v7.2rc5 is released!
RouterOS version 7.2rc5 has been released "v7 testing" channel!
Before an upgrade:
1) Remember to make backup/export files before an upgrade and save them on another storage device;
2) Make sure the device will not lose power during upgrade process;
3) Device has enough free storage space for all RouterOS packages to be downloaded.
What's new in 7.2rc5 (2022-Mar-23 12:04):
*) api - accept "Content-Type" with specified charset;
*) arm - fixed "auto" CPU frequency setting;
*) arm64 - improved Watchdog initiated reboot reason reporting;
*) backup - fixed cloud backup's creation timezone;
*) bgp - added BGP advertisements display (requires output.keep-sent-attributes to be set);
*) bgp - fixed link-local iBGP address selection;
*) bgp - fixed network advertisement from address-lists after reboot;
*) bridge - fixed firewall "ingress-priority" matcher and "new-priority=from-ingress" action settings from VLAN tagged frames;
*) ccr2004 - improved system stability on CCR2004-12S+2XS;
*) crs1xx/2xx - fixed static switch host addresses after link down;
*) crs1xx/2xx - ignore static bridge host addresses (switch unicast-fdb should be used instead);
*) dhcpv6 - added VRF support;
*) dude - fixed The Dude client compatibility with RouterOS v7;
*) firewall - improved available port lookup for source NAT when free port range is exhausted;
*) ipsec - fixed "identities" menu emptying after RouterOS upgrade/reboot;
*) ipv6 - do not add duplicate dynamic prefix when static already exists;
*) ipv6 - fixed "retransmissit-interval" unit value;
*) ipv6 - fixed VLAN tagged PPPoE packet receiving on RB5009;
*) l2tp - fixed CHAP challenge packet processing over IPsec;
*) l3hw - improved routing table offloading for CRS305, CRS326-24G-2S+, CRS328, netPower, netFiber devices;
*) led - fixed LED behavior on Audience;
*) led - reduced LTE signal LED range to -70;
*) log - added warning message when connection tracking table is full;
*) lte - add IPv6 address on interface as well;
*) lte - added support for Uplink CA reporting;
*) lte - changed "CS/PS" registration type from "both" to "any" on R11e-LTE un R11e-LTE6;
*) lte - do not loose "band" configuration after reboot on Chateau 5G;
*) lte - fixed AT command response handling on R11e-LTE;
*) lte - fixed MBIM modem reset on AT timeout;
*) lte - fixed link flapping when loosing cellular signal on R11e-LTE un R11e-LTE6;
*) ntp - improved service stability when none of the NTP servers are reachable for a while;
*) ospf - general stability improvements;
*) ospf - improved DB retransmit logging;
*) ospf - send notifies for neighbors;
*) ovpn - improved memory allocation on Tile in "ethernet" mode;
*) ovpn - improved system stability in high load scenarios;
*) pimsm - fixed menu prints;
*) pimsm - general stability improvements;
*) queue - fixed queued IPv6 traffic considered as "invalid" by Firewall;
*) rb4011 - fixed jumbo frame processing on SFP+ port when using 1G module;
*) rip - added logging;
*) rip - fixed route metrics;
*) rip - fixed route redistribution;
*) rip - use nexthop with interface;
*) route - fixed "table" menu emptying after RouterOS upgrade;
*) route - fixed BGP atomic aggregate value;
*) route - fixed ECMP route removal;
*) route - general stability improvements;
*) routerboard - fixed "ether2" interface presence on some RBwAPGR devices;
*) routerboard - fixed WPS button functionality on Audience;
*) routing - added PCAP viewer tool for BGP advertisements debugging purposes;
*) routing-filter - fixed "bgp-*-communities-empty" matcher;
*) sfp - improved SFP module detection on CRS106 and CRS112;
*) smips - improved RAM allocation;
*) switch - added "rx-overflow" counter for 88E6393X (RB5009) and 88E6191X (CCR2004-16G-2S+) switch chips;
*) switch - improved packet forwarding with enabled "cpu-flow-control" setting between different rate interfaces for 88E6393X (RB5009) and 88E6191X (CCR2004-16G-2S+) switch chips;
*) tr069-client - added support for 5G band configuration;
*) tr069-client - added support for wireless "skip-DFS" configuration;
*) winbox - added missing "3GGP RAW" parameter under "Interface/Wireless/Interworking Profile" menu;
*) winbox - added missing "accounting", "interim-update" and "radius-password" parameters under "IP/DHCP Server" menu;
*) winbox - allow adding more than 100 tagged/untagged interfaces under "Bridge/VLAN" menu;
*) winbox - allow configuring "VTEP" under "Interface/VXLAN" menu;
*) winbox - fixed "00:00:00" time printing;
*) winbox - fixed switch related settings for MT7621 switch chip (hEX, hEX S, RBM33G, RBM11G, LtAP);
*) winbox - moved IPv4 and IPv6 "Rules" menus under "Routing" menu;
*) winbox - properly show "v" flag instead of "y" under "IP/Route" menu;
*) winbox - properly update server list under "System/NTP Client/Servers" menu;
*) winbox - show "System/Health/Settings" only on boards that have configurable values;
*) www - fixed "tls-version" for SSL;
*) x86 - allow to select disk for install image;
*) x86 - fixed NVME partition path;
*) zerotier - fixed IPv6 support;
To upgrade, click "Check for updates" at /system package in your RouterOS configuration interface, or head to our download page: http://www.mikrotik.com/download
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after some problem has appeared on device
Please keep this forum topic strictly related to this particular RouterOS release.
Before an upgrade:
1) Remember to make backup/export files before an upgrade and save them on another storage device;
2) Make sure the device will not lose power during upgrade process;
3) Device has enough free storage space for all RouterOS packages to be downloaded.
What's new in 7.2rc5 (2022-Mar-23 12:04):
*) api - accept "Content-Type" with specified charset;
*) arm - fixed "auto" CPU frequency setting;
*) arm64 - improved Watchdog initiated reboot reason reporting;
*) backup - fixed cloud backup's creation timezone;
*) bgp - added BGP advertisements display (requires output.keep-sent-attributes to be set);
*) bgp - fixed link-local iBGP address selection;
*) bgp - fixed network advertisement from address-lists after reboot;
*) bridge - fixed firewall "ingress-priority" matcher and "new-priority=from-ingress" action settings from VLAN tagged frames;
*) ccr2004 - improved system stability on CCR2004-12S+2XS;
*) crs1xx/2xx - fixed static switch host addresses after link down;
*) crs1xx/2xx - ignore static bridge host addresses (switch unicast-fdb should be used instead);
*) dhcpv6 - added VRF support;
*) dude - fixed The Dude client compatibility with RouterOS v7;
*) firewall - improved available port lookup for source NAT when free port range is exhausted;
*) ipsec - fixed "identities" menu emptying after RouterOS upgrade/reboot;
*) ipv6 - do not add duplicate dynamic prefix when static already exists;
*) ipv6 - fixed "retransmissit-interval" unit value;
*) ipv6 - fixed VLAN tagged PPPoE packet receiving on RB5009;
*) l2tp - fixed CHAP challenge packet processing over IPsec;
*) l3hw - improved routing table offloading for CRS305, CRS326-24G-2S+, CRS328, netPower, netFiber devices;
*) led - fixed LED behavior on Audience;
*) led - reduced LTE signal LED range to -70;
*) log - added warning message when connection tracking table is full;
*) lte - add IPv6 address on interface as well;
*) lte - added support for Uplink CA reporting;
*) lte - changed "CS/PS" registration type from "both" to "any" on R11e-LTE un R11e-LTE6;
*) lte - do not loose "band" configuration after reboot on Chateau 5G;
*) lte - fixed AT command response handling on R11e-LTE;
*) lte - fixed MBIM modem reset on AT timeout;
*) lte - fixed link flapping when loosing cellular signal on R11e-LTE un R11e-LTE6;
*) ntp - improved service stability when none of the NTP servers are reachable for a while;
*) ospf - general stability improvements;
*) ospf - improved DB retransmit logging;
*) ospf - send notifies for neighbors;
*) ovpn - improved memory allocation on Tile in "ethernet" mode;
*) ovpn - improved system stability in high load scenarios;
*) pimsm - fixed menu prints;
*) pimsm - general stability improvements;
*) queue - fixed queued IPv6 traffic considered as "invalid" by Firewall;
*) rb4011 - fixed jumbo frame processing on SFP+ port when using 1G module;
*) rip - added logging;
*) rip - fixed route metrics;
*) rip - fixed route redistribution;
*) rip - use nexthop with interface;
*) route - fixed "table" menu emptying after RouterOS upgrade;
*) route - fixed BGP atomic aggregate value;
*) route - fixed ECMP route removal;
*) route - general stability improvements;
*) routerboard - fixed "ether2" interface presence on some RBwAPGR devices;
*) routerboard - fixed WPS button functionality on Audience;
*) routing - added PCAP viewer tool for BGP advertisements debugging purposes;
*) routing-filter - fixed "bgp-*-communities-empty" matcher;
*) sfp - improved SFP module detection on CRS106 and CRS112;
*) smips - improved RAM allocation;
*) switch - added "rx-overflow" counter for 88E6393X (RB5009) and 88E6191X (CCR2004-16G-2S+) switch chips;
*) switch - improved packet forwarding with enabled "cpu-flow-control" setting between different rate interfaces for 88E6393X (RB5009) and 88E6191X (CCR2004-16G-2S+) switch chips;
*) tr069-client - added support for 5G band configuration;
*) tr069-client - added support for wireless "skip-DFS" configuration;
*) winbox - added missing "3GGP RAW" parameter under "Interface/Wireless/Interworking Profile" menu;
*) winbox - added missing "accounting", "interim-update" and "radius-password" parameters under "IP/DHCP Server" menu;
*) winbox - allow adding more than 100 tagged/untagged interfaces under "Bridge/VLAN" menu;
*) winbox - allow configuring "VTEP" under "Interface/VXLAN" menu;
*) winbox - fixed "00:00:00" time printing;
*) winbox - fixed switch related settings for MT7621 switch chip (hEX, hEX S, RBM33G, RBM11G, LtAP);
*) winbox - moved IPv4 and IPv6 "Rules" menus under "Routing" menu;
*) winbox - properly show "v" flag instead of "y" under "IP/Route" menu;
*) winbox - properly update server list under "System/NTP Client/Servers" menu;
*) winbox - show "System/Health/Settings" only on boards that have configurable values;
*) www - fixed "tls-version" for SSL;
*) x86 - allow to select disk for install image;
*) x86 - fixed NVME partition path;
*) zerotier - fixed IPv6 support;
To upgrade, click "Check for updates" at /system package in your RouterOS configuration interface, or head to our download page: http://www.mikrotik.com/download
If you experience version related issues, then please send supout file from your router to support@mikrotik.com. File must be generated while router is not working as suspected or after some problem has appeared on device
Please keep this forum topic strictly related to this particular RouterOS release.
-

