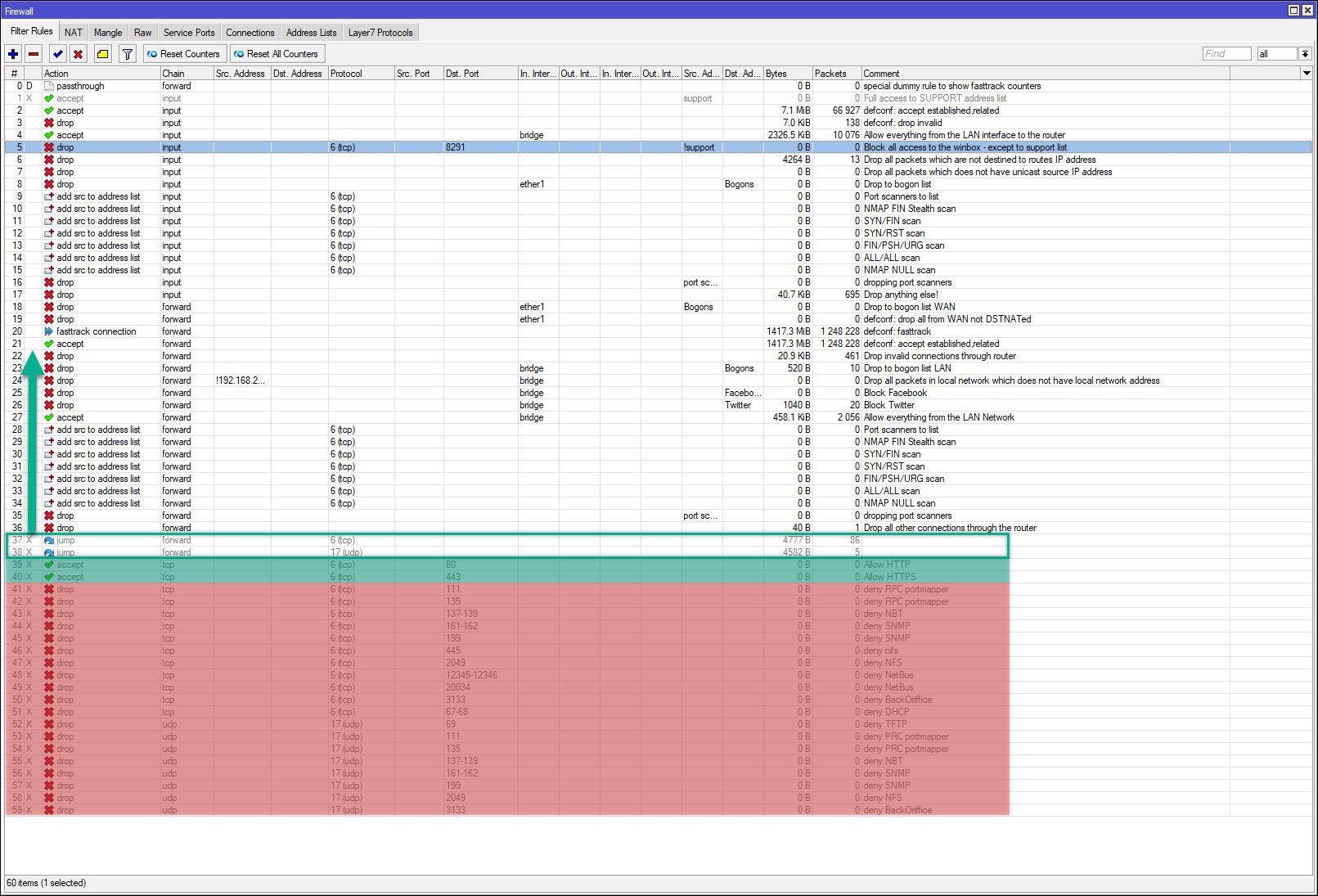
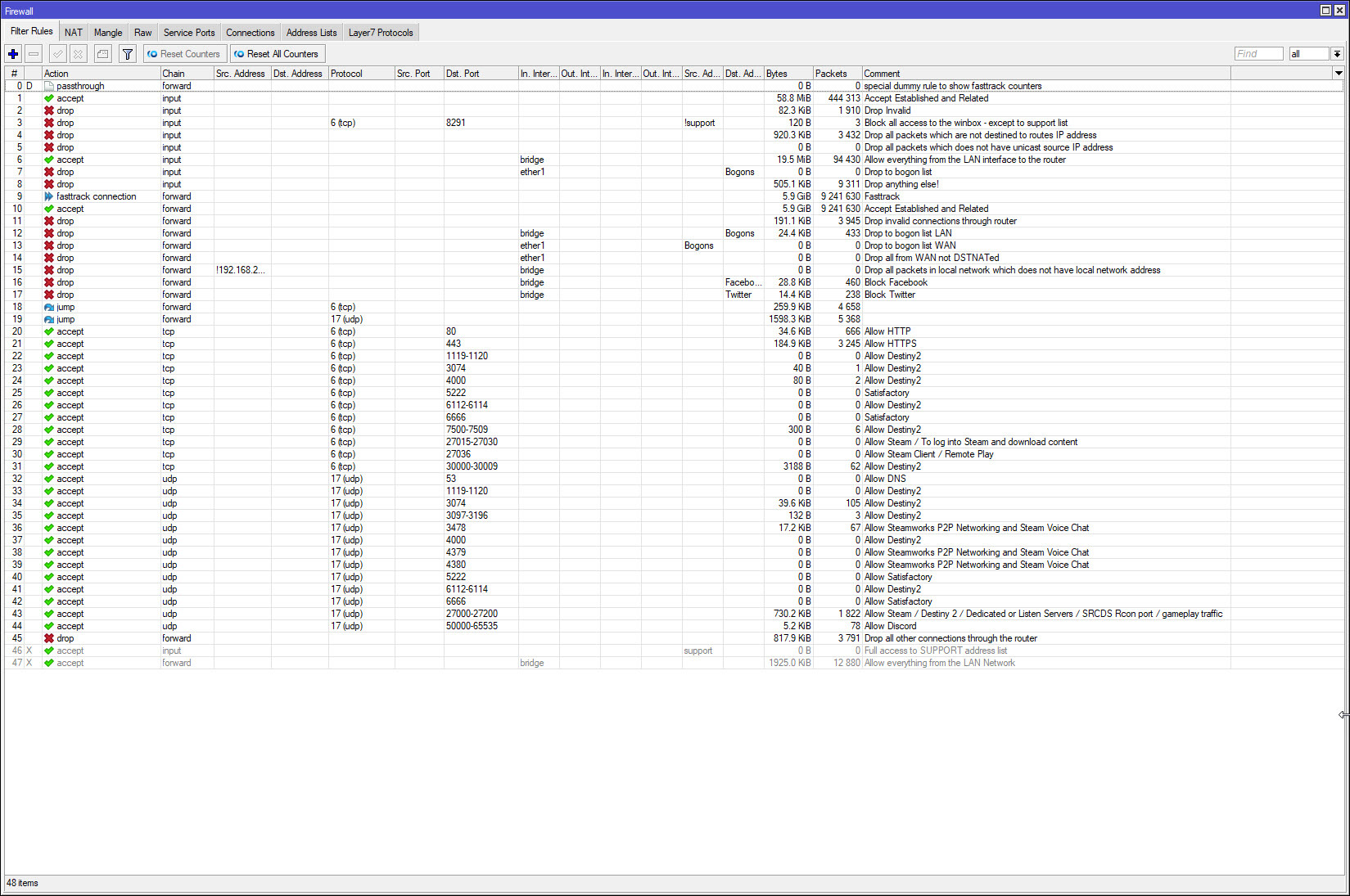
First of all, what chain does what. Traffic that is destined to something on the router itself (Winbox, SSH to the router, etc) is affected by the INPUT chain.
Traffic that is destined to something other than the router but has to be routed through the router (A PC accessing a web page, etc) is affected by the FORWARD chain.
Traffic that is originates from the router itself (The router making a DNS or SNTP query, etc) is affected by the OUTPUT chain. Very often there is nothing in the Output chain.
The order of rules within a chain is critical. Rules are processed in order. With the exception of a couple of rule types (passthrough for example), as soon as a rule accepts a packet, the rest of that chain is ignored. So for example if I have a rule that accepts all TCP traffic, and the next rule drops TCP traffic on port 2020, the second rule will never drop because the first rule will have already accepted it. Although you CAN mix chains - HOWEVER, DON'T DO IT. The router does not care, and it won't affect operation at all, however it makes the rules FAR harder for us poor humans to read.
If a packet gets to the end of a chain and still has not been accepted or deleted, that packet will be accepted. Therefore, it is essential to put a drop everything rule at the end of each chain. The general concept that most of us use is to explicitly allow what we want to allow and let the drop all at the end drop the packets.
Here are a couple of specifics:
add action=accept chain=input comment=\
"Allow everything from the LAN interface to the router" in-interface=\
bridge
add action=drop chain=input comment="Block all access to the winbox - except t\
o support list" dst-port=8291 protocol=tcp src-address-list=!support
