ZZ:ZZ:ZZ:ZZ:ZZ) Post Source Mac Address: 00:00:00_00:00:00 (00:00:00:00:00:00) SrcAddr: 10.69.110.16 (10.69.110.16) DstAddr: 10.10.153.218 (10.10.153.218) NextHop: 10.10.153.218 (10.10.153.218) SrcMask: 0 DstMask: 0 IP TTL: 63 IsMulticast: 0 IP Header Length: 5 IP Total Length: 96 UDP Length: 0 TCP Sequence Number: 0 TCP Acknowledgement Number: 0 TCP Windows Size: 0 IGMP Type: 0 IPv4 ICMP Type: 8 IPv4 ICMP Code: 0 Post NAT Source IPv4 Address: 10.69.110.16 (10.69.110.16) Post NAT Destination IPv4 Address: 10.10.153.218 (10.10.153.218) Post NAPT Source Transport Port: 0 Post NAPT Destination Transport Port: 0 Flow 2 IPVersion: 04 [Duration: 1.820000000 seconds] StartTime: 16011.220000000 seconds EndTime: 16013.040000000 seconds Packets: 3 Octets: 288 SrcPort: 0 DstPort: 0 InputInt: 0 OutputInt: 4 Protocol: 1 IP ToS: 0x00 TCP Flags: 0x00 Destination Mac Address: 00:00:00_00:00:00 (00:00:00:00:00:00) Post Source Mac Address: Routerbo_ZZ:ZZ:ZZ (ZZ:ZZ:ZZ:ZZ:ZZ:ZZ) SrcAddr: 10.10.153.218 (10.10.153.218) DstAddr: 10.69.110.16 (10.69.110.16) NextHop: 10.10.153.217 (10.10.153.217) SrcMask: 0 DstMask: 0 IP TTL: 64 IsMulticast: 0 IP Header Length: 5 IP Total Length: 96 UDP Length: 0 TCP Sequence Number: 0 TCP Acknowledgement Number: 0 TCP Windows Size: 0 IGMP Type: 0 IPv4 ICMP Type: 0 IPv4 ICMP Code: 0 Post NAT Source IPv4 Address: 10.10.153.218 (10.10.153.218) Post NAT Destination IPv4 Address: 10.69.110.16 (10.69.110.16) Post NAPT Source Transport Port: 0 Post NAPT Destination Transport Port: 0 Flow 3 IPVersion: 04 [Duration: 0.000000000 seconds] StartTime: 16013.120000000 seconds EndTime: 16013.120000000 seconds Packets: 2 Octets: 1056 SrcPort: 2055 DstPort: 2055 InputInt: 0 OutputInt: 4 Protocol: 17 IP ToS: 0x00 TCP Flags: 0x00 Destination Mac Address: 00:00:00_00:00:00 (00:00:00:00:00:00) Post Source Mac Address: Routerbo_ZZ:ZZ:ZZ (ZZ:ZZ:ZZ:ZZ:ZZ:ZZ) SrcAddr: 10.10.153.218 (10.10.153.218) DstAddr: 10.26.35.34 (10.26.35.34) NextHop: 10.10.153.217 (10.10.153.217) SrcMask: 0 DstMask: 0 IP TTL: 255 IsMulticast: 0 IP Header Length: 5 IP Total Length: 528 UDP Length: 508 TCP Sequence Number: 0 TCP Acknowledgement Number: 0 TCP Windows Size: 0 IGMP Type: 0 IPv4 ICMP Type: 0 IPv4 ICMP Code: 0 Post NAT Source IPv4 Address: 10.10.153.218 (10.10.153.218) Post NAT Destination IPv4 Address: 10.26.35.34 (10.26.35.34) Post NAPT Source Transport Port: 0 Post NAPT Destination Transport Port: 0 Flow 4 IPVersion: 04 [Duration: 0.000000000 seconds] StartTime: 16013.120000000 seconds EndTime: 16013.120000000 seconds Packets: 2 Octets: 800 SrcPort: 2055 DstPort: 2055 InputInt: 0 OutputInt: 4 Protocol: 17 IP ToS: 0x00 TCP Flags: 0x00 Destination Mac Address: 00:00:00_00:00:00 (00:00:00:00:00:00) Post Source Mac Address: Routerbo_ZZ:ZZ:ZZ (ZZ:ZZ:ZZ:ZZ:ZZ:ZZ) SrcAddr: 10.10.153.218 (10.10.153.218) DstAddr: 10.69.110.21 (10.69.110.21) NextHop: 10.10.153.217 (10.10.153.217) SrcMask: 0 DstMask: 0 IP TTL: 255 IsMulticast: 0 IP Header Length: 5 IP Total Length: 400 UDP Length: 380 TCP Sequence Number: 0 TCP Acknowledgement Number: 0 TCP Windows Size: 0 IGMP Type: 0 IPv4 ICMP Type: 0 IPv4 ICMP Code: 0 Post NAT Source IPv4 Address: 10.10.153.218 (10.10.153.218) Post NAT Destination IPv4 Address: 10.69.110.21 (10.69.110.21) Post NAPT Source Transport Port: 0 Post NAPT Destination Transport