I am trying to configure VLANs on a network. Currently the network diagram looks as follows:
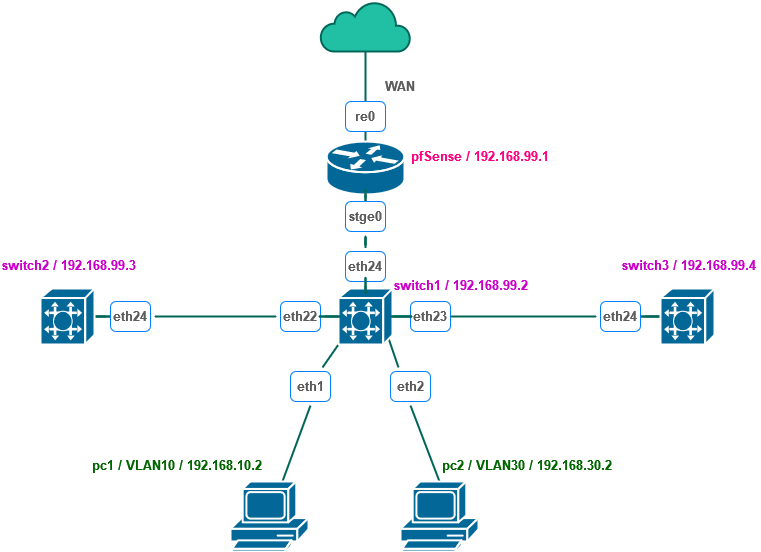
On the CRS326 switches, I have this configuration for VLANs:
switch1:
Code: Select all
/system identity
set name=switch1
/interface bridge
add name=BR1 protocol-mode=none
/interface ethernet
set [ find default-name=ether4 ] disabled=yes
set [ find default-name=ether5 ] disabled=yes
set [ find default-name=ether6 ] disabled=yes
set [ find default-name=ether7 ] disabled=yes
set [ find default-name=ether8 ] disabled=yes
set [ find default-name=ether9 ] disabled=yes
set [ find default-name=ether10 ] disabled=yes
set [ find default-name=ether11 ] disabled=yes
set [ find default-name=ether12 ] disabled=yes
set [ find default-name=ether13 ] disabled=yes
set [ find default-name=ether14 ] disabled=yes
set [ find default-name=ether15 ] disabled=yes
set [ find default-name=ether16 ] disabled=yes
set [ find default-name=ether17 ] disabled=yes
set [ find default-name=ether18 ] disabled=yes
set [ find default-name=ether19 ] disabled=yes
set [ find default-name=ether20 ] disabled=yes
set [ find default-name=ether21 ] disabled=yes
set [ find default-name=sfp-sfpplus1 ] disabled=yes
set [ find default-name=sfp-sfpplus2 ] disabled=yes
/interface bridge port
add bridge=BR1 interface=ether1 pvid=10
add bridge=BR1 interface=ether2 pvid=30
add bridge=BR1 interface=ether3 pvid=50
add bridge=BR1 interface=ether22
add bridge=BR1 interface=ether23
add bridge=BR1 interface=ether24
/interface bridge vlan
add bridge=BR1 tagged=ether24,ether22,ether23 untagged=ether1 vlan-ids=10
add bridge=BR1 tagged=ether24,ether22,ether23 untagged=ether2 vlan-ids=30
add bridge=BR1 tagged=ether24,ether22,ether23 untagged=ether3 vlan-ids=50
add bridge=BR1 tagged=BR1,ether24,ether22,ether23 vlan-ids=99
/ip address
add address=192.168.99.2/24 interface=VLAN_99_MANAGEMENT network=192.168.99.0
/tool romon
set enabled=yes
/interface bridge set BR1 vlan-filtering=yesCode: Select all
/system identity
set name=switch2
/interface bridge
add name=BR1 protocol-mode=none
/interface ethernet
set [ find default-name=ether2 ] disabled=yes
set [ find default-name=ether3 ] disabled=yes
set [ find default-name=ether4 ] disabled=yes
set [ find default-name=ether5 ] disabled=yes
set [ find default-name=ether6 ] disabled=yes
set [ find default-name=ether7 ] disabled=yes
set [ find default-name=ether8 ] disabled=yes
set [ find default-name=ether9 ] disabled=yes
set [ find default-name=ether10 ] disabled=yes
set [ find default-name=ether11 ] disabled=yes
set [ find default-name=ether12 ] disabled=yes
set [ find default-name=ether13 ] disabled=yes
set [ find default-name=ether14 ] disabled=yes
set [ find default-name=ether15 ] disabled=yes
set [ find default-name=ether16 ] disabled=yes
set [ find default-name=ether17 ] disabled=yes
set [ find default-name=ether18 ] disabled=yes
set [ find default-name=ether19 ] disabled=yes
set [ find default-name=ether20 ] disabled=yes
