From Mikrotik to Ubiquiti UniFi and back to Mikrotik
Hello all, it's ben a good while since I've been on here!
Way-back-when I had a RB2011UiAS-2HnD-IN which I used as my main home router. This was connected to a pair of VDSL services via the two providers supplied 'broadband routers', with me using the RB2011 to load balance between the two among other things. At that time I was using some old Cisco LAN switches and APs that I'd managed to collect during my time working in the networking industry for far too many years.
Then I discovered UniFi and liked the glossy look of it and firstly changed to their APs then I got one of their LAN switches then finally (the biggest mistake) was to swap the RB2011 out for their USG (router). I think I was influenced by their nice app and interface and how it was all joined up in one place, which it is. However during the time that I've had the UniFi setup it's not been the most reliable thing, I've had a number of random issues and the frustrating thing is that often their shiny application doesn't show that anything is wrong, when there plainly is. The other issue is the functionality is limited via their interface and seems to be developing in features very slowly. Lastly the load-balancing has never worked properly for me. Yes you can do stuff under the hood (in their difficult to understand CLI) but you have to mess about to stop the controller (which is part of their solution) overwriting the under-the-hood changes that you have done. So I think it's time to come back to Mikrotik where you can configure pretty much whatever you want and with a proper CLI!
So (finally) to my question(s).
I currently have 3 x AP-AC-LR APs an 8-port US-8-60W PoE switch (still using an old Cisco PoE switch too), the USG router and their controller (running on W10). This solution is for my home (including home office) and I will be connecting to my 2 x VDSL services as before (both with <20Mbps download).
My thoughts are as follows:
RB4011iGS+RM
3 x cAP ac
2 x hEX PoE (to provide PoE to the APs and also some CCTV) - then possibly still using my old Cisco switch too
Or do I collapse the routing and switching into just a CRS328-24P-4S+RM (I assume this has a fan, I would like fanless)
Or maybe the CRS112-8P-4S-IN & CSS326-24G-2S+RM
What I don't know is what's the key differences between the RB4011iGS+RM, CRS328-24P-4S+RM & CRS112-8P-4S-IN in relation to their routing capability. I can see that the RB4011 seems to be a lot more powerful. I will be wanting to use the router for CAPsMAN too.
One thing I noticed is that the these newer routers (compared to the RB2011) don't have USB ports (I seem to recall the recommendation with the RB2011 to use a USB memory stick to avoid wearing out the internal storage, is this not an issue anymore?)
Any comments/thoughts appreciated.
Way-back-when I had a RB2011UiAS-2HnD-IN which I used as my main home router. This was connected to a pair of VDSL services via the two providers supplied 'broadband routers', with me using the RB2011 to load balance between the two among other things. At that time I was using some old Cisco LAN switches and APs that I'd managed to collect during my time working in the networking industry for far too many years.
Then I discovered UniFi and liked the glossy look of it and firstly changed to their APs then I got one of their LAN switches then finally (the biggest mistake) was to swap the RB2011 out for their USG (router). I think I was influenced by their nice app and interface and how it was all joined up in one place, which it is. However during the time that I've had the UniFi setup it's not been the most reliable thing, I've had a number of random issues and the frustrating thing is that often their shiny application doesn't show that anything is wrong, when there plainly is. The other issue is the functionality is limited via their interface and seems to be developing in features very slowly. Lastly the load-balancing has never worked properly for me. Yes you can do stuff under the hood (in their difficult to understand CLI) but you have to mess about to stop the controller (which is part of their solution) overwriting the under-the-hood changes that you have done. So I think it's time to come back to Mikrotik where you can configure pretty much whatever you want and with a proper CLI!
So (finally) to my question(s).
I currently have 3 x AP-AC-LR APs an 8-port US-8-60W PoE switch (still using an old Cisco PoE switch too), the USG router and their controller (running on W10). This solution is for my home (including home office) and I will be connecting to my 2 x VDSL services as before (both with <20Mbps download).
My thoughts are as follows:
RB4011iGS+RM
3 x cAP ac
2 x hEX PoE (to provide PoE to the APs and also some CCTV) - then possibly still using my old Cisco switch too
Or do I collapse the routing and switching into just a CRS328-24P-4S+RM (I assume this has a fan, I would like fanless)
Or maybe the CRS112-8P-4S-IN & CSS326-24G-2S+RM
What I don't know is what's the key differences between the RB4011iGS+RM, CRS328-24P-4S+RM & CRS112-8P-4S-IN in relation to their routing capability. I can see that the RB4011 seems to be a lot more powerful. I will be wanting to use the router for CAPsMAN too.
One thing I noticed is that the these newer routers (compared to the RB2011) don't have USB ports (I seem to recall the recommendation with the RB2011 to use a USB memory stick to avoid wearing out the internal storage, is this not an issue anymore?)
Any comments/thoughts appreciated.
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
Keep ubiquiti for Wi-Fi, replace USG with RB4011 for routing.
Mikrotik wifi will be considerably slower than ubiquiti, especially with capsman.
CRS devices are meant to be used as switches. They can do routing, but performance will be slow.
Mikrotik wifi will be considerably slower than ubiquiti, especially with capsman.
CRS devices are meant to be used as switches. They can do routing, but performance will be slow.
-

-
simplextech
just joined
- Posts: 5
- Joined:
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
Very interested in this as I have nearly the same scenario at home that I'm looking to move to Mikrotik.
I've seen throughout the forum that Unifi AP's are faster but to what degree?
I'm limited by a rural DSL line and LTE modems I use. I plan on using a Hex S to load balance the connectiosn but even then I'm highly unlikely to notice any "speed" difference from a Mikrotik vs Unifi AP.... but I'm interested in hearing other reasons to keep the Unifi AP's.
I've seen throughout the forum that Unifi AP's are faster but to what degree?
I'm limited by a rural DSL line and LTE modems I use. I plan on using a Hex S to load balance the connectiosn but even then I'm highly unlikely to notice any "speed" difference from a Mikrotik vs Unifi AP.... but I'm interested in hearing other reasons to keep the Unifi AP's.
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
Hi all,
I am very interested in this topic also. I have an almost all Unifi setup also and was looking at replacing the USG-3P. I was looking for something that might support Wireguard or something better than the L2TP VPN built into the USG for connecting to my network when I am away. I was thinking maybe get something to play with to see if RouterOS would fit my needs (the online demo looks like a steep learning curve). the 4011 was mentioned in this post but could I get something cheaper to play and move to the 4011 if it works out? Would the hEX S work? I dont think the L4 vs L5 would make a difference to me. Also, can I assume that if I buy the hardware, the license comes with it?
Here is my current setup...
USG-3P --> US-16-150W --> 2x - UAP-nanoHD
TP-Link EAP-225 also
i have 3 networks configured in the system. 1 VPN, 1 main network and 1 VLAN for all my IoT devices.
Thanks for any advice you can provide.
CyBuzz
I am very interested in this topic also. I have an almost all Unifi setup also and was looking at replacing the USG-3P. I was looking for something that might support Wireguard or something better than the L2TP VPN built into the USG for connecting to my network when I am away. I was thinking maybe get something to play with to see if RouterOS would fit my needs (the online demo looks like a steep learning curve). the 4011 was mentioned in this post but could I get something cheaper to play and move to the 4011 if it works out? Would the hEX S work? I dont think the L4 vs L5 would make a difference to me. Also, can I assume that if I buy the hardware, the license comes with it?
Here is my current setup...
USG-3P --> US-16-150W --> 2x - UAP-nanoHD
TP-Link EAP-225 also
i have 3 networks configured in the system. 1 VPN, 1 main network and 1 VLAN for all my IoT devices.
Thanks for any advice you can provide.
CyBuzz
Last edited by CyBuzz on Thu Sep 10, 2020 12:46 am, edited 2 times in total.
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
Hi all
Well, I skipped the hEX S and I received the RB4011 last night and have started to play around with it. I think this will be a steep learning curve since I am not a network expert and just a tinkerer. Here is what I did and the list of things I need to figure out since Ubiquiti made it so easy. I understand though from reading on here that the hardware is much better than the USG.
My Setup:
I realize the RB4011 connected to the USG is not good and eventually the USG will be replaced with the RB4011. The stuff connected to my USG(Lan1) will eventually be moved over to my RB4011(WAN2/LAN2) but had to leave this up while I am figuring stuff out since we work from home.
LAN1
Cable Modem -> USG-3P(LAN1) -> TP-Link(TL-SG108E) |-> UAP-NanoHD(1)(4 SSIDs: A(disabled, was IoT), B, C & D) & UCK1 &
Other Clients
WAN2/LAN2
Cable Modem -> USG-3P(WAN2/LAN2) -> RB4011(Port1) -> RB4011(Port 6) -> US16-150W -> UAP-NanoHD(2)(2 SSIDs: E & F) & Other clients & Netgear GS208 -> other clients(some wired IoT devices)
Cable Modem -> USG-3P(WAN2/LAN2) -> RB4011(Port1) -> RB4011(Port 8) -> UnRaid server(runs UnifiController to manage UAP-Nanohd(2) and US16-150W)
Cable Modem -> USG-3P(WAN2/LAN2) -> RB4011(Port1) -> RB4011(Port 10) -> TP-Link EAP225(2 SSIDs: G & H)
Networks:
USG
LAN1: 192.168.XX.XX/24
WAN2/LAN2: 10.10.YY.YY/24
RB4011
WAN: 10.10.YY.YY
LAN: 192.168.ZZ.ZZ/24 (Bridge)
My Goals:
1. Get everything moved from USG to RB4011 (weekend or late night to avoid downtime)
2. Isolate my IoT(SSID E) network so that my wireless IoT devices only have internet access and no access into the LAN but I can get to them from within the LAN.
