Page 1 of 1
IPsec site 2 site VPN. Ping fails in one direction.
Posted: Fri Feb 05, 2016 8:48 am
by PeterLemmen
Hi,
I've configured an IPsec Site 2 site VPN connection between a public Cloud and my on premise environment. Weird thing: PING only works in one direction. I'm able to ping from my on premise environment to virtual machines in the Cloud.
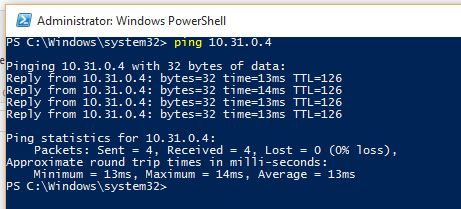
But when I try to ping from the Cloud to my machines on premise it fails.
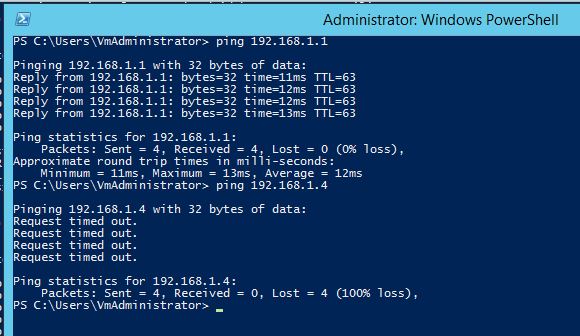
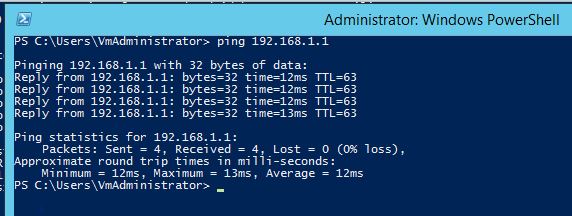
I don't think it is a firewall problem because a ping from the Cloud side to the Mikrotik router on premise is succesfull:
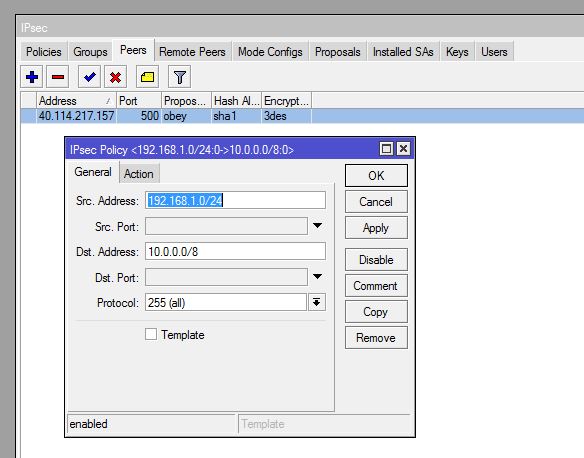
Maybe the reply of the device behind the Mikrotik router somehow gets lost and is not delivered at the device that initiated the ping on the public cloud side. A routing problem? Shouldn't this be covered by the config of the VPN at the Mikrotik side (IPsec policy)?
Probably something tiny I missed somehow. But what did I miss or do wrong? Hope someone is able to help.
Thanks in advance.
Peter
Re: IPsec site 2 site VPN. Ping fails in one direction.
Posted: Fri Feb 05, 2016 2:58 pm
by Revelation
Without seeing more details, it looks like you need to ensure that you have a route back across the tunnel for the return traffic.
Re: IPsec site 2 site VPN. Ping fails in one direction.
Posted: Fri Feb 05, 2016 4:19 pm
by BartoszP
Check this @ 3/4 of text or search "Site to Site IpSec Tunnel":
http://wiki.mikrotik.com/wiki/Manual:IP/IPsec
Re: IPsec site 2 site VPN. Ping fails in one direction.
Posted: Fri Feb 05, 2016 6:25 pm
by PeterLemmen
Without seeing more details, it looks like you need to ensure that you have a route back across the tunnel for the return traffic.
Hi,
What kind of route should that be? I could not find a requirement for adding a specific route for return traffic in the guidelines. I've used this part of the Mikrotik manual as reference:
http://wiki.mikrotik.com/wiki/Manual:IP ... Sec_Tunnel
Re: IPsec site 2 site VPN. Ping fails in one direction.