-
fischerdouglas
Frequent Visitor

- Posts: 69
- Joined:
- Location: Brazil
- Contact:
Re: v7.2rc5 is released!
Thank you very much!RouterOS version 7.2rc5 has been released "v7 testing" channel!
What's new in 7.2rc5 (2022-Mar-23 12:04):
*) bgp - added BGP advertisements display (requires output.keep-sent-attributes to be set);
Re: v7.2rc5 is released!
Thats a big changelog. THX for your hard work.
Re: v7.2rc5 is released!
bgp - added BGP advertisements display (requires output.keep-sent-attributes to be set);
winbox - allow configuring "VTEP" under "Interface/VXLAN" menu;
ipv6 - fixed VLAN tagged PPPoE packet receiving on RB5009;
queue - fixed queued IPv6 traffic considered as "invalid" by Firewall;
thanks a ton finally
winbox - allow configuring "VTEP" under "Interface/VXLAN" menu;
ipv6 - fixed VLAN tagged PPPoE packet receiving on RB5009;
queue - fixed queued IPv6 traffic considered as "invalid" by Firewall;
thanks a ton finally
-

-
StubArea51
Trainer

- Posts: 1741
- Joined:
- Location: stubarea51.net
- Contact:
Re: v7.2rc5 is released!
Yassssss! :)
Code: Select all
What's new in 7.2rc5 (2022-Mar-23 12:04):
*) bgp - added BGP advertisements display (requires output.keep-sent-attributes to be set);Re: v7.2rc5 is released!
Update on RB5009 from RC4 to RC5 (ROS and RouterBoard FW) without Issues.
I´ll now test the IPv6 Queues......keep your fingers crossed ;-)
I´ll now test the IPv6 Queues......keep your fingers crossed ;-)
Re: v7.2rc5 is released!
I was about to ask why the container package is missing but then I noticed the changelog was updated.
You do not have the required permissions to view the files attached to this post.
Re: v7.2rc5 is released!
@emils is a fix for SUP-74962 included in this release?
Re: v7.2rc5 is released!
patrick7, if nobody has told you in this ticket, that fix was made, it means, it is not included
Re: v7.2rc5 is released!
@normis Thanks. That means, someone from MikroTik will proactively inform me as soon as the bug has been fixed?
Re: v7.2rc5 is released!
yes, we will let you know
Re: v7.2rc5 is released!
A quick check looks promising, no errors found as in the other ROS7.X releases :-)Update on RB5009 from RC4 to RC5 (ROS and RouterBoard FW) without Issues.
I´ll now test the IPv6 Queues......keep your fingers crossed ;-)
Btw: updates on CRS326-24S+2Q+, CRS328-24P-4S+ and CRS326-24G-2S+ went smooth without problems (ROS and FW)
Until now: Good job MT :-D
Re: v7.2rc5 is released!
Do you also update the MT Apps in RC releases ( like missing allowed IP addresses in peer settings )?
*) ios app - text
*) ios app - text
Re: v7.2rc5 is released!
RouterOS released have nothing to do with smartphone apps.
If you have a bug with smartphone app, email a bug report with pictures. Thanks.
If you have a bug with smartphone app, email a bug report with pictures. Thanks.
Re: v7.2rc5 is released!
Had a bit of a scare because Winbox closed directly on connecting. But soon it became clear that I was still using version 3.32, with version 3.35 it worked perfectly.
rb4011 - fixed jumbo frame processing on SFP+ port when using 1G module is the reason that I that soon updated from 7.1.5 to 7.2RC5 and the PPPoE is now showing a nice 1500 MTU instead of 1492 before.
It was a long wait but certainly worth it.
rb4011 - fixed jumbo frame processing on SFP+ port when using 1G module is the reason that I that soon updated from 7.1.5 to 7.2RC5 and the PPPoE is now showing a nice 1500 MTU instead of 1492 before.
It was a long wait but certainly worth it.
Re: v7.2rc5 is released!
Many many data fields are not populated with the MT App under IOS on my iPhone ... far too many to take pics .... I do not think that MikroTik look at this frequently.Do you also update the MT Apps in RC releases ( like missing allowed IP addresses in peer settings )?
*) ios app - text
Re: v7.2rc5 is released!
Is it anticipated that this release will resolve the slower than expected transfer rate issues with the RB5009 2.5G interface forwarding traffic when 2.5G is being advertised on the interface?*) switch - improved packet forwarding with enabled "cpu-flow-control" setting between different rate interfaces for 88E6393X (RB5009) and 88E6191X (CCR2004-16G-2S+) switch chips;
Re: v7.2rc5 is released!
I have noticed missing information in connections in Winbox regarding UDP/4500 (VPN tunnels)
I have several IKEv2 connections to an VPN provider and the tunnels are normally visible as UDP/4500. Now the displayed number of tunnels come and go like they are discontecting.
Then I also noticed if data is going trough the tunnels that traffic is not always shown shown. Does any one else also the same observation using 7.2RC5?
Update: I went back to 7.1.5 and there it also occurs. Tried it with Winbox 3.35 and, also with 3.32 which I used before.
Update 2: after running 7.1.5 for a while I still had no-connects to websites or time-out. So I went back to 7.1.1 which works fine for me. Next week I will upgrade first back to 7.1.5 and if that runs fine I will try again 7.2RC5.
Traffic is also not shown in connection tracking if is an IKEv2 tunnel but on the WireGuard traffic is show. This might be normal in v7 that traffic is not for IKEv2. On 7.1.1 tunnels also disappear and reappear.
I have several IKEv2 connections to an VPN provider and the tunnels are normally visible as UDP/4500. Now the displayed number of tunnels come and go like they are discontecting.
Then I also noticed if data is going trough the tunnels that traffic is not always shown shown. Does any one else also the same observation using 7.2RC5?
Update: I went back to 7.1.5 and there it also occurs. Tried it with Winbox 3.35 and, also with 3.32 which I used before.
Update 2: after running 7.1.5 for a while I still had no-connects to websites or time-out. So I went back to 7.1.1 which works fine for me. Next week I will upgrade first back to 7.1.5 and if that runs fine I will try again 7.2RC5.
Traffic is also not shown in connection tracking if is an IKEv2 tunnel but on the WireGuard traffic is show. This might be normal in v7 that traffic is not for IKEv2. On 7.1.1 tunnels also disappear and reappear.
Last edited by msatter on Thu Mar 24, 2022 2:06 pm, edited 4 times in total.
-

