And news from our test.
Generally, at 6.40rc2, with Rostelecom working too! Bottom details in russian.
Итак, господа, настало счастье для пользователей УЦН - оно работает, но прочитайте текст ниже, чтобы сходу не наступить на грабли.
У РТ есть какая-то привязка. После подключения под МАСом "Альфа" нельзя сразу подключаться с другого девайса с МАСом "Бета".
То есть, склонируйте МАС-адрес на Микротик во избежании проблем, если совсем недавно подключались с какого-то другого девайса. То же самое касается тех, кто будет использовать виртуальные интерфейсы с МАС-адресами, отличными от того, который чуть ранее выходил в сеть (если выходил).
Еще раз на пальцах: Настраиваем интерфейс, успешно подключаемся, отключаем интерфейс, меняем МАС и больше не можем подключиться - будет ошибка
802.1x authentication timeout, словно введен неверный логин/пароль или не поддерживается PEAP.
Мой рабочий конфиг выглядел так:
/interface wireless security-profiles
set [ find default=yes ] supplicant-identity=MikroTik
add authentication-types=wpa2-eap eap-methods=peap management-protection=allowed mode=dynamic-keys mschapv2-password=pasW0000000rd mschapv2-username=7700000006 name=7700000006 supplicant-identity=7700000006 tls-mode=dont-verify-certificate
/interface wireless
set [ find default-name=wlan1 ] band=2ghz-b/g/n channel-width=20/40mhz-Ce disabled=no frequency=auto security-profile=7700000006 ssid=RTWiFi wps-mode=disabled
Дальше получаем на интерфейса адрес и натим.
Спасибо
Uldis за поддержку.
Какие схемы работают, а какие нет (на всех схемах опечатка - virtial читать как virtual):
РАБОТАЕТ:
 НЕ
НЕ работает:
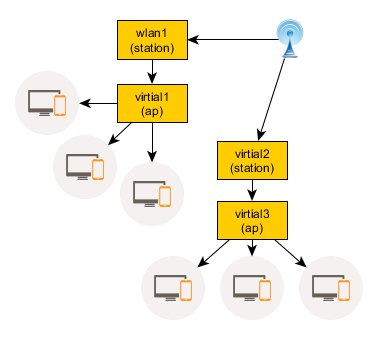
wlan1 и virtual2 успешно получают адреса по DHCP, но шлюз видят только через один из интерфейсов. Через оба сразу трафик не побежит (L2 с AP по второму подключению не работает, кроме DHCP).
Все извраты с попыткой уйти от маршрутизации и обойтись псевдобриджом также не помогают - ну не работает 2 одновременных station подключения.
Если Микротик сможет это пофиксить - будет здорово!
Сейчас объясню почему это так важно.


Если все будут жить под мачтой и пользоваться услугой сидя под столбом - вопросов нет.
Но до жилых домов расстояние больше, чем зона покрытия.
Мы сделали большой шаг, чтобы зацепиться за точку доступа, уже можно использовать SXT для приема сигнала, но что делать, если расстояние слишком большое?
Тогда нужно терминировать много-много клиентов на одной SXT, дотянуть их до места распределения, примерно так:

Для реализации схемы не хватает капельки чуда