Posted: Sun Feb 07, 2016 8:41 am
by jaytcsd
I had the same problem, switched to EOIP tunnels and made both sites the same IP range, working fine now.
Re: IPsec site 2 site VPN. Ping fails in one direction.
Posted: Tue Feb 09, 2016 10:43 pm
by PeterLemmen
I had the same problem, switched to EOIP tunnels and made both sites the same IP range, working fine now.
Hi,
Thanks for your help! The other side of my Site 2 site connection is Microsoft Public Cloud Azure. I don't think they are supporting EOIP tunnels. Is there an alternative to solving this issue, I can do on the MikroTik side without the need to change technologies or protocols at the Microsoft side?
Peter
Re: IPsec site 2 site VPN. Ping fails in one direction.
Posted: Tue Feb 09, 2016 10:44 pm
by PeterLemmen
Да, это неплохой вариант.
Bedankt!
Re: IPsec site 2 site VPN. Ping fails in one direction.
Posted: Fri Feb 12, 2016 9:47 am
by jaytcsd
I have never tried a tunnel from a Mikrotik to any other router.
Greg Sowell has examples of IPsec and IPIP tunnels from Mikrotik to Cisco on his site.
http://gregsowell.com/?p=1290
Re: IPsec site 2 site VPN. Ping fails in one direction.
Posted: Mon Feb 15, 2016 11:07 pm
by PeterLemmen
I have never tried a tunnel from a Mikrotik to any other router.
Greg Sowell has examples of IPsec and IPIP tunnels from Mikrotik to Cisco on his site.
http://gregsowell.com/?p=1290
Hi,
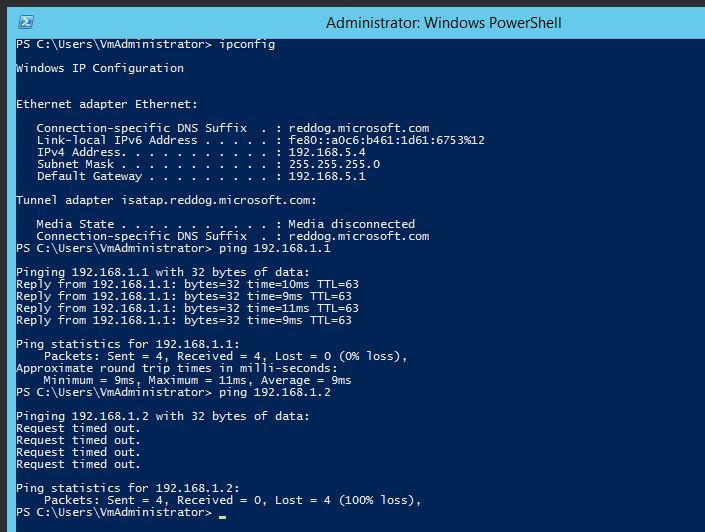
Yes I know the site of Greg. Followed some of his video's. The weird thing is it's almost working perfect. I can even ping my router from the public cloud (azure) side. I recently changed all IP spaces on public cloud side so they are now more similar to the on premise side. But all though everything was changed and re-configured with the new IP space the result is still exactly the same:
1) Ping from Azure VM to Mikrotik router is succesfull
2) Ping from device behind Mikrotik router to Azure VM is succesfull
3) RDP session from device behind Mikrotik router to Azure VM is succesfull
4) Ping to on premise device (behind the Mikrotik router) from Azure VM fails
Re: IPsec site 2 site VPN. Ping fails in one direction.
Posted: Tue Feb 16, 2016 2:35 pm
by ekobravo
Hi,
Did you find the solution?
I have the same problem. I've configured an IPsec Site 2 site VPN connection between HQ and remote office. I’m using RB2011iL-IN in both offices. PING only works in one direction. I'm able to ping from my on HQ to remote office. Not just that I'm able to connect to any pc from the HQ to remote office. From remote office I can not ping or connect to for example MainServer.
Thanks in advance.
Re: IPsec site 2 site VPN. Ping fails in one direction.
Posted: Tue Feb 16, 2016 2:42 pm
by PeterLemmen
Hi,
Did you find the solution?
