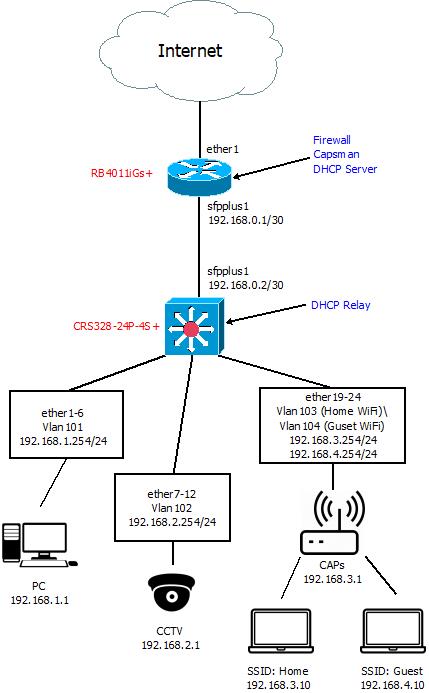
So for a case where
the wireless interfaces are created at the CAPsMAN machine, this is a real life configuration adopted to your network.
To simplify things and save a bit of CPU, the home and guest subnets are linked to individual bridge interfaces, so no VLANs are used for them.
CAPsMAN:
/interface bridge
add name=br-home protocol-mode=none
add name=br-guest protocol-mode=none
/ip address
add interface=br-home address=192.168.3.254/24
add interface=br-guest address=192.168.4.254/24
/caps-man channel
add band=2ghz-b/g/n control-channel-width=20mhz extension-channel=disabled frequency=2412,2432,2452,2472 name=2G4
add band=5ghz-a/n/ac control-channel-width=20mhz extension-channel=Ce frequency=5180,5200,5220,5240,5260,5280,5300,5320 name=5G
/caps-man security
add authentication-types=wpa2-psk encryption=aes-ccm name=home passphrase=pwd-for-home
add authentication-types=wpa2-psk encryption=aes-ccm name=guest passphrase=pwd-for-guest
/caps-man configuration
add channel=2G4 country="wonderland" datapath=home distance=indoors installation=indoor mode=ap name=home-2G security=home ssid=home
add channel=5G country="wonderland" datapath=home distance=indoors installation=indoor mode=ap name=home-5G security=home ssid=home
add country="wonderland" datapath=guest distance=indoors installation=indoor mode=ap name=guest-2G security=guest ssid=guest
add country="wonderland" datapath=guest distance=indoors installation=indoor mode=ap name=guest-5G security=guest ssid=guest
/caps-man datapath
add bridge=br-home local-forwarding=no name=home
add bridge=br-guest local-forwarding=no name=guest
/caps-man manager
set enabled=yes
/caps-man provisioning
add action=create-enabled hw-supported-modes=b,g,gn master-configuration=home-2G slave-configurations=guest-2G
add action=create-enabled hw-supported-modes=a,an,ac master-configuration=home-5G slave-configurations=guest-5G
(plus the DHCP server configurations for 192.168.3.0/24 and 192.168.4.0/24 and some firewall rules if required)
CAP:
/interface wireless cap
set enabled=yes interfaces=wlan1,wlan2 caps-man-addresses=192.168.0.1
(how do you define the CAP's own IP address and routing is up to you; the own address just must not be in 192.168.3.0/24 or 192.168.4.0/24).
For
local forwarding on CAPs, it would look as follows:
CAPsMAN:
/caps-man channel
add band=2ghz-b/g/n control-channel-width=20mhz extension-channel=disabled frequency=2412,2432,2452,2472 name=2G4
add band=5ghz-a/n/ac control-channel-width=20mhz extension-channel=Ce frequency=5180,5200,5220,5240,5260,5280,5300,5320 name=5G
/caps-man security
add authentication-types=wpa2-psk encryption=aes-ccm name=home passphrase=pwd-for-home
add authentication-types=wpa2-psk encryption=aes-ccm name=guest passphrase=pwd-for-guest
/caps-man configuration
add channel=2G4 country="wonderland" datapath=home distance=indoors installation=indoor mode=ap name=home-2G security=home ssid=home
add channel=5G country="wonderland" datapath=home distance=indoors installation=indoor mode=ap name=home-5G security=home ssid=home
add country="wonderland" datapath=guest distance=indoors installation=indoor mode=ap name=guest-2G security=guest ssid=guest
add country="wonderland" datapath=guest distance=indoors installation=indoor mode=ap name=guest-5G security=guest ssid=guest
/caps-man datapath
add bridge=bridge local-forwarding=yes name=home
add bridge=bridge local-forwarding=yes name=guest vlan-mode=use-tag vlan-id=104
/caps-man manager
set enabled=yes
/caps-man provisioning
add action=create-enabled hw-supported-modes=b,g,gn master-configuration=home-2G slave-configurations=guest-2G
add action=create-enabled hw-supported-modes=a,an,ac master-configuration=home-5G slave-configurations=guest-5G
The assumption here is that VLAN 103 is available tagless on the CAP-facing ports of the 328, so CAP's own address is in 192.168.3.0/24 as on your drawing. The VLAN-related settings below are relevant for
vlan-filtering=yes on the bridge, but you actually don't need this mode with this simple setup. If you keep
vlan-filtering=no, the
pvid settings in
/interface bridge port section are irrelevant, and so is the whole section
/interface bridge vlan; if you opt to use
vlan-filtering=yes, first set all the
/interface bridge ... settings without it (i.e. with the default
no) and then, as the last step, do
/interface bridge set bridge vlan-filtering=yes. Otherwise you'll lock yourself out.
/interface bridge
add name=bridge pvid=103
/interface bridge port
add bridge=bridge interface=ether1 pvid=103
/interface bridge vlan
add bridge=bridge vlan-ids=103
add bridge=bridge vlan-ids=104 tagged=bridge,ether1
/ip dhcp-client
add interface=bridge
/interface wireless cap
set enabled=yes interfaces=wlan1,wlan2 caps-man-addresses=192.168.0.1
Also here, setting
vlan-filtering to
yes may be a dangerous step if
sfpplus1 is a member port of the bridge.
/interface bridge
add name=bridge vlan-filtering=yes
/interface bridge vlan
add bridge=bridge vlan-ids=103 tagged=bridge
add bridge=bridge vlan-ids=104 tagged=bridge,ether19,ether20,ether21,ether22,ether23,ether24
/interface bridge port
add bridge=bridge interface=ether19 pvid=103
add bridge=bridge interface=ether20 pvid=103
add bridge=bridge interface=ether21 pvid=103
add bridge=bridge interface=ether22 pvid=103
add bridge=bridge interface=ether23 pvid=103
add bridge=bridge interface=ether24 pvid=103
/interface vlan
add name=bridge.home.103 vlan-id=103 interface=bridge
add name=bridge.guest.104 vlan-id=104 interface=bridge
/ip address
add interface=bridge.home.103 address=192.168.3.254/24
add interface=bridge.guest.104 address=192.168.4.254/24
(plus the DHCP server configurations for 192.168.3.0/24 and 192.168.4.0/24 and some firewall rules if required)
If you set
caps-manager=192.168.0.1 in the
/ip dhcp-server network row responsible for assigning IP configuration to the CAPs, you don't need to configure it statically on the CAPs, so it becomes more or less a zero-touch configuration on the CAP devices if you use the reset button to boot them into CAP mode. There is just some non-intuitive step you have to take to make them stay in CAP mode on the next power cycle, it has been discussed here on the forum about half a year ago.