Page 1 of 1
Brute passwords of microtik devices from the local network, how to identify malware?
Posted: Fri Oct 29, 2021 5:11 pm
by riwer
Hello,
In the logs of Mikrotik devices (router and 3 access points), I periodically (few times a week) find the following
login failure for user admin from 192.168.1.147 via ssh
login failure for user MikroTikSystem from 192.168.1.147 via ssh
login failure for user dircreate from 192.168.1.147 via ssh
login failure for user EServicios from 192.168.1.147 via ssh
and similar entries for ftp and telnet
I configured logging of ports 21,22,23 on Mikrotik devices and can see the time and details of connections from the hosts on the local network
Oct/28/2021 22:39:01 firewall,info login telnet/ftp/ssh input: in:bridge out:(unknown 0), src-mac f8:0f:41:b5:0b:34, proto TCP (SYN), 192.168.1.147:61740->192.168.1.81:22, len 52
The brute-forcing of passwords comes from different windows hosts every time, sometimes it happens at night when there is no one at the workplace, so the human factor disappears
I scanned the last two hosts from which there was a brute-force attack with three different antivirus tools and they did not find anything dangerous
Perhaps the malicious code is using spoofing of the attacker's address?
Does anyone have any idea how to identify malware?
Re: Brute passwords of microtik devices from the local network, how to identify malware?
Posted: Fri Oct 29, 2021 5:47 pm
by holvoetn
It seems to be the same IP address each time ?
Check log files which MAC received that IP address.
Is it always the same device ?
My take (others will surely have much better ideas)
Check in your IP leases which device has that MAC address. If there is some malware spoofing the IP, it should have a different IP (but then again they should be able to do the same with MAC).
If you're lucky, there is a name next to it which might help you to find which device it is.
If not, at least you now should have a handle.
Firewall rule:
/ip firewall filter
add chain=forward src-mac-address=aa:bb:cc:dd:ee:ff action=drop
Someone should come complaining ...

PS and update your anti-virus tools on all clients !!
Re: Brute passwords of microtik devices from the local network, how to identify malware?
Posted: Fri Oct 29, 2021 7:07 pm
by anav
Please post your config including firewall rules to ensure there are not gaps.
/export hide-sensitive file=anynameyouwish
Re: Brute passwords of microtik devices from the local network, how to identify malware?
Posted: Sun Nov 14, 2021 10:20 pm
by dbenes
I can see this issue was not yet closed. I have similar one:
My Mikrotik devices are under this attack:
nov/12 22:26:40 system,error,critical login failure for user from 192.168.215.48 via ssh
nov/12 22:26:40 system,error,critical login failure for user admin from 192.168.215.48 via ssh
nov/12 22:26:40 system,error,critical login failure for user admin from 192.168.215.48 via ssh
nov/12 22:26:40 system,error,critical login failure for user MikroTikSystem from 192.168.215.48 via ssh
nov/12 22:26:40 system,error,critical login failure for user admin from 192.168.215.48 via ssh
nov/12 22:26:41 system,error,critical login failure for user dircreate from 192.168.215.48 via ssh
nov/12 22:26:41 system,error,critical login failure for user SolucTec from 192.168.215.48 via ssh
nov/12 22:26:41 system,error,critical login failure for user EServicios from 192.168.215.48 via ssh
After some investigation I recognized the source is my computer !
I am using PC+Win10, antivirus installed and updated, no viruses found.
Now trying to find what sw is to the hell calling port 22 from my computer
Did anyone find what it is?
Re: Brute passwords of microtik devices from the local network, how to identify malware?
Posted: Mon Nov 15, 2021 7:52 pm
by holvoetn
What worries me... with different user accounts.
You got a bug. I think...
Re: Brute passwords of microtik devices from the local network, how to identify malware?
Posted: Mon Nov 15, 2021 11:14 pm
by rextended
Your computer have remote desktop service active?