-
elgrandiegote
newbie
- Posts: 40
- Joined:
- Location: Buenos Aires, Argentina
Re: v7.2rc5 is released!
openvpn server udp, windows client version 2.5.6
this is normal?
this is normal?
You do not have the required permissions to view the files attached to this post.
Re: v7.2rc5 is released!
There's still a bug in the IPv6 firewall forward chain:
If an interface belongs to a vrf and you specify the same interface as in-interface, packets are not matched against the rule. In my case the packet matched the deny-all rule at the end and devices couldn't connect. in-interface parameter works if the interface is not part of a vrf. IPv4 firewall rule works correctly with in-interface set.
If an interface belongs to a vrf and you specify the same interface as in-interface, packets are not matched against the rule. In my case the packet matched the deny-all rule at the end and devices couldn't connect. in-interface parameter works if the interface is not part of a vrf. IPv4 firewall rule works correctly with in-interface set.
Code: Select all
/ip vrf
add interfaces=0077.GUEST name=VRF-GUESTCode: Select all
#works
/ipv6 firewall filter
add action=accept chain=forward out-interface=WG.MULLVAD.V6 src-address=fc00:0:0:77::/64Code: Select all
#doesn't work
/ipv6 firewall filter
add action=accept chain=forward in-interface=0077.GUEST out-interface=WG.MULLVAD.V6 src-address=fc00:0:0:77::/64-

-
elgrandiegote
newbie
- Posts: 40
- Joined:
- Location: Buenos Aires, Argentina
Re: v7.2rc5 is released!
After a few minutes of connection, this message appears, and it does not try to reconnect.
You do not have the required permissions to view the files attached to this post.
Re: v7.2rc5 is released!
Every time I reboot my router this happens to all graphs (CPU, Memory, Interfaces, Queues):
This has been happening since v7.2rc4.
I guess it might be related to my timezone because it's UTC-3 and the graph seems to be missing exactly 3h of data for every reboot.
This has been happening since v7.2rc4.
I guess it might be related to my timezone because it's UTC-3 and the graph seems to be missing exactly 3h of data for every reboot.
Code: Select all
/system clock
set time-zone-name=America/Sao_Paulo
/system ntp client
set enabled=yes
/system ntp client servers
add address=time1.google.com
add address=time2.google.com
add address=time3.google.com
add address=time4.google.com
/system package update
set channel=testing
/system routerboard settings
set auto-upgrade=yes
/tool graphing
set store-every=hour
/tool graphing interface
add
/tool graphing queue
add
/tool graphing resource
add
You do not have the required permissions to view the files attached to this post.
Re: v7.2rc5 is released!
Unfortunately it is not fixed completely.*) route - fixed "table" menu emptying after RouterOS upgrade;
I have a test router (CHR) with 7.2rc3 that I did not upgrade to 7.2rc4 because of this bug (after I already encountered it on another test router).
This had a second routing table with only some static routes and a couple of routing rules to select this table.
After the upgrade from 7.2rc3 to 7.2rc5 the second table was still in the /routing table list (add fib name=hamnet) and the static routes in that table remained OK, but the routing rules of the form "add action=lookup src-address=xx.xx.xx.xx/xx table=hamnet" now all had "table=*4000" instead of the table name and did not work anymore (this also happened in 7.2rc4 on other routers).
So I was locked out. Fortunately I also have console access via ESXi so I could recover it.
Re: v7.2rc5 is released!
but what command can we use for displaying BGP advertisements ?RouterOS version 7.2rc5 has been released "v7 testing" channel!
What's new in 7.2rc5 (2022-Mar-23 12:04):
*) bgp - added BGP advertisements display (requires output.keep-sent-attributes to be set);
-

-
armandfumal
Member Candidate

- Posts: 163
- Joined:
- Location: Weiswampach,LUX
- Contact:
Re: v7.2rc5 is released!
*) bgp - added BGP advertisements display (requires output.keep-sent-attributes to be set);
*) routing - added PCAP viewer tool for BGP advertisements debugging purposes;
Does somebody can explain how to ? where is the cmd ?
I can save the file and open the pcap file with wireshark and see the advertisements but it seems it is possible in RoS now...
*) routing - added PCAP viewer tool for BGP advertisements debugging purposes;
Does somebody can explain how to ? where is the cmd ?
I can save the file and open the pcap file with wireshark and see the advertisements but it seems it is possible in RoS now...
Re: v7.2rc5 is released!
There is some discussion about that BGP viewing in this topic: viewtopic.php?p=920879#p920879
-

-
armandfumal
Member Candidate

- Posts: 163
- Joined:
- Location: Weiswampach,LUX
- Contact:
Re: v7.2rc5 is released!
ThanksThere is some discussion about that BGP viewing in this topic: viewtopic.php?p=920879#p920879
Re: v7.2rc5 is released!
+1but what command can we use for displaying BGP advertisements ?RouterOS version 7.2rc5 has been released "v7 testing" channel!
What's new in 7.2rc5 (2022-Mar-23 12:04):
*) bgp - added BGP advertisements display (requires output.keep-sent-attributes to be set);
Re: v7.2rc5 is released!
Thanks for fixing the led on the audience 🙂
Re: v7.2rc5 is released!
Wow nice changelog. How long before some changes like The Dude and BGP networks after reboot fix, trickle to v7.1.x ? Before 7.2rc was too unstable, now it looks like the obvious better choice over 7.1 with all these fixes
Edit: Still says no dude package, so this just seems like a client-side fix for now
Edit: Still says no dude package, so this just seems like a client-side fix for now
Last edited by fragtion on Thu Mar 24, 2022 4:06 am, edited 3 times in total.
Re: v7.2rc5 is released!
Confirmed, this is finally working again :)*) ipv6 - fixed VLAN tagged PPPoE packet receiving on RB5009;
Re: v7.2rc5 is released!
I can confirm that this also fixes the issue of DSCP marked SSH or VoIP connections when using PPPoE with VLAN tagged interfaces.*) ipv6 - fixed VLAN tagged PPPoE packet receiving on RB5009;
Also, I finally get an MTU of 1500 if the underlying interface has MTU 1508, as you'd expect with PPPoE.
-