3. Isolate wired IoT devices (Roku, Audio Receiver, Game Consoles) like wireless IoT devices
4. Migrate SSIDs from UAP-NanoHD(1) to UAP-NanoHD(2)
5. Remove the USG-3p from the setup and only use the 4011 router
6. Set up some sort of VPN (I liked being able to connect into the home network when away with the USG)5.
7. Set up RADIUS server (had one on USG) for authentication for VPN if needed
8. Clean up the mess of the space where all this hardware is located :-)
9. Document/Label ports so I dont spend so much time tracing cables.
Right now the thing I am most concerned with and dont have a clue how to implement is isolation of the IoT devices. It was easy on the Ubiquiti stuff, not so much here.
Thanks for reading everyone. If anyone has insight, I welcome it. I will be digging through these forums as much as I can.
CyBuzz
Well, I skipped the hEX S and I received the RB4011 last night and have started to play around with it. I think this will be a steep learning curve since I am not a network expert and just a tinkerer. Here is what I did and the list of things I need to figure out since Ubiquiti made it so easy. I understand though from reading on here that the hardware is much better than the USG.
My Setup:
I realize the RB4011 connected to the USG is not good and eventually the USG will be replaced with the RB4011. The stuff connected to my USG(Lan1) will eventually be moved over to my RB4011(WAN2/LAN2) but had to leave this up while I am figuring stuff out since we work from home.
LAN1
Cable Modem -> USG-3P(LAN1) -> TP-Link(TL-SG108E) |-> UAP-NanoHD(1)(4 SSIDs: A(disabled, was IoT), B, C & D) & UCK1 &
Other Clients
WAN2/LAN2
Cable Modem -> USG-3P(WAN2/LAN2) -> RB4011(Port1) -> RB4011(Port 6) -> US16-150W -> UAP-NanoHD(2)(2 SSIDs: E & F) & Other clients & Netgear GS208 -> other clients(some wired IoT devices)
Cable Modem -> USG-3P(WAN2/LAN2) -> RB4011(Port1) -> RB4011(Port 8) -> UnRaid server(runs UnifiController to manage UAP-Nanohd(2) and US16-150W)
Cable Modem -> USG-3P(WAN2/LAN2) -> RB4011(Port1) -> RB4011(Port 10) -> TP-Link EAP225(2 SSIDs: G & H)
Networks:
USG
LAN1: 192.168.XX.XX/24
WAN2/LAN2: 10.10.YY.YY/24
RB4011
WAN: 10.10.YY.YY
LAN: 192.168.ZZ.ZZ/24 (Bridge)
My Goals:
1. Get everything moved from USG to RB4011 (weekend or late night to avoid downtime)
2. Isolate my IoT(SSID E) network so that my wireless IoT devices only have internet access and no access into the LAN but I can get to them from within the LAN.
3. Isolate wired IoT devices (Roku, Audio Receiver, Game Consoles) like wireless IoT devices
4. Migrate SSIDs from UAP-NanoHD(1) to UAP-NanoHD(2)
5. Remove the USG-3p from the setup and only use the 4011 router
6. Set up some sort of VPN (I liked being able to connect into the home network when away with the USG)5.
7. Set up RADIUS server (had one on USG) for authentication for VPN if needed
8. Clean up the mess of the space where all this hardware is located :-)
9. Document/Label ports so I dont spend so much time tracing cables.
Right now the thing I am most concerned with and dont have a clue how to implement is isolation of the IoT devices. It was easy on the Ubiquiti stuff, not so much here.
Thanks for reading everyone. If anyone has insight, I welcome it. I will be digging through these forums as much as I can.
CyBuzz
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
Good article how to setup the RB4011 device for vlans etc.......
I too would stick with other vendors wifi and get the wired only RB4011.
viewtopic.php?f=23&t=143620
I too would stick with other vendors wifi and get the wired only RB4011.
viewtopic.php?f=23&t=143620
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
Thanks for all that information. I have read through it twice and think it will take another to see how it applies specifically to my devices. This is going to take some time.Good article how to setup the RB4011 device for vlans etc.......
I too would stick with other vendors wifi and get the wired only RB4011.
viewtopic.php?f=23&t=143620
CyBuzz
-

-
StubArea51
Trainer

- Posts: 1742
- Joined:
- Location: stubarea51.net
- Contact:
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
Consider using the Audience.
MikroTik audience is fantastic for home WiFi....I have three of them as APs/MPLS routers and use a CRS328 for switching with a CCR1009 to connect to symmetric 1G fiber. Then I use OSPF/MPLS to build VPLS for the main and IoT SSIDs.
I hope we'll see MikroTik continue to add wireless features and improve performance to grab market share away from the Ubnt dumspter fire.
This is my simple home network with MikroTik wireless ;)
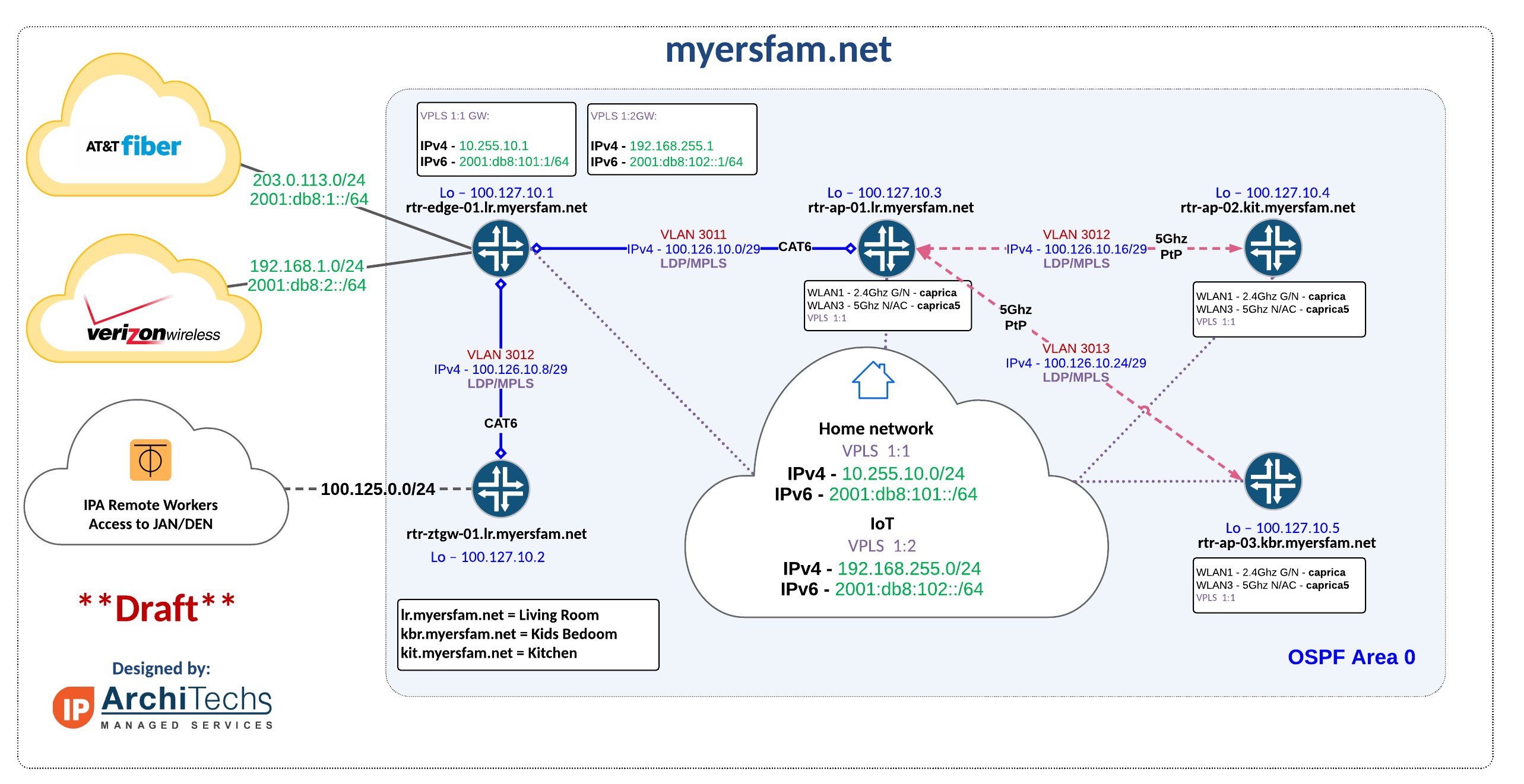
MikroTik audience is fantastic for home WiFi....I have three of them as APs/MPLS routers and use a CRS328 for switching with a CCR1009 to connect to symmetric 1G fiber. Then I use OSPF/MPLS to build VPLS for the main and IoT SSIDs.
I hope we'll see MikroTik continue to add wireless features and improve performance to grab market share away from the Ubnt dumspter fire.
This is my simple home network with MikroTik wireless ;)

Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
Hey IPANet, how do you compare audience to previous wifi like on capac etc....
Also do you have to run the beta software to gain the advantages?
I dont see anything extraordinary about them except the high price for just a wifi5 AP.
Call me a sceptic but where is the gain in using these.......... Doesnt look wall mountable much either.
Also do you have to run the beta software to gain the advantages?
I dont see anything extraordinary about them except the high price for just a wifi5 AP.
Call me a sceptic but where is the gain in using these.......... Doesnt look wall mountable much either.
Last edited by anav on Fri Jul 09, 2021 10:33 pm, edited 1 time in total.
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
IPANetEngineer, thank you for the information. I will take a look in the future however my goal is to replace my Ubiquiti USG with the RB4011 that I purchased. I do not intend to replace my Ubiquiti APs or Switch or any other hardware unless I have to (incompatibility or failure) so I am going to try and work with what I have.Consider using the Audience.