Re: Brute passwords of microtik devices from the local network, how to identify malware?
Posted: Mon Nov 15, 2021 11:50 pm
by ivicask
You have virus i saw this at customers laptop also recently, it had some obvious name like crcs, i forgot exactly, and was even visible in regular startup entries...
Cleanup your pc dude.
Re: Brute passwords of microtik devices from the local network, how to identify malware?
Posted: Tue Nov 16, 2021 2:52 am
by Znevna
Two weeks, he probably lost the routers already.
login failure for user admin from 192.168.1.147 via ssh <--- how to identify??? lol.
Re: Brute passwords of microtik devices from the local network, how to identify malware?
Posted: Thu Feb 23, 2023 2:28 pm
by spanik
Hello All
Sorry to hijack this old post, but I now have exactly the same as descibed as riwer & dbenes.
A rather recent PC (Clean windows 11 installation, up to date with all securyt hotfixes and deployed from Day #1 with Paid AVG Antivirus & Paid Malwarebytes) is now flagged as the source of multiple attempts to ssh, telnet and ftp onto my running Mikrotik device running Router OS 7.7
It is always the same users that are tried:
MikroTikSystem
dircreate
EServicios
HPSupport
guest
admin
root
etc...
I have a script that monitors failed logins, and I was informed automatically
20:32:54 - login failure for user admin from 192.168.0.46 via ssh;
20:32:55 - login failure for user admin from 192.168.0.46 via ssh;
20:32:56 - login failure for user admin from 192.168.0.46 via ssh;
20:32:57 - login failure for user dircreate from 192.168.0.46 via ssh;
20:32:58 - login failure for user MikroTikSystem from 192.168.0.46 via ssh;
20:32:59 - login failure for user EServicios from 192.168.0.46 via ssh;
20:33:00 - login failure for user from 192.168.0.46 via ssh;
20:33:01 - login failure for user SolucTec from 192.168.0.46 via ssh;
20:33:02 - login failure for user admin from 192.168.0.46 via ssh;
20:33:03 - login failure for user root from 192.168.0.46 via ssh;
20:33:04 - login failure for user sysadm from 192.168.0.46 via ssh;
20:33:05 - login failure for user user from 192.168.0.46 via ssh;
20:33:06 - login failure for user admin from 192.168.0.46 via ssh;
20:33:07 - login failure for user from 192.168.0.46 via ssh;
20:33:08 - login failure for user admin from 192.168.0.46 via ssh;
20:33:10 - login failure for user Admin from 192.168.0.46 via ssh;
20:33:10 - login failure for user root from 192.168.0.46 via ssh;
20:33:10 - login failure for user root from 192.168.0.46 via ssh;
20:33:11 - login failure for user admin from 192.168.0.46 via ssh;
20:33:12 - login failure for user guest from 192.168.0.46 via ssh;
20:33:14 - login failure for user Administrator from 192.168.0.46 via ssh;
20:33:14 - login failure for user root from 192.168.0.46 via ssh;
20:33:14 - login failure for user root from 192.168.0.46 via ssh;
20:33:15 - login failure for user meo from 192.168.0.46 via ssh;
20:33:16 - login failure for user Admin from 192.168.0.46 via ssh;
20:33:17 - login failure for user admin from 192.168.0.46 via ssh;
20:33:18 - login failure for user ubnt from 192.168.0.46 via ssh;
20:33:20 - login failure for user root from 192.168.0.46 via ssh;
20:33:21 - login failure for user admin from 192.168.0.46 via ssh;
20:33:22 - login failure for user vodafone from 192.168.0.46 via ssh;
20:33:23 - login failure for user admin from 192.168.0.46 via ssh;
20:33:24 - login failure for user Administrator from 192.168.0.46 via ssh;
20:33:25 - login failure for user root from 192.168.0.46 via ssh;
20:33:26 - login failure for user Admin from 192.168.0.46 via ssh;