-
StubArea51
Trainer

- Posts: 1741
- Joined:
- Location: stubarea51.net
- Contact:
Re: v7.2rc5 is released!
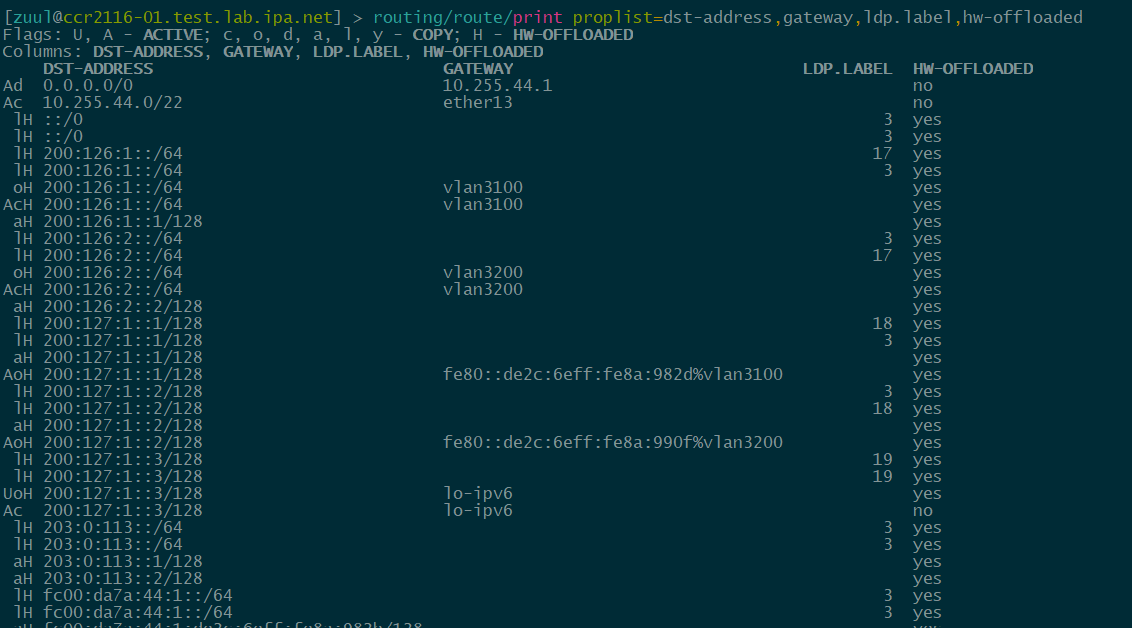
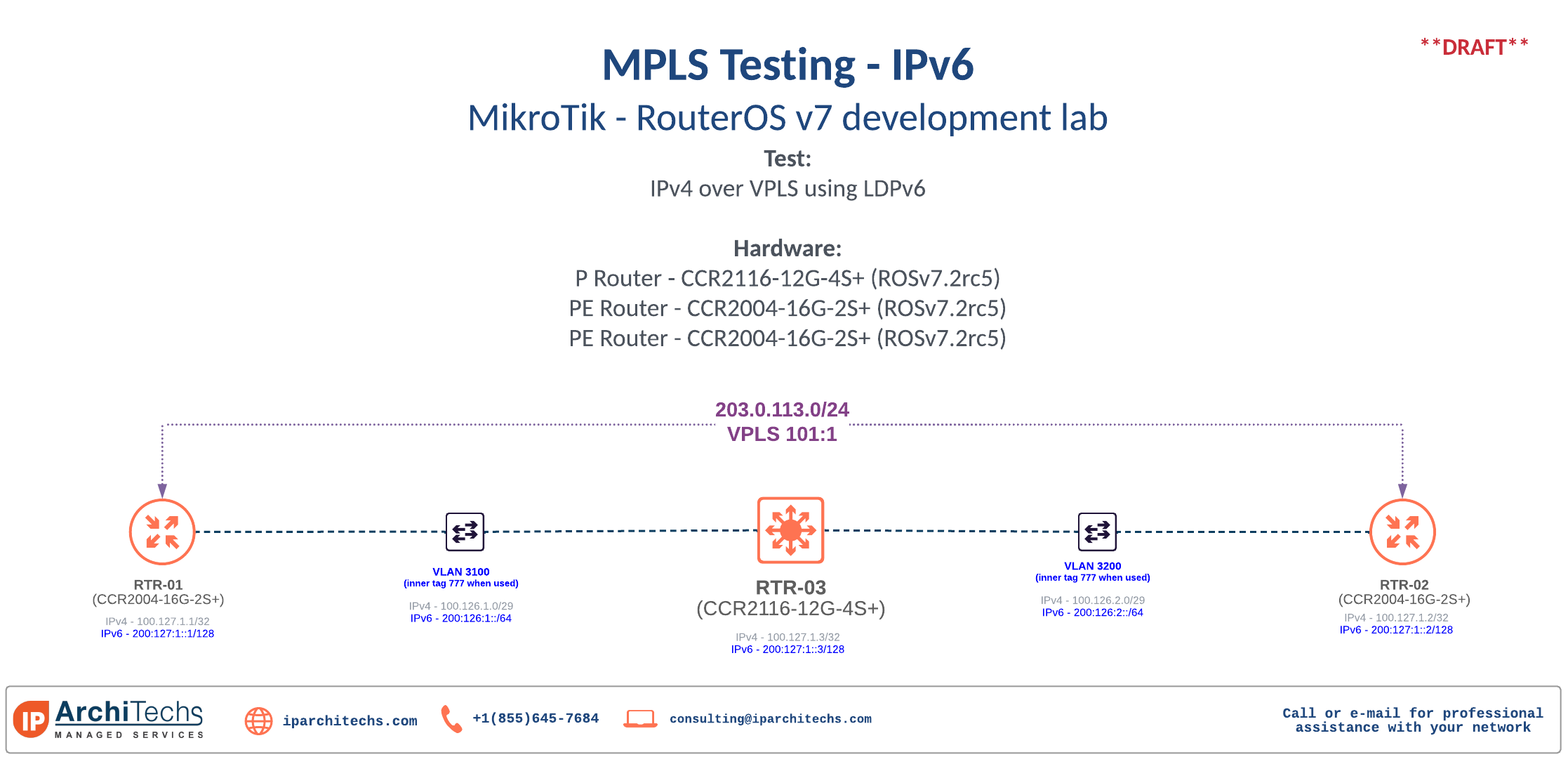
Did IPv6 and MPLS get enabled for hw-offload?
I'm pushing 1.6Gbps over VPLS using LDPv6 through a CCR2116 P router and have two CCR2004-16G-2S+ acting as PEs
The routing/route output shows IPv6 labeled prefixes as hw-offloaded and the cpu on the CCR2116 is only at 4% under a 1.6Gbps load
routing/route/print
Lab topology
I'm pushing 1.6Gbps over VPLS using LDPv6 through a CCR2116 P router and have two CCR2004-16G-2S+ acting as PEs
The routing/route output shows IPv6 labeled prefixes as hw-offloaded and the cpu on the CCR2116 is only at 4% under a 1.6Gbps load
routing/route/print