I have the same problem. I've configured an IPsec Site 2 site VPN connection between HQ and remote office. I’m using RB2011iL-IN in both offices. PING only works in one direction. I'm able to ping from my on HQ to remote office. Not just that I'm able to connect to any pc from the HQ to remote office. From remote office I can not ping or connect to for example MainServer.
Thanks in advance.
Hi Ekobravo,
No solution yet. As you have the same issue maybe it's not supported on the MikroTik side or some kind of bug in the MikroTik router product?
Re: IPsec site 2 site VPN. Ping fails in one direction.
Posted: Tue Feb 16, 2016 3:54 pm
by PeterLemmen
This is the configuration on MikroTik side I'm using:
# feb/16/2016 14:01:57 by RouterOS 6.33.5
#
/ip ipsec policy group
set
/ip ipsec proposal
set [ find default=yes ] disabled=yes enc-algorithms=aes-128-ctr lifetime=10m \
pfs-group=none
add enc-algorithms=3des lifetime=1h name="Azure Site 2 Site VPN" pfs-group=\
none
/ip ipsec peer
add address=*.*.*.*/32 enc-algorithm=3des nat-traversal=no secret=\
******* send-initial-contact=no
/ip ipsec policy
set 0 disabled=yes dst-address=0.0.0.0/32 src-address=0.0.0.0/32
add dst-address=192.168.4.0/22 proposal="Azure Site 2 Site VPN" \
sa-dst-address=*.*.*.* sa-src-address=*.*.*.* src-address=\
192.168.0.0/22 tunnel=yes
Re: IPsec site 2 site VPN. Ping fails in one direction.
Posted: Tue Feb 16, 2016 5:19 pm
by ekobravo
I'm using similar configuration. Try so far probably 4-5 times with even different routers. This is my first IPces configuration. I managed to setup PPTP, EOIP, EOIP over PPTP etc. (for different customer) and it's working fine.
This is what I don't get. Why MikroTik help doesn't want to help? It is beyond believe. If is something (like for example) hardware doesn't support this they should come and say it. Or if there is solution... they should know...tell us. It is unbelievable.
Thanks for your reply look like we are on our own on this.
P.S. If you find solution please post it. THANKS
Re: IPsec site 2 site VPN. Ping fails in one direction.
Posted: Wed Feb 17, 2016 10:05 am
by jaytcsd
Re: IPsec site 2 site VPN. Ping fails in one direction.
Posted: Wed Feb 17, 2016 1:07 pm
by HansHinnekint
Hi,
I'm a bit further than that: I can ping in both directions but not yet really use it:
This is the config:
Home Range: 192.168.1.0/24
Azure Network Range: 10.200.0.0/16
My Pubic IP: 81.3.30.135
Azure gateway IP: 140.13.104.73
These are my settings:
/ip ipsec peer
add address=140.13.104.73/32 dpd-interval=disable-dpd enc-algorithm=aes-256 \
lifetime=1h secret=VeryDeepSeCret!
/ip ipsec policy
add dst-address=10.200.0.0/16 sa-dst-address=140.113.104.73 sa-src-address=\
81.3.30.135 src-address=192.168.1.0/24 tunnel=yes
/ip firewall filter
add chain=input comment="Allow from Azure" log=yes protocol=ipsec-esp \
src-address=140.13.104.73
add chain=forward in-interface=Internet-Outside src-address=10.200.0.0/16
add chain=input comment="default configuration" protocol=icmp
add chain=input comment="default configuration" connection-state=\
established,related
add action=drop chain=input comment="default configuration" in-interface=\
Internet-Outside log=yes
add action=fasttrack-connection chain=forward comment="default configuration" \
connection-state=established,related
add chain=forward comment="default configuration" connection-state=\
established,related
add action=drop chain=forward comment="default configuration" \
connection-state=invalid log=yes
add action=drop chain=forward comment="default configuration" \
connection-nat-state=!dstnat connection-state=new in-interface=\
Internet-Outside log=yes
/ip firewall nat
add chain=srcnat comment="Azure VPN Tunnel" dst-address=10.200.0.0/16 log=yes \
src-address=192.168.1.0/24
add chain=dstnat comment="Azure VPN Tunnel" dst-address=\
192.168.1.0/24 src-address=10.200.0.0/16
add action=masquerade chain=srcnat comment="default configuration" \
out-interface=Internet-Outside
Still struggling on using basic things like RDP over this connection.