20:33:29 - login failure for user from 192.168.0.46 via telnet;
20:33:30 - login failure for user admin from 192.168.0.46 via telnet;
20:33:31 - login failure for user admin from 192.168.0.46 via telnet;
20:33:38 - login failure for user admin from 192.168.0.46 via ftp;
20:33:39 - login failure for user admin from 192.168.0.46 via ftp;
20:33:40 - login failure for user admin from 192.168.0.46 via ftp;
20:33:41 - login failure for user dircreate from 192.168.0.46 via ftp;
20:33:42 - login failure for user MikroTikSystem from 192.168.0.46 via ftp;
20:33:43 - login failure for user EServicios from 192.168.0.46 via ftp;
20:33:44 - login failure for user SolucTec from 192.168.0.46 via ftp;
20:33:45 - login failure for user admin from 192.168.0.46 via ftp;
20:33:46 - login failure for user root from 192.168.0.46 via ftp;
20:33:47 - login failure for user sysadm from 192.168.0.46 via ftp;
20:33:48 - login failure for user user from 192.168.0.46 via ftp;
20:33:49 - login failure for user admin from 192.168.0.46 via ftp;
20:33:50 - login failure for user admin from 192.168.0.46 via ftp;
20:33:51 - login failure for user Admin from 192.168.0.46 via ftp;
20:33:52 - login failure for user root from 192.168.0.46 via ftp;
20:33:53 - login failure for user admin from 192.168.0.46 via ftp;
20:33:54 - login failure for user guest from 192.168.0.46 via ftp;
20:33:55 - login failure for user Administrator from 192.168.0.46 via ftp;
20:33:56 - login failure for user root from 192.168.0.46 via ftp;
20:33:57 - login failure for user meo from 192.168.0.46 via ftp;
20:33:58 - login failure for user Admin from 192.168.0.46 via ftp;
20:33:59 - login failure for user admin from 192.168.0.46 via ftp;
20:34:00 - login failure for user ubnt from 192.168.0.46 via ftp;
20:34:01 - login failure for user root from 192.168.0.46 via ftp;
20:34:02 - login failure for user admin from 192.168.0.46 via ftp;
20:34:03 - login failure for user vodafone from 192.168.0.46 via ftp;
20:34:04 - login failure for user admin from 192.168.0.46 via ftp;
20:34:05 - login failure for user Administrator from 192.168.0.46 via ftp;
20:34:06 - login failure for user root from 192.168.0.46 via ftp;
20:34:08 - login failure for user Admin from 192.168.0.46 via ftp;
20:34:09 - login failure for user admim from 192.168.0.46 via ftp;
20:34:10 - login failure for user webadmin from 192.168.0.46 via ftp;
20:34:11 - login failure for user tech from 192.168.0.46 via ftp;
20:34:12 - login failure for user administrator from 192.168.0.46 via ftp;
20:34:13 - login failure for user manager from 192.168.0.46 via ftp;
20:34:14 - login failure for user root from 192.168.0.46 via ftp;
20:34:15 - login failure for user sysadmin from 192.168.0.46 via ftp;
20:34:16 - login failure for user login from 192.168.0.46 via ftp;
20:34:17 - login failure for user guest from 192.168.0.46 via ftp;
20:34:18 - login failure for user admin2 from 192.168.0.46 via ftp;
20:34:19 - login failure for user user from 192.168.0.46 via ftp;
20:34:20 - login failure for user root from 192.168.0.46 via ftp;
20:34:22 - login failure for user root from 192.168.0.46 via ftp;
20:34:23 - login failure for user support from 192.168.0.46 via ftp;
20:34:24 - login failure for user root from 192.168.0.46 via ftp;
20:34:25 - login failure for user admin from 192.168.0.46 via ftp;
20:34:26 - login failure for user admin from 192.168.0.46 via ftp;
20:34:27 - login failure for user HPSupport from 192.168.0.46 via ftp;
20:34:28 - login failure for user root from 192.168.0.46 via ftp;
20:34:29 - login failure for user root from 192.168.0.46 via ftp;