Lab topology

Re: v7.2rc5 is released!
Wifiwave2 package: still no wifi access rule numbers visible in Winbox to sort rules/understand order.
Will this be part of final 7.2? (I hope so)
Will this be part of final 7.2? (I hope so)
Re: v7.2rc5 is released!
That is interesting... When reading that I eagerly upgraded my RB4011 but for me this problem has not been fixed.I can confirm that this also fixes the issue of DSCP marked SSH or VoIP connections when using PPPoE with VLAN tagged interfaces.*) ipv6 - fixed VLAN tagged PPPoE packet receiving on RB5009;
Re: v7.2rc5 is released!
wireguard with ipv6 peers still doesn't work, you ought to reenter peer's ipv6 address (in allowed address) to allow ipv6 connection for that peer, meanwhile other peers loose ipv6
tested on 7.2rc5 hex and hap ac^2
basic peer config looks like
tested on 7.2rc5 hex and hap ac^2
Code: Select all
# mar/24/2022 11:38:03 by RouterOS 7.2rc5
# software id =
#
# model = RouterBOARD 750G r3
# serial number =
/interface wireguard
add listen-port=443 mtu=1420 name=ep3 private-key="..."
add listen-port=63016 mtu=1420 name=njalla private-key="..."
/interface wireguard peers
add allowed-address=0.0.0.0/0,::/0 endpoint-address=198.167.192.13 \
endpoint-port=51820 interface=njalla public-key="..."
add allowed-address=10.2.1.2/32,fd02:21::2/128 interface=ep3 public-key="..."
add allowed-address=10.2.1.3/32,fd02:21::3/128 interface=ep3 public-key="..."
/ipv6 firewall address-list
add address=::/128 list=bogon
add address=fec0::/10 list=bogon
add address=::ffff:0.0.0.0/96 list=bogon
add address=::/96 list=bogon
add address=100::/64 list=bogon
add address=2001:db8::/32 list=bogon
add address=2001:10::/28 list=bogon
add address=3ffe::/16 list=bogon
add address=ipv6.google.com disabled=yes list=resolve
add address=mikrotik.com list=resolve
add address=ipv6.google.com list=resolve
add address=wireguard.com list=resolve
add address=fd02:20::/64 list=njalla
add address=fd02:21::/64 list=njalla
/ipv6 firewall filter
add action=drop chain=input comment="drop invalid" connection-state=invalid
add action=accept chain=input comment="accept ICMPv6" protocol=icmpv6
add action=accept chain=input comment="accept established,related,untracked" \
connection-state=established,related,untracked
add action=accept chain=input comment="accept UDP traceroute" port=\
33434-33534 protocol=udp
add action=accept chain=input comment=\
"accept DHCPv6-Client prefix delegation" dst-port=546 protocol=udp \
src-address=fe80::/10
add action=accept chain=input comment="accept WG" dst-port=51820,6310 \
in-interface-list=all-input protocol=udp
add action=accept chain=input comment="accept IPsec ESP" protocol=ipsec-esp
add action=accept chain=input comment="accept IPsec AH" protocol=ipsec-ah
add action=accept chain=input comment="accept IPsec" dst-port=500,4500 \
protocol=udp
add action=accept chain=input comment="accept all that matches ipsec policy" \
ipsec-policy=in,ipsec
add action=accept chain=forward comment="accept established, related" \
connection-state=established,related
add action=drop chain=input comment="drop all from WAN" in-interface-list=\
all-input
add action=drop chain=forward comment="drop invalid" connection-state=invalid
add action=drop chain=forward comment="drop packets with bad src ipv6" \
src-address-list=bogon
add action=drop chain=forward comment="drop packets with bad dst ipv6" \
dst-address-list=bogon
add action=drop chain=forward comment="rfc4890 drop hop-limit=1" hop-limit=\
equal:1 protocol=icmpv6
add action=accept chain=forward comment="accept ICMPv6" protocol=icmpv6
add action=accept chain=forward comment="accept HIP" protocol=139
add action=accept chain=forward comment="accept IKE" dst-port=500,4500 \
protocol=udp
add action=accept chain=forward comment="accept ipsec AH" protocol=ipsec-ah
add action=accept chain=forward comment="accept ipsec ESP" protocol=ipsec-esp
add action=accept chain=forward comment=\
"accept all that matches ipsec policy" ipsec-policy=in,ipsec
add action=drop chain=forward comment=\
"drop everything else not coming from LAN" in-interface-list=all-input
/ipv6 firewall nat
add action=masquerade chain=srcnat ipsec-policy=out,none out-interface=njalla \
src-address-list=njalla
/ipv6 address
add address=fd02:20::1 interface=lo1
add address=fd02:21::1 interface=ep3
add address=fd03:1337::10 advertise=no interface=njalla
/ipv6 route
add disabled=no dst-address=::/0 gateway=fd03:1337::1 routing-table=main
add disabled=no distance=1 dst-address=2000::/3 gateway=njalla routing-table=\
main scope=30 target-scope=10
/ip address
add address=10.2.0.1/21 interface=lo1 network=10.2.0.0
add address=10.13.37.10/24 interface=njalla network=10.13.37.0
add address=10.2.1.0/24 interface=ep3 network=10.2.1.0
/ip firewall address-list
add address=0.0.0.0/8 list=bogon
add address=10.0.0.0/8 list=bogon
add address=100.64.0.0/10 list=bogon
add address=127.0.0.0/8 list=bogon
add address=169.254.0.0/16 list=bogon
add address=172.16.0.0/12 list=bogon
add address=192.0.0.0/24 list=bogon
add address=192.0.2.0/24 list=bogon
add address=192.168.0.0/16 list=bogon
add address=198.18.0.0/15 list=bogon
add address=198.51.100.0/24 list=bogon
add address=203.0.113.0/24 list=bogon
add address=224.0.0.0/4 list=bogon
add address=240.0.0.0/4 list=bogon
add address=10.2.0.0/21 list=local
add address=10.2.0.0/21 list=njalla
add address=10.2.8.0/21 list=njalla
/ip firewall filter
add action=add-src-to-address-list address-list=input-ep2 \
address-list-timeout=8h chain=input comment="list WG:443" disabled=yes \
dst-port=443 in-interface-list=all-input protocol=udp
add action=add-src-to-address-list address-list=input-ep1 \
address-list-timeout=8h chain=input comment="list WG:51820" disabled=yes \
dst-port=51820 in-interface-list=all-input protocol=udp
add action=accept chain=input comment="accept WG" dst-port=\
443,25260,51820,61952,62840,63016 in-interface-list=all-input protocol=\
udp
add action=accept chain=input comment="accept IPsec ESP" in-interface-list=\
all-input protocol=ipsec-esp
add action=accept chain=input comment="accept IPsec" dst-port=500,1701,4500 \
in-interface-list=all-input protocol=udp
add action=accept chain=input comment="accept WinBox" dst-port=8291 \
in-interface-list=all-input protocol=tcp src-address-list=white
add action=accept chain=input comment="accept SSH" dst-port=32610 \
in-interface-list=all-input protocol=tcp
add action=drop chain=input comment="drop invalid" connection-state=invalid
add action=accept chain=input comment="accept ICMP" protocol=icmp
add action=drop chain=input comment="drop bogon" in-interface-list=all-input \
src-address-list=bogon
add action=add-src-to-address-list address-list=trap address-list-timeout=2w \
chain=input comment="FIN scan" in-interface-list=all-input protocol=tcp \
src-address-list=!white tcp-flags=fin,!syn,!rst,!psh,!ack,!urg
add action=add-src-to-address-list address-list=trap address-list-timeout=2w \
chain=input comment="SYN/FIN scan" in-interface-list=all-input protocol=\
tcp src-address-list=!white tcp-flags=fin,syn
add action=add-src-to-address-list address-list=trap address-list-timeout=2w \
chain=input comment="SYN/RST scan" in-interface-list=all-input protocol=\
tcp src-address-list=!white tcp-flags=syn,rst
add action=add-src-to-address-list address-list=trap address-list-timeout=2w \
chain=input comment="FIN/PSH/URG scan" in-interface-list=all-input \
protocol=tcp src-address-list=!white tcp-flags=fin,psh,urg,!syn,!rst,!ack
add action=add-src-to-address-list address-list=trap address-list-timeout=2w \
chain=input comment="ALL/ALL scan" in-interface-list=all-input protocol=\
tcp src-address-list=!white tcp-flags=fin,syn,rst,psh,ack,urg
add action=add-src-to-address-list address-list=trap address-list-timeout=2w \
chain=input comment="NULL scan" in-interface-list=all-input protocol=tcp \
src-address-list=!white tcp-flags=!fin,!syn,!rst,!psh,!ack,!urg
add action=add-src-to-address-list address-list=trap address-list-timeout=2w \
chain=input comment="TCP psd=21,3s,3,1 scan" in-interface-list=all-input \
protocol=tcp psd=21,3s,3,1 src-address-list=!white
add action=add-src-to-address-list address-list=trap address-list-timeout=2w \
chain=input comment="port knocking" dst-port=\
20-25,53,109,110,137-139,445,1433,3389,5060 in-interface-list=all-input \
protocol=tcp src-address-list=!white
add action=accept chain=input comment="accept established, related" \
connection-state=established,related,untracked
add action=drop chain=input comment="drop all from WAN" in-interface-list=\
all-input
add action=accept chain=forward comment="accept IPsec in policy" \
ipsec-policy=in,ipsec
add action=accept chain=forward comment="accept IPsec out policy" \
ipsec-policy=out,ipsec
add action=fasttrack-connection chain=forward comment=fasttrack \
connection-state=established,related hw-offload=yes out-interface=\
all-ethernet
add action=accept chain=forward comment=\
"accept established, related, untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="drop invalid" connection-state=invalid
add action=drop chain=forward comment="drop all from WAN not DSTNATed" \
connection-nat-state=!dstnat connection-state=new in-interface-list=\
all-input
/ip firewall mangle
add action=change-mss chain=forward comment="pdmtu njalla" new-mss=\
clamp-to-pmtu out-interface=njalla passthrough=yes protocol=tcp \
tcp-flags=syn tcp-mss=1390-65535
add action=route chain=prerouting comment="route to njalla" dst-address-list=\
!bogon passthrough=no route-dst=10.13.37.1 src-address-list=njalla
/ip firewall nat
add action=masquerade chain=srcnat comment=masqurade ipsec-policy=out,none \
out-interface=njalla src-address-list=njalla
/ip firewall raw
add action=drop chain=prerouting comment="drop trap" in-interface-list=\
all-input src-address-list=trap
add action=drop chain=prerouting dst-address-list=!njalla src-address-list=\
drop
/ip firewall service-port
set ftp disabled=yes
set tftp disabled=yes
set irc disabled=yes
set h323 disabled=yes
set sip disabled=yes
set pptp disabled=yesCode: Select all
[Interface]
PrivateKey = ...
Address = fd02:21::2/128, 10.2.1.2/32
DNS = 10.2.0.1
[Peer]
PublicKey = M8sxz8etMnVkwmjcsKhfC0tpIc2p4Dlatq/3KShPtys=
AllowedIPs = 0.0.0.0/0, ::/0
Endpoint = ...:443
Last edited by borr on Thu Mar 24, 2022 11:17 am, edited 1 time in total.
Re: v7.2rc5 is released!
Any indication when partitioning on the RB5009 will work?
Re: v7.2rc5 is released!
That is a catch-all, so traffic is sent to this peer. Looks like configuration issue on your device...Code: Select all/interface wireguard peers add allowed-address=0.0.0.0/0,::/0 [...]
Re: v7.2rc5 is released!
It's not like IPSec rules. It does allow any traffic to be received from this peer, but it does not force all traffic to go through this peer, routing policy must be implemented additionally in Wireguard.
Re: v7.2rc5 is released!
Nah, you misunderstood. If you have several peers configured for one wireguard interface the "allowed-address" setting decides which peer receives the traffic routed to that interface. So given the traffic is actually routed to the correct wireguard interface but only one peer receives all that traffic it is most likely an issue with allowed addresses. So "allowed-address=0.0.0.0/0,::/0" is a catch-all for all traffic routed to the interface the peer is configured for.
Re: v7.2rc5 is released!
he has two wireguard interfaces, one containing that peer with ::/0 and another interface with two other peers, they shouldn't interfere as long as he has proper routing for all that, which I didn't check.
Re: v7.2rc5 is released!
Oh, missed that detail... For just one peer configured on that interface it is ok.
Re: v7.2rc5 is released!
please look into an export, i’ve included all the detailshe has two wireguard interfaces, one containing that peer with ::/0 and another interface with two other peers, they shouldn't interfere as long as he has proper routing for all that, which I didn't check.
Re: v7.2rc5 is released!
@Borr please start your own thread for the configuration issues you are having with Wireguard. It will get better attention and wont distract from others attempting to report on the actual thread topic. When you do, please add a network diagram as well.
-