Re: IPsec site 2 site VPN. Ping fails in one direction.
Posted: Wed Feb 17, 2016 2:05 pm
by ekobravo
I'm using version 6.34.1
I can ping from HQ router everything but from remote office I can ping only HQ router.
I did try to add ipip with ipsec but it is doing the same thing. I think we are missing some routing here but I'm not sure what. I can also ping in both directions but only routers IP nothing else.
I'm at the point that I will probably get cisco routers and finish the job. I can not understand why Mikrotik is not helping. Forum should be the place that we are helping one to another. But if there is no right answer or solution Mikrotik should jump in. They should help. We are buying their product. We are using their product.
Where is the logic (read future) here?????
Re: IPsec site 2 site VPN. Ping fails in one direction.
Posted: Wed Feb 17, 2016 2:47 pm
by HansHinnekint
I'm using version 6.34.1
I can ping from HQ router everything but from remote office I can ping only HQ router.
I did try to add ipip with ipsec but it is doing the same thing. I think we are missing some routing here but I'm not sure what. I can also ping in both directions but only routers IP nothing else.
I'm at the point that I will probably get cisco routers and finish the job. I can not understand why Mikrotik is not helping. Forum should be the place that we are helping one to another. But if there is no right answer or solution Mikrotik should jump in. They should help. We are buying their product. We are using their product.
Where is the logic (read future) here?????
Well, I think you need to add the source NAT rules (like in my sample above) to make it work.
Re: IPsec site 2 site VPN. Ping fails in one direction.
Posted: Wed Feb 17, 2016 3:26 pm
by ekobravo
I have this
/ip firewall nat
add chain=srcnat comment="VPN Tunnel" dst-address=192.168.17.0/24 log=no \
src-address=172.16.20.0/24
add action=masquerade chain=srcnat comment="default configuration" \
out-interface=WAN
Re: IPsec site 2 site VPN. Ping fails in one direction.
Posted: Wed Feb 17, 2016 5:59 pm
by HansHinnekint
I have this
/ip firewall nat
add chain=srcnat comment="VPN Tunnel" dst-address=192.168.17.0/24 log=no \
src-address=172.16.20.0/24
add action=masquerade chain=srcnat comment="default configuration" \
out-interface=WAN
I just had a word with Mirotik Support and they were really helpfull:
What I needed to do is:
/ip ipsec peer
add address=140.13.104.73/32 dpd-interval=disable-dpd enc-algorithm=aes-256 \
lifetime=1h secret=VeryDeepSeCret!
/ip ipsec policy
add dst-address=10.200.0.0/16 sa-dst-address=140.113.104.73 sa-src-address=\
81.3.30.135 src-address=192.168.1.0/24 tunnel=yes
/ip firewall filter
add chain=forward comment="Allow from Azure" dst-address=10.200.0.0/16 \
src-address=192.168.1.0/24 place-before=0
/add chain=forward dst-address=192.168.1.0/24 src-address=10.200.0.0/16 \
place-before=0
/add chain=input comment="Allow from Azure" log=yes protocol=ipsec-esp \
src-address=140.113.104.73
/ip firewall nat
add chain=srcnat comment="Azure VPN Tunnel" dst-address=10.200.0.0/16 log=yes \
src-address=192.168.1.0/24 place-before=0
Now everything works fine

Re: IPsec site 2 site VPN. Ping fails in one direction.
Posted: Wed Feb 17, 2016 6:52 pm
by ekobravo
Thanks for reply I'll try this and let you know,

Re: IPsec site 2 site VPN. Ping fails in one direction.
Posted: Wed Feb 17, 2016 7:08 pm
by ekobravo
For me still not working:
This is what I put:
/ip firewall filter
add chain=forward comment="" dst-address=192.168.17.0/24 \
src-address=172.16.20.0/24
add chain=forward comment="" dst-address=172.16.20.0/24 \
src-address=192.168.17.0/24
it is place-before=0
/ip firewall nat
add chain=srcnat comment="VPN Tunnel" dst-address=192.168.17.0/24 log=no \
src-address=172.16.20.0/24
add action=masquerade chain=srcnat comment="default configuration" \
out-interface=WAN
Re: IPsec site 2 site VPN. Ping fails in one direction.