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
Well whoo hoooo! I was able to create a VLAN on the RB4011 with all the other stuff (Network, dhcp server, firewall rule, etc.) from reading reading reading....this forum is awesome. I was then able to set my 2 APs to have an SSID with that VLAN for IoT stuff and get that all configured so they can talk to the internet but not talk to anything on the rest of my network. I am far from done but feel accomplished with this success however i am not sure why it all works....but it does :-D
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
Good news, if you want a review of your config thus far
/export hide-sensitive file=anynameyouwish
/export hide-sensitive file=anynameyouwish
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
Mikrotik kills Ubnt when it comes to routing. However their APs are really good.
The CRS328 has a good enough CPU for a handle a NAT and firewall for at least a 100/100M connection.
The CRS328 has a good enough CPU for a handle a NAT and firewall for at least a 100/100M connection.
-

-
toxicfusion
Member

- Posts: 326
- Joined:
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
I have dumped Ubiquiti Wi-Fi for my personal and all by clients. It is now all MikroTik for Routing + Wifi [Always used MikroTik for routing....]. Some clients I will use TP-LinK EAP access points; they are nearly identical to Unifi but more stable..... hint.Keep ubiquiti for Wi-Fi, replace USG with RB4011 for routing.
Mikrotik wifi will be considerably slower than ubiquiti, especially with capsman.
CRS devices are meant to be used as switches. They can do routing, but performance will be slow.
MikroTik Wifi can be just as fast as UBT consumer. All about configuration, [channel config, AP placement is key!]. MikroTik will be more stable and in my experience, better radio sensitivity. YMMV!!!
The RB4011 is a great router, powerful. Be sure to run routerOS 4.57.10 - fixes stablility the stability issues some had . The RB4011 will not break a sweat running CapsMAN.
Use CapsMAN with LOCAL FORWARDING ON!. Otherwise, performance will be SHI*%.
In regards to switching. Go with a Regular CRS instead of the HEX units. CRS running SwOS will be easier to manage. HEX's are great, just use switch CHIP or configure CPU based vlan with bridge method. Or, keep your Unifi Switch until it dies [it will]. Use Any Smart managed PoE switch of your pick.
-

-
toxicfusion
Member

- Posts: 326
- Joined:
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
I agree 100% with your statements. I'm waiting for MT to release new wireless devices, alongside of RouterOS 7. Time is near! Ubnt is very much dumpster fire; not to mention the data breach -- much worse than they publicly admit. I've dumped all Ubt products over year ago. Not looking back.Consider using the Audience.
MikroTik audience is fantastic for home WiFi....I have three of them as APs/MPLS routers and use a CRS328 for switching with a CCR1009 to connect to symmetric 1G fiber. Then I use OSPF/MPLS to build VPLS for the main and IoT SSIDs.
I hope we'll see MikroTik continue to add wireless features and improve performance to grab market share away from the Ubnt dumspter fire.
This is my simple home network with MikroTik wireless ;)

Ubt products are consumer toys with shiny interface. Easy to turn the knobs.
Yes - Folks running a WISP will argue otherwise. That is different story with the Ubt airfiber products. Or Move to Cambium [wisp].
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
I did this....but where is the file saved and how do i get to it?Good news, if you want a review of your config thus far
/export hide-sensitive file=anynameyouwish
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
I do not run WISP, but I do lots of wireless installations …’lots’. ….. UBNT wireless is excellent in FACT outstanding …. Tik Wireless is very POOR … VERY POOR. UBNT Has AI that works really well in mesh environments … how long before MikroTik will have AI … 10 yrs ???Ubt products are consumer toys with shiny interface. Easy to turn the knobs.
Yes - Folks running a WISP will argue otherwise. That is different story with the Ubt airfiber products. Or Move to Cambium [wisp].
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
Wow, this has been challenging. I think I have figured out much of what I wanted to do on my list. I feel accomplished since this isn't my trade. I am looking to this group in hopes you can look at my config and see if i did anything glaringly bad.
So, my list...
1. Done - Get everything moved from USG to RB4011 (weekend or late night to avoid downtime)
2. Done - Isolate my IoT(SSID E) network so that my wireless IoT devices only have internet access and no access into the LAN but I can get to them from within the LAN.
3. Done - had to figure out VLAN/PVID on my TL-SG108E - Isolate wired IoT devices (Roku, Audio Receiver, Game Consoles) like wireless IoT devices
4. Done - Migrate SSIDs from UAP-NanoHD(1) to UAP-NanoHD(2)
5. Done - Remove the USG-3p from the setup and only use the 4011 router
6. Done - Set up some sort of VPN (I liked being able to connect into the home network when away with the USG)5.
7. ToDo if needed - Set up RADIUS server (had one on USG) for authentication for VPN if needed
8. :-( Not looking forward to this - Clean up the mess of the space where all this hardware is located :-)
9. Started - Document/Label ports so I dont spend so much time tracing cables.
I have also added to the list of to-do items a few more things:
1. My UAP-nanoHDs both work fine however in the Controller (running in a docker on unraid) they both show as adopting. Since they work...not going to worry about that at the moment.
2. Figure out how to connect my switch to my router via SFP (Unifi is SFP and Switch is SFP+)
3. Play around with DNS. I use Pihole for local DNS and not sure i have the router set up right....but it works.
Anyway, for now, for what i know...it works as i want it to. Please take a look at my config and let me know if it is ok. If i am missing something, please let me know also.
So, my list...
1. Done - Get everything moved from USG to RB4011 (weekend or late night to avoid downtime)
2. Done - Isolate my IoT(SSID E) network so that my wireless IoT devices only have internet access and no access into the LAN but I can get to them from within the LAN.
3. Done - had to figure out VLAN/PVID on my TL-SG108E - Isolate wired IoT devices (Roku, Audio Receiver, Game Consoles) like wireless IoT devices
4. Done - Migrate SSIDs from UAP-NanoHD(1) to UAP-NanoHD(2)
5. Done - Remove the USG-3p from the setup and only use the 4011 router
6. Done - Set up some sort of VPN (I liked being able to connect into the home network when away with the USG)5.
7. ToDo if needed - Set up RADIUS server (had one on USG) for authentication for VPN if needed
8. :-( Not looking forward to this - Clean up the mess of the space where all this hardware is located :-)
9. Started - Document/Label ports so I dont spend so much time tracing cables.
I have also added to the list of to-do items a few more things:
1. My UAP-nanoHDs both work fine however in the Controller (running in a docker on unraid) they both show as adopting. Since they work...not going to worry about that at the moment.
2. Figure out how to connect my switch to my router via SFP (Unifi is SFP and Switch is SFP+)
3. Play around with DNS. I use Pihole for local DNS and not sure i have the router set up right....but it works.
Anyway, for now, for what i know...it works as i want it to. Please take a look at my config and let me know if it is ok. If i am missing something, please let me know also.
You do not have the required permissions to view the files attached to this post.
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
I've told TP-Link that I'll bitch about this issue and warn users with any chance I get but this is ridiculous, two in two days!
@CyBuzz see what I wrote here about TL-SG108E: viewtopic.php?f=2&t=175848#p863639
And below.. since @anav was talking about a totally different switch series.
@CyBuzz see what I wrote here about TL-SG108E: viewtopic.php?f=2&t=175848#p863639
And below.. since @anav was talking about a totally different switch series.
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
Yup I did find some threads about the SG108 series.I've told TP-Link that I'll bitch about this issue and warn users with any chance I get but this is ridiculous, two in two days!
@CyBuzz see what I wrote here about TL-SG108E: viewtopic.php?f=2&t=175848#p863639
And below.. since @anav was talking about a totally different switch series.
I believe their may be a work around and that is ensure the PVID of 1 is replaced by any other pvid if possible (at least for trunk or hybrid ports).
or flash netgear firmware on it......... (or get a switch that works somewhat to standard)
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
As for the config.
(1) This is new in that have not seen this set before......???
/ip firewall connection tracking set enabled=yes
(2) Missing dns-server for IOT vlan ???
/ip dhcp-server network
add address=10.10.1.0/24 comment=VPN gateway=192.168.73.1 netmask=24
add address=10.10.50.0/24 comment="VLAN500 IoT Network" gateway=10.10.50.1 \ Dns?????
netmask=24
add address=192.168.73.0/24 comment=defconf dns-server=192.168.73.226 \
gateway=192.168.73.1 netmask=24
(3) Purpose of all these being allowed to router?? Why are they all admin IT folks??
/ip firewall address-list
add address=192.168.73.2-192.168.73.254 list=allowed_to_router
add address=10.10.50.2-10.10.50.254 list=allowed_to_router
add address=10.10.1.1-10.10.1.10 list=allowed_to_router
(4) Input chain rules can be simplified, so many block rules, JUST use as last rule a drop all else rule!
As to the above (3), the allowed list SHOULD ONLY BE FOR ADMIN ACCESS.
you will still need the LAN users to access DNS services of the router.
Adjusted the order.........
ip firewall filter
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment="defconf: accept ICMP" protocol=icmp
add action=accept chain=input comment=\
"address-list for IP addresses, that are allowed to access router;" \
src-address-list=allowed_to_router
add action=accept chain=input comment=VPN dst-port=1194 protocol=tcp ??????????******
add action=accept chain=input comment="Allow LAN DNS queries - TCP" \
connection-state=new dst-port=53 in-interface-list=LAN protocol=tcp
add action=accept chain=input comment="Allow LAN DNS queries-UDP" \
connection-state=new dst-port=53 in-interface-list=LAN protocol=udp
add action=drop chain=input comment="drop all else"
What is the purpose of the VPN rule, just asking as its a non-standard ipsec port........