Port: 0 Flow 5 IPVersion: 04 [Duration: 1.010000000 seconds] StartTime: 16012.600000000 seconds EndTime: 16013.610000000 seconds Packets: 4 Octets: 256 SrcPort: 2000 DstPort: 39216 InputInt: 4 OutputInt: 0 Protocol: 6 IP ToS: 0x00 TCP Flags: 0x18 Destination Mac Address: Routerbo_ZZ:ZZ:ZZ (ZZ:ZZ:ZZ:ZZ:ZZ:ZZ) Post Source Mac Address: 00:00:00_00:00:00 (00:00:00:00:00:00) SrcAddr: 10.10.153.217 (10.10.153.217) DstAddr: 10.10.153.218 (10.10.153.218) NextHop: 10.10.153.218 (10.10.153.218) SrcMask: 0 DstMask: 0 IP TTL: 64 IsMulticast: 0 IP Header Length: 5 IP Total Length: 64 UDP Length: 0 TCP Sequence Number: 1439408196 TCP Acknowledgement Number: 786858306 TCP Windows Size: 905 IGMP Type: 0 IPv4 ICMP Type: 0 IPv4 ICMP Code: 0 Post NAT Source IPv4 Address: 10.10.153.217 (10.10.153.217) Post NAT Destination IPv4 Address: 10.10.153.218 (10.10.153.218) Post NAPT Source Transport Port: 0 Post NAPT Destination Transport Port: 0 Flow 6 IPVersion: 04 [Duration: 2.030000000 seconds] StartTime: 16011.580000000 seconds EndTime: 16013.610000000 seconds Packets: 9 Octets: 528 SrcPort: 39216 DstPort: 2000 InputInt: 0 OutputInt: 4 Protocol: 6 IP ToS: 0x00 TCP Flags: 0x18 Destination Mac Address: 00:00:00_00:00:00 (00:00:00:00:00:00) Post Source Mac Address: Routerbo_ZZ:ZZ:ZZ (ZZ:ZZ:ZZ:ZZ:ZZ:ZZ) SrcAddr: 10.10.153.218 (10.10.153.218) DstAddr: 10.10.153.217 (10.10.153.217) NextHop: 10.10.153.217 (10.10.153.217) SrcMask: 0 DstMask: 0 IP TTL: 64 IsMulticast: 0 IP Header Length: 5 IP Total Length: 64 UDP Length: 0 TCP Sequence Number: 786858282 TCP Acknowledgement Number: 1439408184 TCP Windows Size: 913 IGMP Type: 0 IPv4 ICMP Type: 0 IPv4 ICMP Code: 0 Post NAT Source IPv4 Address: 10.10.153.218 (10.10.153.218) Post NAT Destination IPv4 Address: 10.10.153.217 (10.10.153.217) Post NAPT Source Transport Port: 0 Post NAPT Destination Transport Port: 0 No. Time Source Destination Protocol Length Info 385861 752.592360000 10.10.153.218 10.26.35.34 CFLOW 830 IPFIX partial flow (788/8 bytes) Frame 385861: 830 bytes on wire (6640 bits), 830 bytes captured (6640 bits) on interface 0 Ethernet II, Src: Routerbo_XX:XX:XX (XX:XX:XX:XX:XX:XX), Dst: YY:YY:YY:YY:YY:YY (YY:YY:YY:YY:YY:YY) Internet Protocol Version 4, Src: 10.10.153.218 (10.10.153.218), Dst: 10.26.35.34 (10.26.35.34) User Datagram Protocol, Src Port: 2055 (2055), Dst Port: 2055 (2055) Cisco NetFlow/IPFIX Version: 10 Length: 8 Timestamp: Jul 5, 1970 12:12:00.000000000 GTB Daylight Time ExportTime: 16017120 FlowSequence: 386 Observation Domain Id: 0 Set 1 FlowSet Id: (Data) (258) FlowSet Length: 772 Flow 1 IPVersion: 04 [Duration: 0.000000000 seconds] StartTime: 16014.870000000 seconds EndTime: 16014.870000000 seconds Packets: 2 Octets: 192 SrcPort: 0 DstPort: 0 InputInt: 4 OutputInt: 0 Protocol: 1 IP ToS: 0x00 TCP Flags: 0x00 Destination Mac Address: Routerbo_ZZ:ZZ:ZZ (ZZ:ZZ:ZZ:ZZ:ZZ:ZZ) Post Source Mac Address: 00:00:00_00:00:00 (00:00:00:00:00:00) SrcAddr: 10.69.110.16 (10.69.110.16) DstAddr: 10.10.153.218 (10.10.153.218) NextHop: 10.10.153.218 (10.10.153.218) SrcMask: 0 DstMask: 0 IP TTL: 63 IsMulticast: 0 IP Header Length: 5 IP Total Length: 96 UDP Length: 0 TCP Sequence Number: 0 TCP Acknowledgement Number: 0 TCP Windows Size: 0 IGMP Type: 0 IPv4 ICMP Type: 8 IPv4 ICMP Code: 0 Post NAT Source IPv4 Address: 10.69.110.16 (10.69.110.16) Post NAT Destination IPv4 Address: 10.10.153.218 (10.10.153.218) Post NAPT Source Transport Port: 0 Post NAPT Destination Transport Port: 0 Flow 2 IPVersion: 04 [Duration: 0.000000000 seconds] StartTime: 16014.870000000 seconds EndTime: 16014.870000000 seconds Packets: 2 Octets: 192 SrcPort: 0 DstPort: 0 InputInt: 0 OutputInt: 4 Protocol: 1 IP ToS: 0x00 TCP Flags: 0x00 Destination Mac Address: 00:00:00_00:00:00 (00:00:00:00:00:00) Post Source Mac Address: Routerbo_ZZ:ZZ:ZZ (ZZ:ZZ:ZZ:ZZ:ZZ:ZZ) SrcAddr: 10.10.153.218 (10.10.153.218) DstAddr: 10.69.110.16 (10.69.110.16) NextHop: 10.10.153.217 (10.10.153.217) SrcMask: 0 DstMask: 0 IP TTL: 64 IsMulticast: 0 IP Header Length: 5 IP Total Length: 96 UDP Length: 0 TCP Sequence Number: 0 TCP Acknowledgement Number: 0 TCP Windows Size: 0 IGMP Type: 0 IPv4 ICMP Type: 0 IPv4 ICMP Code: 0 Post NAT Source IPv4 Address: 10.10.153.218 (10.10.153.218) Post NAT Destination IPv4 Address: 10.69.110.16 (10.69.110.16) Post NAPT Source Transport Port: 0 Post NAPT Destination Transport Port: 0 Flow 3 IPVersion: 04 [Duration: 27.660000000 seconds] StartTime: 15987.450000000 seconds EndTime: 16015.110000000 seconds Packets: 411 Octets: 32667 SrcPort: 65470 DstPort: 8291 InputInt: 4 OutputInt: 0 Protocol: 6 IP ToS: 0x00 TCP Flags: 0x18 Destination Mac Address: Routerbo_ZZ:ZZ:ZZ (ZZ:ZZ:ZZ:ZZ:ZZ:ZZ) Post Source Mac Address: 00:00:00_00:00:00 (00:00:00:00:00:00) SrcAddr: 10.26.35.34 (10.26.35.34) DstAddr: 10.10.153.218 (10.10.153.218) NextHop: 10.10.153.218 (10.10.153.218) SrcMask: 0 DstMask: 0 IP TTL: 61 IsMulticast: 0 IP Header Length: 5 IP Total Length: 523 UDP Length: 0 TCP Sequence Number: 537131081 TCP Acknowledgement Number: 3081807626 TCP Windows Size: 65184 IGMP Type: 0 IPv4 ICMP Type: 0 IPv4 ICMP Code: 0 Post NAT Source IPv4 Address: 10.26.35.34 (10.26.35.34) Post NAT Destination IPv4 Address: 10.10.153.218 (10.10.153.218) Post NAPT Source Transport Port: 0 Post NAPT Destination Transport Port: 0 Flow 4 IPVersion: 04 [Duration: 0.000000000 seconds] StartTime: 16015.120000000 seconds EndTime: 16015.120000000 seconds Packets: 2 Octets: 1248 SrcPort: 2055 DstPort: 2055 InputInt: 0 OutputInt: 4 Protocol: 17 IP ToS: 0x00 TCP Flags: 0x00 Destination Mac Address: 00:00:00_00:00:00 (00:00:00:00:00:00) Post Source Mac Address: Routerbo_ZZ:ZZ:ZZ (ZZ:ZZ:ZZ:ZZ:ZZ:ZZ) SrcAddr: 10.10.153.218 (10.10.153.218) DstAddr: 10.26.35.34 (10.26.35.34) NextHop: 10.10.153.217 (10.10.153.217) SrcMask: 0 DstMask: 0 IP TTL: 255 IsMulticast: 0 IP Header Length: 5 IP Total Length: 624 UDP Length: 604 TCP Sequence Number: 0 TCP Acknowledgement Number: 0 TCP Windows Size: 0 IGMP Type: 0 IPv4 ICMP Type: 0 IPv4 ICMP Code: 0 Post NAT Source IPv4 Address: 10.10.153.218 (10.10.153.218) Post NAT Destination IPv4 Address: 10.26.35.34 (10.26.35.34) Post NAPT Source Transport Port: 0 Post NAPT Destination Transport Port: 0 Flow 5 IPVersion: 04 [Duration: 0.000000000 seconds] StartTime: 16015.120000000 seconds EndTime: 16015.120000000 seconds Packets: 2 Octets: 936 SrcPort: 2055 DstPort: 2055 InputInt: 0 OutputInt: 4 Protocol: 17 IP ToS: 0x00 TCP Flags: 0x00 Destination Mac Address: 00:00:00_00:00:00 (00:00:00:00:00:00) Post Source Mac Address: Routerbo_ZZ:ZZ:ZZ (ZZ:ZZ:ZZ:ZZ:ZZ:ZZ) SrcAddr: 10.10.153.218 (10.10.153.218) DstAddr: 10.69.110.21 (10.69.110.21) NextHop: 10.10.153.217 (10.10.153.217) SrcMask: 0 DstMask: 0 IP TTL: 255 IsMulticast: 0 IP Header Length: 5 IP Total Length: 468 UDP Length: 448 TCP Sequence Number: 0 TCP Acknowledgement Number: 0 TCP Windows Size: 0 IGMP Type: 0 IPv4 ICMP Type: 0 IPv4 ICMP Code: 0 Post NAT Source IPv4 Address: 10.10.153.218 (10.10.153.218) Post NAT Destination IPv4 Address: 10.69.110.21 (10.69.110.21) Post NAPT Source Transport Port: 0 Post NAPT Destination Transport Port: 0 Flow 6 IPVersion: 04 [Duration: 0.000000000 seconds] StartTime: 16015.600000000 seconds EndTime: 16015.600000000 seconds Packets: 3 Octets: 192 SrcPort: 2000 DstPort: 39216 InputInt: 4 OutputInt: 0 Protocol: 6 IP ToS: 0x00 TCP Flags: 0x18 Destination Mac Address: Routerbo_ZZ:ZZ:ZZ (ZZ:ZZ:ZZ:ZZ:ZZ:ZZ) Post Source Mac Address: 00:00:00_00:00:00 (00:00:00:00:00:00) SrcAddr: 10.10.153.217 (10.10.153.217) DstAddr: 10.10.153.218 (10.10.153.218) NextHop: 10.10.153.218 (10.10.153.218) SrcMask: 0 DstMask: 0 IP TTL: 64 IsMulticast: 0 IP Header Length: 5 IP Total Length: 64 UDP Length: 0 TCP Sequence Number: 1439408232 TCP Acknowledgement Number: 786858342 TCP Windows Size: 905 IGMP Type: 0 IPv4 ICMP Type: 0 IPv4 ICMP Code: 0 Post NAT Source IPv4 Address: 10.10.153.217 (10.10.153.217) Post NAT Destination IPv4 Address: 10.10.153.218 (10.10.153.218) Post NAPT Source Transport Port: 0 Post NAPT Destination Transport Port: 0 Flow 7 IPVersion: 04 [Duration: 8.370000000 seconds] StartTime: 16007.320000000 seconds EndTime: 16015.690000000 seconds Packets: 50 Octets: 3700 SrcPort: 42989 DstPort: 161 InputInt: 4 OutputInt: 0 Protocol: 17 IP ToS: 0x00 TCP Flags: 0x00 Destination Mac Address: Routerbo_ZZ:ZZ:ZZ (ZZ:ZZ:ZZ:ZZ:ZZ:ZZ) Post Source Mac Address: 00:00:00_00:00:00 (00:00:00:00:00:00) SrcAddr: 10.69.110.15 (10.69.110.15) DstAddr: 10.10.153.218 (10.10.153.218) NextHop: 10.10.153.218 (10.10.153.218) SrcMask: 0 DstMask: 0 IP TTL: 63 IsMulticast: 0 IP Header Length: 5 IP Total Length: 74 UDP Length: 54 TCP Sequence Number: 0 TCP Acknowledgement Number: 0 TCP Windows Size: 0 IGMP Type: 0 IPv4 ICMP Type: 0 IPv4 ICMP Code: 0 Post NAT Source IPv4 Address: 10.69.110.15 (10.69.110.15) Post NAT Destination IPv4 Address: 10.10.153.218 (10.10.153.218) Post NAPT Source Transport Port: 0 Post NAPT Destination Transport Port: 0 Flow 8 IPVersion: 04 [Duration: 6.340000000 seconds] StartTime: 16009.350000000 seconds EndTime: 16015.690000000 seconds Packets: 48 Octets: 3600 SrcPort: 161 DstPort: 42989 InputInt: 0 OutputInt: 4 Protocol: 17 IP ToS: 0x00 TCP Flags: 0x00 Destination Mac Address: 00:00:00_00:00:00 (00:00:00:00:00:00) Post Source Mac Address: Routerbo_ZZ:ZZ:ZZ (ZZ:ZZ:ZZ:ZZ:ZZ:ZZ) SrcAddr: 10.10.153.218 (10.10.153.218) DstAddr: 10.69.110.15 (10.69.110.15) NextHop: 10.10.153.217 (10.10.153.217) SrcMask: 0 DstMask: 0 IP TTL: 64 IsMulticast: 0 IP Header Length: 5 IP Total Length: 75 UDP Length: 55 TCP Sequence Number: 0 TCP Acknowledgement Number: 0 TCP Windows Size: 0 IGMP Type: 0 IPv4 ICMP Type: 0 IPv4 ICMP Code: 0 Post NAT Source IPv4 Address: 10.10.153.218 (10.10.153.218) Post NAT Destination IPv4 Address: 10.69.110.15 (10.69.110.15) Post NAPT Source Transport Port: 0 Post NAPT Destination Transport Port: 0
Those bad timestamps cause software like nfacct/pmacct to insert bad data to the database.
