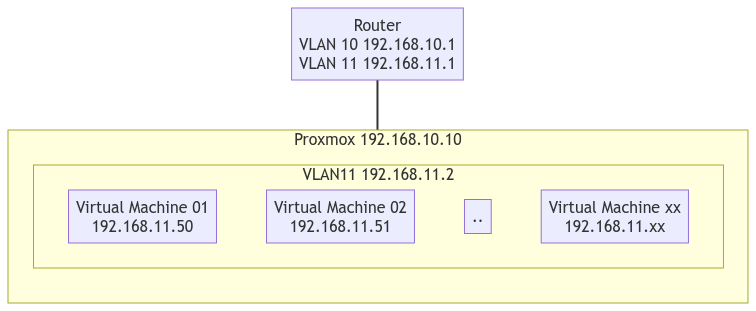
after resolving this issue viewtopic.php?t=206359 just wanted to know how to setup RouterOS 7 (without external switch) in order to have the following setup:
- VLAN10, 192.168.10.0/24, for router and proxmox management
- VLAN11, 192,168,11.0/24, for virtualized machines inside Proxmox nodes on VLAN10
Besides Proxmox and virtualized machines setup, what would be the correct configuration of tagget/untagged in the router. Now I have the following conf (only what I believe is important for VLAN conf) but only VLAN10 is working (internet, LAN connection), VLAN11 outside proxmox working ok, VLAN11 inside proxmox seems not to have network connectivity (inside and outside):
Code: Select all
/interface bridge
add name=aBridge port-cost-mode=short protocol-mode=none pvid=11 vlan-filtering=yes
/interface vlan
add interface=aBridge name=VLAN10 vlan-id=10
add interface=aBridge name=VLAN11 vlan-id=11
/interface list
add name=WAN
add name=LAN
[...]
/ip pool
add name=VLAN10_POOL ranges=192.168.10.100-192.168.10.200
add name=VLAN11_POOL ranges=192.168.11.100-192.168.11.200
/ip dhcp-server
add address-pool=VLAN10_POOL interface=VLAN10 lease-time=10m name=VLAN10_DHCP
add address-pool=VLAN11_POOL interface=VLAN11 lease-time=10m name=VLAN11_DHCP
[..]
/interface bridge port
add bridge=aBridge frame-types=admit-only-untagged-and-priority-tagged interface=ether2 internal-path-cost=10 path-cost=10 pvid=10
add bridge=aBridge frame-types=admit-only-untagged-and-priority-tagged interface=ether3 internal-path-cost=10 path-cost=10 pvid=10
add bridge=aBridge frame-types=admit-only-untagged-and-priority-tagged interface=wlan1 internal-path-cost=10 path-cost=10 pvid=10
add bridge=aBridge frame-types=admit-only-untagged-and-priority-tagged interface=wlan2 internal-path-cost=10 path-cost=10 pvid=11
add bridge=aBridge frame-types=admit-only-untagged-and-priority-tagged interface=ether4 internal-path-cost=10 path-cost=10 pvid=11
add bridge=aBridge frame-types=admit-only-untagged-and-priority-tagged interface=ether5 internal-path-cost=10 path-cost=10 pvid=11
[..]
/interface bridge vlan
add bridge=3TSBridge tagged=3TSBridge vlan-ids=101
add bridge=3TSBridge tagged=3TSBridge vlan-ids=100
/interface list member
add interface=ether1 list=WAN
add interface=VLAN10 list=LAN
add interface=VLAN11 list=LAN
/ip address
add address=192.168.10.1/24 interface=VLAN10 network=192.168.10.0
add address=192.168.11.1/24 interface=VLAN11 network=192.168.11.0
[..]
/ip dhcp-server network
add address=192.168.10.0/24 dns-server=192.168.10.1 gateway=192.168.10.1
add address=192.168.11.0/24 dns-server=192.168.11.1 gateway=192.168.11.1
/ip dns
set allow-remote-requests=yes
/ip firewall address-list
add address=192.168.10.0/24 list=LAN
add address=192.168.11.0/24 list=LAN
/ip firewall filter
add action=accept chain=input comment="Accept established/related/untracked" connection-state=established,related,untracked
add action=drop chain=input comment="Drop invalid" connection-state=invalid
add action=accept chain=input comment="Accept ICMP" protocol=icmp
add action=accept chain=input comment="Accept local loopback (for CAPsMAN)" dst-address=127.0.0.1
add action=drop chain=input comment="Drop all not comming from LAN" in-interface-list=!LAN
add action=accept chain=forward comment="Accept in ipsec policy" ipsec-policy=in,ipsec
add action=accept chain=forward comment="Accept out ipsec policy" ipsec-policy=out,ipsec
add action=fasttrack-connection chain=forward comment="Fastrack for established/related" connection-state=established,related hw-offload=yes
add action=accept chain=forward comment="Accept forwardig of established/related/untracked" connection-state=established,related,untracked
add action=drop chain=forward comment="Drop all WAN not NATed" connection-nat-state=!dstnat connection-state=new in-interface-list=WAN
/ip firewall nat
add action=masquerade chain=srcnat comment="NAT out" ipsec-policy=out,none out-interface-list=WAN
[..]
Juan Ignacio.