Posted: Wed Feb 17, 2016 7:17 pm
by HansHinnekint
For me still not working:
This is what I put:
/ip firewall filter
add chain=forward comment="" dst-address=192.168.17.0/24 \
src-address=172.16.20.0/24
add chain=forward comment="" dst-address=172.16.20.0/24 \
src-address=192.168.17.0/24
it is place-before=0
/ip firewall nat
add chain=srcnat comment="VPN Tunnel" dst-address=192.168.17.0/24 log=no \
src-address=172.16.20.0/24
add action=masquerade chain=srcnat comment="default configuration" \
out-interface=WAN
I got help from Mirotik after a mail to
support@mikrotik.com (Maris B.) he was really helpfull
Re: IPsec site 2 site VPN. Ping fails in one direction.
Posted: Wed Feb 17, 2016 7:22 pm
by ekobravo
Is it possible that "fasttrack dummy rule" makes mess in firewall,what do you think? I have on one router but not on another one.
Re: IPsec site 2 site VPN. Ping fails in one direction.
Posted: Wed Feb 17, 2016 9:54 pm
by HansHinnekint
Is it possible that "fasttrack dummy rule" makes mess in firewall,what do you think? I have on one router but not on another one.
According to the support guy 'We have to accept the traffic in firewall that should go through the ipsec tunnel before the fasttrack rule.'
this is why the
place-before=0 is required
Re: IPsec site 2 site VPN. Ping fails in one direction.
Posted: Wed Feb 17, 2016 10:19 pm
by ekobravo
I know but I can not place the ipsec tunnel before the fasttrack rule. I can not even delete fasttrack rule. I'm just searching forum to find out how to remove or disable this rule but looks like it is not possible. Anyhow, thanks.
Re: IPsec site 2 site VPN. Ping fails in one direction.
Posted: Wed Feb 17, 2016 10:37 pm
by scampbell
To get rid of fasttrack there is a firewall rule created by default directly below the two rules to allow established and related with an action=fasttrack-connection.
The rule looks like this:-
"add action=fasttrack-connection chain=forward comment="default configuration" \
connection-state=established,related"
Delete this then reboot your router - the dynamic rules should no longer be present.
If your VPN is only working one way try disabling (temporarily) any drop rules in the firewall. Does it now work ? If yes then you need to ensure your VPN traffic is allowed in. It's incoming interface is the WAN interface (perhaps ether1 or pppoe-out1? )
Dont forget to re-enable your drop rules after this !!!
Enabling logging on any drop rules may also be helpful.
Also check any dst-nat rules are not catching your IPSEC traffic. Disable them while testing or make them very specific by specifying a dst-address that is your WAN address.
Lastly download and read the Packet Flow Diagram - it is very helpful in understanding how IPSEC is processed through the router.
Re: IPsec site 2 site VPN. Ping fails in one direction.
Posted: Thu Feb 18, 2016 9:54 am
by PeterLemmen
Thank you scampbell for your useful tip to temporary disable firewall rules. I disabled them one by one and found out the following rule from the default configuration was blocking my ping from Microsoft Azure to on premise network:
add action=drop chain=forward comment="default configuration" \
connection-nat-state=!dstnat connection-state=new in-interface=\
ether1-gateway
I was also earlier in contact with Maris B. from support. He pointed me to the following information on the MikroTik WIKI:
http://wiki.mikrotik.com/wiki/Manual:IP ... d_proposal
You can find there that you need to put in the NAT Bypass. I think what is missing is you
ALSO have to add a Firewall Filter Rule to allow the traffic from the remote side to forward into your on premise network. This was blocked by the above rule in my MikroTik router that I put in my router during initial setup and at that time (and still does) makes sense.
Could not find anything about this in the MikroTik WIKI link I shared above. But that's ok because at least now I could figure out what I needed to solve this problem. I just allow the subnet in Microsoft Azure to communicate with the subnet on premise with this single line and put it on top of the Filter rules:
add chain=forward comment="Allow from Azure" dst-address=192.168.0.0/22 \
src-address=192.168.4.0/22 place-before=0
Problem solved, everything working now.
