Any idea what command I should actually use not to brick the vm again?
The one given in the docs: “/system/device-mode/update container=yes”.
Home mode is very wrong for this.
Any idea what command I should actually use not to brick the vm again?

# container name comparison string. ".*" to run all containers
:local containerName ".*";
#:local containerName "0110745e-6724-4c41-ab87-e21c054ebf3d|1306f802-a3d8-4436-ae41-4d991709cef0";
# timeout in seconds for up state
:local timeout 60;
# $up return - nonzero when containers can execute
:local up do={ :return [/ip/dhcp-client/print count-only where status=bound]; }
# wait for $up to be nonzero or timeout to expire
:local count 0;
:while (($count < $timeout) and ([$up] = 0)) do={
:delay 1s
:set count ($count+1);
}
if ([$up] = 0) do={
:log warning "container $containerName timeout after $count seconds";
} else={
:local min 0;
:local max ([/container/print count-only]-1);
:log info "container $containerName ready to start after $count seconds";
:local startCount 0;
for i from=$min to=$max do={
if (([/container/print as-value]->$i->"name") ~ $containerName) do={
:local name ([/container/print as-value]->$i->"name");
:local tag ([/container/print as-value]->$i->"tag");
if (([/container/print as-value]->$i->"status") = "stopped") do={
:log info "container [$i] name=$name tag=$tag starting";
/container/start $i;
:set startCount ($startCount+1);
} else={
:log info "container [$i] name=$name tag=$tag not in stopped state";
}
}
}
:log info "container $startCount containers started";
}
+1Hi! Could it be possible to use tun/tap interfaces? it is very necessary for tinc mesh network. Now tun module is loaded after using Zerotier interface, but no rights to create /dev/no/tun device. However, the bridge interface can be created, which is already very pleasing.
I have now created a container for myself with alpine, set up openssh and am very happy with the opportunity to deploy though custom dns and http services. If the possibility of tinc and generally access to tun/tap services appears, then it will be super cool!
This is a scripting thing, "0" only means something only after a print was issued, otherwise it doesn't point to anything, that's why it fails, it's mentioned somewhere in the docs and/or in the forums for sure.If at reboot I start the container directly from the scheduler at Start Time 'startup' with On-Event '/container/start 0' it silently fails.
It is not. Containers (docker/lxc) do usually have its own namespace for PID, network, etc. It does mean that you fully control network interfaces, ip routes, iptables, and this is separate from the host. It means that you can configure VPN that will only be available in a container, and the host (mikrotik) controls how the traffic from veth should be handled.That kind of features would always be difficult. How do you want the traffic to be routed? For the static veth interfaces you define that at the RouterOS side during setup of your container, but when the container would be allowed to setup dynamic interfaces (like tunnels), what would they be connected to?
# RouterOS
/interface veth
add address=172.17.0.3/16 gateway=172.17.0.1 name=ssh-veth
/container config
set registry-url=https://registry-1.docker.io
/container envs
add list=ssh name=SUDO_ACCESS value=true
add list=ssh name=PASSWORD_ACCESS value=true
add list=ssh name=USER_NAME value=user
add list=ssh name=USER_PASSWORD value=password
add list=ssh name=TZ value=Europe/Warsaw
/container
add envlist=ssh interface=ssh-veth logging=yes remote-image=linuxserver/openssh-server:latest
# Terminal
$ ssh -p 2222 user@172.17.0.3
PTY allocation request failed
$ ssh -p 2222 user@172.17.0.3 mount
/dev/sda2 on / type ext3 (rw,nosuid,nodev,noatime)
tmpfs on /dev type tmpfs (rw,nosuid,relatime,size=65536k,mode=755,uid=32768,gid=32768)
proc on /proc type proc (rw,nosuid,nodev,noexec,relatime)
sysfs on /sys type sysfs (rw,nosuid,nodev,noexec,relatime)
devpts on /dev/pts type devpts (rw,nosuid,noexec,relatime,mode=600,ptmxmode=000)
There's a problem with filesystems mounted with `nosuid` preventing usage of `sudo` (and possibly PTY access). This is also present on all mounted disk.
Code: Select all# RouterOS /interface veth add address=172.17.0.3/16 gateway=172.17.0.1 name=ssh-veth /container config set registry-url=https://registry-1.docker.io /container envs add list=ssh name=SUDO_ACCESS value=true add list=ssh name=PASSWORD_ACCESS value=true add list=ssh name=USER_NAME value=user add list=ssh name=USER_PASSWORD value=password add list=ssh name=TZ value=Europe/Warsaw /container add envlist=ssh interface=ssh-veth logging=yes remote-image=linuxserver/openssh-server:latest # Terminal $ ssh -p 2222 user@172.17.0.3 PTY allocation request failed $ ssh -p 2222 user@172.17.0.3 mount /dev/sda2 on / type ext3 (rw,nosuid,nodev,noatime) tmpfs on /dev type tmpfs (rw,nosuid,relatime,size=65536k,mode=755,uid=32768,gid=32768) proc on /proc type proc (rw,nosuid,nodev,noexec,relatime) sysfs on /sys type sysfs (rw,nosuid,nodev,noexec,relatime) devpts on /dev/pts type devpts (rw,nosuid,noexec,relatime,mode=600,ptmxmode=000)
[admin@router01] > /disk print
Flags: M, r - RAID-MEMBER; p - PARTITION
Columns: SLOT, MODEL, SERIAL, INTERFACE, NAME, FS, LABEL, FREE, SIZE
# SLOT MODEL SERIAL INTERFACE NAME FS LABEL FREE SIZE
0 usb1 Samsung Portable SSD T3 0123456789AB USB 2.10 480Mbps 232.9GiB
1 Mp usb1-part1 disk1 ext4 router01-usb 230.7GiB 232.9GiB
[admin@router01] > /container export
# jun/26/2022 14:04:10 by RouterOS 7.4beta4
# software id = SX2N-XPCP
#
# model = RB5009UG+S+
# serial number = 0123456789AB
/container mounts
add dst=/etc/pihole name=etc_pihole src=/disk1/etc
add dst=/etc/dnsmasq.d name=dnsmasq_pihole src=/disk1/etc-dnsmasq.d
/container
add envlist=pihole_envs interface=veth1 mounts=dnsmasq_pihole,etc_pihole root-dir=disk1/pihole
/container config
set registry-url=https://registry-1.docker.io
/container envs
add list=pihole_envs name=TZ value=America/Detroit
add list=pihole_envs name=WEBPASSWORD value=<password>
add list=pihole_envs name=DNSMASQ_USER value=root
Thanks a lot!! I tried with the physical reset button and this time it worked!Just power off/on or use the reset button (ie no soft reboot). Don't forget to install the Container package.