-
th0massin0
Member Candidate

- Posts: 156
- Joined:
- Location: Poland
Re: v7.2rc5 is released!
@normis Could you please investigate something more about SUP-67642 ?
Re: v7.2rc5 is released!
I am on an RB5009, so it may have not been fixed on the 4011 (as the Change log explicitly mentions the 5009 only). Probably good idea to let MT know in any ticket you may have open with them on this.That is interesting... When reading that I eagerly upgraded my RB4011 but for me this problem has not been fixed.
I can confirm that this also fixes the issue of DSCP marked SSH or VoIP connections when using PPPoE with VLAN tagged interfaces.
Re: v7.2rc5 is released!
I have a ticket open, but to make it proceed I need to supply them with debugging info like traces, and it is a lot of work to setup a suitable test environment.I am on an RB5009, so it may have not been fixed on the 4011 (as the Change log explicitly mentions the 5009 only). Probably good idea to let MT know in any ticket you may have open with them on this.
(the only real datapoint I have been able to provide to them is that it works perfectly OK when the same config is loaded in a 2011 instead of a 4011)
So I was hopeful that it was now "accidentally" fixed because of the ticket you had open for the 5009. As it certainly is architecture-dependent.
Did you do plain SSH over PPPoE+VLAN? In my case I have a GRE/IPsec tunnel over PPPoE+VLAN and inside that I do SSH or BGP which gets stuck (due to nonzero DSCP).
I can fix it by putting a mangle rule in postrouting that clears the DSCP.
Re: v7.2rc5 is released!
Yes, I do "plain" VLAN+PPPoE. In my case it's the WAN connection and then I access SSH or VoIP resources on the internet. This was broken with certain DSCP values before but now seems to be fixed on my 5009.Did you do plain SSH over PPPoE+VLAN? In my case I have a GRE/IPsec tunnel over PPPoE+VLAN and inside that I do SSH or BGP which gets stuck (due to nonzero DSCP).
I mean this, to me, strongly suggests that you are seeing the same bug that we've seen on the 5009. I do remember seeing the same thing on my 4011 before I replaced it with a 5009.I can fix it by putting a mangle rule in postrouting that clears the DSCP.
Re: v7.2rc5 is released!
Yes it is likely the same thing. It also happened in RouterOS v6.49. I upgraded to v7 mainly to see if it was fixed. But it was the same.
I think it is either something ARM-specific (endianness? compiler bug?) or something switchchip-specific. On the 2011 it works as it should, I used it for many years.
I will have to wire an external switch with mirror function between the 4011 and my DSL modem and make a trace from there. Still not have gotten around to it.
Complicating factor is that this router has many VPN tunnels all working continuously and it is difficult to trace a single one from the PPPoE stream.
So it gets deferred all the time.
I think it is either something ARM-specific (endianness? compiler bug?) or something switchchip-specific. On the 2011 it works as it should, I used it for many years.
I will have to wire an external switch with mirror function between the 4011 and my DSL modem and make a trace from there. Still not have gotten around to it.
Complicating factor is that this router has many VPN tunnels all working continuously and it is difficult to trace a single one from the PPPoE stream.
So it gets deferred all the time.
-

-
blurrybird
newbie
- Posts: 38
- Joined:
Re: v7.2rc5 is released!
Can confirm that IPv6 queues are fixed in this release. Running on an hAP ac2 and RB5009 for some basic home network duties without issue.
Re: v7.2rc5 is released!
Does CAPsMAN already support Wave2 drivers?
Re: v7.2rc5 is released!
No, it doesn´t :-/Does CAPsMAN already support Wave2 drivers?
Re: v7.2rc5 is released!
Is there anyone who uses CAPsMAN on 7.2 and what experience has been with them?
Is ROS 7.2 already solid enough?
Is ROS 7.2 already solid enough?
Re: v7.2rc5 is released!
Unfortunately, yes, it is normal. But I start to think that in v6 it never really worked and now it is omitted because this device does not support it (which v6 did not know).I've noticed that CPU frequency missing from Resources. Is it normal?
Re: v7.2rc5 is released!
Yes, maybe. On my hAP ac2 I have seen variable CPU frequency working, but never on my 4011. Also not in v6. And when setting a lower CPU speed, the temperature remained exactly the same. So likely it did nothing.
Re: v7.2rc5 is released!
After 2 days testing I see issues with 5Ghz clients using Wifiwave2.
To do comparison is it possible to get the rc4 SW on which all worked fine?
release notes don't say anything about wifiwave2, but who can trust release notes ;-)
To do comparison is it possible to get the rc4 SW on which all worked fine?
release notes don't say anything about wifiwave2, but who can trust release notes ;-)
Re: v7.2rc5 is released!
Take download link for rc5 and replace all occurrences of "rc5" with "rc4" ... e.g. https://download.mikrotik.com/routeros/7.2rc5/routeros-7.2rc5-arm.npk -> https://download.mikrotik.com/routeros/7.2rc4/routeros-7.2rc4-arm.npk and similarly for the ZIP file containing extra packages.To do comparison is it possible to get the rc4 SW on which all worked fine?
What are the issues you encountered?
Re: v7.2rc5 is released!
You can just switch to your other partition where you saved the 7.2rc4 before upgrading, to compare it.To do comparison is it possible to get the rc4 SW on which all worked fine?
Re: v7.2rc5 is released!
Thanks MKX, great tip, works !What are the issues you encountered?
I see several 5G clients having suddenly problems to connect and keep stable connection.
Again, Wifi is not a simple science, and many things influence perf. and range. But having no issues
for few weeks and since Wednesday's upgrade a few makes me "suspicious". I prefer to downgrade and check it.
Re: v7.2rc5 is released!
When I was configuring my Audience I noticed clients could not connect to any of its radios until Audience synchronised time (to NTP server). Time step was usually "huge" (at least 20 seconds) so if time difference vetween client and AP is indeed the probkem, I've no idea what kind of offset is still acceptable.
Audience (and many other ARM devices) run at variable CPU speed. I can imagine that change in CPU speed can disturb time on device ...
I'm setting my audience to fixed CPU frequency to see if there's any difference.
Audience (and many other ARM devices) run at variable CPU speed. I can imagine that change in CPU speed can disturb time on device ...
I'm setting my audience to fixed CPU frequency to see if there's any difference.
Re: v7.2rc5 is released!
With the customer I work for, one of the first things I check when not getting a lease on dhcp for a client is time discrepancies.
Close to 50% it is the reason.
I've seen it cause issues already for 4 hours difference. Stupid Cisco router behind xDSL modem, nothing too advanced.
Close to 50% it is the reason.
I've seen it cause issues already for 4 hours difference. Stupid Cisco router behind xDSL modem, nothing too advanced.
Re: v7.2rc5 is released!
I'm just happy as Dude is back.
PS: Still waiting for unicorn mug.