(5) Forward chain rules......... Moved Forward chain vlan rule mixed in with input chain rules further down, The Vlan500 rule is not required as you have it covered with the drop all rule at the end of the forward chain. Destination NAT rule is also not required in a drop format as you have the drop rule at the end covering that. So I modified it to allow DST NAT in the accept format.
add action=accept chain=forward comment="defconf: accept in ipsec policy" \
ipsec-policy=in,ipsec
add action=accept chain=forward comment="defconf: accept out ipsec policy" \
ipsec-policy=out,ipsec
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related
add action=accept chain=forward comment=\
"defconf: accept established,related, untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=accept chain=forward comment="Forward VPN to LAN" dst-address=\
192.168.73.0/24 src-address=10.10.1.0/24
add action=accept chain=forward comment="allow port forwarding"\
connection-nat-state=dstnat connection-state=new in-interface-list=WAN
add action=drop chain=input comment=\
"Drop any input packets that get this far"
(1) This is new in that have not seen this set before......???
/ip firewall connection tracking set enabled=yes
(2) Missing dns-server for IOT vlan ???
/ip dhcp-server network
add address=10.10.1.0/24 comment=VPN gateway=192.168.73.1 netmask=24
add address=10.10.50.0/24 comment="VLAN500 IoT Network" gateway=10.10.50.1 \ Dns?????
netmask=24
add address=192.168.73.0/24 comment=defconf dns-server=192.168.73.226 \
gateway=192.168.73.1 netmask=24
(3) Purpose of all these being allowed to router?? Why are they all admin IT folks??
/ip firewall address-list
add address=192.168.73.2-192.168.73.254 list=allowed_to_router
add address=10.10.50.2-10.10.50.254 list=allowed_to_router
add address=10.10.1.1-10.10.1.10 list=allowed_to_router
(4) Input chain rules can be simplified, so many block rules, JUST use as last rule a drop all else rule!
As to the above (3), the allowed list SHOULD ONLY BE FOR ADMIN ACCESS.
you will still need the LAN users to access DNS services of the router.
Adjusted the order.........
ip firewall filter
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment="defconf: accept ICMP" protocol=icmp
add action=accept chain=input comment=\
"address-list for IP addresses, that are allowed to access router;" \
src-address-list=allowed_to_router
add action=accept chain=input comment=VPN dst-port=1194 protocol=tcp ??????????******
add action=accept chain=input comment="Allow LAN DNS queries - TCP" \
connection-state=new dst-port=53 in-interface-list=LAN protocol=tcp
add action=accept chain=input comment="Allow LAN DNS queries-UDP" \
connection-state=new dst-port=53 in-interface-list=LAN protocol=udp
add action=drop chain=input comment="drop all else"
What is the purpose of the VPN rule, just asking as its a non-standard ipsec port........
(5) Forward chain rules......... Moved Forward chain vlan rule mixed in with input chain rules further down, The Vlan500 rule is not required as you have it covered with the drop all rule at the end of the forward chain. Destination NAT rule is also not required in a drop format as you have the drop rule at the end covering that. So I modified it to allow DST NAT in the accept format.
add action=accept chain=forward comment="defconf: accept in ipsec policy" \
ipsec-policy=in,ipsec
add action=accept chain=forward comment="defconf: accept out ipsec policy" \
ipsec-policy=out,ipsec
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related
add action=accept chain=forward comment=\
"defconf: accept established,related, untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=accept chain=forward comment="Forward VPN to LAN" dst-address=\
192.168.73.0/24 src-address=10.10.1.0/24
add action=accept chain=forward comment="allow port forwarding"\
connection-nat-state=dstnat connection-state=new in-interface-list=WAN
add action=drop chain=input comment=\
"Drop any input packets that get this far"
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
As for the config.
(1) This is new in that have not seen this set before......???
/ip firewall connection tracking set enabled=yes
Not sure what that is. I assume that is a default setting as I don't recall enabling this.
(2) Missing dns-server for IOT vlan ???
/ip dhcp-server network
add address=10.10.1.0/24 comment=VPN gateway=192.168.73.1 netmask=24
add address=10.10.50.0/24 comment="VLAN500 IoT Network" gateway=10.10.50.1 \ Dns?????
netmask=24
add address=192.168.73.0/24 comment=defconf dns-server=192.168.73.226 \
gateway=192.168.73.1 netmask=24
For the networks without DNS explicitly set, it appears they get the DNS as the gatewayIP and the .226 server which i have set as my DNS server (PiHole). Sincethe time i posted this, i explicitly set a DNS address(.226) for the VPN Network.
(3) Purpose of all these being allowed to router?? Why are they all admin IT folks??
/ip firewall address-list
add address=192.168.73.2-192.168.73.254 list=allowed_to_router
add address=10.10.50.2-10.10.50.254 list=allowed_to_router
add address=10.10.1.1-10.10.1.10 list=allowed_to_router
I thought this was to allow traffic through the router...this is new to me. Should i remove this address list and firewall rule all together? I assume i will still be able to manage the router from the webfig correct?
(4) Input chain rules can be simplified, so many block rules, JUST use as last rule a drop all else rule!
As to the above (3), the allowed list SHOULD ONLY BE FOR ADMIN ACCESS.
you will still need the LAN users to access DNS services of the router.
Adjusted the order.........
I will work on adjusting the order of the rules. Most of those are default rules that were set up with the router.
ip firewall filter
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment="defconf: accept ICMP" protocol=icmp
add action=accept chain=input comment=\
"address-list for IP addresses, that are allowed to access router;" \
src-address-list=allowed_to_router
add action=accept chain=input comment=VPN dst-port=1194 protocol=tcp ??????????******
add action=accept chain=input comment="Allow LAN DNS queries - TCP" \
connection-state=new dst-port=53 in-interface-list=LAN protocol=tcp
add action=accept chain=input comment="Allow LAN DNS queries-UDP" \
connection-state=new dst-port=53 in-interface-list=LAN protocol=udp
add action=drop chain=input comment="drop all else"
I will add the Allow LAN DNS rules you put in BOLD. This might be why something i was playing with (Static DNS) wasnt working. :-D
What is the purpose of the VPN rule, just asking as its a non-standard ipsec port........
The VPN rule was just what the OpenVPN instructions i found had in the instructions. (https://www.micu.eu/ovpn-server/)
(5) Forward chain rules......... Moved Forward chain vlan rule mixed in with input chain rules further down, The Vlan500 rule is not required as you have it covered with the drop all rule at the end of the forward chain. Destination NAT rule is also not required in a drop format as you have the drop rule at the end covering that. So I modified it to allow DST NAT in the accept format.
I will have to read through this a bit to make sure i cover all the rules. Thank you for the review.
add action=accept chain=forward comment="defconf: accept in ipsec policy" \
ipsec-policy=in,ipsec
add action=accept chain=forward comment="defconf: accept out ipsec policy" \
ipsec-policy=out,ipsec
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related
add action=accept chain=forward comment=\
"defconf: accept established,related, untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=accept chain=forward comment="Forward VPN to LAN" dst-address=\
192.168.73.0/24 src-address=10.10.1.0/24
add action=accept chain=forward comment="allow port forwarding"\
connection-nat-state=dstnat connection-state=new in-interface-list=WAN
add action=drop chain=input comment=\
"Drop any input packets that get this far"
Thank you for reviewing this. I really appreciate it. Coming from Ubiquiti i never saw all the rules written out. This is quite a learning experience.
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
it is the switch i had so i used it. I was thinking of getting a different one. Somehow though i got it to work. I created a VLAN (50) for ports 5-8 untagged, tagged port1 if i revcall and then PVID 50 on port 5-8. i just tried to get to the management webpage though and cant now....so...on to figure that out.Yup I did find some threads about the SG108 series.I've told TP-Link that I'll bitch about this issue and warn users with any chance I get but this is ridiculous, two in two days!
@CyBuzz see what I wrote here about TL-SG108E: viewtopic.php?f=2&t=175848#p863639
And below.. since @anav was talking about a totally different switch series.
I believe their may be a work around and that is ensure the PVID of 1 is replaced by any other pvid if possible (at least for trunk or hybrid ports).
or flash netgear firmware on it......... (or get a switch that works somewhat to standard)
Do you recommend a switch to put in the TL place? I was just going to order an RB260GS however i will use up all the ports on it. Maybe the CSS610 but dont know much about the cloud switches
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
When you add the drop all rule at the end of the INPUT CHAIN as recommended,
AND you dont have allow rules for the admin to access the router, prior to that last rule you will be locked out of the router
I just didnt understand the purpose of the allow list you had as it didnt seem to be related to Admin access for example.
The only thing users typicallky need access to on the router is DNS services.
AND you dont have allow rules for the admin to access the router, prior to that last rule you will be locked out of the router
I just didnt understand the purpose of the allow list you had as it didnt seem to be related to Admin access for example.
The only thing users typicallky need access to on the router is DNS services.
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
:-) I did just that...locked out of router but luckily had a terminal session open to the router and could re-enable the rule.When you add the drop all rule at the end of the INPUT CHAIN as recommended,
AND you dont have allow rules for the admin to access the router, prior to that last rule you will be locked out of the router
I just didnt understand the purpose of the allow list you had as it didnt seem to be related to Admin access for example.
The only thing users typicallky need access to on the router is DNS services.
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
I dont know what i did but now my IoT network cant get anywhere. I can connect to it and it gets the right IP address and DNS but no internet. some really weird stuff going on now too. i put everything back to what it was and no luck.
dang...i should have stopped while ahead
got it going again...now back to the suggestions :-)
dang...i should have stopped while ahead
got it going again...now back to the suggestions :-)
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
I probably should have stated this up front...some of the firewall rules i added were suggested by the internet...like the block dns from WAN and again...i have never written firewall rules before...or dug this deep into it.
if i understand the input chain...anything coming into the router that isnt explicitly allowed will be dropped when it hits my 'drop all else' rule so in regards to someone on the internet doing a DNS query on my public IP...it would drop because there was no accept rule for it in the input chain.