Thanks a lot guys for your help!
Cheers,
Peter
Re: IPsec site 2 site VPN. Ping fails in one direction.
Posted: Thu Feb 18, 2016 11:26 am
by mrz
Not only that, but also fast-track rule affects ipsec traffic. So for tunnel mode to work properly you need to allow tunnelled traffic before fast-track or rule with connection-nat-state=!dstnat.
Re: IPsec site 2 site VPN. Ping fails in one direction.
Posted: Thu Feb 18, 2016 4:13 pm
by ekobravo
Not only that, but also fast-track rule affects ipsec traffic. So for tunnel mode to work properly you need to allow tunnelled traffic before fast-track or rule with connection-nat-state=!dstnat.
And how can I do this? If I try yo move firewall rule before fast-track rule I'm getting this error message:
"Couldn't move Firewall Rule <172.16.20.0/24->192.168.17.0/24> -cannot move builtin(6)"
If I try to delete this is what I'm getting:
""Couldn't move Firewall Rule <> - -cannot move builtin(6)"
So, is it the only way to reset configuration, remove configuration and start from beginning?
Thanks
Re: IPsec site 2 site VPN. Ping fails in one direction.
Posted: Fri Feb 19, 2016 12:11 pm
by mrz
Not sure what exactly you are trying to move, but none of my mentioned rules are built in. They are created either by default configuration or by user.
Re: IPsec site 2 site VPN. Ping fails in one direction.
Posted: Fri Feb 19, 2016 12:18 pm
by HansHinnekint
Not sure what exactly you are trying to move, but none of my mentioned rules are built in. They are created either by default configuration or by user.
This is done by the
place-before=0 option
This is what works for me:
/ip firewall filter
add chain=forward comment="Allow from Azure" dst-address=10.200.0.0/16 \
src-address=192.168.1.0/24 place-before=0
/add chain=forward dst-address=192.168.1.0/24 src-address=10.200.0.0/16 \
place-before=0
Re: IPsec site 2 site VPN. Ping fails in one direction.
Posted: Fri Feb 19, 2016 5:12 pm
by ekobravo
Not sure what exactly you are trying to move, but none of my mentioned rules are built in. They are created either by default configuration or by user.
This is done by the
place-before=0 option
This is what works for me:
/ip firewall filter
add chain=forward comment="Allow from Azure" dst-address=10.200.0.0/16 \
src-address=192.168.1.0/24 place-before=0
/add chain=forward dst-address=192.168.1.0/24 src-address=10.200.0.0/16 \
place-before=0
Problem also solved, everything working now.THANKS
Re: IPsec site 2 site VPN. Ping fails in one direction.
Posted: Wed Aug 31, 2016 11:15 am
by arovah
Hi guys,
I have same issue. If i ping from mikrotik to vm cloud was failed but if i test ping from vm cloud to my mikrotik was success.
I have set firewall nat in mikrotik :
add chain=srcnat action=accept place-before=0 src-address=10.62.1.0/24 dst-address=192.168.62.0/24
And add firewall filter :
add chain=forward dst-address=10.62.1.0/24 src-address=192.168.62.0/24 place-before=0
add chain=forward dst-address=192.168.62.0/24 src-address=10.62.1.0/24 place-before=0
This is my ip for vm cloud :
ip public : 119.202.xxx.xxx
ip private : 192.168.62.0/24
This is my ip for mikrotik :
ip public : 202.202.xxx.xxx
ip private : 10.62.1.0/24
Please any solution ? Thanks in advance
Re: IPsec site 2 site VPN. Ping fails in one direction.
Posted: Wed Mar 14, 2018 12:09 am
by phatone007
I have this
/ip firewall nat
add chain=srcnat comment="VPN Tunnel" dst-address=192.168.17.0/24 log=no \
src-address=172.16.20.0/24
add action=masquerade chain=srcnat comment="default configuration" \
out-interface=WAN
I just had a word with Mirotik Support and they were really helpfull:
What I needed to do is:
/ip ipsec peer
add address=140.13.104.73/32 dpd-interval=disable-dpd enc-algorithm=aes-256 \
lifetime=1h secret=VeryDeepSeCret!