set [ find default-name=ether21 ] disabled=yes
set [ find default-name=ether22 ] disabled=yes
set [ find default-name=ether23 ] disabled=yes
set [ find default-name=sfp-sfpplus1 ] disabled=yes
set [ find default-name=sfp-sfpplus2 ] disabled=yes
/interface vlan
add interface=BR1 name=VLAN_99_MANAGEMENT vlan-id=99
/interface bridge port
add bridge=BR1 interface=ether1 pvid=10
add bridge=BR1 interface=ether24
/interface bridge vlan
add bridge=BR1 tagged=ether24 untagged=ether1 vlan-ids=10
add bridge=BR1 tagged=BR1,ether24 vlan-ids=99
/ip address
add address=192.168.99.3/24 interface=VLAN_99_MANAGEMENT network=192.168.99.0
/tool romon
set enabled=yes
/interface bridge set BR1 vlan-filtering=yesswitch3:
Code: Select all
/system identity
set name=switch3
/interface bridge
add name=BR1 protocol-mode=none
/interface ethernet
set [ find default-name=ether2 ] disabled=yes
set [ find default-name=ether3 ] disabled=yes
set [ find default-name=ether4 ] disabled=yes
set [ find default-name=ether5 ] disabled=yes
set [ find default-name=ether6 ] disabled=yes
set [ find default-name=ether7 ] disabled=yes
set [ find default-name=ether8 ] disabled=yes
set [ find default-name=ether9 ] disabled=yes
set [ find default-name=ether10 ] disabled=yes
set [ find default-name=ether11 ] disabled=yes
set [ find default-name=ether12 ] disabled=yes
set [ find default-name=ether13 ] disabled=yes
set [ find default-name=ether14 ] disabled=yes
set [ find default-name=ether15 ] disabled=yes
set [ find default-name=ether16 ] disabled=yes
set [ find default-name=ether17 ] disabled=yes
set [ find default-name=ether18 ] disabled=yes
set [ find default-name=ether19 ] disabled=yes
set [ find default-name=ether20 ] disabled=yes
set [ find default-name=ether21 ] disabled=yes
set [ find default-name=ether22 ] disabled=yes
set [ find default-name=ether23 ] disabled=yes
set [ find default-name=sfp-sfpplus1 ] disabled=yes
set [ find default-name=sfp-sfpplus2 ] disabled=yes
/interface vlan
add interface=BR1 name=VLAN_99_MANAGEMENT vlan-id=99
/interface bridge port
add bridge=BR1 interface=ether1 pvid=10
add bridge=BR1 interface=ether24
/interface bridge vlan
add bridge=BR1 tagged=ether24 untagged=ether1 vlan-ids=10
add bridge=BR1 tagged=BR1,ether24 vlan-ids=99
/ip address
add address=192.168.99.4/24 interface=VLAN_99_MANAGEMENT network=192.168.99.0
/tool romon
set enabled=yes
/interface bridge set BR1 vlan-filtering=yesMy router is pfSense. There I have set up VLANs on the LAN interface:
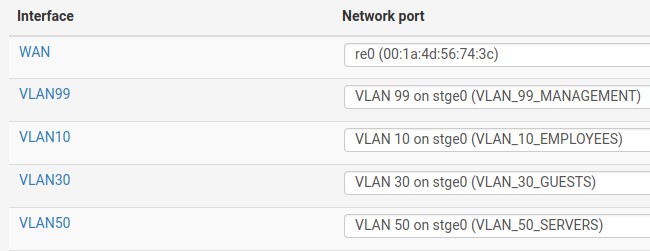
Their addresses are:

The only problem for now is that from PC1 (VLAN10) I cannot access the switches. In fact, on pfSense I don't see the swiches visible in the ARP table at all. Winbox doesn't detect them for me either. It looks like they have no IP addresses set. Can you guys help? Additionally, I have no problem to connect from PC1 (192.168.10.2) to pfSense (192.168.99.1). For all VLANs I temporarily set up a firewall to pass all traffic for each protocol.