I also understand the forward chain is kind of the same way though it applies to traffic/packet for another NIC on the local network. For packets routed through the local server.
what it looks like what i dont understand is that i have a rule that is forward VPN to LAN, which i thought i needed however i dont. i turned that rule off and can still get to my LAN from VPN. This leads me to test the 'drop VLAN50' and find that unless that is turned ON that i can get to my LAN from VLAN. this leads me to think that traffic is allowed unless explicitly dropped (like i was doing with DNS from WAN).
is input drop unless explicitly allowed and forward allow unless explicitly dropped?
anav, you indicated that the drop at the end of the list would take care of the VLAN50 rule. it was set on the input chain (duplicate of one above) so i switched it to the forward chain but that didnt allow me to access the internet but could get to the local LAN (from LAN) do i disabled it.
This is where i am getting confused. Please take a look at my FW rules and see if you can see what i am missing. it works the way it is set up right now but i want to make sure i am not doing something that will get me in trouble later.
if i understand the input chain...anything coming into the router that isnt explicitly allowed will be dropped when it hits my 'drop all else' rule so in regards to someone on the internet doing a DNS query on my public IP...it would drop because there was no accept rule for it in the input chain.
I also understand the forward chain is kind of the same way though it applies to traffic/packet for another NIC on the local network. For packets routed through the local server.
what it looks like what i dont understand is that i have a rule that is forward VPN to LAN, which i thought i needed however i dont. i turned that rule off and can still get to my LAN from VPN. This leads me to test the 'drop VLAN50' and find that unless that is turned ON that i can get to my LAN from VLAN. this leads me to think that traffic is allowed unless explicitly dropped (like i was doing with DNS from WAN).
is input drop unless explicitly allowed and forward allow unless explicitly dropped?
anav, you indicated that the drop at the end of the list would take care of the VLAN50 rule. it was set on the input chain (duplicate of one above) so i switched it to the forward chain but that didnt allow me to access the internet but could get to the local LAN (from LAN) do i disabled it.
This is where i am getting confused. Please take a look at my FW rules and see if you can see what i am missing. it works the way it is set up right now but i want to make sure i am not doing something that will get me in trouble later.
You do not have the required permissions to view the files attached to this post.
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
I dont like looking at parts of a config only as they are all related.......... and its not in winbox export format either??
You have added some of the new rule but kept the old ones which in the end does not do the job.
You have added some of the new rule but kept the old ones which in the end does not do the job.
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
Thanks anav. I thought it would be easier to review just doing a /ip firewall filter print to a file than the whole thing. I have attached my current export.I dont like looking at parts of a config only as they are all related.......... and its not in winbox export format either??
You have added some of the new rule but kept the old ones which in the end does not do the job.
I added all the new rules and thought I removed/disabled the ones you recommended. Which ones do you see that are causing an issue.
These are the differences in the input chain from what you recommended.
Rule 0 (Fasttrack)...should this be removed?
Disabled(not removed) 6 and 7 (drop external DNS queries)
Rule 10, accept to local loopback (for CAPsMAN) i kept since it was a default rule. i don't know if i need it or not since i don't use CAPsMAN
Rule 11, drop all not coming from LAN, default rule so i kept this
These are the differences in the forward chain from your recommendation...
Rule 18, I disabled(though you kept) the Forward VPN to LAN because it seems like i didn't need it. I could VPN in from my phone and get to stuff on my 192.168.72.0 network.
Rule 19, i disabled the default rule drop all from WAN not DSTNATed at your suggestion 'do not use the drop format and use the accept format', your allow port forwarding rule which is Rule 21 is enabled.
Rule 20 i kept enabled as it didn't seem rule 23 was dropping VLAN50->LAN traffic. If i understood your recommendation, rule 20 wasn't needed because of rule 23 however in testing, if 23 is enabled and 20 disabled, i am able to get to the LAN from VLAN50 however as soon as i re-enable 20 it is blocked.
Rule 22 is disabled, i was just messing around with drop rules that didn't work
Rule 23 is the last rule you recommended (added this AM) that drops any input at that point.
So, in the end, i think i implemented all of your recommendations and explained why i implemented the differences. From what i have tested it seems to 'work' meaning i can get to what I want and cant get to what i don't want. However I just don't want people that shouldn't get to stuff to have access to stuff :-). In the quoted post you end with "does not do the job" and that is what i want to understand...what am i missing...what part of the job am i failing at. I am very thankful that you are taking your time to help me. Thank you Thank you Thank you!
CyBuzz
You do not have the required permissions to view the files attached to this post.
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
(1) /ip dhcp-server network
add address=10.10.1.0/24 comment=VPN dns-server=192.168.73.226 gateway=\
192.168.73.1 netmask=24
add address=10.10.50.0/24 comment="VLAN500 IoT Network" gateway=10.10.50.1 \
netmask=24
dns server for vlan500, ?????????????
(2) Get rid of these...... not required
add action=drop chain=input comment="Drop external DNS requests" disabled=yes \
dst-port=53 in-interface=ether1 protocol=tcp
add action=drop chain=input comment="Drop external DNS requests" disabled=yes \
dst-port=53 in-interface=ether1 protocol=udp
(3) Yes you can delete this if you dont use capsman
add action=accept chain=input comment=\
"defconf: accept to local loopback (for CAPsMAN)" dst-address=127.0.0.1
(4) Delete this rule.....it serves no purpose
add action=drop chain=input comment="defconf: drop all not coming from LAN" \
in-interface-list=!LAN
WHY BECAUSE THE DROP ALL RULE follows it!!!
add action=drop chain=input comment="defconf: drop all not coming from LAN" \
in-interface-list=!LAN
add action=drop chain=input comment="drop all else"
(5) Duplicate input chain rule at the very bottom of the forward chain can be removed.....
add action=drop chain=input comment=\
"Drop any input packets that get this far"
(6) These two rules can be removed... as you already have port forwarding handled and with the drop all rule vlan to subnet traffic is automatically blocked at L3.
add action=drop chain=forward comment=\
"defconf: drop all from WAN not DSTNATed" connection-nat-state=!dstnat \
connection-state=new disabled=yes in-interface-list=WAN
add action=drop chain=forward comment=\
"Drop any traffic from VLAN50 not going to the internet" in-interface=\
vlan50 out-interface=!ether1
(7) What is missing is a forward chain rule to allow LAN to WAN traffic.
add address=10.10.1.0/24 comment=VPN dns-server=192.168.73.226 gateway=\
192.168.73.1 netmask=24
add address=10.10.50.0/24 comment="VLAN500 IoT Network" gateway=10.10.50.1 \
netmask=24
dns server for vlan500, ?????????????
(2) Get rid of these...... not required
add action=drop chain=input comment="Drop external DNS requests" disabled=yes \
dst-port=53 in-interface=ether1 protocol=tcp
add action=drop chain=input comment="Drop external DNS requests" disabled=yes \
dst-port=53 in-interface=ether1 protocol=udp
(3) Yes you can delete this if you dont use capsman
add action=accept chain=input comment=\
"defconf: accept to local loopback (for CAPsMAN)" dst-address=127.0.0.1
(4) Delete this rule.....it serves no purpose
add action=drop chain=input comment="defconf: drop all not coming from LAN" \
in-interface-list=!LAN
WHY BECAUSE THE DROP ALL RULE follows it!!!
add action=drop chain=input comment="defconf: drop all not coming from LAN" \
in-interface-list=!LAN
add action=drop chain=input comment="drop all else"
(5) Duplicate input chain rule at the very bottom of the forward chain can be removed.....
add action=drop chain=input comment=\
"Drop any input packets that get this far"
(6) These two rules can be removed... as you already have port forwarding handled and with the drop all rule vlan to subnet traffic is automatically blocked at L3.
add action=drop chain=forward comment=\
"defconf: drop all from WAN not DSTNATed" connection-nat-state=!dstnat \
connection-state=new disabled=yes in-interface-list=WAN
add action=drop chain=forward comment=\
"Drop any traffic from VLAN50 not going to the internet" in-interface=\
vlan50 out-interface=!ether1
(7) What is missing is a forward chain rule to allow LAN to WAN traffic.
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
Thanks anav.
Attached is my new export.
Your Recommendations:
1. Added DNS servers
2. Deleted rules "Block external DNS"
3. Deleted rule "loopback for capsman"
4. Deleted rule "default drop if not coming from LAN"
5. Deleted rule "drop all input" duplicate
6. Deleted rules "drop WAN not DSTNATed" and "drop VLAN50 not to internet"
7. Added rule to allow LAN to Internet(ether1)
I also added a drop forward chain rule at the end to drop anything that gets that far. I did this to 'match' the input chain rule. Doing so, blocked my VLAN from getting to the internet so i added a rule to allow that. When I set up the LAN to WAN forward i did it bridge -> ether1 in hopes this covered the VLAN50 (it is listed as an interface under bridge) but it didnt work, probably my lack of VLAN/router/bridge knowledge. I also had to set up an all ppp (VPN) to internet(ether1) so i could get out to the internet.
Again, thank you for the time you are spending working through this with me.
Attached is my new export.
Your Recommendations:
1. Added DNS servers
2. Deleted rules "Block external DNS"
3. Deleted rule "loopback for capsman"
4. Deleted rule "default drop if not coming from LAN"
5. Deleted rule "drop all input" duplicate
6. Deleted rules "drop WAN not DSTNATed" and "drop VLAN50 not to internet"
7. Added rule to allow LAN to Internet(ether1)
I also added a drop forward chain rule at the end to drop anything that gets that far. I did this to 'match' the input chain rule. Doing so, blocked my VLAN from getting to the internet so i added a rule to allow that. When I set up the LAN to WAN forward i did it bridge -> ether1 in hopes this covered the VLAN50 (it is listed as an interface under bridge) but it didnt work, probably my lack of VLAN/router/bridge knowledge. I also had to set up an all ppp (VPN) to internet(ether1) so i could get out to the internet.