PS: Still waiting for unicorn mug.

Re: v7.2rc5 is released!
I have had zero problems with this build so far. Or at least no new ones ;). Upgraded several systems from v7.2rc4 to rc5: MIPSBE (RB953), ARM (wAPacR,hAPac2), ARM64 (RB5009).I'm just happy as Dude is back.
Years I've been wanting to monitor LTE RSRQ/RSRP with the Dude, without script+cloud, finally:

Re: v7.2rc5 is released!
I'm just happy as Dude is back.
PS: Still waiting for unicorn mug.

Are you able to use dude in any way ? I loaded the package, but can't do anything with it yet.. :
Furthermore, the client (using latest 7.2rc5 client) says no dude package found when connecting to this router[admin@rb5009] > /dude/print
error - contact MikroTik support and send a supout file (2)
[admin@rb5009] > /dude/export
#error exporting /dude
@Amm0 I'm guessing it's not working on your rb5009 either?
Update: I tried to uninstall the dude package and reboot, but after not being able to connect back to the router for 10 minutes I hooked up the serial console and confirmed more than half my config had gone corrupt/missing (*at least the dude package was uninstalled successfully as well...*). Did another full config-reset and restored my last working backup, and posted "before and after" supout.rifs to support (SUP-78036). I advise RB5009 users steer clear of the dude until we know more about this
Re: v7.2rc5 is released!
Hi Mikrotik,
Is the TLS fix (*) www - fixed "tls-version" for SSL;) in this release going to be rolled into the stable (7.1.x) release train?
On 7.1.x TLSv1.0 and 1.1 are still offered, as are weak ciphers -
This is despite being set.
Andy
Is the TLS fix (*) www - fixed "tls-version" for SSL;) in this release going to be rolled into the stable (7.1.x) release train?
On 7.1.x TLSv1.0 and 1.1 are still offered, as are weak ciphers -
Code: Select all
SSLv2 not offered (OK)
SSLv3 not offered (OK)
TLS 1 offered (deprecated)
TLS 1.1 offered (deprecated)
TLS 1.2 offered (OK)
TLS 1.3 not offered and downgraded to a weaker protocol
NPN/SPDY not offered
ALPN/HTTP2 not offered
Testing cipher categories
NULL ciphers (no encryption) not offered (OK)
Anonymous NULL Ciphers (no authentication) not offered (OK)
Export ciphers (w/o ADH+NULL) not offered (OK)
LOW: 64 Bit + DES, RC[2,4] (w/o export) not offered (OK)
Triple DES Ciphers / IDEA not offered
Obsolete CBC ciphers (AES, ARIA etc.) offered
Strong encryption (AEAD ciphers) offered (OK)
This is despite
Code: Select all
tls-version=only-1.2Andy
Re: v7.2rc5 is released!
Nope not on RB5009, didn't try... Only an Audience I use for testing. But I very interested in it working on RB5009.@Amm0 I'm guessing it's not working on your rb5009 either?I'm just happy as Dude is back.
We have a couple of pair of RB5009 using VRRP in quasi-production. I had some issues with 7.1.1, which is only reason why the RB5009 are on the 7.2rc5 chain. I'm sure the RB5009 will stabilize, but yeah I read the reports of odd problems... Seen some even. Not my first test case for anything ;). I still haven't been adventurous to try the new VRRP "sync connection" on my pair of RB5009 in service.
Still VERY happy to see the package return! I can wait a few builds for it get sorted out, never was going to be problematic for us. We sometimes use Dude today to do "self monitoring" e.g. use Dude server to record stats on device it's running on with remote sites/LTE devices, since any remote monitoring uses potentially limited bandwidth. So as "snmp recorder" the Dude it's great.
Re: v7.2rc5 is released!
Is there a good way of not forgetting to copy your current config to all partitions after any configuration changes?You can just switch to your other partition where you saved the 7.2rc4 before upgrading, to compare it.
Re: v7.2rc5 is released!
Not sure what that "fix" implies but on my rb5009 the issue hasn't been fixed. With frequency set to auto(default) and using simple queue with cake or fq codel max speed is 700-750, but setting frequency to 1400 gets full 940 speed on a gigabit link
*) arm - fixed "auto" CPU frequency setting;
Re: v7.2rc5 is released!
Well, in my case I use it to store entire versions before upgrade, so the "copy partition" operation is just part of my procedure to upgrade:Is there a good way of not forgetting to copy your current config to all partitions after any configuration changes?You can just switch to your other partition where you saved the 7.2rc4 before upgrading, to compare it.
- check if there are no garbage files and delete them
- copy part0 to part1
- download upgrade
- reboot
Sometimes I make a "checkpoint" of an entire setup without doing an upgrade, e.g. before major changes. Then I just do the first 2 steps.
When that has been done, and one wants to do it again, there also is a "save config to" operation, but I use it only when the destination partition has the same RouterOS version.
Of course anything can be scripted and scheduled...
-

-
blurrybird
newbie
- Posts: 38
- Joined:
Re: v7.2rc5 is released!
hAP ac2 after upgrading was extremely unstable. Would crash and lock up when trying to access it via either webfig or winbox.
Worked out the CPU was running at 400MHz and set to the auto setting.
Setting manually to 716MHz seems to have fixed the problem for now.
Worked out the CPU was running at 400MHz and set to the auto setting.
Setting manually to 716MHz seems to have fixed the problem for now.
-

-
zainarbani
Frequent Visitor

- Posts: 54
- Joined:
- Location: Pati, Indonesia
Re: v7.2rc5 is released!
unified kernel = easy to maintain != easy to bring up
kudos to whoever behind this development
kudos to whoever behind this development
Re: v7.2rc5 is released!
unified kernel = easy to maintain != easy to bring up
kudos to whoever behind this development
I don't think that having several kernel variants with different patch sets and compile options would ensure better stability and/or lower number of bugs. One has to remember that kernel in v6 was used almost unaltered for many years, during which a number of problems were solved. I'm pretty sure MT devs are on similar track right now, latest releases (7.1.5 and 7.2rc5) seem to be much better than early v7 releases. As they say, Rome wasn't built in a day.
Re: v7.2rc5 is released!
I think the RB4011 does not have settable CPU frequency and the fact you could set it in 6.49.5 was an error that has been fixed in 7.2On my RB4011iGS+ after upgrade from 6.49.5 to 7.2rc5 I can't even set CPU frequency
-

-
zainarbani
Frequent Visitor

- Posts: 54
- Joined:
- Location: Pati, Indonesia
Re: v7.2rc5 is released!
I didn't said that MikroTik should bring different kernel for each board/releases, what i mean is since mikrotik adopt unified kernel style then initial migrations/bringup to new kernel would take more time. lets say ARM arch, there's atleast 25 device using same build/kernel even phisically looks the same but kernel conf (pinctrl, gpio, clock freq, pci, etc) was different. thats only the kernel side, tons of proprietary modules need to be adapted as well.I don't think that having several kernel variants with different patch sets and compile options would ensure better stability and/or lower number of bugs.
Re: v7.2rc5 is released!
If MT wants to introduce same feature set to all of supported devices (different architectures, different hardware), then they have to do all the stuff at the same time regardless.
Much of stuff you're mentioning (clock, PCI, ...) is automatically set up or detected by linux kernel for the last 20+ years. Different thing are drivers (just because linux kernel displays the name it doesn't mean it's got driver ... and the other way around), but drivers are again pretty much the same regardless exact hardware construction and even architecture.
There are bugs which have to be ironed out (e.g. clock scaling on particular devices, stability of some drivers, etc.), but I don't think it would be benefitial to do things on separate kernel variants at this stage (v7 being rolled with lots of stability fixes on all supported architectures).
BTW, I don't see what "unified kernel style" means in context of this debate.
Much of stuff you're mentioning (clock, PCI, ...) is automatically set up or detected by linux kernel for the last 20+ years. Different thing are drivers (just because linux kernel displays the name it doesn't mean it's got driver ... and the other way around), but drivers are again pretty much the same regardless exact hardware construction and even architecture.
There are bugs which have to be ironed out (e.g. clock scaling on particular devices, stability of some drivers, etc.), but I don't think it would be benefitial to do things on separate kernel variants at this stage (v7 being rolled with lots of stability fixes on all supported architectures).
BTW, I don't see what "unified kernel style" means in context of this debate.
-