The first rule will allow any local address full access to the router. The second rule blocks WinBox access except for selected addresses. Wrong order. The first rule will have allowed the access and the second rule will not every be seen.
add action=drop chain=input comment=\
"Drop all packets which are not destined to routes IP address" \
dst-address-type=!local
I assume you really meant ... router's IP address". If the pocket is not destined to the router, it won';t be in the input chain.
add action=drop chain=input comment=\
"Drop all packets which does not have unicast source IP address" \
src-address-type=!unicast
What about a DHCP request? That is a broadcast a I recall.
add action=drop chain=input comment="Drop to bogon list" dst-address-list=\
Bogons in-interface=ether1
That one is a major debate. Some people will tell you that this is absolutely essential, and some people don't care. I can tell you that I had Bogon drop rules in my routers for several years, and NEVER counted a single packet. So is it important?
You went to great effort to drop twitter and facebook by blocking screen fulls of IP addresses. Unless you have a way to keep that up to date, my guess is that it will only be partially effective - and may well block other stuff over time.
add action=drop chain=forward comment=\
"Drop all other connections through the router"
add action=jump chain=forward disabled=yes jump-target=tcp protocol=tcp
add action=jump chain=forward disabled=yes jump-target=udp protocol=udp
You are dropping all traffic that gets this far in the Forward chain, and then have two more rules that will never see traffic because of the drop all rule (and they are disabled - along with all the rules in the TCP and UDP chains - so maybe those were put in for some testing only).