Again, thank you for the time you are spending working through this with me.
You do not have the required permissions to view the files attached to this post.
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
This is too funny but my spidey sense just tingled!!!
I was looking at why you still had this rule..........
add action=accept chain=forward comment=\
"Allow VLAN50 traffic to the internet(ether1)" in-interface=vlan50 \
out-interface=ether1
You have defined vlan50 as being part of the bridge but HAVE NOT DEFINED WHICH PORTS the vlan will use?
To be honest I get confused by people who
a. use the bridge do dhcp
b. then use separate vlan to do dhcp etc.
I prefer to use vlans for all traffic except maybe keeping one port for emergency access off the bridge.
Oh and yes a VLAN is NOT a bridge port and thus this line must be removed......
/interface bridge port
add bridge=bridge comment=defconf interface=ether2
add bridge=bridge comment=defconf interface=ether3
add bridge=bridge comment=defconf interface=ether4
add bridge=bridge comment=defconf interface=ether5
add bridge=bridge comment=defconf interface=ether6
add bridge=bridge comment=defconf interface=ether7
add bridge=bridge comment=defconf interface=ether8
add bridge=bridge comment=defconf interface=ether9
add bridge=bridge comment=defconf interface=ether10
add bridge=bridge comment=defconf interface=sfp-sfpplus1
add bridge=bridge comment=VLAN50 interface=vlan50
Be that as it may it should be doable as basically you have the bridge giving out DHCP on all the etherports which is fine.
We just need to define which ports you want your vlan to run on and
a. if the port is going to a dumb device OR
b. if the port is going to smart device.
So please let me know where v50 is going and to what devics??
I was looking at why you still had this rule..........
add action=accept chain=forward comment=\
"Allow VLAN50 traffic to the internet(ether1)" in-interface=vlan50 \
out-interface=ether1
You have defined vlan50 as being part of the bridge but HAVE NOT DEFINED WHICH PORTS the vlan will use?
To be honest I get confused by people who
a. use the bridge do dhcp
b. then use separate vlan to do dhcp etc.
I prefer to use vlans for all traffic except maybe keeping one port for emergency access off the bridge.
Oh and yes a VLAN is NOT a bridge port and thus this line must be removed......
/interface bridge port
add bridge=bridge comment=defconf interface=ether2
add bridge=bridge comment=defconf interface=ether3
add bridge=bridge comment=defconf interface=ether4
add bridge=bridge comment=defconf interface=ether5
add bridge=bridge comment=defconf interface=ether6
add bridge=bridge comment=defconf interface=ether7
add bridge=bridge comment=defconf interface=ether8
add bridge=bridge comment=defconf interface=ether9
add bridge=bridge comment=defconf interface=ether10
add bridge=bridge comment=defconf interface=sfp-sfpplus1
add bridge=bridge comment=VLAN50 interface=vlan50
Be that as it may it should be doable as basically you have the bridge giving out DHCP on all the etherports which is fine.
We just need to define which ports you want your vlan to run on and
a. if the port is going to a dumb device OR
b. if the port is going to smart device.
So please let me know where v50 is going and to what devics??
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
Additional points..
(1) I don't have this rule on my config set on my router, nor have seen it on other config, so just stating not sure what that does??
/ip firewall connection tracking
set enabled=yes
I checked on winbox, and the closest thing I could find was
IP Firewall CONNECTIONS TAB, there is a box selection for tracking when I click on that the entries are AUTO and loose TCP tracking is checked.
The loose tcp tracking maybe related to the fact that under services I have RP Filter: "Loose" as the selection.
Funny nothing shows on the config line so maybe tis so minor as not required to mention??
In any case probably fine leaving as it is.
The second one can be set to LAN no harm.
/ip neighbor discovery-settings
set discover-interface-list=none
(2) For security purposes recommended to DISABLE , there is no reason I am aware of to make such services available.
ip service
set telnet address=192.168.73.0/24 disabled=yes
set ftp disabled=yes
set www address=192.168.73.0/24,10.10.1.0/24 port=8080
set ssh address=192.168.73.0/24 port=2200
set www-ssl address=192.168.73.0/24
set api address=192.168.73.0/24 disabled=yes
set winbox address=192.168.73.0/24
set api-ssl address=192.168.73.0/24 disabled=yes
(3) for Winbox access this should be set to LAN or MANAGEMENT and since VLAN50 is part of LAN recommend creating a Management interface listing.
/tool mac-server mac-winbox
set allowed-interface-list=Management
/interface list
add comment=defconf name=WAN
add comment=defconf name=LAN
add name=Management
/interface list member
add comment="defconf - WAN" interface=ether1 list=WAN
add comment="VLAN50 for IoT Network" interface=vlan50 list=LAN
add comment="defconf - LAN" interface=bridge list=LAN
add interface=bridge list=Management
(1) I don't have this rule on my config set on my router, nor have seen it on other config, so just stating not sure what that does??
/ip firewall connection tracking
set enabled=yes
I checked on winbox, and the closest thing I could find was
IP Firewall CONNECTIONS TAB, there is a box selection for tracking when I click on that the entries are AUTO and loose TCP tracking is checked.
The loose tcp tracking maybe related to the fact that under services I have RP Filter: "Loose" as the selection.
Funny nothing shows on the config line so maybe tis so minor as not required to mention??
In any case probably fine leaving as it is.
The second one can be set to LAN no harm.
/ip neighbor discovery-settings
set discover-interface-list=none
(2) For security purposes recommended to DISABLE , there is no reason I am aware of to make such services available.
ip service
set telnet address=192.168.73.0/24 disabled=yes
set ftp disabled=yes
set www address=192.168.73.0/24,10.10.1.0/24 port=8080
set ssh address=192.168.73.0/24 port=2200
set www-ssl address=192.168.73.0/24
set api address=192.168.73.0/24 disabled=yes
set winbox address=192.168.73.0/24
set api-ssl address=192.168.73.0/24 disabled=yes
(3) for Winbox access this should be set to LAN or MANAGEMENT and since VLAN50 is part of LAN recommend creating a Management interface listing.
/tool mac-server mac-winbox
set allowed-interface-list=Management
/interface list
add comment=defconf name=WAN
add comment=defconf name=LAN
add name=Management
/interface list member
add comment="defconf - WAN" interface=ether1 list=WAN
add comment="VLAN50 for IoT Network" interface=vlan50 list=LAN
add comment="defconf - LAN" interface=bridge list=LAN
add interface=bridge list=Management
-

-
toxicfusion
Member

- Posts: 326
- Joined:
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
What was last MikroTik AP you deployed and tested against Unifi lineup? MT getting better and making a "SLOW" comeback...I do not run WISP, but I do lots of wireless installations …’lots’. ….. UBNT wireless is excellent in FACT outstanding …. Tik Wireless is very POOR … VERY POOR. UBNT Has AI that works really well in mesh environments … how long before MikroTik will have AI … 10 yrs ???Ubt products are consumer toys with shiny interface. Easy to turn the knobs.
Yes - Folks running a WISP will argue otherwise. That is different story with the Ubt airfiber products. Or Move to Cambium [wisp].
I no longer trust UBT.
Back to OP Topic -
Great success on your transition over to the RB4011.
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
anav, thank you for that reply. It is a lot to consume. I will take a look and see what i can comprehend tonight. it sounds like i have set up my router and bridge incorrectly and i have many questions about that...remember...i am very new to this and it doesnt surprise me that i may have done something wrong :-). I think i read in another post that you have a similar set up (UBNT APs, Switch and 4011). can you share your config with me so i can take a look?
I will try and get a diagram put together if that will help.
CyBuzz
I will try and get a diagram put together if that will help.
CyBuzz
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
yes the diagram will be very helpful.
No your config is not that far off the mark and its a matter, as usual, of understanding the requirements correctly which then a design can be prescribed.
No your config is not that far off the mark and its a matter, as usual, of understanding the requirements correctly which then a design can be prescribed.
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
This is too funny but my spidey sense just tingled!!!
I was looking at why you still had this rule..........
add action=accept chain=forward comment=\
"Allow VLAN50 traffic to the internet(ether1)" in-interface=vlan50 \
out-interface=ether1
You have defined vlan50 as being part of the bridge but HAVE NOT DEFINED WHICH PORTS the vlan will use?
To be honest I get confused by people who
a. use the bridge do dhcp
b. then use separate vlan to do dhcp etc.
I prefer to use vlans for all traffic except maybe keeping one port for emergency access off the bridge.
This is my inexperience with setting this up. If i need to set up a vlan for all traffic then i will have to figure out how that will work. I also am not quite sure i understand the bridge or its purpose. I thought it was just a grouping for whatever interfaces you put in it so i could create Bridge1 to house ports 2-5 and Bridge 2 to house ports 6-10...not sure if that is right thought.
Oh and yes a VLAN is NOT a bridge port and thus this line must be removed......
/interface bridge port
add bridge=bridge comment=defconf interface=ether2
add bridge=bridge comment=defconf interface=ether3
add bridge=bridge comment=defconf interface=ether4
add bridge=bridge comment=defconf interface=ether5
add bridge=bridge comment=defconf interface=ether6
add bridge=bridge comment=defconf interface=ether7
add bridge=bridge comment=defconf interface=ether8
add bridge=bridge comment=defconf interface=ether9
add bridge=bridge comment=defconf interface=ether10
add bridge=bridge comment=defconf interface=sfp-sfpplus1
add bridge=bridge comment=VLAN50 interface=vlan50
I removed this VLAN from the bridge
Be that as it may it should be doable as basically you have the bridge giving out DHCP on all the etherports which is fine.