Also it discards many flows due to bad sequence number (although checking the capture the sequence numbers seem ok. Maybe nfacct consults the timestamp along with the sequence number to detect if a received flow is valid)
Here's my traffic flow configuration:
[Ticket#2016052966000463]Code: Select all> /ip traffic-flow export verbose # may/29/2016 22:35:09 by RouterOS 6.36rc19 # software id = # /ip traffic-flow set active-flow-timeout=1m cache-entries=32k enabled=yes inactive-flow-timeout=1s interfaces=ether3-ibgp /ip traffic-flow ipfix set bytes=yes dst-address=yes dst-address-mask=yes dst-mac-address=yes dst-port=yes first-forwarded=yes gateway=yes icmp-code=yes \ icmp-type=yes igmp-type=yes in-interface=yes ip-header-length=yes ip-total-length=yes ipv6-flow-label=yes is-multicast=yes \ last-forwarded=yes nat-dst-address=yes nat-dst-port=yes nat-src-address=yes nat-src-port=yes out-interface=yes packets=yes \ protocol=yes src-address=yes src-address-mask=yes src-mac-address=yes src-port=yes tcp-ack-num=yes tcp-flags=yes tcp-seq-num=yes \ tcp-window-size=yes tos=yes ttl=yes udp-length=yes /ip traffic-flow target add disabled=no dst-address=10.69.110.21 port=2055 src-address=0.0.0.0 v9-template-refresh=20 v9-template-timeout=1m version=9 add disabled=no dst-address=10.26.35.34 port=2055 src-address=0.0.0.0 v9-template-refresh=20 v9-template-timeout=1m version=ipfix
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Or any news on this? http://forum.mikrotik.com/viewtopic.php ... te#p527731
Ticket #2016052566000621
It's been over a month and I haven't even got a response on that ticket...
Ticket #2016052566000621
It's been over a month and I haven't even got a response on that ticket...
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
*) wap-ac - fixed performance problems with 2.4GHz wireless (additional reboot after upgrade required);
After update signal become worse (wAP-ac working as repeater, main router hap AC). wAP-ac loosing connections constantly...
After update signal become worse (wAP-ac working as repeater, main router hap AC). wAP-ac loosing connections constantly...
Re: RE: Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
PleaseI got it, so I must wait..bajodel - This is different fix for other issue.
Please.. answer.. when do you plan to make partitions work on RB3011/ARM ?
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Did you enable wireless-rep package and upgrade firmware ? If it does no help, please write to support and add supout file in attachment.*) wap-ac - fixed performance problems with 2.4GHz wireless (additional reboot after upgrade required);
After update signal become worse (wAP-ac working as repeater, main router hap AC). wAP-ac loosing connections constantly...
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Yes wirelles -rep was enables. Version 6.36rc30 - everything was ok.
-

-
kimdobranski
newbie
- Posts: 43
- Joined:
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Hi,
Would love it if WAN MAC address of Router was available as a form variable for the hotspot system.
Would love it if WAN MAC address of Router was available as a form variable for the hotspot system.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
comparing old "static entries" in adress-lists and "dynamic entries" with negative lifetime(basically ~ same functionality so far) i would admit that last one - make routers boot-up a LOT faster. so if you have say 15-50(and up to 0.4m on CCR's isn't extraordinary thing, but generally uncommon)k entries in you adress lists - you will notice it, perhaps.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Version 6.36rc36 has been released.
Changes since previous version:
*) clock - fixed time keeping for SXT ac, 911L, cAP, mAP lite, wAP;
*) dude - (changes discussed here: forum.mikrotik.com/viewtopic.php?f=8&t=108083);
*) ipsec - show remote peer address in error messages when possible;
*) lte - display message in lte,error log if no response received;
*) lte - display message in lte,error log when PIN is required;
*) modem - added support for Alcatel OneTouch X600;
*) upnp - fixed firewall rules not being dynamic;
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash
Changes since previous version:
*) clock - fixed time keeping for SXT ac, 911L, cAP, mAP lite, wAP;
*) dude - (changes discussed here: forum.mikrotik.com/viewtopic.php?f=8&t=108083);
*) ipsec - show remote peer address in error messages when possible;
*) lte - display message in lte,error log if no response received;
*) lte - display message in lte,error log when PIN is required;
*) modem - added support for Alcatel OneTouch X600;
*) upnp - fixed firewall rules not being dynamic;
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
I just tested my mAP Lite and clock works fine now.Version 6.36rc36 has been released.
Changes since previous version:
*) clock - fixed time keeping for SXT ac, 911L, cAP, mAP lite, wAP;
Thanks!
-

-
diablothebest
newbie
- Posts: 31
- Joined:
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
We test this RC on two X86 machines! Use netinstall to make USB RoS flash! All machines reboot after RoS boot to login screen!
