Setting up ikev2 road worrior set up. Following step on mikrotik wiki.
Cteated CA signed, created server cert signed with CA, created windows client cert signed with CA.
Exported windows client cert and installed on windows 10 .
No matter what i do getting error ike failed to find vald cert on local machine.
Re: IPsec IKE2 can find valid sertificate
On Windows, do you have the certificate in "local machine" store? If you put it in "local user" store, which I definitely did at first, because it was more logical when I wanted VPN only for that one user, it doesn't work.
Re: IPsec IKE2 can find valid sertificate
Cert is installed on local machine not userOn Windows, do you have the certificate in "local machine" store? If you put it in "local user" store, which I definitely did at first, because it was more logical when I wanted VPN only for that one user, it doesn't work.
Re: IPsec IKE2 can find valid sertificate
Could someone show all steps creating certs for ikev2 for windows 10
Re: IPsec IKE2 can find valid sertificate [SOLVED]
You need to import also CA, not just client cert.
Re: IPsec IKE2 can find valid sertificate
you are 100% right this what i have done today and it works perfectly, you just confirmed it and you are right as always, really appreciate your input.You need to import also CA, not just client cert.
Re: IPsec IKE2 can find valid sertificate
Does this still work ???? I have followed the wiki to the letter, i have imported both ca and client certs (client.crt) and Client.pkcs12 to the local computer Trusted Root Certtification store - and i still get Cant connect to IKE failed to find Valid machine cerificate. Error ?
Also on my Windows 10 machine i cant select certificate in the setup it changes to General Authentication Method. I can go into network adapter and select certificate there !
Also on my Windows 10 machine i cant select certificate in the setup it changes to General Authentication Method. I can go into network adapter and select certificate there !
Re: IPsec IKE2 can find valid sertificate
A wild guess - when exporting the certificate for the client, have you entered the export-passphrase? Because if you don't, e.g. as you think it's not necessary because you only copy the file on a LAN, the private key is not exported at all, hence the exported certificate cannot be used to sign data after import on the client machine.I have followed the wiki to the letter, i have imported both ca and client certs (client.crt) and Client.pkcs12 to the local computer Trusted Root Certtification store - and i still get Cant connect to IKE failed to find Valid machine cerificate.
The CA certificate should be exported without the private key (so without entering the export-passphrase) for import at client, the client certificate should be exported with the private key.
Also, I don't get why you mention client.crt as the wiki clearly says to use only pkcs12 format (where the certificate and the key are exported into the same file).
Re: IPsec IKE2 can find valid sertificate
These are steps I did -
1. Create CA
2. Create server certificate
3. Create client certificate
4. Export client certificate as PKCS12
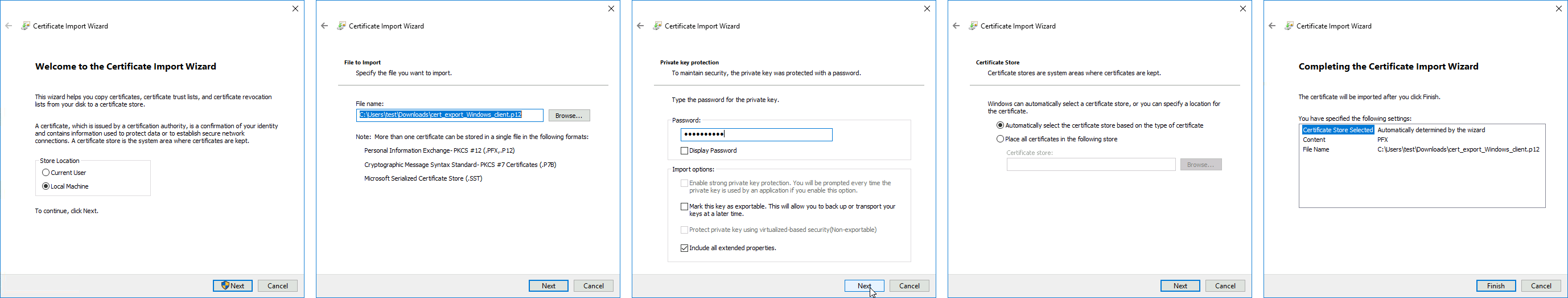
5. Import certificate to Local Machine store
6. Create new VPN profile
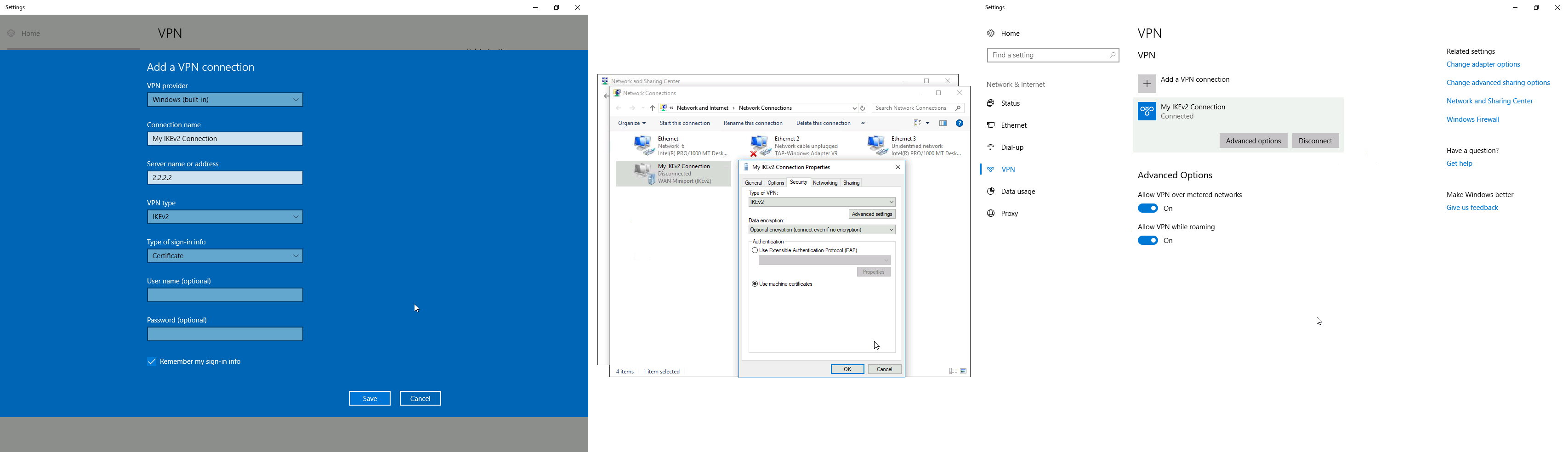
Now, if you have more than one IKE2 RSA VPN's created, you should specify which certificate Windows should use, because Windows is stupid and can't automatically determine the right certificate for each VPN profile.
1. Open Powershell and enter certlm.msc to open Local Machine Certificate tool
2. Under Trusted Root Certification.. find your certificate and open it with double click
3. Select Details and copy Serial number
4. Go back to Powershell and create new variable with specified serial number
$ca = Get-ChildItem Cert:\LocalMachine\Root\ | ? SerialNumber -EQ <serial number>
5. Check whether variable can find you certificate, it should return something
$ca
6. Add certificate to your created VPN profile
Set-VpnConnection -Name <your VPN profile name> -MachineCertificateIssuerFilter $ca
Be happy now.
1. Create CA
Code: Select all
/certificate
add common-name=XX.XX.XX.XX name=XX.XX.XX.XX
sign "XX.XX.XX.XX" ca-crl-host=XX.XX.XX.XX2. Create server certificate
Code: Select all
add common-name=XX.XX.XX.XX subject-alt-name=IP:XX.XX.XX.XX key-usage=tls-server name="IKE2 RSA server"
sign "IKE2 RSA server" ca=XX.XX.XX.XX3. Create client certificate
Code: Select all
add common-name=Client name=Client key-usage=tls-client
sign Client ca=XX.XX.XX.XX4. Export client certificate as PKCS12
Code: Select all
export-certificate Client export-passphrase=SuperStrongPass123 type=pkcs125. Import certificate to Local Machine store