We just need to define which ports you want your vlan to run on and
a. if the port is going to a dumb device OR
b. if the port is going to smart device.
So please let me know where v50 is going and to what devics??
Again, my lack of knowledge shows through here. my VLAN50 is 'defined' in my access points on particular SSIDs. For the UAP-nanoHDs i created a network in the controller software called IOT and made it a VLAN 50 and then the SSIDs are on that network. In my TPLink EAP225 i enabled VLAN on the SSIDs and gave them a VLANID of 50. I then set up the VLAN in the router with an interface, address, DHCP, etc. I am not sure what you mean by what port. the port that the EAP-225 comes in on is port 10 on the router and the UAP-nanoHDs are on ports on the US-16-150W. There are also SSIDs that arent on a VLAN on each of the access points. I am not sure what you mean by a smart/dumb device. When i get my RB260GSP i am going to make 3 of those ports VLAN50 and the others not on a vlan(normal network). would the APs and RB260 be 'smart' devices? Does the router need to know what port that device is on even through there are VLANed and non VLANed interfaces on it?
Attached is a rough network diagram. I have never done one of these before so be kind :-)
Additional points..
(1) I don't have this rule on my config set on my router, nor have seen it on other config, so just stating not sure what that does??
/ip firewall connection tracking
set enabled=yes
I checked on winbox, and the closest thing I could find was
IP Firewall CONNECTIONS TAB, there is a box selection for tracking when I click on that the entries are AUTO and loose TCP tracking is checked.
The loose tcp tracking maybe related to the fact that under services I have RP Filter: "Loose" as the selection.
Funny nothing shows on the config line so maybe tis so minor as not required to mention??
In any case probably fine leaving as it is.
I dont use WinBox as I am on a linux machine. I use webfig and it is also under firewall/connections/tracking. Loose TCP tracking is checked on the tracking screen.
The second one can be set to LAN no harm.
/ip neighbor discovery-settings
set discover-interface-list=none
I will make that change
(2) For security purposes recommended to DISABLE , there is no reason I am aware of to make such services available.
ip service
set telnet address=192.168.73.0/24 disabled=yes
set ftp disabled=yes
set www address=192.168.73.0/24,10.10.1.0/24 port=8080
set ssh address=192.168.73.0/24 port=2200
set www-ssl address=192.168.73.0/24
set api address=192.168.73.0/24 disabled=yes
set winbox address=192.168.73.0/24
set api-ssl address=192.168.73.0/24 disabled=yes
i need the www ones there because i use the webfig not winbox
(3) for Winbox access this should be set to LAN or MANAGEMENT and since VLAN50 is part of LAN recommend creating a Management interface listing.
/tool mac-server mac-winbox
set allowed-interface-list=Management
/interface list
add comment=defconf name=WAN
add comment=defconf name=LAN
add name=Management
/interface list member
add comment="defconf - WAN" interface=ether1 list=WAN
add comment="VLAN50 for IoT Network" interface=vlan50 list=LAN
add comment="defconf - LAN" interface=bridge list=LAN
add interface=bridge list=Management
I am not quite sure i follow this Management interface. On that note, should i have made a VLAN50 interface list for my IoT VLAN?
Anyway, thanks for your help...yet again.
You do not have the required permissions to view the files attached to this post.
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
Very nice diagram!
Questions.
1. Do you have a guest wifi for visitors?
2. Why do you have some devices on your home lan, like direcTV, ip camera, roku etc. Put them on a media VLAN for example.
In general you should shave off any devices that you do not control that has internal software from the home network (non-trusted) devices but not necessarily evil though.
3. Why do you not have a separate work network, if one or the other is infected one should ensure appropriate barriers are in place to prevent contamination in either direction but mostly home to work for example.
So looking at your layout I would have one more wlan for guests, maybe one for media, and an appropriate number of vlans added.
The only thing I cannot comment on is the unifi controller but hoping its a smart device so that you send it vlans.
(vlans for wifi and vlan which it gets its IP from for management purposes aka like home vlan if thats the managment vlan).
Questions.
1. Do you have a guest wifi for visitors?
2. Why do you have some devices on your home lan, like direcTV, ip camera, roku etc. Put them on a media VLAN for example.
In general you should shave off any devices that you do not control that has internal software from the home network (non-trusted) devices but not necessarily evil though.
3. Why do you not have a separate work network, if one or the other is infected one should ensure appropriate barriers are in place to prevent contamination in either direction but mostly home to work for example.
So looking at your layout I would have one more wlan for guests, maybe one for media, and an appropriate number of vlans added.
The only thing I cannot comment on is the unifi controller but hoping its a smart device so that you send it vlans.
(vlans for wifi and vlan which it gets its IP from for management purposes aka like home vlan if thats the managment vlan).
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
Very nice diagram!
Questions.
1. Do you have a guest wifi for visitors?
Not yet. I need to do that. I also need to have a 'Kids' network. Both of those are 'I really need to do this' items.
2. Why do you have some devices on your home lan, like direcTV, ip camera, roku etc. Put them on a media VLAN for example.
In general you should shave off any devices that you do not control that has internal software from the home network (non-trusted) devices but not necessarily evil though.
Those are wired and i didnt know how or wasnt able to vlan them. I think i may(if i can figure it out) be able to VLAN the ports that the DirecTv and IP Camera are on. They are on my US-16-150W so i should be able to VLAN the port through the controller software. The others, on the wired network connecting to the TPLink will get VLANed this weekend when my RB260 arrives.
3. Why do you not have a separate work network, if one or the other is infected one should ensure appropriate barriers are in place to prevent contamination in either direction but mostly home to work for example.
Another thing i should do. Same reasoning i should get the kids on their own network.
So looking at your layout I would have one more wlan for guests, maybe one for media, and an appropriate number of vlans added.
The only thing I cannot comment on is the unifi controller but hoping its a smart device so that you send it vlans.
(vlans for wifi and vlan which it gets its IP from for management purposes aka like home vlan if thats the managment vlan).
i still need to understand the Bridge and what you mean by telling the VLANs what ports to run on...i still dont get those concepts. Additionally i need to figure out the "Native VLAN" concept.
As for wlans/ssids, it appears i can not have more than 4 SSIDs on my UAP-nanoHDs...so i need to figure that out now. I was thinking i needed more than that to separate out stuff and have them all on their own VLAN.
SSID1 - Main Network
SSID2 - Work Network
SSID3 - Kid1
SSID4 - Kid 2
SSID5 - IoT/Media
SSID6 - Guest
SSID7 - Management
Edited to attach new diagram with Future state
You do not have the required permissions to view the files attached to this post.
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
If you got Mikrotik APs, you might be able to have all those SSIDs by creating "virtual interfaces" which you then link the VLANs to.
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
Well, i think i have this working for now. I am sure there is more to do but this seems to work at the moment. I still need to understand the bridge concept and LAN list concept but for now I think i have a rudimentary understanding. I also want to put my regular network on a VLAN as i think that is recommended. I was able to get WINE working on my laptop so i can run winbox under linux now. Thank you all for your help and guidance.
Here is my latest export:
Here is my latest export:
You do not have the required permissions to view the files attached to this post.
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
(1) what is the relationship between the interface ovpn-cybuzz and VLAN10?
(2) Still waiting for network diagram ;-) otherwise your bridge port settings or lack of any detail on them is confusing.
(3) Interface list members seems incomplete and why are some disabled?
For example, all your VLANs should be entered as LAN entities
If you need to identify a sub group of vlans for example create a new interface list item and use that where required in firewall rules.
(3) Your forward chain firewall rules are a mess due to (2), no diagram and no detail in bridge port settings.
(4) What devices/users use bridge Subnet ???
Glad to help on config once we have a clearer picture.
(2) Still waiting for network diagram ;-) otherwise your bridge port settings or lack of any detail on them is confusing.
(3) Interface list members seems incomplete and why are some disabled?
For example, all your VLANs should be entered as LAN entities
If you need to identify a sub group of vlans for example create a new interface list item and use that where required in firewall rules.
(3) Your forward chain firewall rules are a mess due to (2), no diagram and no detail in bridge port settings.
(4) What devices/users use bridge Subnet ???
Glad to help on config once we have a clearer picture.
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
(1) what is the relationship between the interface ovpn-cybuzz and VLAN10?
ovpn-cybuzz is the dynamic interface that gets created when i VPN into the network and VLAN10 is the VLAN for the VPN
(2) Still waiting for network diagram ;-) otherwise your bridge port settings or lack of any detail on them is confusing.
send me an example of what would be helpful. i could work forever on a diagram. What detail is needed? in post #39 there is something i put together. what else needs to be added? i guess it has changed a little. i will update it.
(3) Interface list members seems incomplete and why are some disabled?
For example, all your VLANs should be entered as LAN entities
If you need to identify a sub group of vlans for example create a new interface list item and use that where required in firewall rules.
I dont know. I dont quite get what the relationship between all that is and just got what i needed to work. in trying things i made changes and then disabled the changes i didnt need or that didnt seem to be needed at the time
(3) Your forward chain firewall rules are a mess due to (2), no diagram and no detail in bridge port settings.
I dont quite know how the chain rules are a mess because i dont have a diagram. They seem to work but maybe they would be easier to understand with a diagram? I also dont get the bridge concept(mentioned above) other than all my ports on the router are a listed as 'in' or part of bridge.
(4) What devices/users use bridge Subnet ???
i am not sure i understand this question.
Glad to help on config once we have a clearer picture.
i am going to read up on the bridge, the interface lists and see what i can do for a diagram and get back with everyone. Thanks for taking a look.