20:34:30 - login failure for user admin from 192.168.0.46 via ftp;
20:34:31 - login failure for user login from 192.168.0.46 via ftp;
20:34:32 - login failure for user admin from 192.168.0.46 via ftp;
20:34:33 - login failure for user guest from 192.168.0.46 via ftp;
20:34:35 - login failure for user root from 192.168.0.46 via ftp;
20:34:36 - login failure for user admin from 192.168.0.46 via ftp;
20:34:37 - login failure for user root from 192.168.0.46 via ftp;
20:34:38 - login failure for user admin from 192.168.0.46 via ftp;
20:40:30 - login failure for user admin from 192.168.0.46 via web;
20:41:14 - login failure for user from 192.168.0.46 via telnet;
20:41:15 - login failure for user admin from 192.168.0.46 via telnet;
20:41:16 - login failure for user admin from 192.168.0.46 via telnet;
20:41:25 - login failure for user admin from 192.168.0.46 via ftp;
20:41:27 - login failure for user admin from 192.168.0.46 via ftp;
20:41:28 - login failure for user admin from 192.168.0.46 via ftp;
20:41:29 - login failure for user dircreate from 192.168.0.46 via ftp;
20:41:30 - login failure for user MikroTikSystem from 192.168.0.46 via ftp;
20:41:31 - login failure for user EServicios from 192.168.0.46 via ftp;
20:41:32 - login failure for user SolucTec from 192.168.0.46 via ftp;
20:41:34 - login failure for user admin from 192.168.0.46 via ftp;
20:41:35 - login failure for user root from 192.168.0.46 via ftp;
20:41:36 - login failure for user sysadm from 192.168.0.46 via ftp;
20:41:37 - login failure for user user from 192.168.0.46 via ftp;
20:41:38 - login failure for user admin from 192.168.0.46 via ftp;
20:41:39 - login failure for user admin from 192.168.0.46 via ftp;
20:41:40 - login failure for user Admin from 192.168.0.46 via ftp;
20:41:41 - login failure for user root from 192.168.0.46 via ftp;
20:41:42 - login failure for user admin from 192.168.0.46 via ftp;
20:41:44 - login failure for user guest from 192.168.0.46 via ftp;
20:41:45 - login failure for user Administrator from 192.168.0.46 via ftp;
20:41:46 - login failure for user root from 192.168.0.46 via ftp;
20:41:47 - login failure for user meo from 192.168.0.46 via ftp;
20:41:48 - login failure for user Admin from 192.168.0.46 via ftp;
20:41:49 - login failure for user admin from 192.168.0.46 via ftp;
20:41:50 - login failure for user ubnt from 192.168.0.46 via ftp;
20:41:51 - login failure for user root from 192.168.0.46 via ftp;
20:41:52 - login failure for user admin from 192.168.0.46 via ftp;
20:41:53 - login failure for user vodafone from 192.168.0.46 via ftp;
20:41:54 - login failure for user admin from 192.168.0.46 via ftp;
20:41:56 - login failure for user Administrator from 192.168.0.46 via ftp;
20:41:57 - login failure for user root from 192.168.0.46 via ftp;
20:41:58 - login failure for user Admin from 192.168.0.46 via ftp;
20:41:59 - login failure for user admim from 192.168.0.46 via ftp;
20:42:00 - login failure for user webadmin from 192.168.0.46 via ftp;
20:42:01 - login failure for user tech from 192.168.0.46 via ftp;
20:42:02 - login failure for user administrator from 192.168.0.46 via ftp;
20:42:03 - login failure for user manager from 192.168.0.46 via ftp;
20:42:04 - login failure for user root from 192.168.0.46 via ftp;
20:42:05 - login failure for user sysadmin from 192.168.0.46 via ftp;
20:42:06 - login failure for user login from 192.168.0.46 via ftp;
20:42:07 - login failure for user guest from 192.168.0.46 via ftp;
20:42:08 - login failure for user admin2 from 192.168.0.46 via ftp;
20:42:09 - login failure for user user from 192.168.0.46 via ftp;