I had the same issue. In my case, I found it was best to do configuration by setting environment variables to change all the settings I wanted as defined in the PiHole Docker documentation.Does anyone have this working with PiHole and with the ability to make changes? The PiHole container will run for me, but any attempt to make changes through the UI and save fails, so I cannot actually configure the thing. System is configured per the docs with an external SSD mounted as `disk1`.
[admin@KDTA-1806Grace] /container/config> /container/envs/print
0 list="pihole" name="TZ" value="UTC"
1 list="pihole" name="WEBPASSWORD" value="transrightsarehumanrights"
2 list="pihole" name="DNSMASQ_USER" value="root"
3 list="pihole" name="FTLCONF_REPLY_ADDR4" value="172.17.0.2"
4 list="pihole" name="ADMIN_EMAIL" value="nope@youwish.example"
5 list="pihole" name="PIHOLE_DOMAIN" value="lan"
6 list="pihole" name="TEMPERATUREUNIT" value="f"
7 list="pihole" name="DNSMASQ_LISTENING" value="all"
8 list="pihole" name="REV_SERVER" value="true"
9 list="pihole" name="REV_SERVER_DOMAIN" value="lan"
10 list="pihole" name="REV_SERVER_TARGET" value="192.168.0.1"
11 list="pihole" name="REV_SERVER_CIDR" value="192.168.0.0/24"
12 list="pihole" name="PIHOLE_DNS_" value="1.1.1.2;1.0.0.2"
This is a bug, waiting for a fix.Does anyone have this working with PiHole and with the ability to make changes? The PiHole container will run for me, but any attempt to make changes through the UI and save fails, so I cannot actually configure the thing. System is configured per the docs with an external SSD mounted as `disk1`.
Yes, "list" was replaced with "key" but it doesn't work.
That I didn't try. And it works?
Would you be so kind as to explain to me how you remove the container, I am an apprentice in the matter?I had to remove the containers and start over. and it worked for me.That I didn't try. And it works?
/container/remove [find];
/container/envs/remove [find];
/container/mounts/remove [find];
Would you be so kind as to explain to me how you remove the container, I am an apprentice in the matter?I had to remove the containers and start over. and it worked for me.
Thanks.
fixed!Nice, is the sudo bug fixed? viewtopic.php?t=178342#p940376
It will remove containers, environments and mount points.Code: Select all/container/remove [find]; /container/envs/remove [find]; /container/mounts/remove [find];
Would you be so kind as to explain to me how you remove the container, I am an apprentice in the matter?
Thanks.
Nice! I've done a quick test with pihole and it doesn't seem to throw that error anymore, indeed.fixed!Nice, is the sudo bug fixed? viewtopic.php?t=178342#p940376
/container/remove [find];
/container/envs/remove [find];
/container/mounts/remove [find];
Hi,
if someone is interested, I built containers for OLSRd V1 and OLSRd V2.
I posted it on the FunkFeuer forum (german).
All containers as also experienced information about it with used commands and scripts to properly start the containers after reboot is also mentioned.
Thanks for this awesome feature in RouterOS!
Yeah, I'm no expert here but it seems the mounts don't get created for some reason and something else restricts mkdir from functioning properly.someone was able to run adguardhome?
share your settings
/container mounts
add dst=/opt/adguardhome/work name=agh_workdir src=/zdisk/containers/adguardhome/tmp
add dst=/opt/adguardhome/conf name=agh_conf src=/zdisk/containers/adguardhome/home/container
add remote-image=adguard/adguardhome:latest interface=veth2 logging=yes mounts=agh_workdir,agh_conf root-dir=zdisk/containers/adguardhomeI am a user of AdGuard Home and PiHole, the former I use in the primary DNS and the latter in the secondary, and I am very interested in putting them to work as a container inside my RB3011, but I have not been successful in configuring AdGuard Home as a container well .someone was able to run adguardhome?
share your settings
Yeah, I'm no expert here but it seems the mounts don't get created for some reason and something else restricts mkdir from functioning properly.someone was able to run adguardhome?
share your settings
I only managed to get it working by using as mounts some directories from inside the container >.> not ideal.
Code: Select all/container mounts add dst=/opt/adguardhome/work name=agh_workdir src=/zdisk/containers/adguardhome/tmp add dst=/opt/adguardhome/conf name=agh_conf src=/zdisk/containers/adguardhome/home
Znevna, you use AdGuard Home image for "arm" if it is correct please where did you get it?
Thanks.
Code: Select all/container add remote-image=adguard/adguardhome:latest interface=veth2 logging=yes mounts=agh_workdir,agh_conf root-dir=zdisk/containers/adguardhome
Yeah, I'm no expert here but it seems the mounts don't get created for some reason and something else restricts mkdir from functioning properly.someone was able to run adguardhome?
share your settings
I only managed to get it working by using as mounts some directories from inside the container >.> not ideal.
Code: Select all/container mounts add dst=/opt/adguardhome/work name=agh_workdir src=/zdisk/containers/adguardhome/tmp add dst=/opt/adguardhome/conf name=agh_conf src=/zdisk/containers/adguardhome/home
Code: Select all/container add remote-image=adguard/adguardhome:latest interface=veth2 logging=yes mounts=agh_workdir,agh_conf root-dir=zdisk/containers/adguardhome
I've tried creating them manually but it can't write in them.
I have two containers currently added, you can see in the first part of the graph AdGuardHome running over night with no clients, just some lists loaded.Anyone else seeing increasing memory usage over time with running containers even when they are idle?
Doesn't look like it's possible to do a "forced restart" (or poweroff) with some popular cloud providers, like amazon AWS... making it tricky to enable container device-mode on CHR/X86 in those cases. What's the recommended approach for such scenarios?