-

-
diablothebest
newbie
- Posts: 31
- Joined:
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
I'm try to install this RC to VM and get error in the end of instalation!
6.34.6 installs fine.
6.34.6 installs fine.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Version 6.36rc37 has been released.
Changes since previous version:
*) dude - (changes discussed here: forum.mikrotik.com/viewtopic.php?f=8&t=108083);
*) l2tp - fixed crash when rebooting or disabling l2tp while there are still active connections;
*) rb3011 - fixed usb storage mounting;
*) webfig - reduced refresh time for wireless registration table to 1 second;
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash
Changes since previous version:
*) dude - (changes discussed here: forum.mikrotik.com/viewtopic.php?f=8&t=108083);
*) l2tp - fixed crash when rebooting or disabling l2tp while there are still active connections;
*) rb3011 - fixed usb storage mounting;
*) webfig - reduced refresh time for wireless registration table to 1 second;
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Hello,*) l2tp - fixed crash when rebooting or disabling l2tp while there are still active connections;
Is this issue is the one related to LNS setup?
Thanks,
I will answer my own question, yes, it is concerning the LNS setup, I got confirmation from Mikrotik.
Last edited by ganewbie on Tue Jul 12, 2016 11:04 am, edited 1 time in total.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Code: Select all
/ip firewall nat
add action=masquerade chain=srcnat out-interface=!pppoe-out1 src-address=\
192.168.88.8Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
can i make suggestion about newly-implemented "raw table"?
its lack support for dragging/re-ordering rules there like in "firewall" and "nat", "mangle" was. that would be helpful i think.
its lack support for dragging/re-ordering rules there like in "firewall" and "nat", "mangle" was. that would be helpful i think.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Re-ordering works the same as in the other tables.can i make suggestion about newly-implemented "raw table"?
its lack support for dragging/re-ordering rules there like in "firewall" and "nat", "mangle" was. that would be helpful i think.
Probably you don't have the raw table sorted by '#'. If it's sorted by any other field then you cannot move any rules. That goes for all tables, not just raw.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
I noticed lots of issues with the RB3011 router board, and unanswered questions. I'm new to the product and wondering if Mikrotik will provide adequate support for errors released on it's behalf. Are all of the bugs with RB3011 cured yet?
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
To which bugs are you referring to?I noticed lots of issues with the RB3011 router board, and unanswered questions. I'm new to the product and wondering if Mikrotik will provide adequate support for errors released on it's behalf. Are all of the bugs with RB3011 cured yet?
I have an RB3011 and I don't have any issues. If you check the changelog you'll see that some 3011 related bugs are being fixed from release to release. So it's not an abandoned product.
Re: The Dude, v6.36rc test builds.
UPnP stopped working after upgrading to rc37... Any suggestions? I'm dead in the water.
Re: The Dude, v6.36rc test builds.
Do you have a link to let me roll back my 3011 to rc30? The new build broke my UPnP and now my Plex isn't working. I just want to get it working again and rc30 worked great.
Thanks.
Thanks.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
kd6icz - Please send supout file from your device to support@mikrotik.com. UPnP in general is working with this version in our lab. Seems like it should be something specific.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Version 6.36rc39 has been released.
Changes since previous version:
*) chr - fixed CHR seeing its own system disk mounted as additional data disk;
*) dude - (changes discussed here: forum.mikrotik.com/viewtopic.php?f=8&t=108083);
*) ethernet - fixed incorrect ether1 link speed after reboot on rb4xx series routers;
*) firewall - fixed interface list matcher showing incorrect name for NAT rules;
*) lte - added support for ZTE ZM8620;
*) lte - added use-peer-dns option (will work only combined with add-default-route);
*) netinstall - fixed netinstall and cd install for x86 (broken since 6.36rc27);
*) pppoe - do not allow to send out bigger packets than l2mtu if mrru is provided;
*) rb2011 - fixed ether6-ether10 flapping when two ports from both switch chips are in the same bridge;
*) winbox - added arp-timeout setting to all ethernet like interfaces;
*) winbox - added domain name support for IPv6 address list;
*) winbox - do not allow to specify vlan-mode=no-tag in capsman datapath config;
*) winbox - do not show mode setting for WDS interfaces;
*) winbox - fixed crash when using ctrl+d;
*) winbox - make local-address optional for eoipv6, 6to4, ipip, ipipv6 & grev6;
*) winbox - renamed IPv6 "Raw rules" section to "Raw";
*) winbox - set default sa-learning value to "yes" for CRS Ingress VLAN Translation rules;
*) wireless - fixed multiple wireless packages enabled at the same time after upgrade;
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash
Changes since previous version:
*) chr - fixed CHR seeing its own system disk mounted as additional data disk;
*) dude - (changes discussed here: forum.mikrotik.com/viewtopic.php?f=8&t=108083);
*) ethernet - fixed incorrect ether1 link speed after reboot on rb4xx series routers;
*) firewall - fixed interface list matcher showing incorrect name for NAT rules;
*) lte - added support for ZTE ZM8620;
*) lte - added use-peer-dns option (will work only combined with add-default-route);