20:42:10 - login failure for user root from 192.168.0.46 via ftp;
20:42:11 - login failure for user root from 192.168.0.46 via ftp;
20:42:12 - login failure for user support from 192.168.0.46 via ftp;
20:42:14 - login failure for user root from 192.168.0.46 via ftp;
20:42:15 - login failure for user admin from 192.168.0.46 via ftp;
20:42:16 - login failure for user admin from 192.168.0.46 via ftp;
20:42:17 - login failure for user HPSupport from 192.168.0.46 via ftp;
20:42:18 - login failure for user root from 192.168.0.46 via ftp;
20:42:19 - login failure for user root from 192.168.0.46 via ftp;
20:42:20 - login failure for user admin from 192.168.0.46 via ftp;
20:42:21 - login failure for user login from 192.168.0.46 via ftp;
20:42:22 - login failure for user admin from 192.168.0.46 via ftp;
20:42:23 - login failure for user guest from 192.168.0.46 via ftp;
20:42:24 - login failure for user root from 192.168.0.46 via ftp;
I can see 2 waves of about 2 minutes each, then nothing.
This is clearly not a bug and definitely a malware/virus of some kind; I also know this is not IP spoofing as the reported IP is exactly the one from a PC I just started after 3 weeks of it being turned off. So I immediately performed a full scan of the PC (all drives) using AVG & Malwarebytes: nothing
Then I installed in turn: Spybot Search & Destroy, TotalAV and Kaspersky AV and performed full scans: nothing found.
I also looked at the startup programs and nothing comes out out of the ordinary (usual Microsoft, Intel, AsusTek, Corsair Memory, etc...)
And nothing that (even remotely) ressemble to 'crcs' as mentionned by ivicask
Any help appreciated identify (and remove) this malware. I know how to block all of this on the Mikrotik using Firewall rules, but I would rather leave it as is for now and know when I am being probed rather than not knowing it; and would rather fix the issue by getting rid of the malware
Thanks
Re: Brute passwords of microtik devices from the local network, how to identify malware?
Posted: Thu Feb 23, 2023 2:35 pm
by holvoetn
Try Safe Mode. If it stops then, you know there is definitely a service on your machine doing this.
Clean install again leaving out ALL the bloatware including those paid AVG and Malwarebytes. Standard Defender is more then enough for most PCs (though I will come clean admitting I use BitDefender on my personal device, it doesn't probe

)
Wireshark captures might give you some more clues ?
I guess you should be able to detect in Windows Firewall which program tries to reach your MT device (could be wrong but it's so basic that I assume it should be possible) ?
Especially since ftp and telnet are involved, those are easy ports to monitor for.
Re: Brute passwords of microtik devices from the local network, how to identify malware?
Posted: Thu Feb 23, 2023 6:19 pm
by rextended
Your computer have remote desktop service active?
Re: Brute passwords of microtik devices from the local network, how to identify malware?
Posted: Thu Feb 23, 2023 6:35 pm
by anav
rextended, is this a case where blackhole of bogons is effective ??
Re: Brute passwords of microtik devices from the local network, how to identify malware?
Posted: Thu Feb 23, 2023 6:44 pm
by rextended
rextended, is this a case where blackhole of bogons is effective ??
No, is the classic case of the Palantír is needed...
If IP is coming from LAN, is not a bogon from WAN the problem...
For example the BIOS/EFI of the PC can be hacked and is useless also change the internal HDD....
Re: Brute passwords of microtik devices from the local network, how to identify malware?