However, after adding a mount point to a container and starting it up, the "src" directory (valid path) was not created automatically. Anyone else had this problem with mounts?src= points to RouterOS location (could also be src=disk1/etc_pihole if, for example, You decide to put configuration files on external USB media), dst= points to defined location (consult containers manual/wiki/github for information on where to point). If src directory does not exist on first time use then it will be populated with whatever container have in dst location.
FROM ghcr.io/tailscale/tailscale:unstable
COPY run.sh /run.sh
CMD "/run.sh"echo "Starting..."
if [[ -e /tmp/tailscaled.sock ]]; then
echo "Deleting previous sock file"
rm -rf /tmp/tailscaled.sock
fi
echo "Starting tailscaled"
tailscaled --tun=userspace-networking --socket=/tmp/tailscaled.sock &> /dev/null &
echo "Done, PID=$!"
PID=$!
echo "Waiting for sock file"
COUNTER=0
while [[ ! -e /tmp/tailscaled.sock ]]; do
echo The counter is $COUNTER
let COUNTER=COUNTER+1
ls -l /tmp/tailscaled.sock
sleep 1
done
echo "Sock file found at:"
ls -l /tmp/tailscaled.sock
echo "Starting tailscale"
tailscale --socket=/tmp/tailscaled.sock up --accept-dns=false --accept-routes=false --advertise-exit-node --advertise-routes="172.17.0.0/16" --authkey=tskey-...
echo "Done, tailscale started"
wait ${PID}
echo "Done"
how is "bridge mode" any different from current implementation?Is it fair to assume that the MT containers do not support the equivalent of Docker bridge mode networking?
And if that is correct, is future support for bridged mode on the roadmap?
disk1
|
+-- docker
|
+-- containers
|
+-- images
|
+-- mount
|
+-- tmp
mount issues are still not fully fixed - but we are working on this issue.
is there any more functionality we should consider adding before container goes to stable release?
Adding a ramdisk to all router models also those that do not have 16MB flash. To preserve backward compatibility, create a /ramdisk directory in the file space for it.is there any more functionality we should consider adding before container goes to stable release?
download directory as .tar.gz and to upload (and unpack) .tar.gz archive.
I'm having the same problem on AWS.Doesn't look like it's possible to do a "forced restart" (or poweroff) with some popular cloud providers, like amazon AWS... making it tricky to enable container device-mode on CHR/X86 in those cases. What's the recommended approach for such scenarios?
The layers being pulled from registry of container images are `.tar.gz` and MikroTik unpacks them.download directory as .tar.gz and to upload (and unpack) .tar.gz archive.
currently this wouldn't be possible.Will it be possible to add capabilities to containers? For instance, cap NET_ADMIN is required to create/use TUN/TAP virtual network devices for various functions. OpenVPN or other VPN solutions, like OpenConnect requires this functionality.
Maybe you can add such network config capability to the RouterOS container config/setup menus? It could mean certain software (after adaptation) could use the network devices previously setup, without the container having permission to do it by itself.currently this wouldn't be possible.Will it be possible to add capabilities to containers? For instance, cap NET_ADMIN is required to create/use TUN/TAP virtual network devices for various functions. OpenVPN or other VPN solutions, like OpenConnect requires this functionality.
For one, OpenVPN requires this cap after startup. So if this is not possible, then the possibilities are limited to other appliances that are not network-related. It would be a disappointment, really. Proxies, DNS and other things using only sockets or listening ports would work, but adding a new VPN solution is a no go as things stand. Too bad, it had my hopes up.Maybe you can add such network config capability to the RouterOS container config/setup menus? It could mean certain software (after adaptation) could use the network devices previously setup, without the container having permission to do it by itself.
OpenVPN is open source so it can be modified to adapt to a different situation.For one, OpenVPN requires this cap after startup.Maybe you can add such network config capability to the RouterOS container config/setup menus? It could mean certain software (after adaptation) could use the network devices previously setup, without the container having permission to do it by itself.
Are you being sarcastic? But anyway, no, it can't. Using the tuntap kernel module, tun/tap devices, network admin functions, etc. is in its very foundation. And anyway, who would have the capability to make such changes? Even Mikrotik seem to have failed at it.OpenVPN is open source so it can be modified to adapt to a different situation.
Sure it can! I have written software that uses TUN/TAP myself. It requires privileges to create a TUN or TAP interface but once you have done that and opened it you can pass it along as an fd that can be used by less-privileged code.Are you being sarcastic? But anyway, no, it can't.OpenVPN is open source so it can be modified to adapt to a different situation.
If it's indeed the case, then there's some faint hope. But it requires changes in ROS and also requires changes in OVPN. And OVPN is just one application that uses TUN/TAP and/or capabilities. All the rest would need a similar change in upstream specifically for supporting containers in ROS, which, let's be honest, is a niche user base. And that in itself is pretty discouraging WRT container support in ROS. It would be much more efficient and simple if some specific caps would be allowed to be changed in ROS. No other changes would be needed. Naturally, allowing caps in a router for random apps in CTs poses a security risk (containers in themselves do as well), but I think it should be left to the users to deal with it by using or not using the feature.Sure it can! I have written software that uses TUN/TAP myself. It requires privileges to create a TUN or TAP interface but once you have done that and opened it you can pass it along as an fd that can be used by less-privileged code.
So it would be possible to arrange that a container config can create a tun/tap interface and pass it to the container e.g. as fd 3, and the OpenVPN server can be modified to not create the interface itself but assume it is already open on fd 3 (via some parameter).
That would be a simple modification and when you can get it accepted by the upstream it would be a one-time effort (vs a patch you need to apply whenever you get a new version and compile it).
We're not talking about the other configuration requirements. If it's not possible to start a CT requiring tun/tap, there's nothing to talk about. The rest comes after. I'm not worried about that. So it is indeed special if we need quirks and workarounds. But let's wait and see what the final versions bring.There will always be some changes or requirement for configuration. Creating a TUN or TAP is not enough, you also need to configure how it is to be connected to the remainder of the network.
Even when you run OpenVPN natively on a Linux box you will need to do that. So it is nothing special.