*) netinstall - fixed netinstall and cd install for x86 (broken since 6.36rc27);
*) pppoe - do not allow to send out bigger packets than l2mtu if mrru is provided;
*) rb2011 - fixed ether6-ether10 flapping when two ports from both switch chips are in the same bridge;
*) winbox - added arp-timeout setting to all ethernet like interfaces;
*) winbox - added domain name support for IPv6 address list;
*) winbox - do not allow to specify vlan-mode=no-tag in capsman datapath config;
*) winbox - do not show mode setting for WDS interfaces;
*) winbox - fixed crash when using ctrl+d;
*) winbox - make local-address optional for eoipv6, 6to4, ipip, ipipv6 & grev6;
*) winbox - renamed IPv6 "Raw rules" section to "Raw";
*) winbox - set default sa-learning value to "yes" for CRS Ingress VLAN Translation rules;
*) wireless - fixed multiple wireless packages enabled at the same time after upgrade;
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Code: Select all
/ip firewall nat
add action=masquerade chain=srcnat out-interface=!pppoe-out1 src-address=\
192.168.88.8This rule itself is outside the limit of pppoe-out1, why pppoe-out1 will fail after the break.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Upgrade to rc39 changed all my FILTER-Firewall rules with interface-lists to "unknown", resulting in a not working
internet connection after the upgrade. NAT-Rules seem to be corrected, as this changelog tells.
I'm currently manually correcting them for 400 rules. My last compact-export is 6 days old.
internet connection after the upgrade. NAT-Rules seem to be corrected, as this changelog tells.
I'm currently manually correcting them for 400 rules. My last compact-export is 6 days old.
*) firewall - fixed interface list matcher showing incorrect name for NAT rules;
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
works fine on sxt lte. thanks (Ticket#2016062466000121)*) lte - added use-peer-dns option (will work only combined with add-default-route);
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
I see 90% of cpu load on hap ac lite, firewall drop and udp-flood about 25k p/s at 100mbit. On other router (EdgeRouter X) cpu load about 6%... tested with beststresser at 100mbit channel. Some people see 100% cpu load on hap ac at ~200mbit udp flood (firewall drop, not routing!)...
I can email profile screenshot.
I can email profile screenshot.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Don't you have dns service opened to the wan port, do you?
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Version 6.36rc40 has been released.
Changes since previous version:
*) dude - (changes discussed here: forum.mikrotik.com/viewtopic.php?f=8&t=108083);
*) lte - fixed modem network configuration version checks;
*) nat - fixed nat rule disappearance after reboot if interface-list was used (introduced in 6.36rc39);
*) pppoe - allow to set MTU and MRU higher than 1500 for PPPoE;
*) tunnel - fixed rare crash by specifying minimal header length immediately at tunnel initialization;
*) winbox - added 2ghz-g/n band for wireless-rep;
*) winbox - added icons to bridge filter actions similar to ip firewall;
*) winbox - do not show filter for combined fields like bgp-vpn4 RD;
*) winbox - improve filtering on list fields;
*) winbox - show action column as first in bridge firewall;
*) winbox - show error when telnet is not allowed because of permissions;
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash
Changes since previous version:
*) dude - (changes discussed here: forum.mikrotik.com/viewtopic.php?f=8&t=108083);
*) lte - fixed modem network configuration version checks;
*) nat - fixed nat rule disappearance after reboot if interface-list was used (introduced in 6.36rc39);
*) pppoe - allow to set MTU and MRU higher than 1500 for PPPoE;
*) tunnel - fixed rare crash by specifying minimal header length immediately at tunnel initialization;
*) winbox - added 2ghz-g/n band for wireless-rep;
*) winbox - added icons to bridge filter actions similar to ip firewall;
*) winbox - do not show filter for combined fields like bgp-vpn4 RD;
*) winbox - improve filtering on list fields;
*) winbox - show action column as first in bridge firewall;
*) winbox - show error when telnet is not allowed because of permissions;
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after crash
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
No, this is service beststresser.com. My firewall:Don't you have dns service opened to the wan port, do you?
Code: Select all
/ip firewall filter
add action=accept chain=input comment="default configuration" connection-state=established,related \
log-prefix=""
add action=accept chain=input comment="default configuration" icmp-options=!5:0-255 log-prefix="" \
protocol=icmp
add action=accept chain=input comment="igmp proxy" log-prefix="" protocol=igmp
add action=accept chain=input comment=traceroute connection-state=new dst-port=33430-33530 \
log-prefix="" protocol=udp
add action=drop chain=input comment="default configuration" in-interface=wan1 log-prefix=""
add action=fasttrack-connection chain=forward comment="default configuration" connection-state=\
established,related log-prefix=""
add action=accept chain=forward comment="default configuration" connection-state=established,related \
log-prefix=""
add action=drop chain=forward comment="default configuration" connection-state=invalid log-prefix=""
add action=drop chain=forward comment="default configuration" connection-nat-state=!dstnat \
connection-state=new in-interface=wan1 log-prefix=""Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Hello MTguys
I know Mikrotik has changed the ARP menu to show incomplete ARP entries, now we see 00:00:00:00:00:00 as ARP for non used IP addresses.