/ip ipsec policy
add dst-address=10.200.0.0/16 sa-dst-address=140.113.104.73 sa-src-address=\
81.3.30.135 src-address=192.168.1.0/24 tunnel=yes
/ip firewall filter
add chain=forward comment="Allow from Azure" dst-address=10.200.0.0/16 \
src-address=192.168.1.0/24 place-before=0
/add chain=forward dst-address=192.168.1.0/24 src-address=10.200.0.0/16 \
place-before=0
/add chain=input comment="Allow from Azure" log=yes protocol=ipsec-esp \
src-address=140.113.104.73
/ip firewall nat
add chain=srcnat comment="Azure VPN Tunnel" dst-address=10.200.0.0/16 log=yes \
src-address=192.168.1.0/24 place-before=0
Now everything works fine

This worked me me!
Thanks
Re: IPsec site 2 site VPN. Ping fails in one direction.
Posted: Sat May 05, 2018 2:08 pm
by Bas2033
Same problem here. Unfortunately the solution #34 describes doesn't work for me.
Here is my config:
/ip firewall filter
0 ;;; Allow from Local to Azure intern
chain=forward src-address=192.168.6.0/24 dst-address=10.0.0.0/16
1 ;;; Allow from Azure intern to Local
chain=forward action=accept src-address=10.0.0.0/24 dst-address=192.168.6.0/24 log=no log-prefix=""
2 ;;; Allow from Azure extern
chain=input protocol=ipsec-esp src-address=52.233.x.x log=yes
/ip firewall nat
0 ;;; VPN Tunnel to Azure
chain=srcnat action=accept src-address=192.168.6.0/24 dst-address=10.0.0.0/16 log=no log-prefix=""
1 ;;; VPN Tunnel from Azure
chain=srcnat src-address=10.0.0.0/16 dst-address=192.168.6.0/24 log=no
2 ;;; default configuration van forum
chain=srcnat action=masquerade out-interface=ether1 log=no log-prefix=""
/ip ipsec policy
0 A src-address=192.168.6.0/24 src-port=any dst-address=10.0.0.0/16 dst-port=any protocol=all action=encrypt level=require ipsec-protocols=esp tunnel=yes sa-src-address=213.127.x.x sa-dst-address=52.233.x.x
proposal=default ph2-count=1
1 T * group=default src-address=::/0 dst-address=::/0 protocol=all proposal=default template=yes
/ip ipsec/peer
0 address=52.233.x.x/32 auth-method=pre-shared-key secret="secret" generate-policy=no policy-template-group=default exchange-mode=ike2 send-initial-contact=yes hash-algorithm=sha1 enc-algorithm=aes-256,aes-128
dh-group=modp1024 lifetime=8h dpd-interval=disable-dpd
1 R address=::/0 auth-method=pre-shared-key secret="" generate-policy=no policy-template-group=default exchange-mode=main send-initial-contact=yes nat-traversal=yes proposal-check=obey hash-algorithm=sha1
enc-algorithm=aes-128,3des dh-group=modp2048,modp1024 lifetime=1d dpd-interval=disable-dpd
My version of RouterOS is 6.42.1.
Any idea's will be appreciated.
Re: IPsec site 2 site VPN. Ping fails in one direction.
Posted: Tue May 08, 2018 3:22 pm
by Bas2033
Hi all,
I copied the code from the previous post into the Mikrotik. Unfortunately it didn't let me ping my subnet after the Mikrotik.
I use version 6.42.1 of the RouterOS software. Is there some one who can verify this finding on the current RouterOS version ?
Re: IPsec site 2 site VPN. Ping fails in one direction.
Posted: Mon May 14, 2018 8:24 pm
by Bas2033
Hi All,
Emils of Mikrotik helped me out. He said I correctly configured the router. So I rechecked my firewall settings on the windows box. Icmp ports were open. I could ping locally. I shutted the windows firewall complete down. Et voila it worked. I enabled the firewall again. I decided to use the command line to open for ICMP.
netsh advfirewall firewall add rule name="ICMP Allow incoming V4 echo request" protocol=icmpv4:8,any dir=in action=allow and netsh advfirewall firewall add rule name="ICMP Allow incoming V6 echo request" protocol=icmpv6:8,any dir=in action=allow. This worked with 6.42.1
Regards,
Bas