Yes a working guide for an MDNS repeater containertun/tap support will be added in next release. Anything else to consider adding before stable release?
Yes a working guide for an MDNS repeater container
/interface/ethernet/switch/rule
add switch=switch1 mirror=yes ports=ether4,ether5 \
mac-protocol=ip dst-address=224.0.0.251/32 \
protocol=udp dst-port=5353
add switch=switch1 mirror=yes ports=ether4,ether5 \
mac-protocol=ipv6 dst-address6=ff02::fb/128 \
protocol=udp dst-port=5353
That sounds good! How will it be supported? Will we need to create them on the router (host), or will it be possible to apply NET_ADMIN to a specific container so it can add it for itself? I think many software would need to be modified if it can use, but not create the tun/tap device inside the container. That would render the feature unusable as far as I understand.tun/tap support will be added in next release. Anything else to consider adding before stable release?
tun/tap support will be added in next release. Anything else to consider adding before stable release?
Could you allow systemd to work inside container?tun/tap support will be added in next release. Anything else to consider adding before stable release?
Could you allow systemd to work inside container?tun/tap support will be added in next release. Anything else to consider adding before stable release?
NO!Could you allow systemd to work inside container?
/dev/net/tun device now is available for container useThat sounds good! How will it be supported?
NO!Could you allow systemd to work inside container?
/dev/net/tun device now is available for container useThat sounds good! How will it be supported?
Nice!Add your tun/taps as variables for your container. I tested with Zerotier in an Alpine Linux image and it works perfectly:
ZTTUNTAP.png
[cesar@MikroTik] > /interface/veth/export
# jul/27/2022 13:49:44 by RouterOS 7.5beta4
/interface veth
add address=172.31.0.1 gateway=172.31.0.254 name=ripe-atlas
[cesar@MikroTik] > /container/export
# jul/27/2022 13:57:35 by RouterOS 7.5beta4
/container mounts
add dst=/var/atlas-probe/etc name=ripe-atlas-etc src=/disk1/ripe-atlas-etc
add dst=/var/atlas-probe/status name=ripe-atlas-status src=/disk1/ripe-atlas-status
/container
add dns=172.31.0.254 hostname=ripe-atlas interface=ripe-atlas logging=yes mounts=ripe-atlas-etc,ripe-atlas-status root-dir=disk1/ripe-atlas workdir=/var/atlas-probe
/container config
set ram-high=128.0MiB registry-url=https://registry-1.docker.io tmpdir=disk1/container-tmp
[cesar@MikroTik] > /file/print
Columns: NAME, TYPE, SIZE, CREATION-TIME
# NAME TYPE SIZE CREATION-TIME
...
26 disk1 disk jul/27/2022 13:36:31
27 disk1/lost+found directory jul/14/2022 15:18:28
28 disk1/container-tmp directory jul/27/2022 13:36:41
29 disk1/ripe-atlas container store jul/27/2022 13:36:36
[cesar@MikroTik] > /container/shell number=0
/ # route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
/ # ip route show
/ # ifconfig
eth0 Link encap:Ethernet HWaddr 32:14:89:BF:50:B9
inet addr:172.31.0.1 Bcast:0.0.0.0 Mask:0.0.0.0
UP BROADCAST MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:65536 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
/ #
done
[cesar@MikroTik] >
1. mounts needs to be removed and created again if upgraded from version with broken mounts.I'm running RouterOS 7.5beta4 on my hAP ac³ and:
1- mounts still doesn't work for me;
2- I noticed that a default route is not being added to my container, even though gateway is defined in interface/veth.
[admin@MikroTik] > container/shell 2
root@MikroTik:/# ip route show
default via 172.17.0.1 dev eth0
172.17.0.0/24 dev eth0 proto kernel scope link src 172.17.0.4
/interface veth print
i just tried locally - your veth configuration is invalid - you are missing bitmask to address, set address to 172.31.0.1/24
[cesar@MikroTik] > /interface/veth/print
Flags: X - disabled; R - running
0 R name="ripe-atlas" address=172.31.0.1/24 gateway=172.31.0.254
[cesar@MikroTik] > /container/export
# jul/27/2022 15:19:10 by RouterOS 7.5beta4
/container config
set ram-high=128.0MiB registry-url=https://registry-1.docker.io tmpdir=disk1/container-tmp
[cesar@MikroTik] > /file/print
Columns: NAME, TYPE, SIZE, CREATION-TIME
# NAME TYPE SIZE CREATION-TIME
...
26 disk1 disk jul/27/2022 15:18:58
27 disk1/lost+found directory jul/14/2022 15:18:28
[cesar@MikroTik] > /container/mounts/add dst=/var/atlas-probe/etc name=ripe-atlas-etc src=disk1/ripe-atlas-etc
[cesar@MikroTik] > /container/mounts/add dst=/var/atlas-probe/status name=ripe-atlas-status src=disk1/ripe-atlas-status
[cesar@MikroTik] > /container/add dns=172.31.0.254 hostname=ripe-atlas interface=ripe-atlas mounts=ripe-atlas-etc,ripe-atlas-status remote-image=ctassisf/ripe-atlas-alpine:arm32v7 root-dir=disk1/ripe-atlas logging=yes
[cesar@MikroTik] > /log/print
...