Posted: Thu Feb 23, 2023 6:48 pm
by anav
You misunderstood, I meant traffic FROM LAN, black hole bogons is not meant for incoming traffic, or at least I thought but garbage coming from LAN devices (aks dest addresses that have no merit) ????). If one wants to block legitimate WANIPs that are bad sites then get the service for pennies. -
https://itexpertoncall.com/promotional/moab.html
Re: Brute passwords of microtik devices from the local network, how to identify malware?
Posted: Tue Mar 07, 2023 8:57 pm
by spanik
Hello All
Thanks a lot for the various replies & ideas.
After 3 more waves of suspicious scans from various Windows destops & laptops in my house, and after starting to get really worried, I played with a combinations of Wireshark and Process Explorer and managed to narrow it down to the AVG Antivirus !!

(that is indeed installed on all my Windows devices).
Indeed, it seems that during a full scan (either planned or the ones that occur by themselves after a year without a scan having being executed, there is a new 'feature' in the Network Inspector module called
Test network devices for weak passwords ; and that's exactly what AVG does, it performs a port scan on all devices on your network and tries to login using known default users/passwords combinations.
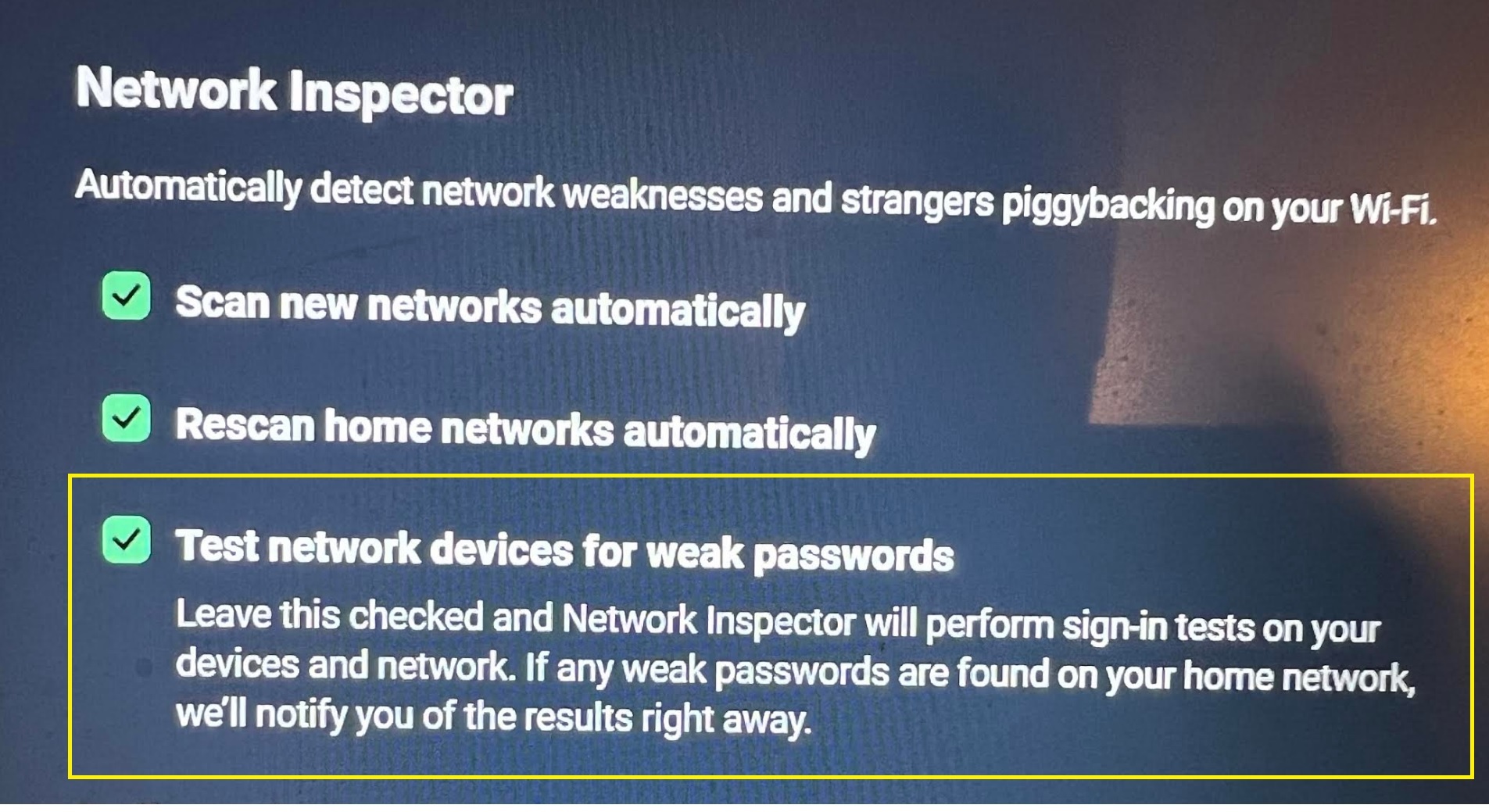
Disabling it stops the brute force from happening

So not a real malware as such, but definitly something I have now turned off; hope this can helps others identify and disable what could be seen by many as a malware
Thanks again to all for your help
Re: Brute passwords of microtik devices from the local network, how to identify malware?
Posted: Tue Mar 07, 2023 9:00 pm
by rextended
It's these kinds of crap programs, that do what want do without ask, the real malware...
I don't think you've popped up a window to ask for permission, and scanning from all devices to all devices is further bullshit, especially if you're using VPNs...
Re: Brute passwords of microtik devices from the local network, how to identify malware?
Posted: Tue Mar 07, 2023 9:02 pm
by holvoetn
I did mention to get rid of AVG, didn't I

Thanks for the feedback, though.
Surely some will encounter this as well so they know what may cause it.