-
zainarbani
Frequent Visitor

- Posts: 54
- Joined:
- Location: Pati, Indonesia
Re: v7.2rc5 is released!
well nvm this is just my opinions tho. and uh.. which debate ?BTW, I don't see what "unified kernel style" means in context of this debate.
Re: v7.2rc5 is released!
Our debate... which debate ?BTW, I don't see what "unified kernel style" means in context of this debate.
-

-
zainarbani
Frequent Visitor

- Posts: 54
- Joined:
- Location: Pati, Indonesia
Re: v7.2rc5 is released!
dude, how this can be a debate? lolOur debate.
well, so umm.. i lose this debate i guess?
Re: v7.2rc5 is released!
Umm.. I have mine set at 1.2 instead of 1.4 and it seems to work, I could test if throughput is hurt at even lower frequencies.I think the RB4011 does not have settable CPU frequency and the fact you could set it in 6.49.5 was an error that has been fixed in 7.2On my RB4011iGS+ after upgrade from 6.49.5 to 7.2rc5 I can't even set CPU frequency
Re: v7.2rc5 is released!
dude, how this can be a debate? lolOur debate.
well, so umm.. i lose this debate i guess?
This is not an argument, it's a debate, so nobody has to loose :wink:
Re: v7.2rc5 is released!
When I was still using v6 I set the CPU frequency to the lowest available and the temperature remained exactly the same. So I doubt it changed anything.Umm.. I have mine set at 1.2 instead of 1.4 and it seems to work, I could test if throughput is hurt at even lower frequencies.
I think the RB4011 does not have settable CPU frequency and the fact you could set it in 6.49.5 was an error that has been fixed in 7.2
Re: v7.2rc5 is released!
On a pair of Audience I've been on ROS7 since initial versions with Wave2.
With this release is the first time I'm having an issue with company laptop - a Dell equipped with AC8265.
The message "Can't connect to this network" and searching in its Windows 10 wlan- Autoconfig Event log there are always 3 consecutive errors:
1.
On security tab, I've got the following checked:
- auth: WPA2/WPA3
- encr: CCMP/CCMP256/GCMP/GCMP256
- passphrase
- disable PMKID
- WPS disabled
All other devices in the household connected without an issue (IOTs, smartphones including an initially stubborn Oneplus9, laptops, Google devices etc) .. except from this crappy Dell.
I'm a limited user so I can't fiddle with drivers..
With this release is the first time I'm having an issue with company laptop - a Dell equipped with AC8265.
The message "Can't connect to this network" and searching in its Windows 10 wlan- Autoconfig Event log there are always 3 consecutive errors:
1.
2.WLAN AutoConfig service started a connection to a wireless network.
Network Adapter: Intel(R) Dual Band Wireless-AC 8265
Interface GUID: {............................}
Connection Mode: Connection to a secure network without a profile
Profile Name: Beta
SSID: Beta
BSS Type: Infrastructure
3.Wireless network association started.
Network Adapter: Intel(R) Dual Band Wireless-AC 8265
Interface GUID: {..........................}
Local MAC Address: XX:XX:XX:XX:XX:XX
Network SSID: Beta
BSS Type: Infrastructure
Authentication: WPA2-Personal
Encryption: AES-CCMP
802.1X Enabled: No
None of the 2 Audience logs shows any attempt of this laptop to connect to the wireless networks.WLAN AutoConfig service failed to connect to a wireless network.
Network Adapter: Intel(R) Dual Band Wireless-AC 8265
Interface GUID: {...................................}
Connection Mode: Connection to a secure network without a profile
Profile Name: Beta
SSID: Beta
BSS Type: Infrastructure
Failure Reason:The specific network is not available.
RSSI: 255
On security tab, I've got the following checked:
- auth: WPA2/WPA3
- encr: CCMP/CCMP256/GCMP/GCMP256
- passphrase
- disable PMKID
- WPS disabled
All other devices in the household connected without an issue (IOTs, smartphones including an initially stubborn Oneplus9, laptops, Google devices etc) .. except from this crappy Dell.
I'm a limited user so I can't fiddle with drivers..
Re: v7.2rc5 is released!
icmp [the router is not able to ping outside hosts after 24/36h of operation, on heavy traffic 40-50gbps] issue is still present on x86 and chr (passthrough) equipped with mellanox connectx-5 cards.
SUP-67221 updated with latest supout taken during the sisue.
regards
Ros
SUP-67221 updated with latest supout taken during the sisue.
regards
Ros
Last edited by rpingar on Tue Mar 29, 2022 3:16 pm, edited 2 times in total.
Re: v7.2rc5 is released!
I saw this as well. Clients report that password is incorrect and can't connect, but nothing in the audience log at all (info logging enabled)None of the 2 Audience logs shows any attempt of this laptop to connect to the wireless networks.
(settings are all showing ok).
Luckily after few reboots problem is gone and did not come back till now. (I did not change or re-enter any password on the client side).
unfortunately little feedback/inputs from Mikrotik on wifiwave2 package content/stability.
Seems they do not care too much, does not motivate me to further dig deeper into this...
Re: v7.2rc5 is released!
Wow!!Did IPv6 and MPLS get enabled for hw-offload?
I'm pushing 1.6Gbps over VPLS using LDPv6 through a CCR2116 P router and have two CCR2004-16G-2S+ acting as PEs
The routing/route output shows IPv6 labeled prefixes as hw-offloaded and the cpu on the CCR2116 is only at 4% under a 1.6Gbps load
Re: v7.2rc5 is released!
I am having big problem with IKEv2 as I wrote earlier and a straight 12 hour search to find the problem I gave up and disabled IKEv2 and only WireGuard for now.
What happens is that the tunnel UDP/4500 itself get route marked which prevent leaking of traffic. How thats happens is unknown to me and in time I will have a new go at it time.I noticed that even the Wireguard start spooking building tunnels up and second tunnels coming in on the same ports.
Maybe there then is happening something in routing between the IKEv2 routing and the WireGuard routes.
What happens is that the tunnel UDP/4500 itself get route marked which prevent leaking of traffic. How thats happens is unknown to me and in time I will have a new go at it time.I noticed that even the Wireguard start spooking building tunnels up and second tunnels coming in on the same ports.
Maybe there then is happening something in routing between the IKEv2 routing and the WireGuard routes.
-

-
vvchumanov
just joined
- Posts: 2
- Joined:
Re: v7.2rc5 is released!
when we full support OpenVPN option ? why don't have import .ovpn edit file ? udp non stable..*) ovpn - improved memory allocation on Tile in "ethernet" mode;
*) ovpn - improved system stability in high load scenarios;
Re: v7.2rc5 is released!
I'll never understand why some users insist on using OpenVPN - MikroTik Limited Edition.
Re: v7.2rc5 is released!
MikroTik only support (part of) the OpenVPN protocol, they do not even call it OpenVPN but rather OVPN. Any similarity seems like a coincidence.when we full support OpenVPN option ? why don't have import .ovpn edit file ? udp non stable..
For some reason, likely licensing or maybe space reasons as well, RouterOS does not use the opensource OpenVPN program.
So features like .ovpn file parsing are not included in it.
Frankly I would have expected OpenVPN to be moved into a separate optional package on v7 and then use the opensource version, but rather they chose to again put a lot of work in their OVPN thing (and still having problems). So the reason not to do that seems really compelling.
Once the Docker container feature is back, it should be possible to put a real OpenVPN service in a docker container and end all this misery... but of course you then need to have a router with sufficient resources (storage, memory) to run it.
Who is online
Users browsing this forum: No registered users and 9 guests