15:19:24 container,info,debug importing remote image: ctassisf/ripe-atlas-alpine, tag: arm32v7
15:19:24 system,info item added by cesar
15:19:26 container,info,debug getting layer sha256:6366ba92f08e2418e90171f1e34bd86ecd50fdc95953b3f33b8943c143518eca
15:19:30 container,info,debug layer sha256:6366ba92f08e2418e90171f1e34bd86ecd50fdc95953b3f33b8943c143518eca downloaded
15:19:30 container,info,debug getting layer sha256:7b664ffcb01348f101ae9482b4449efa814ca80e18f5868b5dab7338f5eb4781
15:19:32 container,info,debug layer sha256:7b664ffcb01348f101ae9482b4449efa814ca80e18f5868b5dab7338f5eb4781 downloaded
15:19:32 container,info,debug getting layer sha256:88339ef1f59938ee0a99f3ffc2e42eedb2f7873706e2fc7f8827213dc00ba6fe
15:19:33 container,info,debug layer sha256:88339ef1f59938ee0a99f3ffc2e42eedb2f7873706e2fc7f8827213dc00ba6fe downloaded
15:19:33 container,info,debug getting layer sha256:fc720c19a07d46fe07832f7da19961fb22103a44bf269b14c779cfeb3c98dcc2
15:19:35 container,info,debug layer sha256:fc720c19a07d46fe07832f7da19961fb22103a44bf269b14c779cfeb3c98dcc2 downloaded
15:19:36 container,info,debug getting layer sha256:4f4fb700ef54461cfa02571ae0db9a0dc1e0cdb5577484a6d75e68dc38e8acc1
15:19:37 container,info,debug layer sha256:4f4fb700ef54461cfa02571ae0db9a0dc1e0cdb5577484a6d75e68dc38e8acc1 downloaded
15:19:37 container,info,debug import successful, container 26844012-e16b-4b21-a097-db3f6a22bcb1
[cesar@MikroTik] > /container/print
0 name="26844012-e16b-4b21-a097-db3f6a22bcb1" tag="ctassisf/ripe-atlas-alpine:arm32v7" os="linux" arch="arm" interface=ripe-atlas root-dir=disk1/ripe-atlas mounts=ripe-atlas-etc,ripe-atlas-status dns=172.31.0.254 hostname="ripe-atlas"
workdir="/var/atlas-probe" logging=yes status=stopped
[cesar@MikroTik] > /file/print
Columns: NAME, TYPE, SIZE, CREATION-TIME
# NAME TYPE SIZE CREATION-TIME
...
26 disk1 disk jul/27/2022 15:19:24
27 disk1/lost+found directory jul/14/2022 15:18:28
28 disk1/container-tmp directory jul/27/2022 15:19:37
29 disk1/ripe-atlas container store jul/27/2022 15:19:30
[cesar@MikroTik] > /container/start 0
[cesar@MikroTik] > /container/print
0 name="26844012-e16b-4b21-a097-db3f6a22bcb1" tag="ctassisf/ripe-atlas-alpine:arm32v7" os="linux" arch="arm" interface=ripe-atlas root-dir=disk1/ripe-atlas mounts=ripe-atlas-etc,ripe-atlas-status dns=172.31.0.254 hostname="ripe-atlas"
workdir="/var/atlas-probe" logging=yes status=running
[cesar@MikroTik] > /file/print
Columns: NAME, TYPE, SIZE, CREATION-TIME
# NAME TYPE SIZE CREATION-TIME
...
26 disk1 disk jul/27/2022 15:19:24
27 disk1/lost+found directory jul/14/2022 15:18:28
28 disk1/container-tmp directory jul/27/2022 15:19:37
29 disk1/ripe-atlas container store jul/27/2022 15:19:30
[cesar@MikroTik] > /container/shell number=0
/ # route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 172.31.0.254 0.0.0.0 UG 0 0 0 eth0
172.31.0.0 0.0.0.0 255.255.255.0 U 0 0 0 eth0
/ # ping 8.8.8.8
PING 8.8.8.8 (8.8.8.8): 56 data bytes
64 bytes from 8.8.8.8: seq=0 ttl=117 time=3.544 ms
64 bytes from 8.8.8.8: seq=1 ttl=117 time=3.656 ms
^C
--- 8.8.8.8 ping statistics ---
2 packets transmitted, 2 packets received, 0% packet loss
round-trip min/avg/max = 3.544/3.600/3.656 ms
/ #
done
[cesar@MikroTik] >
i think i got where it goes wrong. As a workaround currently you can after adding container start it, stop it and start again. Mounts should appear. we will try to fix this in next releases
I'd like to see IPv6 support. Or is there a way to get v6 communication with a container? Most of my VPNs are v6-only nowadays, so I can't really use containers as is.tun/tap support will be added in next release. Anything else to consider adding before stable release?
thanks, noted.I'd like to see IPv6 support.
mount folders are not browsable from RouterOS, but you can access file through ftp,sftp, etc.- The CT can't write to the mounted dirs - is that normal? Is there a way to write to them or to any place that's visible on the host? I need the container to write logs and status files.
/dev/net/tun should be available without creating new ENV variables.- I'm not sure that adding caps works as shown in this post - the /dev/net/tun node already exists in the container per config, so there's no need to create it via entrypoint, for instance. OVPN can add an IP, but can't remove the added IP at CT shutdown.
I see the mounts, but I want to write to them, which is not possible (permission error).mount folders are not browsable from RouterOS, but you can access file through ftp,sftp, etc.- The CT can't write to the mounted dirs - is that normal? Is there a way to write to them or to any place that's visible on the host? I need the container to write logs and status files.
I can't reproduce this. Please write to support with exact steps how are you getting this error and reference to this forum thread.I see the mounts, but I want to write to them, which is not possible (permission error).
I used a test x86 KVM VM (fresh install from CD) with a single drive, can this be a problem? Should I attach a secondary disk and retry?I can't reproduce this. Please write to support with exact steps how are you getting this error and reference to this forum thread.I see the mounts, but I want to write to them, which is not possible (permission error).
Alright, it works, but only in a certain way - as your workaround suggests, starting/stopping the CT makes the mount directory appear and I can access its contents via SFTP. It seems to copy the contents of the pre-existing directory from inside the CT with original permissions. Weird, but not a serious problem.I can't reproduce this. Please write to support with exact steps how are you getting this error and reference to this forum thread.I see the mounts, but I want to write to them, which is not possible (permission error).
23:25:41 container,info,debug importing remote image: zabbix-proxy-sqlite3, tag: alpine-6.0-latest
23:25:41 system,info item added by cesar
23:25:43 container,info,debug error response getting manifests: 401
23:25:43 container,info,debug was unable to import, container 83158f44-edaf-45e5-a46f-df86a1039830
I'm seeing an error when trying to add a container using this remote image: zabbix-proxy-sqlite3:alpine-6.0-latest
Logs:Code: Select all23:25:41 container,info,debug importing remote image: zabbix-proxy-sqlite3, tag: alpine-6.0-latest 23:25:41 system,info item added by cesar 23:25:43 container,info,debug error response getting manifests: 401 23:25:43 container,info,debug was unable to import, container 83158f44-edaf-45e5-a46f-df86a1039830
Should I open a support ticket?