Re: Brute passwords of microtik devices from the local network, how to identify malware?
Posted: Sat Mar 11, 2023 10:45 am
by spanik
Yes indeed rextended, I was never prompted for permissions and you are rigth holvoetn

Will keep it installed (for now) as I have paid for it, but will probably not renew as there is little benefit these days
Re: Brute passwords of microtik devices from the local network, how to identify malware?
Posted: Sat May 20, 2023 9:28 pm
by frengo
NOD32 also does the same.
I post the screenshots of only one device but it does it with all those in the LAN. I also realized that it was the PCs inside the LAN that did it but up until now I've always thought they were controlled by an external hacker.
Basically maybe it's really like this because it's absurd that an antivirus should do these things without asking for permission.
It seems to me something done on purpose for malice and commercial competition against MT who are the best and in any case could take some measures in the new FW.
In total, hacker or no hacker, essentially I have found myself in problems in the last few weeks with three newly bought 9-port RBs of which 2 are unreachable (
viewtopic.php?t=196227) and I hope to save the third by reinstalling the operating system with Netinstall (if it goes successful)....
Re: Brute passwords of microtik devices from the local network, how to identify malware?
Posted: Sat May 20, 2023 9:28 pm
by frengo
NOD32 also does the same.
I post the screenshots of only one device but it does it with all those in the LAN. I also realized that it was the PCs inside the LAN that did it but up until now I've always thought they were controlled by an external hacker.
Basically maybe it's really like this because it's absurd that an antivirus should do these things without asking for permission.
It seems to me something done on purpose for malice and commercial competition against MT who are the best and in any case could take some measures in the new FW.
In total, hacker or no hacker, essentially I have found myself in problems in the last few weeks with three newly bought 9-port RBs of which 2 are unreachable (
viewtopic.php?t=196227) and I hope to save the third by reinstalling the operating system with Netinstall (if it goes successful)....