6. Create new VPN profile

Now, if you have more than one IKE2 RSA VPN's created, you should specify which certificate Windows should use, because Windows is stupid and can't automatically determine the right certificate for each VPN profile.
1. Open Powershell and enter certlm.msc to open Local Machine Certificate tool
2. Under Trusted Root Certification.. find your certificate and open it with double click
3. Select Details and copy Serial number
4. Go back to Powershell and create new variable with specified serial number
$ca = Get-ChildItem Cert:\LocalMachine\Root\ | ? SerialNumber -EQ <serial number>
5. Check whether variable can find you certificate, it should return something
$ca
6. Add certificate to your created VPN profile
Set-VpnConnection -Name <your VPN profile name> -MachineCertificateIssuerFilter $ca
Be happy now.
Re: IPsec IKE2 can find valid sertificate
@Fesiitis, thank you very much for the powershell part. That was the bit I was always missing (luckily, I never actually needed it so far).
-

-
PavelRadvan
just joined
- Posts: 11
- Joined:
- Location: Prague, Czech Republic
Re: IPsec IKE2 can find valid sertificate
Hi,
thanks very much - powershell setting of certificate filter helped also to me.
thanks very much - powershell setting of certificate filter helped also to me.
Re: IPsec IKE2 can find valid sertificate
Tried you metod but not working...
I'm missing one step... when do you setup de client cert on windows client?
I'm missing one step... when do you setup de client cert on windows client?
Re: IPsec IKE2 can find valid sertificate
Mate, million thanks to you for sharing the PowerShell part on how to make IKEv2 to use the proper cert. Thanks gain.
Re: IPsec IKE2 can find valid sertificate
Большое спасибо
Be happy now.
Re: IPsec IKE2 can find valid sertificate
Fesiitis, for two weeks I cannot find a solution for this and your advice with $ca works perfectly!
Big thanks from Bulgaria! I really appreciate your help!
And I laughed when I read that Windows is stupid. It's true! It's stupid!
Big thanks from Bulgaria! I really appreciate your help!
And I laughed when I read that Windows is stupid. It's true! It's stupid!