Are you sure you provided the URL for the router's architecture?
remote-image=zabbix/zabbix-proxy-sqlite3:alpine-6.0-latest imported on mine 5009 without any problems.
I tried on a RB5009 and this zabbix/zabbix-proxy-sqlite3:alpine-6.0-latest tag has linux/arm64 in it: https://hub.docker.com/layers/zabbix-pr ... xt=explore
remote-image=zabbix/zabbix-proxy-sqlite3:alpine-6.0-latest imported on mine 5009 without any problems.
/container/config/exportIs it possible to have more help on how to use CMD in container
how to interact with other containers?
for example a shell command to interact the docker image after it strarts
Thank you. I didn't notice this trickfor example a shell command to interact the docker image after it strarts
Yes, the subcommands of "/container" are underdocumented on the help site. Until their doc people get around to filling that out, use the CLI to discover the commands by poking around with F1 and TAB keystrokes. From there, the Docker docs will help you piece things together.
In this case, you probably want something like "/container shell 0".



I've removed all mounts / workdir references and cleaned up to the bare essentials. Nothing ;-( (and no logging)I don't know why you wrongly defined the workdir, you don't have to write anything there.
And I think that you have to start it without mounts for now, as there's currently a problem with mounts.
Completely erased the container and re-deployed without mounts etc in the first place. Now the container seems to start!
Anyone able to run any "FROM scratch" images in mikrotik?
This is the package I was trying
$ docker buildx build -t stubby --platform linux/arm/v7 --load .
Does the implementation of mikrotik expects certain standard directory structure / files inside the container?
Thanks. I'll keep it as reference. It looks like its doing a bit more stuff, that RUN [ "/bin/busybox", "--install", "/bin" ], then some dev null etc.. Those may be the difference.Yes. I got this one running a few days ago.
Yes I tried both docker buildx, podman build etc.. The problem isn't in build, as I said if I add a bit of alpine base It works.How did you build it? It should be a command like:
Yes, thats what I knew too. But I guess there is something else at play here, mikrotik is doing something before calling the ENTRYPOINT/CMD.It shouldn't. It runs CMD or ENTRY_POINT, and from then on, the container's internal binaries take over.
Thanks, it runs in x86_64 linux via qemu emulation. Then to be sure I started arm64 alpine. Then installed podman inside that container, then run the stubby container there, it still works there.If you have a full-featured Docker build system (e.g. Docker Desktop) it may have QEMU set up to run ARM containers under emulation. You say the container runs there, but I'm not talking about running it as an x86_64 container, but as armv7, to eliminate unnecessary differences between the test and the deployment platforms.
I made the same mistake as jvanhambelgium above and had simply set ram-high to 2048 bytes. Works perfectly now after changing it to 512M.But both containers have been running incredibly slow. I'm talking 45 minutes for pihole to start up (see the timestamp against the log below). Ubuntu started quicker but I logged in via SSH and every command took 10's of seconds to run, even simple ls, df, top.
CPU usage is constantly 0%, this is an unused CCR2004 with basically zero other config on it.
RUN [ "/bin/busybox", "--install", "/bin" ]
then some dev null
I tried From alpine, then removing every package using apk del musl apk-tools etc.... . If I do that then the container runs successfully. So I'm guessing its due to some directory structure.
Hi, gurus.
Since ROS still does not support tls-auth for OpenVPN (so many years...), I've been trying to find a workaround with OpenVPN client (giggio/openvpn-arm) running within the ROS container. However, no success. The client within container successfully connects to VPN server, I can reach the local tunnel endpoint, but for some reason packets are not being forwarded through the OpenVPN tunnel. Has anyone been successful with it?
Yeah, it turns out that was the answer. Adding busybox solves the issue. It seems like mikrotik needs more than just /bin/sh. I tried providing only /bin/sh, but that doesn't work. Surely shouldn't need all applets of busybox. Next time looking for time to waste I'll turn them off one by one to find out exactly which ones are needed. Then need to compile busybox with those applets disabled.RUN [ "/bin/busybox", "--install", "/bin" ]
That tells BusyBox to install all its sub-command links. (Details) I can only speculate about whether doing this in your container will help. The only solid case I could think of is that it might be calling system(3), thus needing a /bin/sh to exist, but that hypothesis isn't borne out by a quick grep over the source code involved. Still, there may be calls out to other common Unix utilities that Busybox provides.
It seems like mikrotik needs more than just /bin/sh.
Next time looking for time to waste I'll turn them off one by one

I can't make it work creating a "veth2"
Hmm, very interesting, but what if mikrotik needs 10 times, spread across all over a-zWith 305 hard links, you can decide the matter in 9 tries. (log₂(305) = 8.25.)
what if mikrotik needs 10 times, spread across all over a-z
Maybe I'll just write a script to automate itbuild, save, curl upload, ssh container add, start. rinse and repeat in loop

Indeed although I added a /ip/interface "veth2" for some reason it was not hooked on my container bridge!By putting veth2 at 172.17.0.3/16, it's inside the subnet of veth1. That means you need to attach it to the "dockers" bridge so it's visible to all the other 172.17.0.0/16 hosts, it participates in the established NAT rule, etc.I can't make it work creating a "veth2"
Alternately, you can switch to a different subnet like 172.18.0.0/16, then do all of the other network setup steps for that second container subnet. This means you'll end up with a "dockers2" bridge, among other things. This method is far more complex, but it can allow for isolation between containers by imposing a routing layer, where you can jam in some RouterOS magic.