However, sometimes this behavior doesn't help, for example, a quick MAC auditing/counting. The default behavior for a lot of years has been changed.

Please, could you make a new setting inside IP -> Settings to hide incomplete ARP entries?

As you can see, mine is already enabled!
Thank you!
I know Mikrotik has changed the ARP menu to show incomplete ARP entries, now we see 00:00:00:00:00:00 as ARP for non used IP addresses.
However, sometimes this behavior doesn't help, for example, a quick MAC auditing/counting. The default behavior for a lot of years has been changed.

Please, could you make a new setting inside IP -> Settings to hide incomplete ARP entries?

As you can see, mine is already enabled!
Thank you!
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Code: Select all
/ip firewall nat
[size=85][font=monospace]add action=masquerade chain=srcnat out-interface=!pppoe-out1 src-address=\[/font][/size]
192.168.88.8-

-
diablothebest
newbie
- Posts: 31
- Joined:
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Please Fix WebFig to correct view in ActiveConnections menu




Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
does anyone else had not working "Manual/Wiki" within WinBox since rc40? (on say HAP and HEX for example)
its not big deal, but quite unusual/infrequent for.
but delay/netflow jitter kinda decreased(unlikely MT backported some patches to kernel, but build with different config kinda may had same impact in countering bloatbuffering).
its not big deal, but quite unusual/infrequent for.
but delay/netflow jitter kinda decreased(unlikely MT backported some patches to kernel, but build with different config kinda may had same impact in countering bloatbuffering).
Last edited by Zorro on Sun Jul 17, 2016 1:45 pm, edited 1 time in total.
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Guys, does not work (6.36rc40, wirwless-rep - yes)
Please check.
Thank you!
Code: Select all
/ interface wireless scan 0 save-file = fileThank you!
Re: The Dude, v6.36rc test builds.
Firewall rules with interface list is not updated to version 6.36rc40
After the update: add action=accept chain=input in-interface-list="" log-prefix=""
Code: Select all
[admin@MikroTik-CHR-Dude] > /interface export compact
# jul/19/2016 15:29:29 by RouterOS 6.36rc30
# software id =
#
/interface list
add name=TEST
/interface list member
add interface=ether1 list=TEST
admin@MikroTik-CHR-Dude] > /ip firewall export compact
# jul/19/2016 15:29:36 by RouterOS 6.36rc30
# software id =
#
/ip firewall filter
add action=accept chain=input in-interface-list=TEST log-prefix=""Code: Select all
[admin@MikroTik-CHR-Dude] > /interface export compact
# jul/19/2016 15:31:53 by RouterOS 6.36rc40
# software id =
#
/interface list
add name=TEST
/interface list member
add interface=ether1 list=TEST
admin@MikroTik-CHR-Dude] > /ip firewall export compact
# jul/19/2016 15:32:01 by RouterOS 6.36rc40
# software id =
#
/ip firewall filter
add action=accept chain=input in-interface-list="" log-prefix=""Re: The Dude, v6.36rc test builds.
Same here... router was not accessible after upgrade because of this. I had to write a script to manually add all interface-lists from a rc38 backup-file again.After the update: add action=accept chain=input in-interface-list="" log-prefix=""
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
About interface list issue. While developing this feature we had to make some changes and now it works little bit differently than it did before. In rc40 you might lose inteface-list matcher value on firewall, but, if you will set it back, then in future after upgrades you should not lose it any more
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
So I upgraded from 6.35.2 to 6.36rc40 and now OSPFv3 doesn´t redistribute any connected routes, although I can see any other external routes but without any gateway displayed within Routing => OSPFv3 => Routes State is shown "full".
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
strods, where your programmers found BROADCASTS addresses in IPv6?
Why in this configuration
ipv6 stack reply ITSELF for pings?
Same for stable branch.
Why in this configuration
Code: Select all
/ipv6 address add address=fc00::1/126 advertise=no interface=vlan4091Code: Select all
[admin@MikroTik] > ping fc00::0 count=5
SEQ HOST SIZE TTL TIME STATUS
0 fc00::1 56 64 0ms echo reply
1 fc00::1 56 64 0ms echo reply
2 fc00::1 56 64 0ms echo reply
3 fc00::1 56 64 0ms echo reply
4 fc00::1 56 64 0ms echo reply
sent=5 received=5 packet-loss=0% min-rtt=0ms avg-rtt=0ms max-rtt=0ms
Re: v6.36rc [release candidate] is released, wireless-fp package is discontinued!
Version 6.36 [current] has been released:
http://forum.mikrotik.com/viewtopic.php ... 88#p548188
http://forum.mikrotik.com/viewtopic.php ... 88#p548188