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
Okay a diagram to detail what is connected to each port on the RB4011 and
a. what vlans are running through the ports.
b. where do you expect bridge traffic that has its own dhcp and pool etc to go and why? who and what is the bridge serving........??
a. what vlans are running through the ports.
b. where do you expect bridge traffic that has its own dhcp and pool etc to go and why? who and what is the bridge serving........??
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
it is not shown on this diagram...all the patch panel connections patch back to the US16-150W switch on various ports.Okay a diagram to detail what is connected to each port on the RB4011 and
The only VLANs that are running through ports are the ones on my RB260GSP so the devices connected are VLAN50 and separate from my other networks. I left on port open (not vlan50) so i could connect hardwired to it with my laptop and not be forced into VLAN50a. what vlans are running through the ports.
If i understand the bridge, it is just being used to allow all the ports on the router to talk to each other. Also if i understand it correctly, i should be creating a VLAN for my "All other devices" that arent on a VLAN now and apply the DHCP that is on my bridge now to that and not have DHCP on the bridge. I think that would cover DHCP for everything that connects since everything that connects would be on a VLAN. I think i would also need to figure out the VLAN through ports thing too so i would ensure that things hardwired were on the right VLAN.b. where do you expect bridge traffic that has its own dhcp and pool etc to go and why? who and what is the bridge serving........??
Any suggested configuration changes would be greatly appreciated since as i have said before....still trying to figure this out.
You do not have the required permissions to view the files attached to this post.
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
Diagram observations.
The RB4011 has not connection back to the same 24 port switch??
I would have expected eth2 from the RB4011 to go to one of the ports on the 24 port switch as a trunk port carrying the necessary vlans for
untagged dumb devices and tagged smarrt devices like the TPLINK eap 245 and RB260GS etc....
I would annotate each device by the vlan it belongs too, not obvious.
which devices does the us16-150W serve (is it a smart switch?) which vlans?
What vlan is dell T30 on,
YOu have SSIDs noted but really care about vlans devices are supposed to use (not necessary) but to identify wlans yes.
Probably tried to do too much with one diagram and best to break it out.
if you have a clear idea of what you want to do then start a configuration and then check it against your diagrams to make sure its what you want.
When you have a coherent config export it here.
All smart devices should get an IP from the management LAN and thus every smart device will have the managment vlan running to it on a trunk port and doesnt necessarily need to go to any device.
The RB4011 has not connection back to the same 24 port switch??
I would have expected eth2 from the RB4011 to go to one of the ports on the 24 port switch as a trunk port carrying the necessary vlans for
untagged dumb devices and tagged smarrt devices like the TPLINK eap 245 and RB260GS etc....
I would annotate each device by the vlan it belongs too, not obvious.
which devices does the us16-150W serve (is it a smart switch?) which vlans?
What vlan is dell T30 on,
YOu have SSIDs noted but really care about vlans devices are supposed to use (not necessary) but to identify wlans yes.
Probably tried to do too much with one diagram and best to break it out.
if you have a clear idea of what you want to do then start a configuration and then check it against your diagrams to make sure its what you want.
When you have a coherent config export it here.
All smart devices should get an IP from the management LAN and thus every smart device will have the managment vlan running to it on a trunk port and doesnt necessarily need to go to any device.
Re: From Mikrotik to Ubiquiti UniFi and back to Mikrotik
*** I apologize now for dumping all this information. Sorry, it is a long read with no TL/DR. ***
I am not sure i am communicating well here. I will try and do a little better. Also note, when i say 'arbitrarily'...it is arbitrary because i dont know any better :-)
Hardware:
RB4011:
Cable modem is connected to RB4011 eth1
16 port switch (US-16-150W) Port 1 is connected to RB4011 eth2 <- not sure if this is considered a trunk...dont quite know anything about trunk yet
UnRaid Server is connected to RB4011 eth5. There is no VLAN for that port and it was arbitrarily attached to eth5 on the RB4011
None of the ports on the Unifi Switch are VLAN tagged.
Devices are arbitrarily plugged into the ports on the Unifi Switch.
Everything on the network other than the server go through the switch (hard wired or via WAP, mostly wireless)
RB260GSP ports 3-5 are configured VLAN 50 because untrusted devices are on those ports.
VLAN Information:
I think i caused a bit of confusion here. I have a 24 port patch panel and 16 port Unifi Switch. The RB4011 does connect to the 16 port switch. It is done through the patch panel on port 24.
I am not sure what a trunk port is yet. need to read up on that.
Which devices should be annotated? Network Devices or end user devices (phones, laptops, tvs)? As i see it, the network devices dont belong to a VLAN, a VLAN is configured on a device. Am i missing this? Should all my network devices (RB4011, RB260GSP, etc) be on VLAN70 (as you indicated below)?
the switch is a smart switch. i manage it through Unifi Controller hosted on the UnRaid server. No VLANS have been configured on it. As noted above, all devices other than the server go through the switch.
the server is not on a VLAN
Do you have an example of a configuration i should be looking to strive for? If i could see a sample configuration that i could model mine after that may help me.
so each of my smart devices should have a 10.10.70.x IP address versus the 192.168.73.x addresses they have now? If this is the case, would i set the port they(APs) are plugged into on the Unifi Switch to VLAN70 or will that cause problems because of VLANs (for each SSID) are on each AP?
I am not sure i am communicating well here. I will try and do a little better. Also note, when i say 'arbitrarily'...it is arbitrary because i dont know any better :-)
Hardware:
- Cable Modem
- RB4011
- 16 Port Unifi Switch (US-16-150W)
- 24 Port Patch Panel
- RB260GSP (VLAN50 on ports 3-5)
- 2x - US-nanoHD (Upstairs and Main) VLANs 20, 30, 40, 50
- TPLink-EAP245 in the basement VLAN 20, 30, 40, 50, 60, 70
RB4011:
- eth1 -> Cable Modem
- eth2 -> Unifi Switch
- eth5 -> UnRaid Server
- Other eth ports unused
Cable modem is connected to RB4011 eth1
16 port switch (US-16-150W) Port 1 is connected to RB4011 eth2 <- not sure if this is considered a trunk...dont quite know anything about trunk yet
UnRaid Server is connected to RB4011 eth5. There is no VLAN for that port and it was arbitrarily attached to eth5 on the RB4011
None of the ports on the Unifi Switch are VLAN tagged.
Devices are arbitrarily plugged into the ports on the Unifi Switch.
Everything on the network other than the server go through the switch (hard wired or via WAP, mostly wireless)
RB260GSP ports 3-5 are configured VLAN 50 because untrusted devices are on those ports.
VLAN Information:
- VLAN10 - VPN inbound
- VLAN20 - Work devices
- VLAN30 - Kid 1 devices
- VLAN40 - Kid 2 devices
- VLAN50 - IoT/Untrusted Devices
- VLAN60 - Guests (not used yet)
- VLAN70 - Management, only connect via SSID that is configured for VLAN70 and only i have the password for that VLAN. Not sure if this is the same management VLAN you are referring to. My diagram was incorrect (copy/paste error) saying phones and tablets. My phone and my laptop are the only devices used to manage the hardware devices.
- Separate networks for Kids, Work, IoT/Untrusted, Guest, Management(per your recommendation) and 'All Other' which i will just call trusted devices for now. I think i have done that with the VLAN configuration that is set up.
- Learn to write firewall rules to manage traffic between the networks (VLANS) and between the networks and the internet. I think i have done this to the best of my abilites so far.
- Print to printer on VLAN50 from all networks except WAN. <- In Progress
- Figure out Bonjour to allow iDevices to print to printer on VLAN50 <- Not Started
- Set up a 'Trusted Devices' VLAN where my devices that connect through Serenity SSID and hard wired (like my server) reside. <- Not Started
Diagram observations.
The RB4011 has not connection back to the same 24 port switch??
I would have expected eth2 from the RB4011 to go to one of the ports on the 24 port switch as a trunk port carrying the necessary vlans for
untagged dumb devices and tagged smarrt devices like the TPLINK eap 245 and RB260GS etc....
I think i caused a bit of confusion here. I have a 24 port patch panel and 16 port Unifi Switch. The RB4011 does connect to the 16 port switch. It is done through the patch panel on port 24.
I am not sure what a trunk port is yet. need to read up on that.
I would annotate each device by the vlan it belongs too, not obvious.
Which devices should be annotated? Network Devices or end user devices (phones, laptops, tvs)? As i see it, the network devices dont belong to a VLAN, a VLAN is configured on a device. Am i missing this? Should all my network devices (RB4011, RB260GSP, etc) be on VLAN70 (as you indicated below)?
which devices does the us16-150W serve (is it a smart switch?) which vlans?
the switch is a smart switch. i manage it through Unifi Controller hosted on the UnRaid server. No VLANS have been configured on it. As noted above, all devices other than the server go through the switch.
What vlan is dell T30 on,
the server is not on a VLAN
YOu have SSIDs noted but really care about vlans devices are supposed to use (not necessary) but to identify wlans yes.
Probably tried to do too much with one diagram and best to break it out.
if you have a clear idea of what you want to do then start a configuration and then check it against your diagrams to make sure its what you want.
When you have a coherent config export it here.
Do you have an example of a configuration i should be looking to strive for? If i could see a sample configuration that i could model mine after that may help me.
All smart devices should get an IP from the management LAN and thus every smart device will have the managment vlan running to it on a trunk port and doesnt necessarily need to go to any device.
so each of my smart devices should have a 10.10.70.x IP address versus the 192.168.73.x addresses they have now? If this is the case, would i set the port they(APs) are plugged into on the Unifi Switch to VLAN70 or will that cause problems because of VLANs (for each SSID) are on each AP?