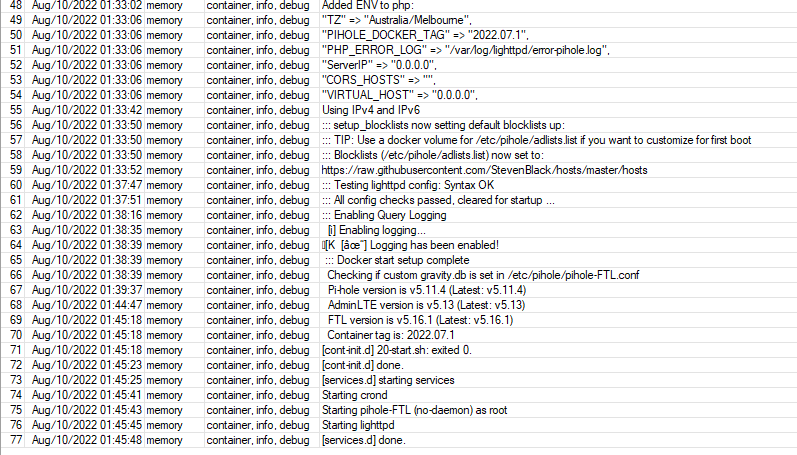
The whole file-structure/permissions/mount-points thing for sure needs some work/fixing in future versions.after upgrade beta5 to beta8 container AdGuard not start
log
15:50:08 container,info,debug 2022/08/15 12:50:08.460390 [info] AdGuard Home, version v0.107.8
15:50:08 container,info,debug 2022/08/15 12:50:08.482883 [info] Initializing auth module: /opt/adguardhome/work/data/sessions.db
15:50:08 container,info,debug 2022/08/15 12:50:08.483123 [error] auth: open DB: /opt/adguardhome/work/data/sessions.db: open /opt/adguardhome/work/data/sessions.db: permission denied
15:50:08 container,info,debug 2022/08/15 12:50:08.483258 [fatal] Couldn't initialize Auth module
please fix it
/container mounts
add dst=/opt/adguardhome/conf name=agh_conf src=/zdisk/container_mounts/agh/conf
add dst=/opt/adguardhome/work name=agh_work src=/zdisk/container_mounts/agh/work 17:39:40 container,info,debug 2022/08/18 14:39:40.171926 [info] AdGuard Home, version v0.107.10
17:39:40 container,info,debug 2022/08/18 14:39:40.172404 [info] This is the first time AdGuard Home is launched
17:39:40 container,info,debug 2022/08/18 14:39:40.172564 [info] Checking if AdGuard Home has necessary permissions
17:39:40 container,info,debug 2022/08/18 14:39:40.173658 [info] AdGuard Home can bind to port 53
17:39:40 container,info,debug 2022/08/18 14:39:40.179003 [fatal] Cannot create DNS data dir at /opt/adguardhome/work/data: mkdir /opt/adguardhome/work/data: permission deniedubuntu@ubuntu:/media/ubuntu/containers/container_mounts/agh$ ls -la
total 16
drwxr-xr-x 4 32768 32768 4096 aug 18 17:39 .
drwxr-xr-x 3 32768 32768 4096 aug 18 17:39 ..
drwxr-xr-x 2 32766 32766 4096 aug 18 17:39 conf
drwxr-xr-x 2 32766 32766 4096 aug 18 17:39 work
ubuntu@ubuntu:/media/ubuntu/containers/container_mounts/agh$ sudo chown 32768:32768 conf
ubuntu@ubuntu:/media/ubuntu/containers/container_mounts/agh$ sudo chown 32768:32768 work
ubuntu@ubuntu:/media/ubuntu/containers/container_mounts/agh$ ls -la
total 16
drwxr-xr-x 4 32768 32768 4096 aug 18 17:39 .
drwxr-xr-x 3 32768 32768 4096 aug 18 17:39 ..
drwxr-xr-x 2 32768 32768 4096 aug 18 17:39 conf
drwxr-xr-x 2 32768 32768 4096 aug 18 17:39 work 23:25:01 container,info,debug 2022/08/18 20:25:01.556901 [info] AdGuard Home, version v0.107.10
23:25:01 container,info,debug 2022/08/18 20:25:01.557206 [info] This is the first time AdGuard Home is launched
23:25:01 container,info,debug 2022/08/18 20:25:01.557325 [info] Checking if AdGuard Home has necessary permissions
23:25:01 container,info,debug 2022/08/18 20:25:01.558153 [info] AdGuard Home can bind to port 53
23:25:01 container,info,debug 2022/08/18 20:25:01.568534 [info] Initializing auth module: /opt/adguardhome/work/data/sessions.db
23:25:01 container,info,debug 2022/08/18 20:25:01.580749 [info] auth: initialized. users:0 sessions:0
23:25:01 container,info,debug 2022/08/18 20:25:01.581431 [info] Initialize web module
23:25:01 container,info,debug 2022/08/18 20:25:01.582222 [info] This is the first launch of AdGuard Home, redirecting everything to /install.html
23:25:01 container,info,debug 2022/08/18 20:25:01.582710 [info] AdGuard Home is available at the following addresses:
23:25:01 container,info,debug 2022/08/18 20:25:01.586599 [info] Go to http://127.0.0.1:3000
23:25:01 container,info,debug 2022/08/18 20:25:01.586796 [info] Go to http://[::1]:3000
23:25:01 container,info,debug 2022/08/18 20:25:01.586976 [info] Go to http://192.168.70.202:3000
23:25:01 container,info,debug 2022/08/18 20:25:01.587243 [info] Go to http://[2a02:edited]:3000@MikroTik can we fix the mounts?
I'm guessing it's not that hard to find out why mounts are created with 32766:32766 instead of 32768:32768
chown nobody /my/mount/pathnobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologincontainers$ ls -lan
total 36
drwxr-xr-x 6 0 0 4096 aug 18 17:39 .
drwxr-x---+ 3 0 0 4096 aug 19 00:01 ..
drwxr-xr-x 3 32768 32768 4096 aug 18 17:39 container_mounts
drwxr-xr-x 3 32768 32768 4096 aug 18 21:34 containers
drwxr-xr-x 3 0 0 4096 aug 18 17:38 docker
drwx------ 2 0 0 16384 iun 24 14:26 lost+found
containers/containers$ ls -lan
total 12
drwxr-xr-x 3 32768 32768 4096 aug 18 21:34 .
drwxr-xr-x 6 0 0 4096 aug 18 17:39 ..
drwxr-xr-x 19 32768 32768 4096 aug 18 17:38 adguardhomecontainers/containers/adguardhome/opt$ ls -lan
total 12
drwxr-xr-x 3 32768 32768 4096 aug 17 18:48 .
drwxr-xr-x 19 32768 32768 4096 aug 18 17:38 ..
drwxr-xr-x 4 32766 32766 4096 aug 17 18:48 adguardhomecontainers/adguardhome/opt/adguardhome$ ls -lan
total 34384
drwxr-xr-x 4 32766 32766 4096 aug 17 18:48 .
drwxr-xr-x 3 32768 32768 4096 aug 17 18:48 ..
-rwxr-xr-x 1 32766 32765 35192832 aug 17 18:48 AdGuardHome
drwxr-xr-x 2 32766 32766 4096 aug 17 18:48 conf
drwxr-xr-x 2 32766 32766 4096 aug 17 18:48 work

alpine:~# mount -t cifs -o rw,username=xx //yy/share /media/share
Password for xx@/yy/share:
mount error(1): Operation not permitted
Refer to the mount.cifs(8) manual page (e.g. man mount.cifs) and kernel log messages (dmesg)
mount: permission denied (are you root?)
alpine:~# dmesg
dmesg: klogctl: Operation not permitted
alpine:~# whoami
root
Would it be possible to add permissions for mounting
Why not NFS instead of SMB? That would be more likely to get accepted and the permissions would work better.The proper feature, then, would be an SMB client for RouterOS, which has been requested many times before.
Why not NFS
That would be more likely to get accepted
the permissions would work better
Is it possible to "mount" usb devices in a container ?
Did you ever TRY to read my message ? I'm searching for HID devices like UPS or even usb/serial devices, not STORAGE devices.Is it possible to "mount" usb devices in a container ?
Did you even try to read the docs? Thin as they currently are, they do cover this.
Routeros is a picky community.When you say USB and mount together, you imply block devices and file systems. HID devices are neither. You can’t “mount” a keyboard in Linux.
As to your actual question, you might be able to do an mknod(8) call and map the dev node in that way. It depends in part on whether the SYS_MKNOD capability is granted at container runtime and whether you can reliably work out what dev node ID the UPS appears under on the host side.
Tricky, but not impossible in principle.
Routeros is a picky community.
i was wrongly remembering docker command uses the the same parameter for mounting folders and "devices".
I'm simply looking for the equivalent of the --device command line parameter of the docker command in linux.
Thanks you very much for your detailed answer,Routeros is a picky community.
Computers are picky things. Those of us who've learned to become facile with them learn not to use the wrong terminology and to jump on instances of it where we see it elsewhere as a sign of either sloppy or outright incorrect thinking. When you're asking for help, you do not want to be giving off the impression of either, else you're likely to get the right answer to the wrong question.
i was wrongly remembering docker command uses the the same parameter for mounting folders and "devices".
There does exist "docker create --mount", but you normally do not use it with /dev, because the container creation process normally does that for you. It's hidden down in the guts of Docker and tricky to get to, but you can see an example of it exposed here, down at the end. Notice the several /dev mounts.
However, although /dev is automatically mounted, you will notice that, if you fire up a random container (e.g. alpine:latest) you won't get things like /dev/sda. This is on purpose, else root inside the container could scribble on your hard disk.
I'm not being pointlessly pedantic here. I'm trying to show why I believe you're off on the wrong track.
I'm simply looking for the equivalent of the --device command line parameter of the docker command in linux.
RouterOS's implementation of containers is closer to the way bare-bones OCI bundle runners like runc and crun work than to full-fat Docker Engine. You'll find yourself missing a lot of what you take to be common affordances.
I doubt the problem is as simple as all this anyway. I did some digging into NUT's USB HID driver, and it looks like it uses libusb to go digging through the device tree. I believe it needs "/sys/bus/usb/devices" to be populated for that to work, which it certainly won't be in a stock container.
If true, even my suggestion to hard-code a /dev node directly into the container won't work.
I also came across this in my investigation, which I found discouraging.
this is in our to do list.The same way tun/tap access was enabled in containers under RouterOS maybe access to usb devices can be enabled too, with a proper feature request.
Hi @rplan,Avahi (mdns Reflector)
Hap AC^2 (256M)
It took a while to get working, but I was able to build an Avahi container. Using the cross build instructions at
https://hub.docker.com/r/taoyou/iperf3-alpine
And the avahi container at
https://github.com/flungo-docker/avahi
It came out a bit over 8M in size, so quite big.
It uses a couple of vlans (Vlan setup currently hard coded in the tar file) on it's veth to connect to the local networks.
It is configured as a mdns reflector.
While working out how to make it work, I used netcat from openwrt to provide a couple of cli sessions. The cli is very basic but works, (You need 2 for when you break one) Probably should learn how to setup a dropbear.
I used 7zip on my desktop to open the tar file, and edit config files, and insert the executables (netcat binary and runcat2.sh script)
It seems to work ok.
Not sure I really want it now though
Yes. Thank you very much!
/container/envs/add key=cap-add name=MYCONTAINER value=NET_ADMIN
/container/envs/add key=device name=MYCONTAINER value=/dev/net/tunIndeed, advanced container network configuration (e.g. with VLAN support) is missing or not described in the documentation.Dear Friends , I have tried many dockers from hub.dockers.com most of them was related to VPN and Proxies and packet ofuscators, and I faced mostly with two problems , first problem , there is no "--cap-add NET_ADMIN" so you can not add dynamic tun interface inside the docker or you can not add special iptable rules inside the docker , and second huge problem when I start second container and set dst nat rules on same range docker bridge and interface or even on second docker bridge and interface , traffic for the first running container becomes lost , i have checked everything and many times , I did all settings with blank config and test environments but the problem exist , please guide me if there are solutions for those two problems. regards
/dev/net/tun access was added in 7.5beta4 and is also included in 7.6. Your provided commands will do nothing.You need to add the variables for your container before you pull it down:
Code: Select all/container/envs/add key=cap-add name=MYCONTAINER value=NET_ADMIN /container/envs/add key=device name=MYCONTAINER value=/dev/net/tun
Where MYCONTAINER is the name of your container.

It would be great to have option to nest docker in a docker, or at least have an option to mount /var/run/docker.sock